
In 2021, IP PBX hacking has brought on $1.82 billion in fraud losses, a 28% enhance from 2019. When threats grow to be unpredictable and the remote-work-related dangers ever enhance, safety is essential. VoIP hacking and assaults can come from the Web or phone traces concentrating on exploiting any vulnerabilities and ultimately exposing your group to toll fraud and theft of confidential data.
So how will you shield your business-crucial PBX system from potential internet threats and inside malfeasance?
This weblog introduces the must-have safety insurance policies and Yeastar PBX System’s revolutionary providers and options that successfully protect you from assaults.
Desk of Contents
6 Sorts of Frequent VoIP Vulnerabilities and Assaults
To keep away from safety breaches of your VoIP PBX telephone system, you will need to perceive the potential vulnerabilities and the frequent forms of cyberattacks.
Potential PBX Safety Vulnerabilities
- Weak or stolen usernames and passwords
- Again doorways and software vulnerabilities
- Poor entry management
- Unencrypted connections
- Information breach attributable to human error
Frequent Sorts of Cyberattacks and VoIP Safety Treats
1. Toll Fraud
- Assault Motion: Make worldwide calls out of your VoIP community, at your expense.
- Assault Function: Generate a excessive quantity of worldwide calls to premium price numbers after which accumulate the income.
2. Reconnaissance
- Assault Motion: Collect all attainable details about the goal earlier than launching an precise assault.
- Assault Function: Determine vulnerabilities and weaknesses, after which create a profitable exploit.
3. Denial-of-Service (DoS)
- Assault Motion: Flood a server with an amazing quantity of requests and deplete all of its bandwidth.
- Assault Function: Stop customers from accessing linked on-line providers or websites.
4. Spoofing
- Assault Motion: Impersonate a person or an organization that the victims belief.
- Assault Function: Acquire entry to private data or steal knowledge.
5. Man-in-the-Center
- Assault Motion: Snoop on the communication between two targets.
- Assault Function: Steal delicate knowledge, resembling login credentials, account particulars, and bank card numbers.
6. Spam Over Web Telephony (SPIT)
- Motion: Bulk and unsolicited robotic calls and voicemails over VoIP to telephones linked to the Web.
- Function: Trick the sufferer into answering or listening to a robocall for top worldwide calling charges.
VoIP Safety Guidelines: Tips on how to Safe Your VoIP Cellphone System
The complexity and number of cyberattacks are ever-increasing, with various kinds of assaults for various malicious functions. Whereas countermeasures differ for every kind of assault, good safety insurance policies assist mitigate the dangers. In lots of instances, the easiest way to safeguard a PBX telephone system is to implement a multi-layered safety answer. Because of this it is advisable to deploy a number of protection measures to guard the weak factors of your telephone system. Every layer will increase general safety and continues to supply system protection even when one of many layers is breached.
Following are some finest practices that may be carried out to construct multi-layered safety in your VoIP telephone system.
1. Preserve Your PBX and SIP Endpoints Up to date
An up-to-date firmware or software program model works like a protecting cowl to protect your PBX or SIP endpoints from safety threats. Sometimes, the latest model is usually essentially the most safe with bugs and different vulnerabilities being discovered and stuck. As well as, with expertise evolving, some crucial safety features or layers of safety are solely supported on the newest model.
2. Defend Towards Community Safety Threats
Your group’s community is the primary line of protection towards cybercrime. If a hacker positive aspects entry to your group’s community that helps VoIP communications, it may end up in Denial of Service (DoS) assaults or important decreases in High quality of Service (QoS). To forestall this from occurring, it is advisable to keep away from exposing the PBX’s intranet to the general public and block unauthorized entry.
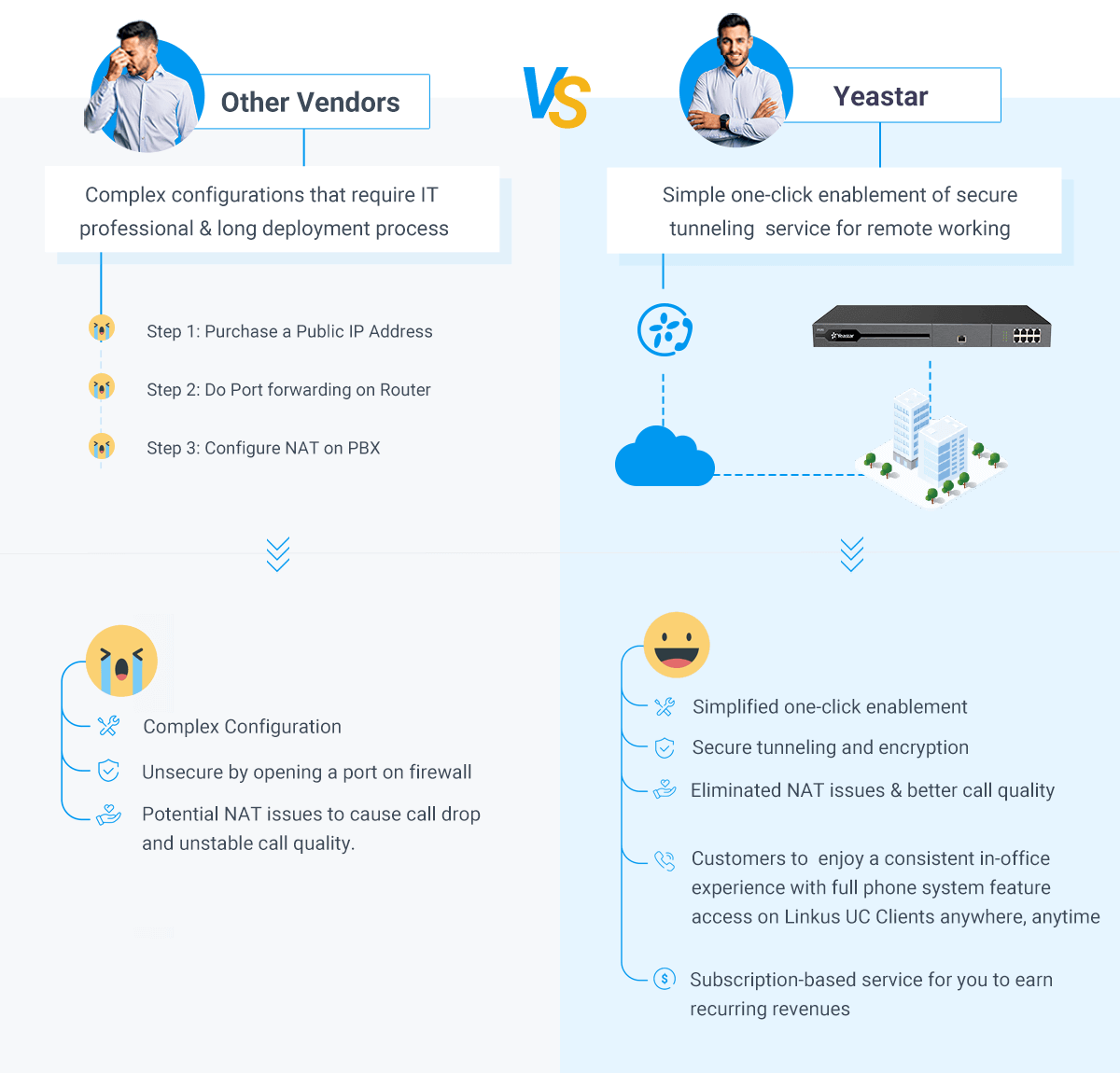
Keep away from Port Forwarding
In an try to supply distant entry for distant and cell customers, most on-premises PBX suppliers will advocate Port Forwarding. However this isn’t a good suggestion in any respect.
Primarily, Port Forwarding maps an exterior port in your public IP handle to the PBX that’s inside your non-public Native Space Community (LAN). This exposes your PBX on the Web and brings potential dangers as a result of hackers may penetrate your community by way of the forwarded port. And as a matter of reality, hacking by way of port forwarding has been the most typical method for hackers to launch assaults.
You will have a safer option to keep distant entry for wanted options and in the mean time, keep away from utilizing port forwarding that exposes your LAN.
To resolve the dilemma, you would possibly leverage tunneling providers like Yeastar Linkus Cloud Service Professional (LCS Professional) or Distant Entry Service (RAS). Coming filled with industrial-grade cloud and encryption expertise, the Yeastar tunneling service creates a securer method for PBX’s distant SIP entry and enterprise communications. It not solely avoids the PBX port forwarding however double-secures the system with granular permission management. You’ll be able to determine which IP addresses and Extension accounts are allowed to entry your PBX remotely through the service, and what PBX providers are allowed for distant entry.
Block Unauthorized Entry to Your PBX
Block undesirable and unauthorized entry to your PBX can considerably lower the potential of your system being hacked. It’s a very important step to forestall phone hacking and mitigate the potential injury and monetary losses to your small business.
a. Limit entry to PBX Administrator Portal
Yeastar P-Collection PBX System is preconfigured with 3 forms of role-based accounts: Tremendous Admin, Administrator, and Customized Person. Every function has acceptable administrative privileges already included. You may also create customized roles with particular administrative privileges to suit person wants. Solely customers with administrative privileges can entry the administrator portal to configure the system options which can be granted to their roles.
When implementing role-based entry management, you grant solely the mandatory privileges to person roles and be certain that roles are given to the proper particular person, thus regulating who and what for the safety permission management.
b. Limit system entry from particular international locations or areas
For those who discover a rise in assaults in your PBX from a selected nation or area, you need to use geographic restrictions (often known as geo-blocking) to forestall guests in particular geographic places from accessing the PBX. By checking a customer’s IP handle towards the PBX’s database, unauthorized entry may be denied.
c. Limit system entry with firewall guidelines
Yeastar P-Collection PBX System has inbuilt firewall guidelines to solely settle for trusted visitors. You may also create firewall guidelines in your PBX to permit or block visitors from particular supply IP handle/area, ports, and MAC addresses. In doing so, suspicious entry that may contribute to assault fraud or name loss can be mechanically blocked.
To forestall large connection makes an attempt or brute drive assaults, you may also make the most of the PBX’s inbuilt IP-Auto-Protection function to outline the allowed variety of IP packets inside a particular time interval. If any IP sends IP packets exceeding the restrict, the system will mechanically block the IP.
3. Mitigate SIP Communications Dangers
SIP trunk is usually used for the transport of voice packets out of your group to the supposed recipient. Any interference may end up in degraded name high quality, full disconnecting of a name, eavesdropping, and many others. To safe SIP trunks, the easiest way is to restrict outbound calls and encrypt calls.
Set Guidelines for Outbound Calls
a. Completely different guidelines for various time durations
Hacking makes an attempt are often made throughout non-business hours, over weekends, and through vacation durations when the system is much less attended. You’ll be able to leverage the Time Situation function to implement completely different inbound or outbound name restriction guidelines for various time durations to bolster the automated management. For instance, you would possibly create a Time Situation referred to as “Holidays”, and disable outbound calls throughout holidays by making use of the Time Situation to an outbound route.
b. Permission to solely those that want it
Your staff carry out completely different duties in your organization, and never all of them must make long-distance or worldwide calls. Take into account configuring completely different outbound routes for various trunks (e.g. native, long-distance, and worldwide), and assign outbound route permissions solely to the customers who require using it.
c. Restrict outbound name frequency
As soon as hackers infiltrate your telephone system, they’ll simply rack up tens of hundreds of {dollars} by making a big quantity of calls. It’s really useful that you simply set a restrict on the variety of outbound calls that may be made inside a preset time interval.
d. Restrict name credit score and cancel auto refill
Telecom suppliers shield clients from exorbitant name prices by inserting an higher threshold on the variety of billable calls that an organization can incur. Limiting the quantity of credit score and canceling auto-refill will assist decrease the losses attributable to toll fraud.
Encrypt Calls
Encrypting your communications can stop eavesdropping or tampering with audio streams between all endpoints.
a. Use TLS to encrypt signaling
Transport Layer Safety (TLS) is a safety layer within the type of a certificates that needs to be authenticated earlier than entry is granted. With TLS enabled, your customers’ names and telephone numbers are hidden and unable to be retrieved by prying eyes and ears.
b. Use SRTP to encrypt media
To strengthen the safety, TLS must be used along with SRTP in your telephone system. These guarantee SIP signaling and audio/video classes secure from any malicious actions.
4. Harden SIP Extensions
When unauthorized entry is gained to SIP extensions, the potential for disruption is especially important. Criminals can exploit your telephone system to make calls and launch different malicious assaults. Implementing a robust password coverage and inserting restrictions on extension registration will assist safe SIP extensions.
Use Sturdy Passwords
A weak password can go away a possible safety hole that hackers can simply exploit. To that finish, robust passwords must be used for each required function in your PBX. On the whole, Yeastar PBX has passwords for extension registrations, the administration internet interface, person internet interfaces, and voicemails. You’ll be able to shield the password within the following methods:
-
- Keep away from the most typical or system default passwords.
- Use a robust password of at the very least 8 characters, together with a mixture of higher case, decrease case, and digits.
- Use completely different passwords for various accounts.
Limit Extension Registration
Yeastar PBX System has robust anti-hacking mechanisms to safeguard SIP registration safety, resembling limiting extension registration to LAN solely and blocking IP addresses for too many failed registration makes an attempt. Furthermore, you might be given the next choices to strengthen the safety:
-
- Limit the IP addresses from which extensions can register.
- Configure a fancy authentication identify utterly completely different from the overall default username.
- Place a restriction based mostly on a telephone’s person agent.
5. Make Contingency Plans
Although a variety of measures may be taken to guard your PBX, there isn’t a absolute security. If an attacker efficiently infiltrated your PBX or compelled your PBX to fail, it is best to have a contingency plan.
Set up Actual-time Monitoring, Logging, and Alert on System Occasions
Leverage occasion logging to observe and document the anomalous operations in your PBX, and subscribe to the crucial occasions. When one thing goes incorrect, you may get notifications well timed and shortly discover out the place the issue lies and work out an answer.
If you’re utilizing a Yeastar PBX system, you possibly can notice the real-time monitoring on the next two platforms:
-
- PBX Administrator Portal: handle a single PBX.
- Yeastar Distant Administration: centrally monitor and handle quite a few customer-premises PBXs.
Schedule Auto Backup
-
- Schedule common backups. In case your PBX can not work, you possibly can reset it and restore configurations from the backup file to make sure a quick restoration.
- Retailer backups in exterior places to forestall the chance of information loss from bodily destruction or theft.
- Apply a backup retention coverage. This helps restrict the quantity of historic and outdated knowledge.
Implement a Redundancy Answer
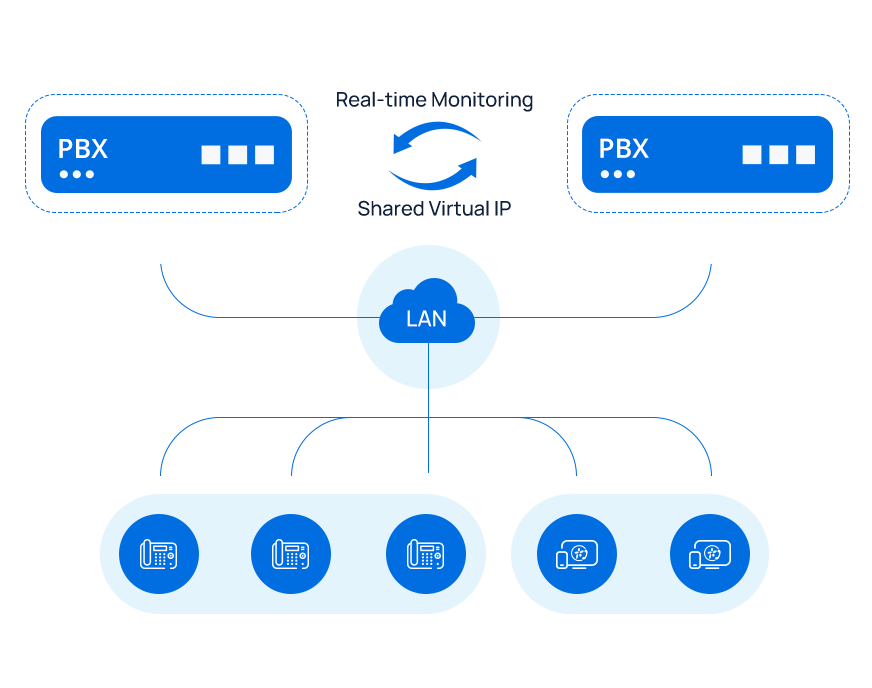
a. Scorching Standby for on-premises PBX System ({Hardware} & Software program-based)
Yeastar on-premises PBX system is provided with the Scorching Standby function without cost, which lets you create a mirroring server pair and get well instantly when a failure happens. To deploy the answer, you want two equivalent PBX servers, which must be the identical within the following facets: Product mannequin, Firmware and {hardware} model, Software program configuration, Native Space Community (LAN) Settings, and {Hardware} Installment.
With Scorching Standby arrange, the next may be achieved:
-
- Quick 1 to 10 seconds automated restoration in occasion of any failure.
- Shared digital IP between the paired energetic and hot-standby PBX servers, which ensures a whole system swap to the standby server when the energetic server fails, together with all IP telephones and third-party integrations linked to the PBX.
- Prompt electronic mail notification through electronic mail or name when a failover occasion happens
b. Excessive Availablity for Cloud PBX
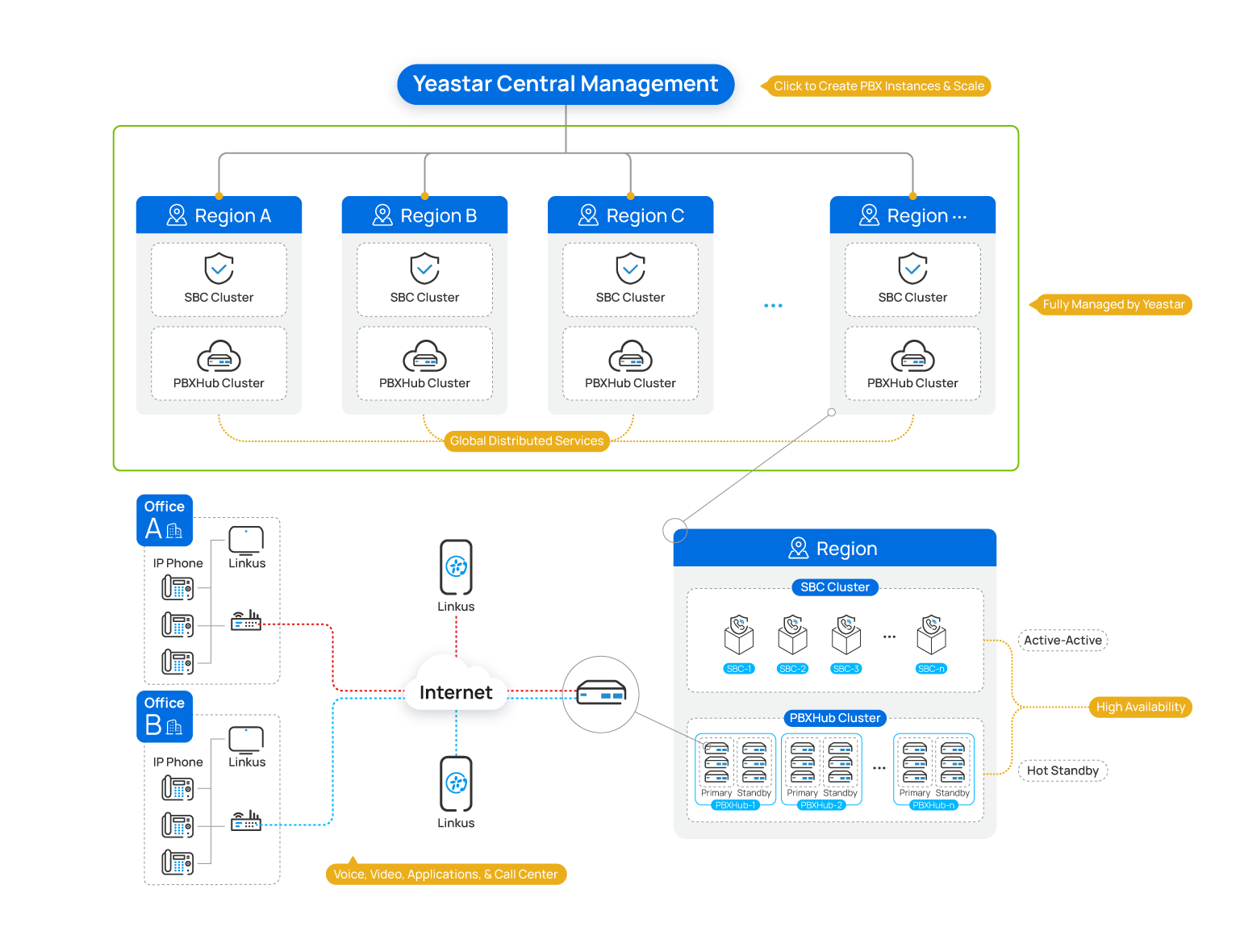
Reliability will not be a function of the cloud; it’s a requirement. Delivered in a cluster-based atmosphere and managed by Yeastar, Yeastar Cloud PBX providers function a high-availability redundant deployment for enhanced catastrophe restoration, which isn’t the case for a lot of single-instance cloud deployments.
PBX situations are deployed as major and secondary pairs, i.e. the new standby mode, to assist seamless failover. We additionally leverage energetic/energetic load balancing to make sure optimum useful resource utilization amongst SBC servers. These servers are all powered by Amazon Net Companies and positioned in varied areas throughout the globe, including extra resilience to your complete service. There are extra built-in safety mechanisms in place to safeguard towards malicious assaults.
Yeastar Safety Options for PBX Distant Entry & Communications
PBX suppliers can by no means be too cautious with VoIP safety. That is very true in the case of the system’s distant entry. Tips on how to perceive distant entry?
For one factor, clients might request the flexibility to entry their telephone methods remotely through the Web. Such distant connections are handy and infrequently mandatory for frequent vacationers, in addition to for geographically dispersed places or staff.
For an additional factor, PBX suppliers might have to ascertain a distant connection to offer distant PBX tech assist, troubleshoot community issues, and resolve points with out the necessity to ship a technician on website.
As is thought, on-premises methods are sometimes restricted to the bodily workplace. Historically, to remotely entry on-premises methods, PBX suppliers must undergo difficult PBX server and community settings, which could incur potential safety dangers.
Yeastar was on the lookout for the most effective answer to assist on-prem and software program PBX customers safe their distant entry and ease by way of the configurations, and we made it. By means of the revolutionary Yeastar tunneling providers and Yeastar Distant Administration device, the distant connection is just one click on away with the least IT and safety issues.
1. For PBX Finish Customers
Safe Tunneling Companies for Distant Enterprise Communications & Collaboration
In an try to supply distant entry for distant and cell customers, most on-premises PBX suppliers will advocate Port Forwarding. However this isn’t a good suggestion in any respect. Port Forwarding requires difficult server and community settings. Worse but, it dangers potential assaults by opening a port on the firewall, by way of which risk actors can simply get full management of the telephone system.
Yeastar supplies revolutionary tunneling service for Yeastar on-premises and Software program PBX, liberating you from dangerous port forwarding, difficult server setup, and troublesome NAT points, so that you don’t want to fret about exposing your intranet to the general public, losing time on advanced deployment, or unstable name high quality to occur and have an effect on your distant enterprise communications. And the most effective a part of that, it takes just one click on so that you can get pleasure from hassle-free and safe distant communications.
The revolutionary tunneling service is known as in another way on completely different Yeastar PBX sequence
-
- Linkus Cloud Service Professional (LCS Professional) for S-Collection VoIP PBX
- Distant Entry Service (RAS) for P-Collection PBX System.
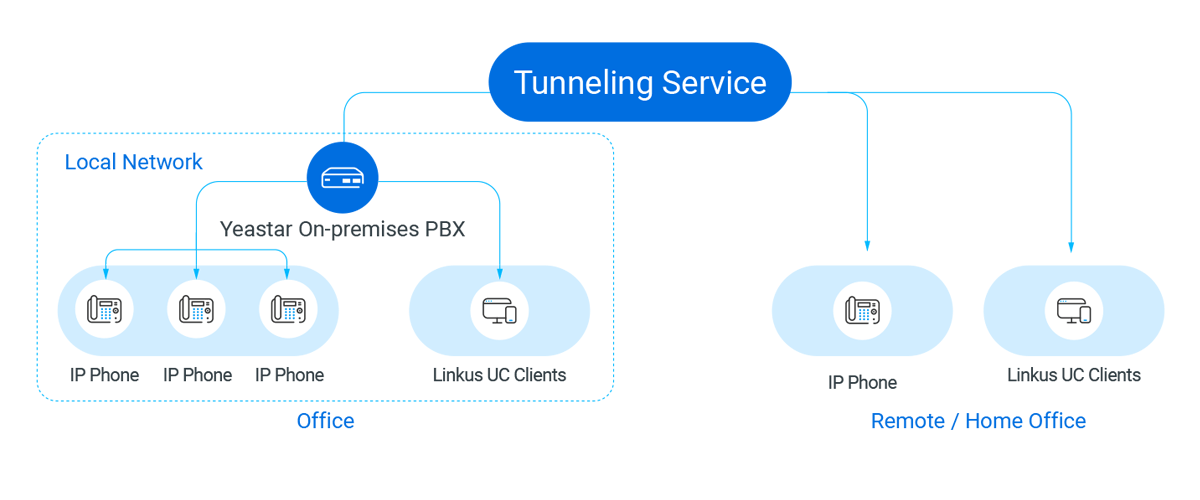
- How safe is the answer?
a. Separate and Non-public Connection
Defend your organization from the potential dangers of PBX community penetration and subsequent problems with toll fraud, knowledge breaches, and cyber-attacks alike. Yeastar tunneling service supplies a tunneling server as an middleman server for knowledge transmission between the PBX and its distant SIP endpoints. Your PBX’s IP handle received’t be uncovered to the general public. All distant connections are direct, undercover, and double safeguarded with account authentication.
b. Unbreakable and Impenetrable Encryption
All transmission between the PBX and the tunneling server is encrypted. And every PBX may have its unique encryption key. Even when the tunneling server is introduced down by a hacker, it is extremely troublesome to switch the tunneling service and get the unique transmission knowledge for the reason that knowledge is encrypted.
c. Per-service Distant Entry Authorization
Yeastar tunneling service affords superior entry management to make sure additional safety. You’ll be able to allow or block distant entry for internet entry, Linkus entry, SIP registrations, LDAP, and API, customise distant entry authorization by extension or division, and apply IP restrictions to additional safe all of the distant entry.
2. For PBX Resellers, MSPs, and Suppliers alike
Machine Distant Monitoring and Administration
In relation to distant assist, most PBX suppliers will advocate both putting in distant desktop software program (e.g. AnyDesk and TeamViewer) on computer systems or doing Port Forwarding for the PBX, however each strategies go away a port open, which may very well be simply exploited by hackers. What’s extra, weak distant connections could make it simple for cybercriminals to interrupt into the session and achieve entry to the shopper’s pc or telephone system.
Delivered through the all-encompassing platform of Yeastar Central Administration, Yeastar Distant Administration permits Yeastar Companions to remotely handle and configure customer-premises Yeastar PBX methods and VoIP gateways in a safe method.
With no Port Forwarding or VPN required, it affords encrypted machine distant connection, round the clock distant system monitoring and alerts, and most significantly, permission-based distant system configurations. When a problem is detected on the shoppers’ units, you obtain notifications instantly and might take immediate actions with out sacrificing system safety.
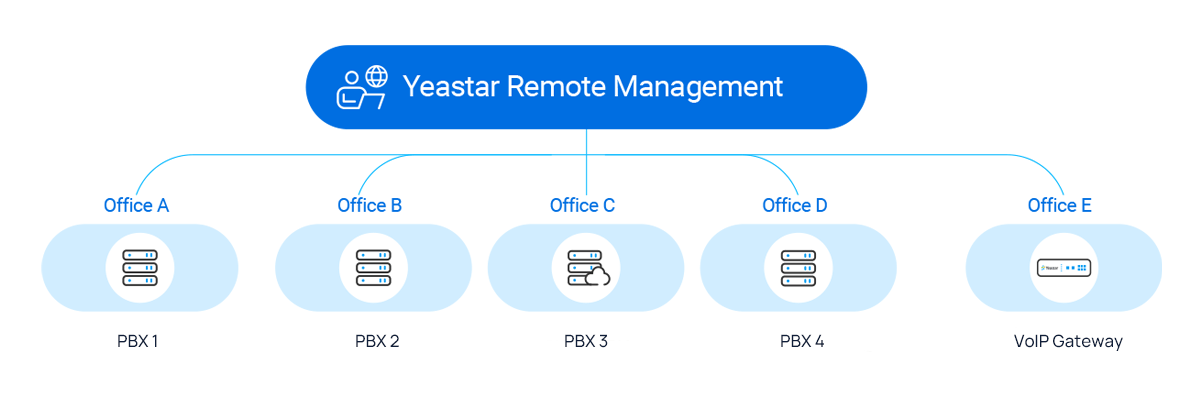
- How safe is the answer?
a. Financial institution-grade Distant Connection
All distant connections are HTTPS secured and performed in an encrypted SSH tunnel to reduce community publicity and finest shield the info integrity and confidentiality.
b. 2-way Connection Authentication
Join distant Yeastar units both by confirming Yeastar ID on the shopper’s machine or by verifying the once-off distant connection authentication code on the shopper’s machine. Each authentication strategies require affirmation from the shopper, successfully retaining the Yeastar units from being maliciously linked and knowledge breaches.
c. Function-based Entry Management
Add colleague accounts to co-manage clients’ units. By limiting account permissions, you possibly can notice granular administration and be certain that entry to distant Yeastar units is restricted to approved engineers just for upkeep operations.
d. Distant Entry Timeout Mechanism
Yeastar Distant Administration supplies a sturdy timeout mechanism to restrict the time of each distant Yeastar machine configuration, which signifies that after the configured time, the URL supplied to entry the distant Yeastar machine will grow to be invalid and the entry can be terminated.
Safe Your VoIP Communications from Right this moment
Organizations that safe voice visitors are extra resilient than those who sit idle. A good PBX System like Yeastar may be the reassurance it is advisable to keep a safe calling atmosphere.
With over 15 years of experience within the VoIP {industry}, Yeastar has been engineering VoIP PBX telephone methods with the precise performance, flexibility, and safety that trendy companies will want for his or her development. Whether or not you want a Cloud PBX System or a {hardware}/software-based telephone system, you possibly can belief us with the industry-leading services. Contact us for an inquiry at present.



