Tales from the SOC is a weblog collection that describes current real-world safety incident investigations performed and reported by the AT&T SOC analyst workforce for AT&T Managed Prolonged Detection and Response prospects.
Government abstract
Since mid-June 2022, AT&T Managed Prolonged Detection and Response (MXDR) Safety Operations Heart (SOC) noticed an unlimited variety of assaults from Mirai botnet-C2 trying to achieve entry to SSH servers as a substitute of Telnet.
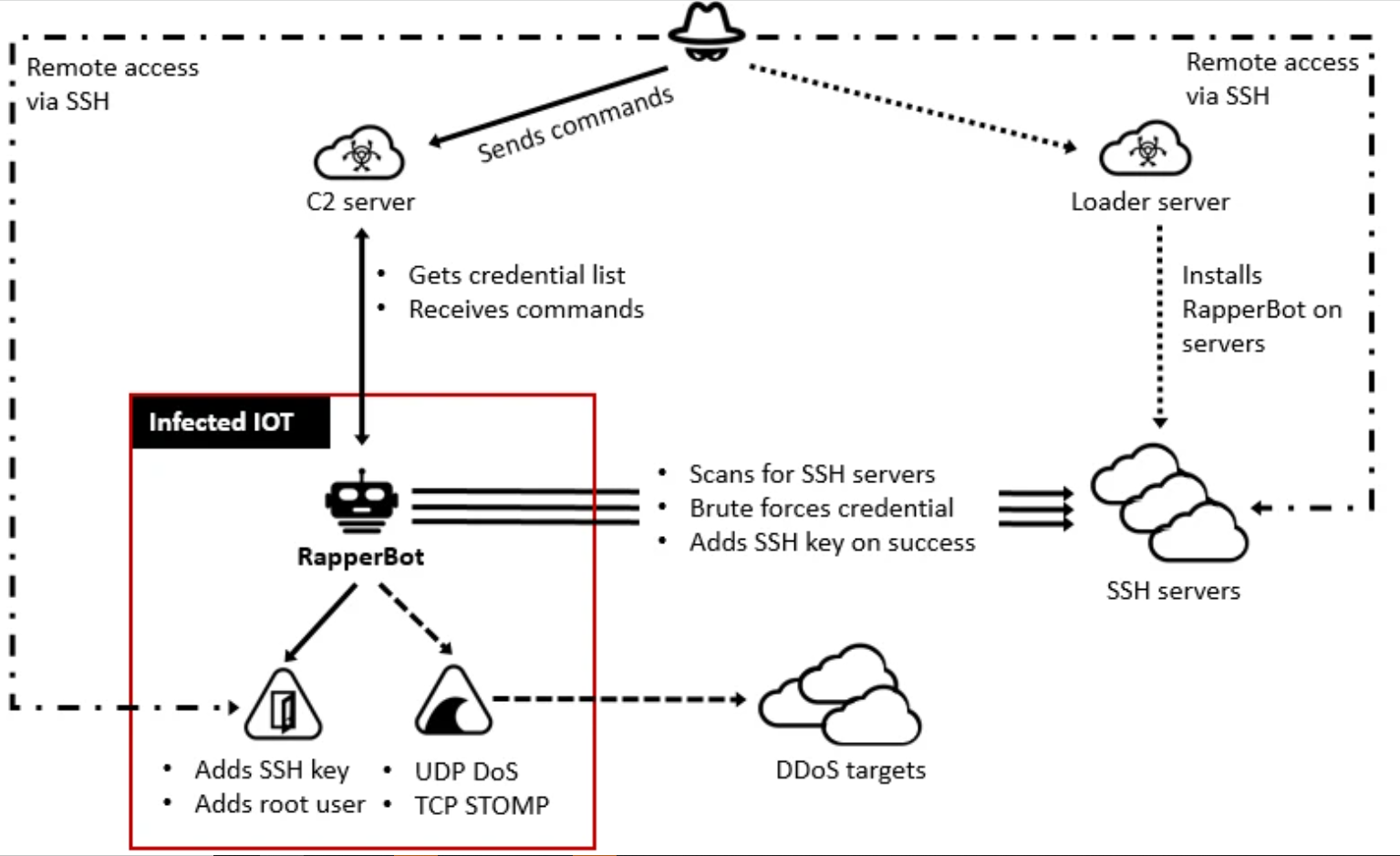
As a result of numerous ways, methods, and procedures (TTP) noticed, this assault has been related to RapperBot botnet (Mirai variants.) RapperBot’s purpose remains to be undefined.
Based on the evaluation that was revealed by FortiGuard Labs, whereas nearly all of Mirai variants can naturally brute pressure Telnet servers that use default or weak passwords, RapperBot specifically scans and makes an attempt to brute pressure SSH servers which can be designed to require password authentication.
A big a part of the malware is executing an SSH 2.0 shopper which is ready to join and brute pressure any SSH server utilizing Diffie-Hellman key alternate with 768-bit or 2048-bit keys and knowledge encryption utilizing AES128-CTR. A singular attribute of brute forcing in RapperBot is using SSH-2.0-HELLOWORLD with a purpose to determine itself to the focused SSH server throughout the SSH Protocol Change section.
One of many malicious Mirai botnet IP addresses had allowed community visitors with an asset in a corporation over SSH port 22. After some knowledge transferring, the session closed with the client-reset motion. The MXDR SOC workforce shortly recognized and beneficial mitigation steps to stop lateral motion and the attacker going additional.
Investigation
Preliminary alarm overview
Indicators of Compromise (IOC)
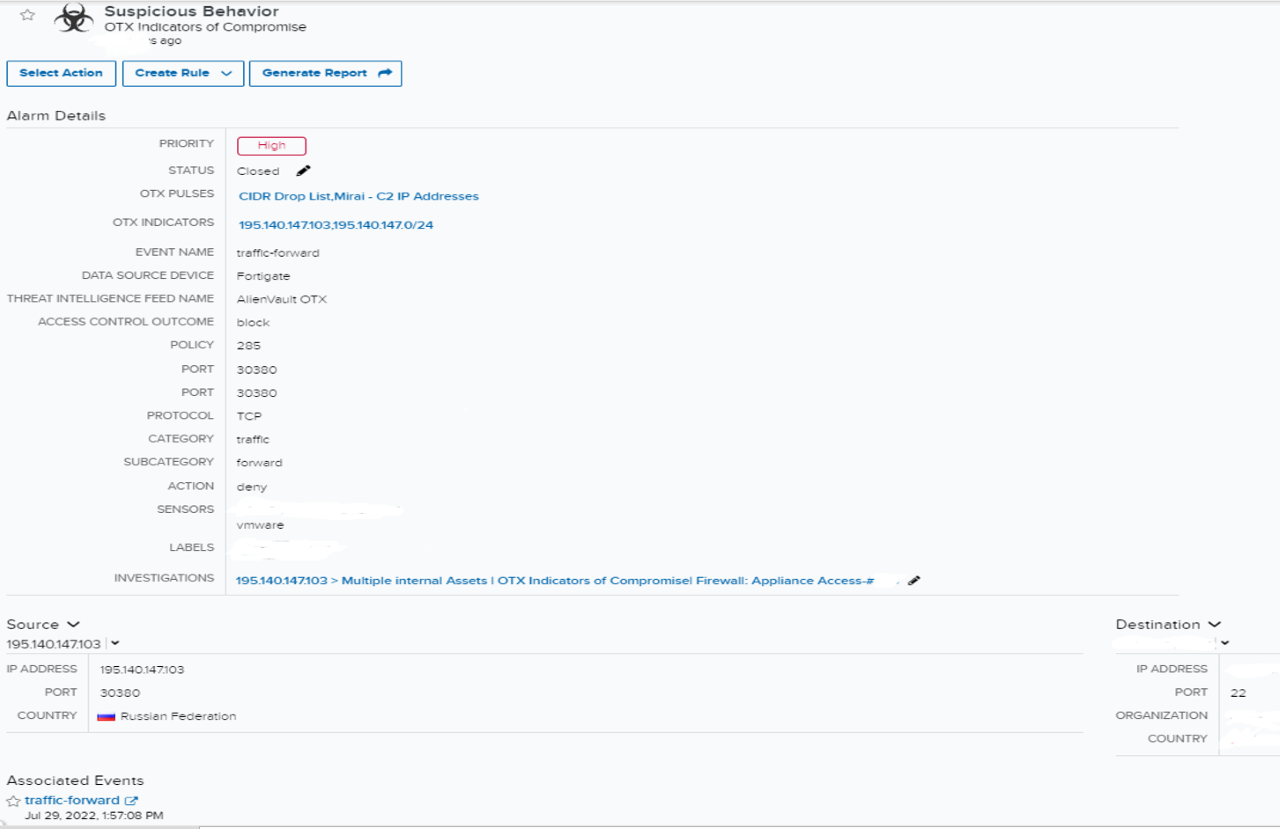
The alarm initiated with the a number of Open Menace Change (OTX) pulses (Miraibotnet-C2- CDIR Drop Checklist) and an OTX indicator of a identified malicious IP. There was community visitors between the identified malicious IP and a public IP of an inside asset in a corporation. The community visitors was over SSH port 22, and the safety system (firewall) motion was a deny. The safety system (firewall) deny motion was proof of the auto-mitigation. On this case, auto-mitigation means the assault is prevented by firewall guidelines and menace intelligence by denying the connection from malicious IP.
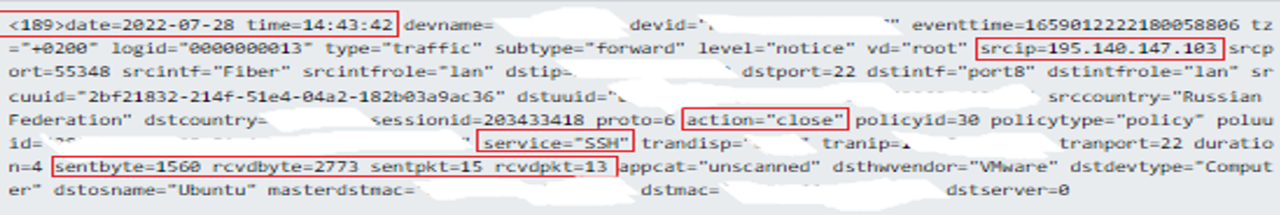
Nonetheless, additional evaluation of the occasions confirmed that the visitors was allowed from the malicious IP to a different inside asset. Along with this, there have been indicators of knowledge switch from supply IP with “sentbyte=1560, rcvdbyte=2773, sentpkt=15, rcvdpkt=13”
** Danger mitigation in Cybersecurity is the discount of the general danger/affect of cyber-attacks. Detection, prevention, and remediation are three parts of danger mitigation in cybersecurity.
Expanded investigation
Occasions search
After checking occasions related to the alarm, the workforce all the time checks the environmental safety to see if the malware had additional penetrated the setting or tried any lateral motion.
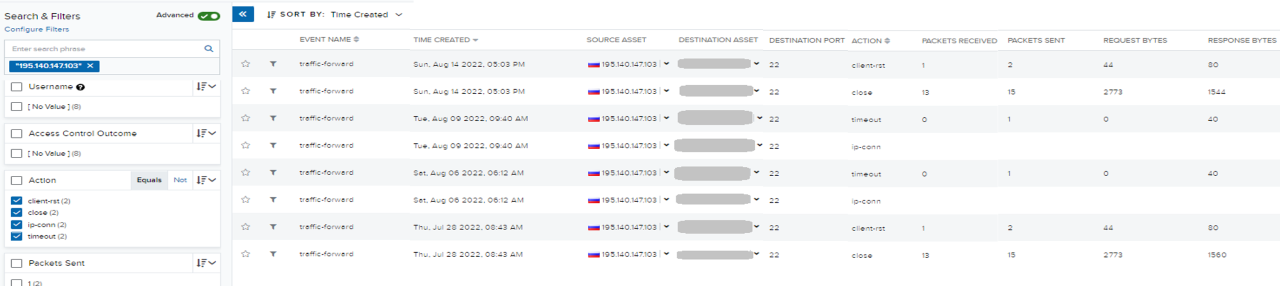
The workforce searched occasions by pivoting on the indicator IP, filtering the previous 90 days of occasions, and the safety system (firewall) allowed motion varieties. It was decided that there have been just a few connections from malicious IP to totally different inside belongings with the client-rst, server-rst, timeout, and closed occasions.
Client-rst – Session reset by shopper, Server-rst – Session reset by server
These are normally session finish causes that present who’s sending TCP (Transmission Management Protocol) reset and the session terminates – so this doesn’t imply {that a} safety system (firewall) is obstructing the visitors. It means after a session is began between client-to-server, it’s terminated by (shopper or server), relying on who despatched the TCP reset. Session-end outcomes might be present in visitors logs.
The workforce suspected that the system is perhaps compromised as a result of the session was reset from the shopper facet (which is the adversary facet.) It was then noticed that the session was closed (terminated) with a considerable amount of packet transmissions.
Occasion deep dive
After additional examination of the allowed connections, the malicious IP confirmed visitors with the client safety system (firewall) over SSH port 22. SSH port 22 makes use of a TCP connection. Due to this fact, earlier than transferring knowledge it wants to ascertain a dependable reference to the 3-way handshakes.
With a purpose to handshake the header (first two packets), TCP makes use of roughly 24 bytes and for regular transmission of packet about 20 bytes. Establishing a dependable reference to 3-way handshake wants simply three packets to be transmitted. Establishing a connection: ~ 128-136 bytes.
One other statement is that the despatched and obtained bytes with the packet dimension are indicators of knowledge transferring as a result of packets and bytes being larger than regular packets and bytes of TCP 3-way handshake. That is believed to be a sign of a payload or compromised credentials.
Rapperbots work like an SSH brute-forcing marketing campaign. After it has gained entry on a tool, it sends its structure to the C2 server – the gadget’s IP, and the credentials used. Then the adversary tries to load the principle payload binary on the compromised gadget by way of binary downloader or software program like ftpget, wget, curl, or tftp, that’s put in on the gadget.
Reviewing for extra indicators
At this level, the attacker tried to get “Preliminary Entry (tactic)” into the community by utilizing “Exploit Public Going through Software” method primarily based on the Mitre Att&ck Framework.
Exploit Public Going through Software is a method which is utilized by adversaries to reap the benefits of vulnerabilities/weaknesses in a program or web dealing with laptop to achieve Preliminary entry to a community. On this case, regardless that there was proof of knowledge switch, proof of payload or lateral motion exercise weren’t seen.
Response
Constructing the investigation
An investigation was created by following the incident response course of. The investigation included figuring out the incident, discovering the basis reason for the incident and Indicators of compromise. Then we made suggestions to the client on mitigation/remediation steps. We communicated with the client to make sure mandatory actions are executed. Really helpful mitigation steps have been:
- Blocking the malicious IP
- Disabling SSH password authentication (if doable)
- Altering passwords to stronger passwords for the gadget.
Incident response is an organizationed strategy and course of to handle cybersecurity breaches/incidents or cyberattacks. It contains a number of steps:
- Figuring out an incident/assault
- Minimizing injury
- Eradicating the basis trigger
- Minimizing restoration value and time
- Studying classes from the incident
- Taking preventative motion
Based on the evaluation that was revealed by FortiGuard Labs, Rapperbot builders improved their code to take care of persistence, which differentiates it from different Mirai variants. Even after rebooting contaminated belongings or eradicating malware, intruders can repeatedly entry contaminated belongings by way of SSH. Due to this fact, rebooting the gadget or eradicating malware Shouldn’t be a everlasting mitigation possibility.
The Rapperbot’s main menace is brute forcing the credentials of SSH. By disabling SSH password authentication (if doable), or altering passwords to stronger passwords for the gadget, the Rapperbot mitigation can simply be executed.
Buyer interplay
The client wished to be stored within the loop and knowledgeable if the assault continues.
Limitations and alternatives
Limitations
On this investigation, MXDR was unable in a position to see contained in the transmitted packets. Because of the dearth of visibility into the community flows within the setting, MXDR has restricted entry to the client setting. Nonetheless, MXDR suspected the information switch may embrace the principle payload binary on the compromised gadget.