
Studies this week illustrate how menace actors contemplate Microsoft Trade as a major goal for gaining preliminary entry to company networks to steal information and deploy ransomware.
CrowdStrike researchers reported this week that the Play ransomware operation utilized a new Microsoft Trade assault dubbed ‘OWASSRF’ that chained exploits for CVE-2022-41082 and CVE-2022-41080 to achieve preliminary entry to company networks.
The ransomware operation then used this entry to steal information and encrypt gadgets on the community.
As one other instance of Microsoft Trade being closely focused by menace actors, ProDaft revealed this week that the FIN7 hacking group created an auto-attack platform known as ‘Checkmarks’ that targets Microsoft Trade.
This platform mechanically scans for Trade servers, exploits vulnerabilities to achieve entry, after which downloads information from the server.
FIN7 would then consider the corporate to find out if it was worthwhile sufficient to deploy ransomware.
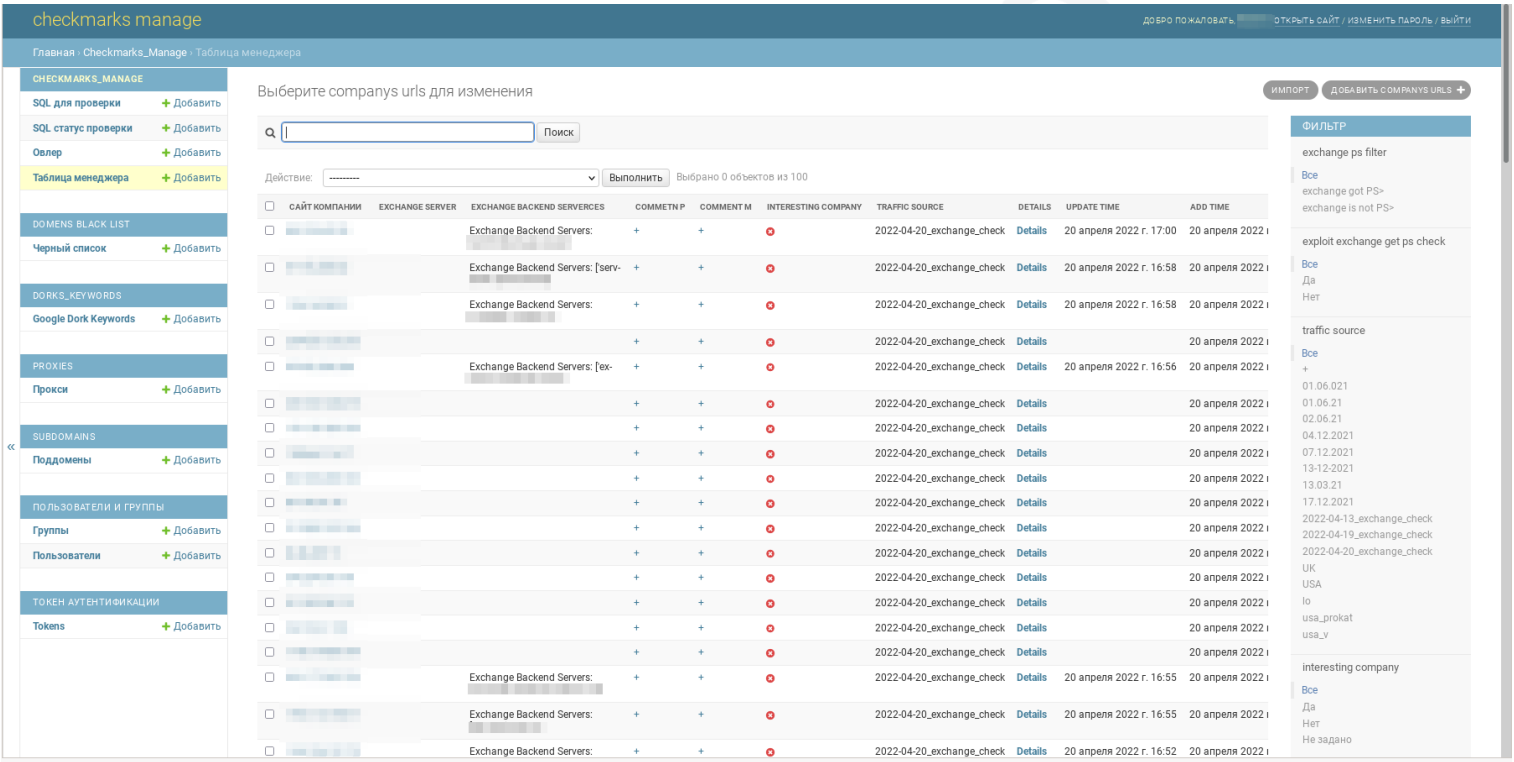
Supply: ProDaft
TrendMicro additionally confirmed this week our September report {that a} Conti cell generally known as Zeon rebranded to Royal Ransomware.
Different experiences this week make clear varied ransomware operations:
Contributors and those that offered new ransomware info and tales this week embody: @BleepinComputer, @FourOctets, @billtoulas, @DanielGallagher, @demonslay335, @struppigel, @jorntvdw, @LawrenceAbrams, @malwrhunterteam, @VK_Intel, @PolarToffee, @fwosar, @Ionut_Ilascu, @Seifreed, @malwareforme, @serghei, @IBMSecurity, @PRODAFT, @CrowdStrike, @LabsSentinel, @Fortinet, @zscaler, @TrendMicro, and @pcrisk.
December nineteenth 2022
Play ransomware claims assault on German lodge chain H-Accommodations
The Play ransomware gang has claimed accountability for a cyber assault on H-Accommodations (h-hotels.com) that has resulted in communication outages for the corporate.
How Reveton Ransomware-as-a-Service Modified Cybersecurity
In 2012, Reveton ransomware emerged. It’s thought-about to be the primary Ransomware-as-a-Service (RaaS) operation ever. Since then, RaaS has enabled gangs with primary technical abilities to launch assaults indiscriminately. Now, almost anybody can create extremely efficient malware campaigns.
December twentieth 2022
Ransomware gang makes use of new Microsoft Trade exploit to breach servers
Play ransomware menace actors are utilizing a brand new exploit chain that bypasses ProxyNotShell URL rewrite mitigations to achieve distant code execution (RCE) on susceptible servers by way of Outlook Internet Entry (OWA).
Nokoyawa Ransomware: Rust or Bust
Nokoyawa ransomware was found in February 2022, sharing code with one other ransomware household generally known as Karma. Nokoyawa ransomware’s lineage can additional be traced again to Nemty ransomware. The unique model of Nokoyawa ransomware was written within the C programming language and file encryption utilized uneven Elliptic Curve Cryptography (ECC) with Curve SECT233R1 (a.ok.a. NIST B-233) utilizing the Tiny-ECDH open supply library mixed with a per file Salsa20 symmetric key. Nokoyawa ransomware 2.0 nonetheless makes use of Salsa20 for symmetric encryption, however the elliptic curve was changed with Curve25519.
New STOP ransomware variants
PCrisk discovered new STOP ransomware variants that append the .isal or .isza extensions.
December twenty first 2022
Conti Group One Splinter Group Resurfaces as Royal Ransomware with Callback Phishing Assaults
Royal ransomware might have been first noticed by researchers round September 2022, nevertheless it has seasoned cybercriminals behind it: The menace actors operating this ransomware — who was once part of Conti Group One, in response to a thoughts map shared by Vitali Kremez — initially dubbed it Zeon ransomware, till they rebranded it to Royal ransomware.
New HardBit 2.0 ransomware
PCrisk discovered the HardBit 2.0 ransomware that appends the .hardbit2 extension and drops ransom notes named How To Restore Your Information.txt.
New STOP ransomware variant
PCrisk discovered a brand new STOP ransomware variant that appends the .iswr extension.
December twenty second 2022
Vice Society ransomware gang switches to new customized encryptor
The Vice Society ransomware operation has switched to utilizing a customized ransomware encrypt that implements a powerful, hybrid encryption scheme primarily based on NTRUEncrypt and ChaCha20-Poly1305.
FIN7 hackers create auto-attack platform to breach Trade servers
The infamous FIN7 hacking group makes use of an automatic assault system that exploits Microsoft Trade and SQL injection vulnerabilities to breach company networks, steal information, and choose targets for ransomware assaults primarily based on monetary measurement.
Ransomware Roundup – Play Ransomware
Play is a relative newcomer to the ransomware recreation, having been detected for the primary time in June 2022. On this report, Play refers to each the group growing and distributing it and the title of the ransomware executable. Like many different operators on this house, Play has adopted the double-extortion methodology of encrypting endpoints and/or different infrastructure of worth inside a company after which threatening to launch exfiltrated information from these machines on the web if a ransom just isn’t paid.

