Within the final three years, for the reason that arrival of the COVID-19 pandemic in the USA, the character of the office has modified considerably. As of February, 76 % of the workforce with a job that may be accomplished from house in the USA was working a hybrid or utterly distant schedule, in response to Pew Analysis. Of that quantity, roughly one-third is totally distant.
On this evolving work local weather, organizations should be more and more vigilant towards malicious and unintentional (non-malicious) insider incidents. Many organizations by no means expertise a headline-grabbing, large-scale insider incident. As an alternative, many insider incidents are unintentional or non-malicious, sometimes the results of a safety incident or coverage violation. Based on our analysis, distraction is a key consider unintentional insider risk incidents. Distracted staff usually tend to make errors that may endanger a corporation, similar to failing to make use of their firm’s digital non-public community (VPN) or clicking on phishing hyperlinks in e mail. For a lot of hybrid and distant staff, distractions involving workspaces in shut proximity to youngsters and different relations can result in unintentional threat. Complete enterprise threat administration that features an insider threat program is a key part to securing organizations on this new atmosphere. On this put up, we current the 13 key components of an insider risk program.
Necessities Associated to Insider Menace
In 2011, the U.S. federal authorities launched an govt order requiring authorities businesses that function or entry categorised laptop networks to construct a proper insider risk detection and safety program.
The federal authorities had been beforehand charged with constructing the Nationwide Insider Menace Process Power, which develops a government-wide insider risk program for deterring, detecting, and mitigating insider threats.
In 2016, the Nationwide Industrial Safety Program Working Guide (NISPOM), which outlines authorities requirements for protection contractors, by way of NISPOM Confirming Change 2, additionally adopted a requirement that members of the Protection Industrial Base (DIB) construct insider risk detection and safety applications. DIB members, like the federal government businesses, should conduct yearly self-assessments of established insider risk applications or impartial third-party assessments.
A variety of high-profile incidents have impacted for-profit corporations as properly, leading to vital momentum to construct insider risk applications within the non-public sector.
Throughout the CERT Nationwide Insider Menace Heart, we now have developed numerous assets to assist public- and private-sector organizations assess the danger posed by trusted insiders. These assets deal with serving to organizations perceive the essential parts of an insider threat program and by what metrics a program is deemed efficient. We will additionally conduct third-party evaluations of insider risk applications for presidency or for-profit entities.
These assets embody the CERT Frequent Sense Information to Mitigating Insider Menace, Seventh Version, which outlines 22 finest practices that organizations can use to mitigate insider risk. Every finest apply contains methods and ways for fast wins and high-impact options, mitigations to reduce implementation challenges and roadblocks, and mappings to notable and related safety and privateness requirements. Greatest apply #2, Develop a Formalized Insider Threat Administration Program, offers a roadmap for organizations to observe.
Different assets embody
The Why and When of Insider Threat Administration
Incorporating insider risk into enterprise-wide threat administration permits this system or group to leverage current assets by
- avoiding duplication of effort with current safety controls targeted on exterior risk mitigation
- guaranteeing the insider threat program has participation from throughout the group, proving risk intelligence (data) from threat administration, data know-how, bodily safety, personnel administration, human assets, threat administration, basic counsel, and features of enterprise.
When contemplating insider threats, you will need to first develop a threat administration mindset. A threat administration mindset understands that the most effective time to develop an insider threat program and a course of for mitigating incidents, each malicious and non-malicious, is earlier than an incident happens. When contemplating the best way to shield organizational belongings, you will need to return to foundational cybersecurity rules and establish the essential belongings or companies or enterprise processes that, if attacked, wouldn’t enable your group to realize its mission as outlined by Brett Tucker within the put up 10 Steps for Managing Threat: OCTAVE FORTE.
In figuring out essential belongings (individuals, amenities, know-how, data), you will need to ask
- What services or products do we offer?
- What data are we entrusted to guard?
- What will we do to offer these companies or merchandise?
- What belongings will we use when performing these duties?
- What are the safety necessities of those belongings?
- What’s the worth of those belongings?
Key Components of an Insider Menace Program
Whereas data know-how (IT) is vital to an insider threat program, it is just one part. Too usually organizations fall into the lure of contemplating their program full as soon as they buy an insider threat administration software. Managing insider risk must be an ongoing, enterprise-wide effort that includes the IT division and others, similar to human assets, basic counsel, threat administration, and bodily safety.
This enterprise-wide method is required as a result of the power to observe person exercise on a community doesn’t at all times assure that monitoring is permitted or that it’s not an invasion of privateness. The identical requirements and tips that require federal businesses and contractors to ascertain insider threat applications to observe person exercise on networks additionally requires privateness and civil liberty safety, which is an space the place a corporation’s basic counsel performs a key position. A holistic method to insider threat administration includes enterprise-wide participation into necessities, monitoring, governance, and oversight of this system—somebody watching the watchers. Oversight is a core precept in our greatest practices.
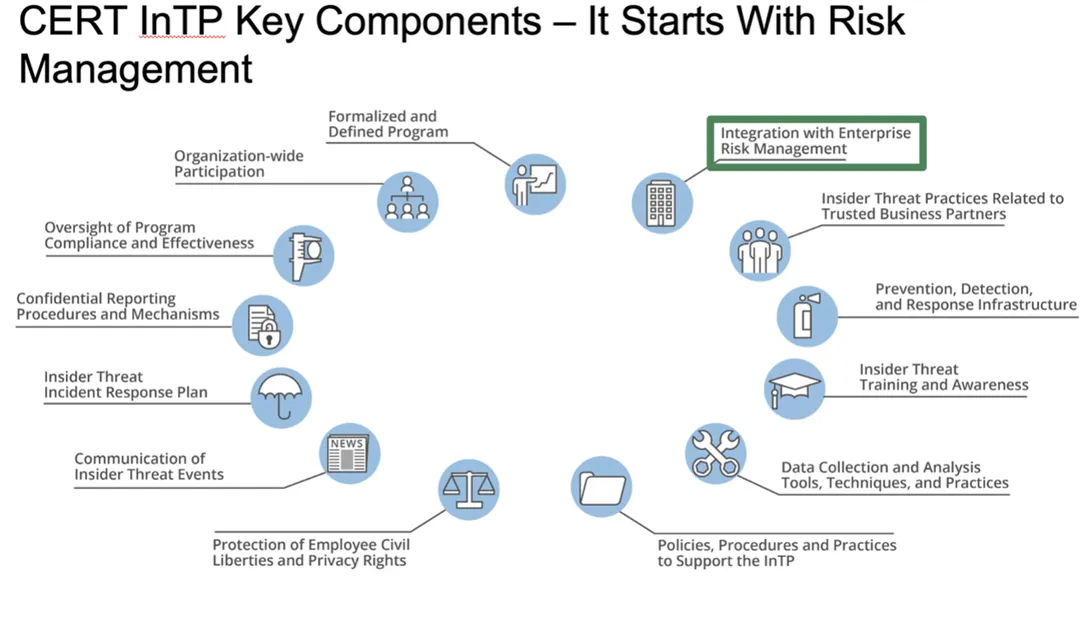
In September 2022, we printed the seventh version of our Frequent Sense Information to Mitigating Insider Threats, which relies on analysis and evaluation of greater than 3,000 incidents. Along with finest practices for mitigating insider threats and assets for varied stakeholders inside a corporation (i.e., administration, human assets, authorized counsel, bodily safety, IT, data safety, information homeowners, and software program), the information outlines the essential components of an insider threat program, proven within the determine beneath:
- Formalized and Outlined Insider Threat Administration Program (IRMP)—This system ought to embody components similar to directives, authorities, a mission assertion, management intent, governance, and a funds.
- Group-Vast Participation—This system ought to have energetic participation from all organizational parts that share or use program information. Senior management ought to present seen help for this system, particularly when the info the IRMP wants is in siloes (i.e., information lives solely in areas or departments similar to human assets [HR], bodily safety, data know-how [IT], or data safety).
- Oversight of Program Compliance and Effectiveness—A governance construction, similar to an IRMP working group or change management board, ought to assist the IRMP program supervisor formulate requirements and working procedures for the IRMP and advocate modifications to current practices and procedures. Additionally, an govt council or steering committee ought to approve modifications beneficial by the working group/change management board. Oversight contains annual self-assessments and exterior entity assessments that consider the compliance and effectiveness of the IRMP.
- Confidential Reporting Procedures and Mechanisms—Not solely do these mechanisms and procedures allow the reporting of suspicious exercise, however when intently coordinated with the IRMP, additionally they be certain that reputable whistleblowers aren’t inhibited or inappropriately monitored.
- Insider Menace Incident Response Plan—This plan have to be greater than only a referral course of to exterior investigators. It ought to element how alerts and anomalies are recognized, managed, and escalated, together with timelines for each motion and formal disposition procedures.
- Communication of Insider Menace Occasions—Occasion data must be appropriately shared with the proper organizational parts, whereas sustaining workforce member confidentiality and privateness. Any such communication contains insider threat tendencies, patterns, and potential future occasions in order that insurance policies, procedures, coaching, and so on., might be modified as acceptable.
- Safety of Workforce Member Civil Liberties and Privateness Rights—Authorized counsel ought to evaluation the IRMP’s selections and actions in any respect phases of program improvement, implementation, and operation.
- Integration with Enterprise Threat Administration—The IRMP should be certain that all features of the group’s threat administration embody insider risk concerns (not simply exterior attackers), and the group ought to contemplate establishing a standalone part for insider threat administration.
- Practices Associated to Managing Trusted Exterior Entities (TEEs)—These practices embody agreements, contracts, and processes reviewed for insider risk prevention, detection, and response capabilities.
- Prevention, Detection, and Response Infrastructure—This infrastructure contains parts, similar to community defenses, host defenses, bodily defenses, instruments, and processes.
- Insider Menace Coaching and Consciousness—This coaching encompasses three features of the group: (1) insider risk consciousness coaching for the group’s total workforce (e.g., workers, contractors, consultants), (2) coaching for IRMP personnel, and (3) role-based coaching for mission specialists who’re prone to observe sure features of insider risk occasions (e.g., HR, Data Safety, Counterintelligence, Administration, Finance).
- Knowledge Assortment and Evaluation Instruments, Strategies, and Practices—These instruments, strategies, and practices embody person exercise monitoring (UAM), information assortment, and evaluation parts of this system. Detailed documentation is required for all features of information assortment, processing, storage, and sharing to make sure compliance with workforce member privateness and civil liberties.
- IRMP Insurance policies, Procedures, and Practices—The IRMP will need to have formal paperwork that element all features of this system, together with its mission, scope of threats, directives, directions, and commonplace working procedures.
- Optimistic Incentives—Organizations ought to encourage constructive workforce habits moderately than coerce it by leveraging positive-incentive-based organizational practices centered on growing job engagement, perceived organizational help, and connectedness at work.
Insider Threat and AI
Machine studying (ML) and synthetic intelligence (AI) have been on the forefront of insider risk anomaly detection for numerous years. Conventional safety controls have concerned instruments that may monitor person exercise, however solely after receiving steering from an analyst on particular behavioral anomalies to be looking out for. This association limits the scope of monitoring to what’s accessible inside conventional controls and at an analyst’s discretion. Such an method could flag exercise if a person downloads 100 paperwork in a day, however what if an insider does one doc a day over 100 days?
AI and ML can delve deeper to find out probably worrisome patterns of exercise by a person by considering statistical and human anomalies.
A brand new class of insider risk instruments, which depend on person entity and habits analytics (UEBA), widens the aperture past technical anomalies involving an worker’s laptop use to include completely different information units. If an worker is leaving a corporation, for instance, the instruments would pull information from the HR administration system. These instruments additionally account for exercise in a corporation’s bodily safety programs, together with badging information or digital camera programs.
UEBA instruments are utilizing AI at the start by incorporating completely different information from throughout a corporation and informing analysts of anomalies with out analysts telling the instruments what must be reported.
Most workers don’t be a part of a corporation meaning to do hurt, and, as we referenced earlier, most insider incidents that do happen are unintentional. No matter intent, all insider incidents contain a misuse of approved entry to a corporation’s essential belongings, and a lot of the incidents are unintentional. We within the CERT Division of the SEI are working to grasp the underlying causes behind stressors and regarding behaviors to detect insider threats early and provide workers help earlier than they commit a dangerous act.