The group behind a classy distant entry Trojan, SilverRAT, has hyperlinks to each Turkey and Syria and plans to launch an up to date model of the instrument to permit management over compromised Home windows techniques and Android units.
In line with a risk evaluation printed on Jan. 3, SilverRAT v1 — which at the moment works solely on Home windows techniques — permits the constructing of malware for keylogging and ransomware assaults, and consists of harmful options, comparable to the flexibility to delete system restore factors, researchers from Singapore-based Cyfirma acknowledged of their evaluation.
SilverRAT Builder Permits Numerous Options
SilverRAT reveals that the area’s cybercriminal teams have gotten extra refined, based on Cyfirma’s evaluation. The primary model of SilverRAT, whose supply code was leaked by unknown actors in October, consists of a builder that enables the consumer to assemble a distant entry Trojan with particular options.
The extra attention-grabbing options, based on Cyfirma’s evaluation, embody utilizing both an IP tackle or webpage for command and management, bypasses for antivirus software program, the flexibility to erase system restore factors, and the delayed execution of payloads.
No less than two risk actors — one utilizing the deal with “Harmful silver” and a second utilizing “Monstermc” — are the builders behind each SilverRAT and a earlier program, S500 RAT, based on Cyfirma’s evaluation. The hackers function on Telegram and thru on-line boards the place they promote malware-as-a-service, distribute cracked RATs from different builders, and provide a wide range of different providers. As well as, they’ve a weblog and web site known as Nameless Arabic.
“There are two individuals managing SilverRAT,” says Rajhans Patel, a risk researcher with Cyfirma. “We’ve got been capable of collect photographic proof of one of many builders.”
Beginning From Boards
The group behind the malware, dubbed Nameless Arabic, is lively on Center Japanese boards, comparable to Turkhackteam, 1877, and no less than one Russian discussion board.
Along with the event of SilverRAT, the group’s builders provide a distributed denial-of-service (DDoS) assaults on demand, says Koushik Pal, a risk researcher with the Cyfirma Analysis workforce.
“We’ve got noticed some exercise from Nameless Arabic since late November 2023,” he says. “They’re recognized to be utilizing a botnet being marketed on Telegram often called ‘BossNet’ to conduct DDOS assaults on massive entities.”
Whereas the Center East risk panorama has been dominated by the state-run and state-sponsored hacking teams in Iran and Israel, homegrown teams comparable to Nameless Arabic proceed to dominate the cybercrime markets. The continuing improvement of instruments comparable to SilverRAT spotlight the dynamic nature of the underground markets within the area.
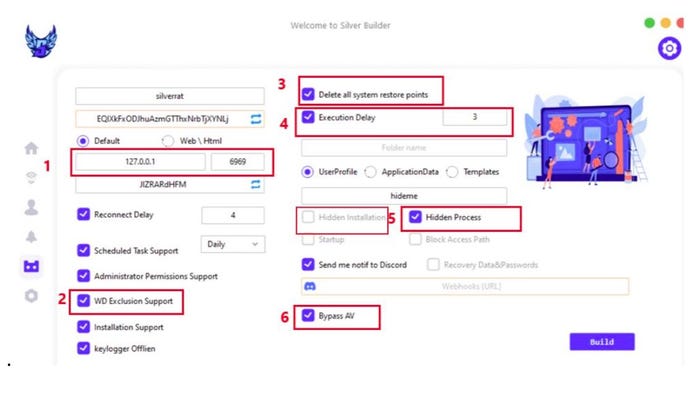
The SilverRAT dashboard for constructing trojans. Supply: Cyfirma
Hacking teams within the Center East are typically fairly different, says Sarah Jones, a cyber risk intelligence analysis analyst at managed detection and response agency Essential Begin, who cautioned that particular person hacking teams are continuously evolving and generalizing their traits might be problematic.
“The extent of technical sophistication varies drastically amongst teams within the Center East,” she says. “Some state-backed actors possess superior capabilities, whereas others depend on less complicated instruments and methods.”
A Gateway By means of Sport Hacks
Of the recognized members of the Nameless Arabic group, no less than one is a former recreation hacker, based on knowledge gathered by researchers at Cyfirma, together with the Fb profile, YouTube channel, and social-media posts of one of many hackers — a person in his early 20s who lives in Damascus, Syria, and began hacking as a teen.
The profile of younger hackers who lower their tooth on discovering exploits for video games transcends the hacking group within the Center East. Youngsters beginning their hacking careers by creating gaming hacks or launching denial-of-service assaults towards recreation techniques has turn out to be a development. Arion Kurtaj, a member of the Lapsus$ group, began as a Minecraft hacker and later moved on to hacking targets comparable to Microsoft, Nvidia, and recreation maker Rockstar.
“We will see an identical development with the developer of SilverRAT,” says Rajhans Patel, a risk researcher with Cyfirma, including within the risk evaluation: “Reviewing the developer’s earlier posts reveals a historical past of providing varied first-person shooter (FPS) recreation hacks and mods.”
The US Division of Homeland Safety’s Cyber Security Assessment Board (CSRB), which conducts autopsy evaluation of main hacks, recognized the persevering with pipeline from juvenile hackers to cybercriminal enterprises as a existential hazard. Governments and personal organizations ought to put in place holistic packages to redirect juveniles away from cybercrime, the CSRB present in its evaluation of the success of the Lapsus$ group in attacking “a number of the world’s most well-resourced and well-defended corporations.”
But younger programmers and technology-savvy youngsters typically discover different methods into the cybercriminal fold as nicely, says Essential Begin’s Jones.
“Hackers, like all inhabitants group, are numerous people with different motivations, expertise, and approaches,” she says. “Whereas some hackers could begin out with recreation hacks and transfer to extra critical instruments and methods, we frequently discover that cybercriminals have a tendency to focus on industries and international locations with weaker cyber defenses.”


