In at present’s computing atmosphere, firmware can imply a number of issues, starting from a whole working system in embedded gadgets to a small flash program in a {hardware} part that tells your working system (OS) about that {hardware}’s capabilities. On this weblog publish, we are going to deal with the vulnerabilities within the latter sort of firmware popularized by the Uniform Extensible Firmware Interface (UEFI). I’ll discover how these vulnerabilities are a profitable goal for high-profile attackers, akin to nation-states which are searching for vulnerabilities within the less-visible parts of at present’s computing atmosphere.
First, to get our footing, it is very important perceive what UEFI actually is. UEFI replaces the legacy Primary Enter/Output System (BIOS), interfacing {hardware} to the OS and gives an extensible intersection between {hardware} and the OS itself. The UEFI customary additionally identifies dependable methods to replace this firmware from the OS. In essence, in at present’s computer systems, there may be one other layer of software program that may assist the OS perceive and use accessible {hardware}. After all, this important layer of software program faces all of the challenges of at present’s software program: bugs, safety points, patching, and upkeep. It additionally lacks visibility, making it arduous for defenders to guard this a part of their computing environments from ever-increasing threats.
Moods of your CPU: Actual, Protected, and System Administration
The Intel CPU structure defines a number of modes through which the CPU operates to interpret, execute, and fulfill the duties requested by the OS. In most fashionable working programs, protected mode gives for safe operations of duties with capabilities, akin to reminiscence isolation between processes. Intel additionally gives a system administration mode (SMM), which is a extremely privileged mode of operation accessible to the OS by way of the particular System Administration Interrupt (SMI) handler. SMM is the first mode through which UEFI operates to interface instantly with the {hardware}. Usually, a single grasp SMI handler will enable for registration and administration of different SMI handlers, that are all recognized by their globally distinctive identifiers (GUIDs).
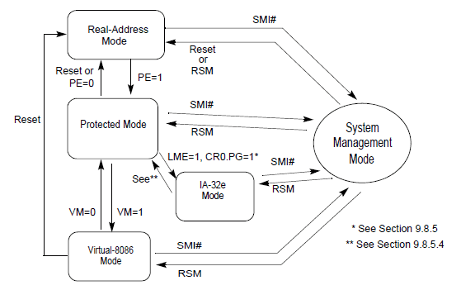
Determine 1: Picture from Intel’s CPU guide
What Can Be Smaller than 0? Effectively –2 Possibly?
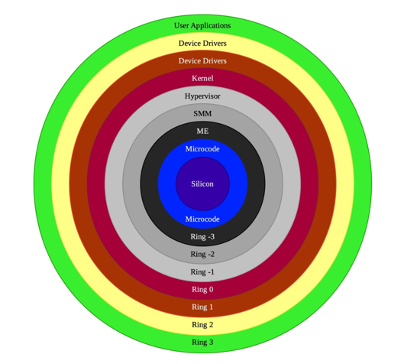
In laptop science, safety rings are used to establish varied ranges of privileged entry to assets in your laptop. Ring 0 is often thought of to be the best degree of entry accessible to a system-level consumer of an OS. Nonetheless, hidden rings (Ring –1 for hypervisor and Ring –2 for SMM) are basically required to carry out duties with privileges better than the OS itself. These embody duties akin to configuring or modifying the configuration of the {hardware} or including new software-based capabilities to an already current {hardware} machine.
In sure circumstances, there are additionally issues, akin to UEFI variables, that present vital knowledge used all through the OS boot course of. The UEFI customary spells out specs for SMI handlers, that are principally software program written to realize system calls to request the CPU to carry out duties within the excessive privilege mode referred to as SMM. Vulnerabilities exist each within the programming of the SMI handler and in correctly defining (and defending) UEFI variables. These actors who can exploit these vulnerabilities are supplied with a excessive privilege mode to execute their code on a focused laptop.
Software program Means Vulnerabilities
As UEFI capabilities are developed, increasingly more functionality is delegated to the UEFI software program to permit it to change, customise, and in some circumstances, improve at the moment accessible {hardware} capabilities of a pc. Most of this software program is written in lower-level languages (principally C) that require cautious use of assets, akin to reminiscence. All of the operations in SMM are saved in a protected space of reminiscence referred to as SMRAM, which is remoted from the working system. The communications initiated by the SMI handlers are abstracted utilizing a communications buffer dubbed CommBuffer. SMRAM additionally has particular code segments (non-writeable) and knowledge segments (non-executable), that are all invoked from the OS utilizing a CommBuffer.
Right this moment, software program anticipated to run with SMM’s privileged mode is supplied by a number of distributors and finally ends up being assembled by an OEM PC vendor earlier than a pc is bought out there. Nearly all of this software program is derived from the instance community-developed mission referred to as Tianocore that gives software program growth kits (SDK) referred to as EDKII for constructing these UEFI modules. EDKII is instance code that requires cautious safety overview, particularly of reminiscence administration, earlier than being carried out for particular use circumstances. Many well-known C coding errors (e.g., unsafe pointers, correct pointer validation, sort confusion, and improper locking) will be simply launched whereas creating UEFI software program. These defects lead the software program to reveal SMRAM contents, corrupt the SMRAM payload, hijack the SMM code circulate, and at last, allow the writing arbitrary code/content material to the Serial Peripheral Interface (SPI) Flash. As a mixed impact, these errors give the attacker a strong approach to write everlasting code on the machine in a most obscure location.
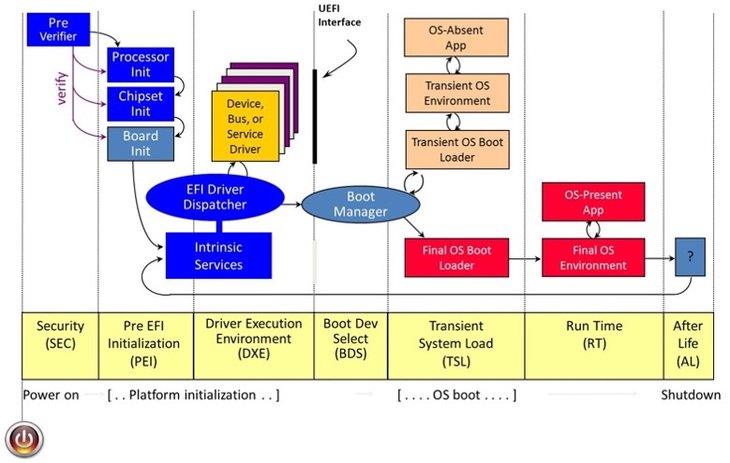
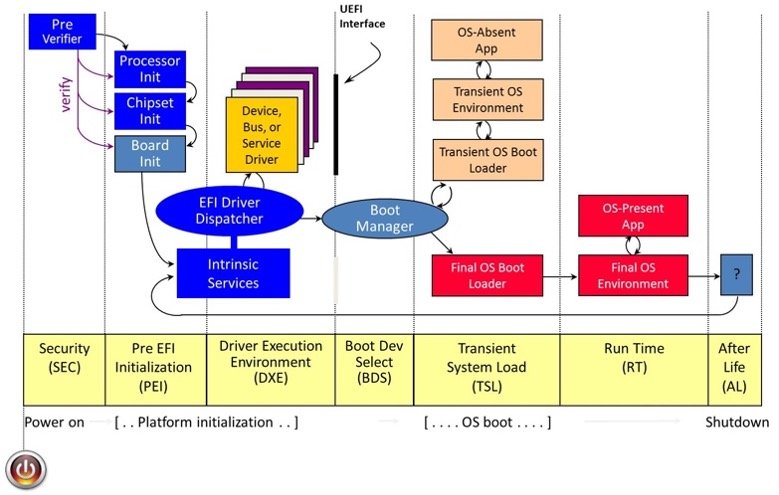
The platform-initialization part diagram from the EDKII Construct Specification repository gives some detailed info on how a contemporary laptop goes by its boot course of. UEFI gives immense capabilities to provoke, configure, and customise the best way through which {hardware} might be used when the pc is working in regular situations. This highly effective functionality is now being explored by each safety researchers and attackers.
For instance, researchers Assaf Carlsbad and Ittai Liba from Sentinnel One disclosed the power to interrupt safe boot to compromise one of many earliest phases of platform initialization. The researchers demonstrated the exploitation of a number of weaknesses ranging from a scarcity of validation of SMRAM contents on account of nested tips to overwrite the secure-boot configuration. In one other current disclosure, researcher Alex Matrsov from Binarly disclosed a lot of SMI handlers that primarily enable privilege escalation within the Drive eXecution Atmosphere (DXE) part that may result in arbitrary code execution in excessive SMM privilege mode of the CPU. These assaults may also be initiated as your laptop is reawakened from sleep mode. The systemic errors mentioned above make every part within the boot course of weak to assault.
Why Assault the SMM?
Ought to we be involved about these vulnerabilities? Do attackers actually need to undergo 1000’s of UEFI implementations to seek out vulnerabilities? SPI Flash communications may be very sluggish in comparison with at present’s widespread assaults, which goal reminiscence and disk as areas for permanence or persistence. Will attackers goal such a sluggish SPI interface for assaults? Beneath are simply among the the explanation why attackers discover UEFI implementations to be a lovely goal for assaults:
- SMM because the excessive floor—SMM gives the attacker highest privilege mode of a CPU, nearly unguarded even by the working programs (Ring 0), hypervisor (Ring –1), and any safety software program together with endpoint detection and response (EDR) in at present’s computing environments.
- P is for persistence in APT—The attacker at present is on the lookout for persistence that can survive rebuilding of the working system. What higher place is accessible than the SPI flash? Principally the BIOS location. Lojax and Sednit, for instance, goal SPI flash for persistence.
- Invisibility—As proven by MoonBounce, an implant written as a UEFI firmware module can work in stealth leaving no hint for the OS or typically even the community.
- A damaged vulnerability lifecycle—Many firmware vulnerabilities both will not be addressed, or they reappear a number of years after discovery. Complicated provide chain and poor firmware replace cycles make UEFI firmware an excellent goal for attackers to think about when creating implants.
What Ought to We Do?
A number of efforts are already underway in analysis and business to enhance UEFI safety. Listed below are just a few efforts that we want to develop into concerned in.
- Greatest practices and higher instruments for UEFI growth—The EDKII specification and a pattern implementation have been very highly effective in onboarding a lot of small corporations for UEFI growth. Nonetheless, a lot of safe coding practices and audits are wanted to make sure that code is protected in opposition to typical abuse of reminiscence primitives in these low-level packages. Analysis and energy are wanted to safe the code by default limiting SMRAM abuse. There’s additionally a necessity for DevSecOps-like efforts to make sure that the firmware growth lifecycle is secured at its very starting.
- SBOM and transparency–—A lot of the UEFI growth and manufacturing of UEFI modules and firmware have been carried out privately by a number of distributors of the provision chain referred to as impartial BIOS distributors (IBV), impartial {hardware} distributors (IHVs), and authentic machine producers (ODMs). Nearly all of these software program modules are protected by proprietary storage and compression methods, which give very low visibility to clients and typically even to the OEMs that bundle and resell the software program. The UEFI firmware house wants a clear and accountable software program invoice of supplies (SBOM) with ample element to help accountable disclosure of parts and vulnerability administration of those parts.
- Instruments to research UEFI photos, modules, and capsules—Considerably associated to the sooner concern of transparency, a lot of the UEFI code is opaque and typically even obfuscated by their distributors. We subsequently want extra clear instruments to research and audit UEFI firmware developed both as a supply code or as binary static code analyzers to establish code circulate and potential abuse of meant UEFI standards-based communications and executions. Right this moment only some software program instruments, akin to Chipsec, enable the dumping of ROM EFI photos. Some reverse-engineering instruments, akin to Sentinel’s Brick and Binarly’s efiXplorer, exist to research UEFI software program modules. The shortage of such instruments limits the quantity of group evaluation and perception wanted to find and deal with safety considerations in UEFI software program.
- Well timed vulnerability lifecycle administration—UEFI firmware vulnerabilities discovery, accountable disclosure of those vulnerabilities, and well timed software program updates to deal with these vulnerabilities will all must be improved. Capabilities, akin to automated updates and capsule-based updates, needs to be commonplace to make sure that UEFI updates will not be cumbersome or complicated for the customers and customers of computing environments. Efforts, akin to Microsoft’s Firmware Replace Platform and Linux Vendor Firmware Service (LVFS) initiatives, try to resolve this by offering a safe approach to replace firmware capsules utilizing a standards-based strategy. LVFS particularly gives an open-source, clear approach to deal with this situation by lowering the burden of delivering the firmware updates on distributors. OEM distributors are urged to actively take part in such efforts to make sure well timed replace of vendor firmware modules.
Addressing Systemic Lessons of Vulnerabilities
On the SEI’s CERT Division, we see UEFI safety as intently associated to our analysis in addressing systemic courses of vulnerabilities. We want to associate and help your efforts by offering help for well timed disclosure, higher evaluation, and a swift response to vulnerabilities within the UEFI software program ecosystems. In case you are fascinated with working with us, please e-mail information@sei.cmu.edu.