After I was a safety government for a late-stage startup within the early days of fintech, a peer informed me the three-envelope parable for the primary time. Its origin just isn’t completely clear (this 1982 Washington Put up opinion piece opens with a two letter Soviet-era model), however the story is usually tailored to many various management roles. For a chief data safety officer (CISO), it reads one thing like this:
A brand new CISO walks into their workplace for the primary time and finds three envelopes on the desk. They’re labeled 1 to three, and with them is a quick word from their predecessor:
“Congratulations on the brand new function! I’m positive that you’re going to do nice. However, if one thing goes incorrect and you might be compelled to answer a significant safety incident or information breach, open the following envelope within the collection for steering.”
Throughout the first incident, the CISO opens the primary envelope to seek out the recommendation,
“Blame your predecessor.”
After the second incident, the CISO opens the second envelope, which says,
“Blame your price range.”
Within the third envelope is one other three-word word,
“Put together three letters.”
The merciless actuality is that many CISOs attain the third-envelope stage after as little as 18 months of their function. The exception could also be CISOs managing safety packages with vital sources, akin to Fortune 500 firms, who appear to retain their roles far longer. However it might be a mistake to imagine that longevity is barely as a consequence of bigger budgets. Most CISOs, whatever the relative depth of their pockets, don’t assume they’ve adequate sources for a really efficient safety program.
In my expertise working with safety executives at organizations of nearly each dimension, I’ve realized that probably the most constant key to success isn’t price range, it’s understanding your organization’s safety “character”—and figuring out the crucial supporting roles and practices wanted to enrich that archetype.
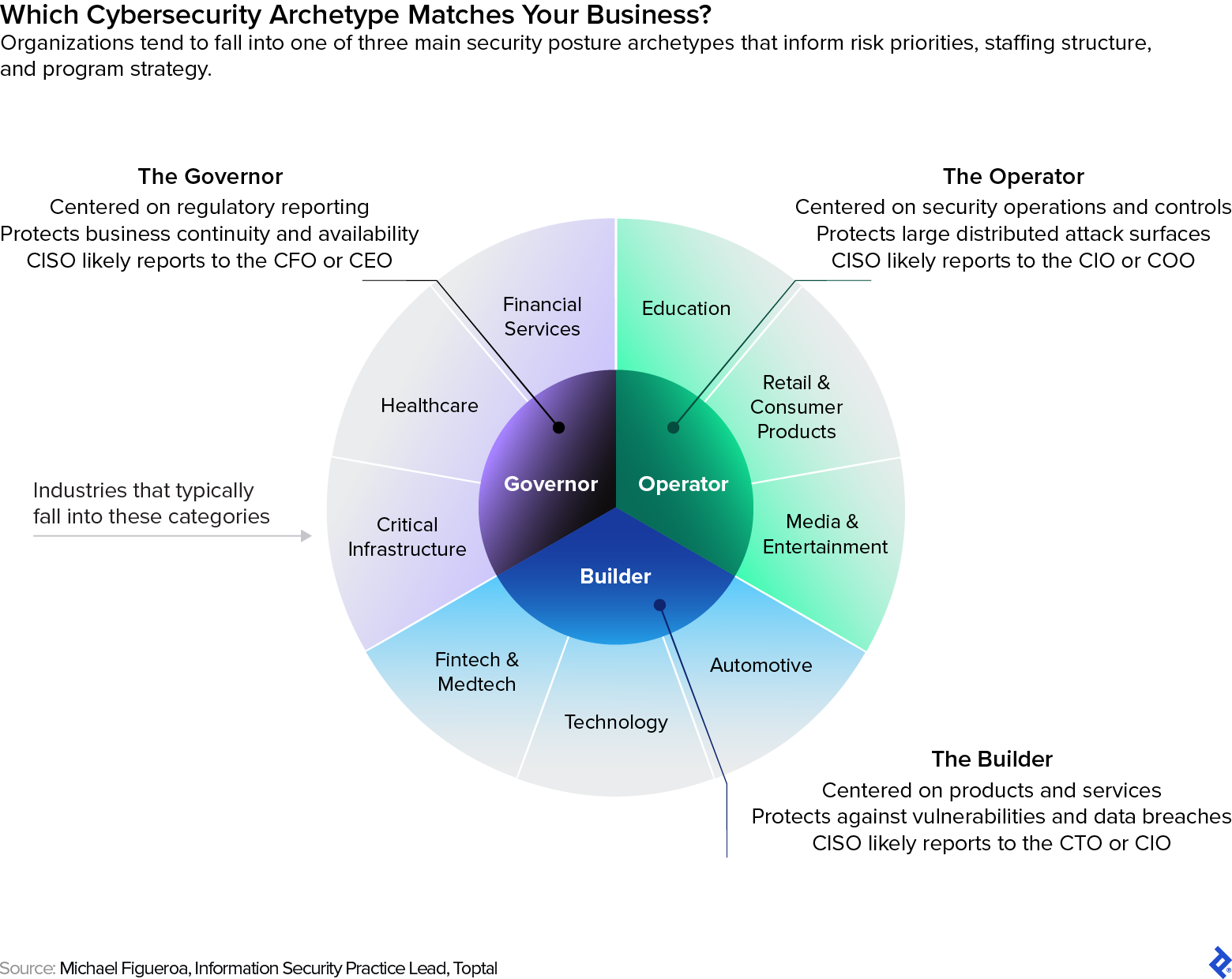
Throughout my 27 years as a safety skilled, and in my function because the Data Safety Follow Lead at Toptal, I’ve discovered that the majority organizations fall into one in every of three safety archetypes:
-
The Operator: Most likely probably the most dominant kind, this character describes metrics-driven organizations which can be most involved about deploying efficient safety operations middle (SOC) capabilities and monitoring how safety controls are carried out, managed, and maintained for effectiveness.
- Operators are usually bigger organizations with loads of shifting elements and huge management groups that distribute threat administration accountability and act on efficiency dashboards to evaluate business-aligned safety dangers and report on mitigation actions.
- A CISO in this kind of group could report on to the CEO (particularly in crucial infrastructure domains), however is extra prone to report back to the COO or chief data officer (CIO).
-
The Builder: Organizations that construct merchandise, run on-line functions, and supply managed providers are inclined to focus most on product safety administration.
- Builders are most involved with growing tightly coupled safety capabilities, sustaining a steady view of how safety controls have to adapt to a altering menace panorama, and mitigating potential exploitation of weaknesses by way of proactive vulnerability evaluation and workforce upskilling.
- In organizations of this sort, the CISO normally stories to the chief expertise officer (CTO) or CIO.
-
The Governor: Banks, healthcare firms, and different organizations that function beneath stringent regulatory oversight should focus most of their consideration on safety governance, threat, and compliance (GRC) efforts to construction and formalize enterprise processes for responding to impartial authorities.
- Governor organizations’ success depends upon monitoring the organizational adherence to safety insurance policies, assessing how enterprise and monetary dangers are impacted by potential and realized safety incidents, and growing common formal stories to particular authorities.
- In a majority of these organizations, the CISO normally stories to the chief monetary officer (CFO) or CEO with sturdy board-level visibility.
Regardless of their background or expertise, a CISO has a greater probability of succeeding in the event that they perceive their group’s character, after which construct a program to match that character by aligning on threat posture, constructing an archetype-appropriate crew, and fascinating strategic third social gathering companions.
Toptal Case Examine
One current shopper I labored with was a expertise firm that serves prospects in a extremely regulated {industry}. As such, their new CISO constructed a program aligned with a Governor safety character, centered on GRC. Whereas that safety posture matched this firm’s prospects, it didn’t match the corporate itself. And, regardless of a formidable background and a strong safety plan, conflicts arose which resulted within the CISO’s exit (and a protracted, six-month seek for a substitute). I helped the corporate leaders understand that, as a substitute of hiring one other GRC-focused CISO, they wanted to supply somebody who was in a position to align with the true Builder archetype of their very own group—somebody who would develop safety packages and react to threat priorities that higher supported their enterprise.
Precedence 1: Align With the Group’s Danger Posture
It’s straightforward for a CISO to tug out an industry-standard safety framework like ISO 27001 or NIST Cybersecurity Framework and measure the maturity of a company’s safety program towards every safety management. Certainly, addressing each management is essential for sustaining a wholesome and sound data safety program. Nevertheless, conducting such an train with out accounting for the group’s threat urge for food threatens pointless friction between the safety program and enterprise leaders.
A extra useful train is to evaluate a given customary framework’s elements towards the group’s safety character to find out which controls are most essential, and which fall too far exterior of acknowledged enterprise dangers to warrant vital funding. That organizational context will finally present a constructive basis for constructing consensus round safety wants.
For instance, in a earlier function the place I managed superior expertise growth for a government-funded analysis laboratory, I needed to allow a cloud-based collaborative work surroundings accessible to each our inner scientists and a world cohort of lecturers. That Builder-aligned want was, on its face, a direct violation of the strict governance posture that a company closely concerned in nationwide protection would seemingly should tackle.
Relatively than try and implement strict safety governance controls that may constrain our engagement with international collaborators, the CISO and I established a segmented infrastructure surroundings that may help the operational wants of the venture whereas compensating for the misplaced safety controls in different Governor-aligned methods. Doing in any other case would have merely pushed the crew to bypass the governance regime completely and defeat completely vital protections.
On this occasion, the CISO and I—a former CISO myself—had been in a position to collaborate and give you an answer. Too typically, nevertheless, CISO’s are considerably on their very own, with out equally educated counterparts in a position to assist them see the large image. In these cases, an impartial safety program design strategist may help establish potential factors of friction and options to these blockers.
Precedence 2: Nurture an Archetype-aligned Safety Group
An efficient safety government should take into account their group’s safety character to optimally align staffing sources to crucial enterprise wants. To do that effectively, they need to typically first overcome their very own experience biases. For instance, in my expertise, firms are inclined to prioritize hiring candidates with direct {industry} expertise over these with experiential potential and archetype alignment. Although direct expertise could definitely be worthwhile, artificially limiting the expertise pool can even reinforce inefficient industry-wide legacy practices and forestall the introduction of useful personality-aligned cross-industry improvements.
Toptal Case Examine
When one world industrial merchandise producer got here to me struggling to establish safety analysts to assist handle a compliance train, I famous that they had been focusing an excessive amount of on expertise, and ignoring their cybersecurity character. As a result of industrial producers typically face stiff regulatory pressures, the corporate was looking for safety GRC professionals. However the firm itself was extra carefully aligned with the Builder character, so I urged a change in technique. The corporate started on the lookout for analysts within the product growth area and rapidly engaged with an government product safety analyst who had a formidable healthtech background. That impartial skilled turned a trusted advisor to the shopper, taking up the coordination of a number of compliance efforts in only a matter of some months.
Precedence 3: Interact With Strategic Third-party Companions
Working in a dynamic menace surroundings with persistently evolving adversaries, safety executives by no means have sufficient price range to guard towards each conceivable assault vector. Equally, they by no means have the sources to totally cowl all the safety controls wanted to defend their firms from assault.
To be best of their use of restricted sources, CISOs ought to construct their crew construction round a agency’s highest safety priorities, and leverage third events and on-demand specialists to handle the remainder.
Other than managed safety providers suppliers who provide normal safety operations help, there’s a pure stigma towards utilizing third events for cybersecurity useful resource wants. Arguments range, however it’s typical for my purchasers to spotlight issues about exterior entry to delicate property, information safety wants, and malicious menace actors posing as contractors. Whereas these are all respectable issues for contract professionals and help personnel, these points are pretty easy to handle by way of widespread controls, akin to offering managed endpoint gear and conducting background checks. Partnering with a 3rd social gathering with a demonstrated world capability to completely vet specialists for identification, background, and expertise can present further assurance.
Even within the best-resourced enterprises, it makes little sense to rent full-time super-specialized staff for fractional wants. However a legacy mindset that facilities cybersecurity protection on inner hires bolstered by an amenable price range makes such an unproductive follow widespread. Nevertheless, for the overwhelming majority of organizations that function with very lean budgets, CISOs can adapt to altering wants in a extra agile style by using third-party sources to enhance decrease precedence areas.
Having a accomplice accessible with the experience to assist map out a resourcing technique that takes benefit of up to date resourcing instruments can imply the distinction between ignoring unacceptable dangers and managing complete cyberdefense capabilities.
Optimum Safety By means of Archetype Alignment
Whereas it could be true that many CISOs advance up the company ladder from technical backgrounds, as I did, safety professionals can come from a variety of instructional {and professional} paths. What they typically have in widespread, nevertheless, is a persistent curiosity about how issues work, an inherent sense of empathy, and a unprecedented affinity for disaster administration.
Data safety professionals function beneath persistent and unyielding adversity, with menace actors consistently probing and experimenting with completely different techniques to seek out only one unprotected point-of-entry. There could also be no absolute safety, however failure doesn’t should be a given. Exploitable weaknesses are sometimes much less about incompetence than a defensive failure of creativeness in an uneven battlefield the place the attackers vastly outnumber the defenders.
By aligning a safety program with a company’s safety character, safety executives can extra successfully prioritize their defensive consideration, handle enterprise dangers, construct buy-in throughout the management crew, and instill a stronger tradition of safety. Perhaps then, these three envelopes we talked about can stay safely unopened and forgotten.
Have a query for Michael or his Data Safety crew? Get in contact.

-5c93a8cc1d2a5f4b917f20dae517e2dc.png)