
A menace actor introduced on a cybercrime discussion board that they offered the supply code and a cracked model of the Zeppelin ransomware builder for simply $500.
The publish was noticed by menace intelligence firm KELA and whereas the legitimacy of the provide has not been validated, the screenshots from the vendor point out that the bundle is actual.
Whoever purchased the bundle may use the malware to spin up a brand new ransomware-as-a-service (RaaS) operation or write a brand new locker based mostly on the Zeppelin household.
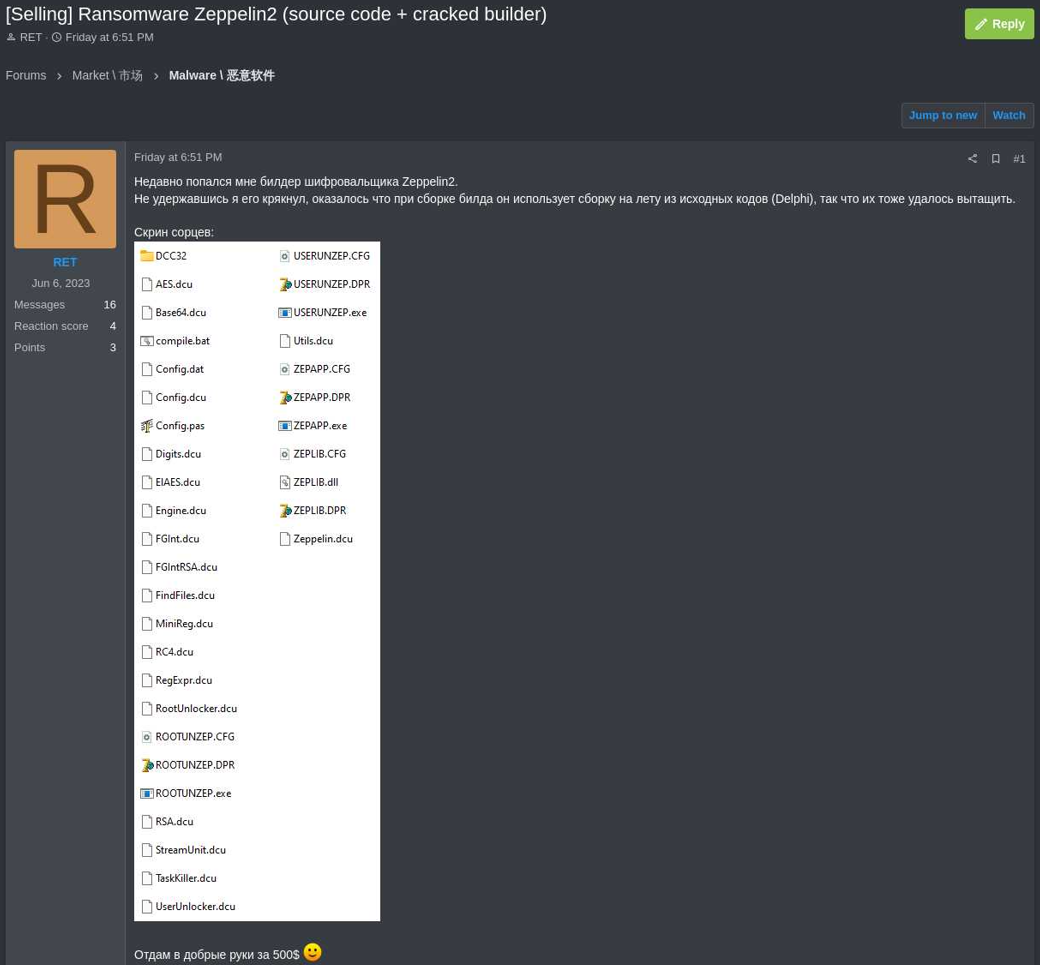
The vendor of the Zeppelin supply code and builder makes use of the deal with ‘RET’ and clarified that they didn’t creator the malware however merely managed to crack a builder model for it. RET added that they’d acquired the bundle with out a license.
“The place I obtained the builder with out a license is my enterprise. […] I simply cracked the builder,” the vendor wrote in a reply to different members of the hacker discussion board.
The cybercriminal famous that they supposed to promote the product to a single purchaser and would freeze the sale till finishing the transaction.
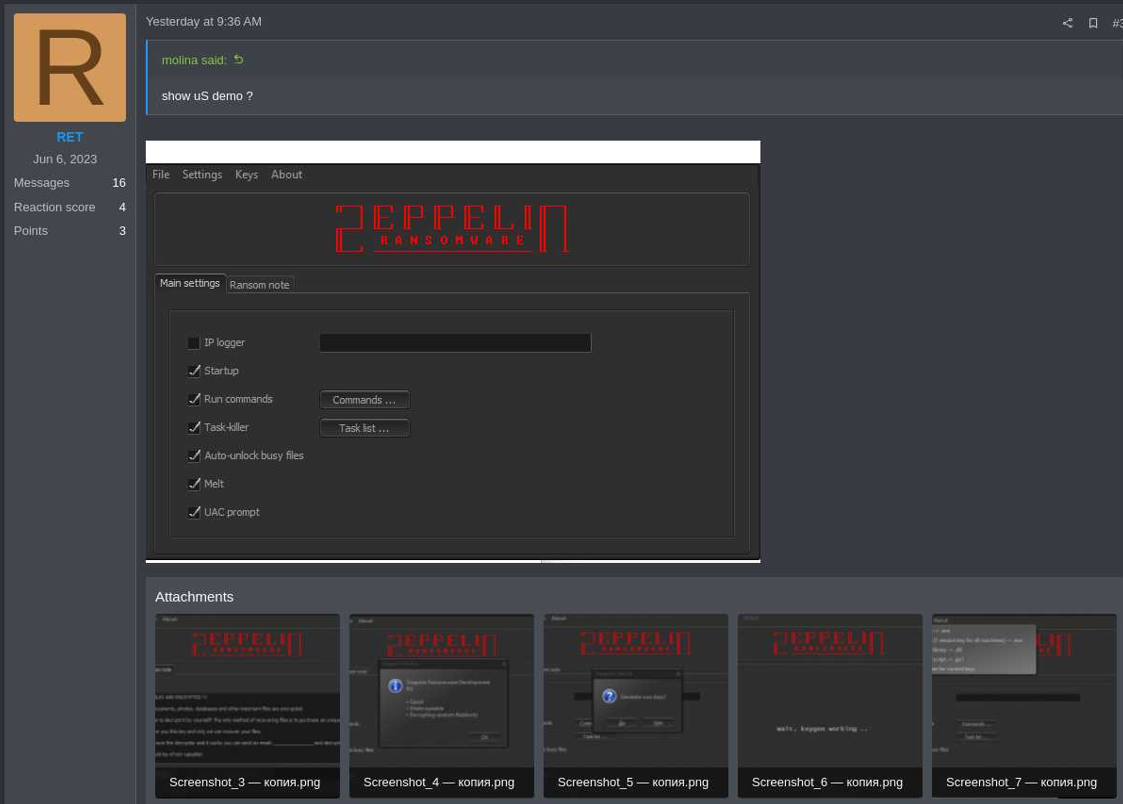
In November 2022, following the discontinuation of the Zeppelin RaaS operation, regulation enforcement and safety researchers disclosed they’d discovered exploitable flaws in Zeppelin’s encryption scheme, permitting them to construct a decrypter and assist victims since 2020.
A person on the Zeppelin discussion board thread asks explicitly whether or not the brand new model has fastened the issues within the cryptography implementation, to which the vendor replies by saying that it is the second model of the malware that ought to now not embrace the vulnerabilities.
Zeppelin ransomware background
Zeppelin is a spinoff of the Delphi-based Vega/VegaLocker malware household that was energetic between 2019 and 2022. It was utilized in double-extortion assaults and its operators typically requested for ransoms as large as $1 million.
Builds of the unique Zeppelin ransomware had been offered for as much as $2,300 in 2021, after its creator had introduced a serious replace for the software program.
The RaaS supplied a comparatively advantageous deal to associates, permitting them to maintain 70% of the ransom funds, with 30% going to the developer.
In the summertime of 2022, the Federal Bureau of Investigation (FBI) warned a couple of new tactic employed by Zeppelin ransomware operators involving a number of rounds of encryption.

