For years, the Center East has maintained its popularity as a fertile floor for superior persistent threats (APTs). Within the midst of routine monitoring of suspicious actions on the techniques of high-profile clients, some based mostly on this area, ESET Analysis stumbled upon a really subtle and unknown backdoor that we have now named Deadglyph. We derived the identify from artifacts discovered within the backdoor (equivalent to 0xDEADB001, proven additionally in Desk 1), coupled with the presence of a homoglyph assault. To the perfect of our data, that is the primary public evaluation of this beforehand undocumented backdoor, utilized by a gaggle that reveals a notable diploma of sophistication and experience. Primarily based on the concentrating on and extra proof, we attribute Deadglyph with excessive confidence to the Stealth Falcon APT group.
Deadglyph’s structure is uncommon because it consists of cooperating elements – one a local x64 binary, the opposite a .NET meeting. This mixture is uncommon as a result of malware usually makes use of just one programming language for its elements. This distinction may point out separate growth of these two elements whereas additionally profiting from distinctive options of the distinct programming languages they make the most of. Completely different language may also be harnessed to hinder evaluation, as a result of blended code is harder to navigate and debug.
The normal backdoor instructions should not carried out within the backdoor binary; as a substitute, they’re dynamically acquired by it from the command and management (C&C) server within the type of further modules. This backdoor additionally options various capabilities to keep away from being detected.
On this blogpost, we take a better take a look at Deadglyph and supply a technical evaluation of this backdoor, its function, and a number of the further elements we obtained. We’re additionally presenting our findings about Deadglyph on the LABScon 2023 convention.
Key factors of the blogpost:
- ESET Analysis found a complicated backdoor with uncommon structure that we have now named Deadglyph.
- The primary elements are encrypted utilizing a machine-specific key.
- Conventional backdoor instructions are carried out by way of further modules acquired from its C&C server.
- We obtained three out of many modules – course of creator, file reader, and information collector.
- We attribute Deadglyph to the Stealth Falcon group.
- Moreover, we discovered a associated shellcode downloader; we postulate it might doubtlessly be used for set up of Deadglyph.
The sufferer of the analyzed infiltration is a governmental entity within the Center East that was compromised for espionage functions. A associated pattern discovered on VirusTotal was additionally uploaded to the file-scanning platform from this area, particularly from Qatar. The focused area is depicted on the map in Determine 1.
Stealth Falcon (also referred to as Undertaking Raven or FruityArmor) is a risk group linked to the United Arab Emirates in accordance with MITRE. Energetic since 2012, Stealth Falcon is thought to focus on political activists, journalists, and dissidents within the Center East. It was first found and described by Citizen Lab, which printed an evaluation of a marketing campaign of spy ware assaults in 2016.
In January 2019, Reuters printed an investigative report on Undertaking Raven, an initiative allegedly using former NSA operatives and aiming on the identical kinds of targets as Stealth Falcon. Primarily based on these two reviews referring to the identical targets and assaults, Amnesty Worldwide has concluded (proven in Determine 2) that Stealth Falcon and Undertaking Raven truly are the identical group.
In September 2019, we printed analysis on a backdoor, attributed to Stealth Falcon, that used an uncommon method, Background Clever Switch Service, for C&C communication. We now reveal the results of our in-depth evaluation of what presumably is the latest addition to Stealth Falcon’s espionage toolset.
Deadglyph backdoor
Deadglyph’s loading chain consists of a number of elements, as illustrated in Determine 3. The preliminary element is a registry shellcode loader, which hundreds shellcode from the registry. This extracted shellcode, in flip, hundreds the native x64 a part of the backdoor – the Executor. The Executor subsequently hundreds the .NET a part of the backdoor – the Orchestrator. Notably, the one element on system’s disk as a file is the preliminary element, which is within the type of a Dynamic Hyperlink Library (DLL). The remaining elements are encrypted and saved inside a binary registry worth.
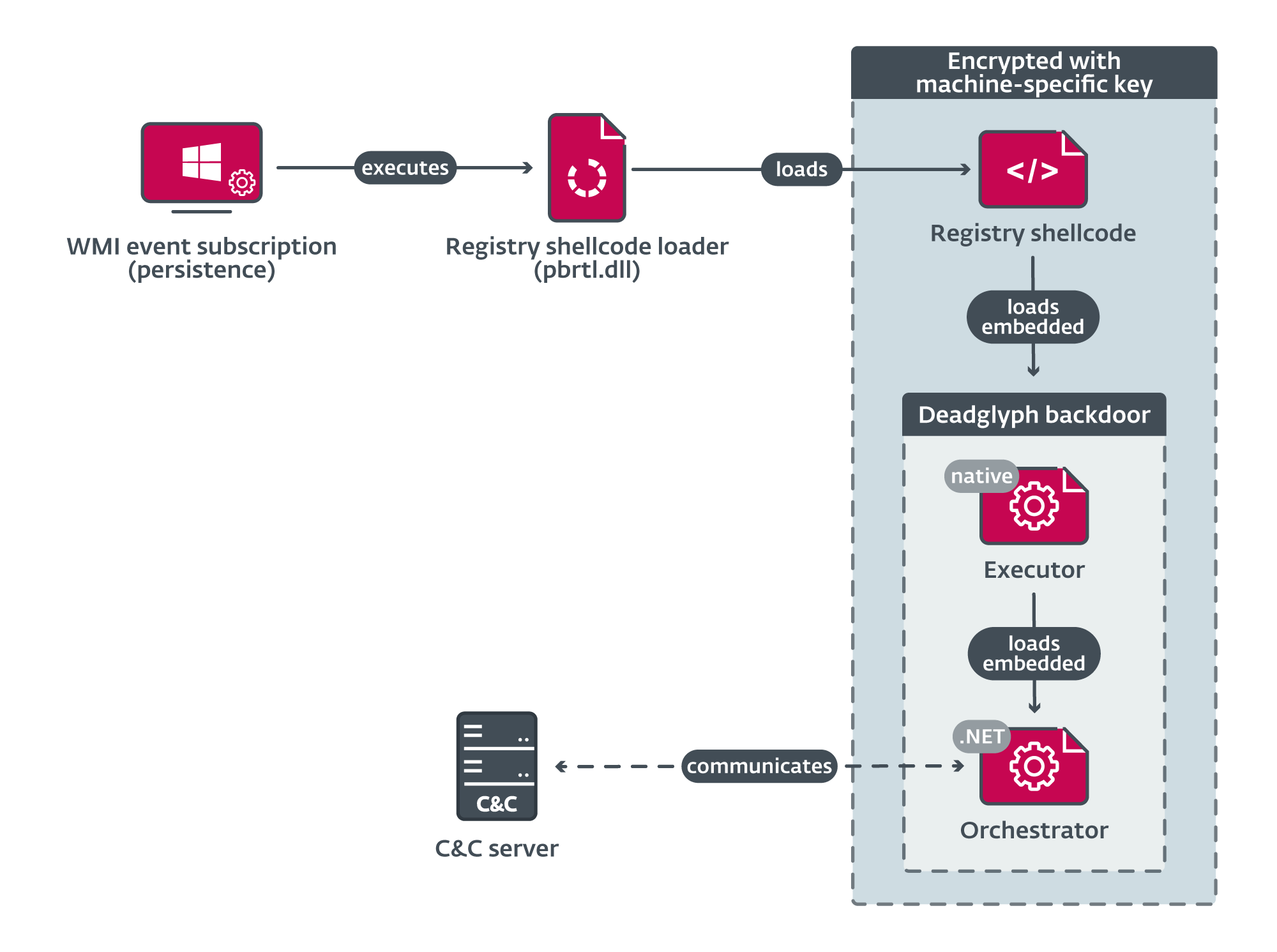
Whereas the exact technique of the preliminary compromise vector shouldn’t be but decided, our suspicion is that an installer element is concerned in deploying additional elements and establishing persistence inside the system.
In the remainder of this part, we analyze every element.
Registry shellcode loader
Deadglyph’s preliminary element is a tiny DLL with a single export, named 1. This element is endured utilizing Home windows Administration Instrumentation (WMI) occasion subscription and serves as a registry shellcode loader. It’s executed by way of the command line rundll32 C:WINDOWSSystem32pbrtl.dll,#1.
The registry shellcode loader begins its operation by decrypting the trail to the encrypted shellcode saved inside the Home windows registry, utilizing RC4. We suspect the trail is exclusive for every sufferer; within the case analyzed right here, the registry path was:
SoftwareClassesCLSID{5abc7f42-1112-5099-b082-ce8d65ba0c47}cAbRGHLg
The foundation registry key’s both HKLM or HKCU, relying on whether or not the present course of is operating with elevated privileges or not. The identical logic might be present in additional elements.
Following this, the loader derives a machine-specific RC4 key utilizing the system UUID retrieved from the uncooked SMBIOS firmware desk. Utilizing this key, it hundreds, decrypts, after which executes the shellcode. You will need to spotlight that this key derivation method ensures that correct decryption gained’t happen if the loader is executed on a special laptop.
Apparently, the loader may also be configured by a flag in its .knowledge part to make use of a hardcoded key to decrypt the shellcode, as a substitute of the machine-specific one.
We noticed a homoglyph assault mimicking Microsoft Company within the VERSIONINFO useful resource of this and different PE elements. This technique employs distinct Unicode characters that seem visually related, however on this case not an identical, to the unique characters, particularly Greek Capital Letter San (U+03FA, Ϻ) and Cyrillic Small Letter O (U+043E, о) in Ϻicrоsоft Corpоratiоn.
Registry shellcode
Comprised of two components, the registry shellcode consists of a decryption routine and an encrypted physique. First, the decryption routine rotates every byte of the encrypted physique to the left by one (ROL 0x01). Subsequently, management is transferred to this decrypted physique. The decrypted physique consists of a PE loader and a PE file, the latter being the Executor, which represents the native a part of the backdoor. This loader is liable for parsing and loading the related PE file.
Executor
The Executor is the native x64 a part of the Deadglyph backdoor, which does the next:
- hundreds its configuration,
- initializes the .NET runtime,
- hundreds the embedded .NET a part of the backdoor (the Orchestrator), and
- acts as a library for the Orchestrator.
First, two default configurations embedded within the .knowledge part are AES-decrypted. The configurations embody numerous parameters, together with encryption keys, security and evasion settings, and the entry level of the following element.
Throughout the preliminary execution, these two default configurations are saved inside the Home windows registry, from the place they’re loaded on subsequent runs, enabling the implementation of updates. The registry path for every configuration is generated with the next format:
HKLMSoftwareClassesCLSID{<variable_GUID>}(Default)
<variable_GUID> is a generated GUID, which is exclusive to every sufferer.
Following this, the .NET runtime is initialized, then the Executor RC4-decrypts the .NET a part of the backdoor often called the Orchestrator. The Orchestrator is positioned inside the .rsrc part of the Executor. The configuration specifies the Orchestrator’s execution technique as an entry level. Furthermore, a definite construction is offered to facilitate accessibility of the Executor’s capabilities by the Orchestrator.
After launching the Orchestrator, the Executor acts as a assist library for the Orchestrator. The Executor accommodates many attention-grabbing capabilities; we describe a few of them within the following part, in context of their utilization by the Orchestrator and additional loaded modules.
Orchestrator
Written in .NET, the Orchestrator is the primary element of the Deadglyph backdoor. This element’s main function includes establishing communication with the C&C server and executing instructions, typically facilitated by means of the middleman function of the Executor. In distinction to the previous elements, the Orchestrator is obfuscated, using .NET Reactor. Internally, the backdoor is known as agent, which is a typical identify for the shopper half in numerous post-exploitation frameworks.
Initialization
The Orchestrator first hundreds its configuration and two embedded modules, every accompanied by its personal set of configurations, from assets. These assets are Deflate compressed and AES encrypted. They’re referenced by an ID that’s SHA-1 hashed right into a useful resource identify. An outline of those assets is offered in Desk 1.
Desk 1. Orchestrator assets
|
Useful resource identify |
ID (decimal) |
ID (hex) |
Description |
|
43ed9a3ad74ed7ab74c345a876b6be19039d4c8c |
2570286865 |
0x99337711 |
Orchestrator configuration. |
|
3a215912708eab6f56af953d748fbfc38e3bb468 |
3740250113 |
0xDEEFB001 |
Community module. |
|
42fb165bc9cf614996027a9fcb261d65fd513527 |
3740250369 |
0xDEEFB101 |
Community module configuration. |
|
e204cdcf96d9f94f9c19dbe385e635d00caaf49d |
3735924737 |
0xDEADB001 |
Timer module. |
|
abd2db754795272c21407efd5080c8a705a7d151 |
3735924993 |
0xDEADB101 |
Timer module configuration. |
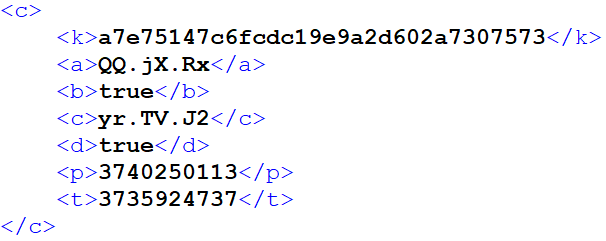
The configuration of the Orchestrator and embedded modules is saved in XML format. An instance of an Orchestrator configuration is proven in Determine 4.
The outline of Orchestrator configuration entries is proven in Desk 2.
Desk 2. Orchestrator configuration entries
|
Key |
Description |
|
AES key used for persisting module configurations. |
|
Community module initialization technique identify. |
|
Unknown community module-related flag. |
|
Timer module initialization technique identify. |
|
Flag enabling utilization of machine-specific AES key (system UUID) for assets. |
|
Community module useful resource ID. |
|
Timer module useful resource ID. |
After the useful resource elements are loaded, a number of threads are created to hold out distinct duties. Certainly one of these threads is liable for conducting atmosphere checks, a operate carried out inside the Executor. One other thread is dedicated to establishing periodic communication with the C&C server, enabling the retrieval of instructions. Lastly, a set of three threads is employed for the aim of executing acquired instructions and subsequently transmitting any generated output again to the C&C server.
The environment-checking thread screens operating processes to determine undesirable ones. This thread operates with two distinct lists of course of names. If a course of on the primary listing is detected, C&C communication and command execution is paused till the undesirable course of not exists. If there’s a match for any course of on the second listing, the backdoor instantly quits and uninstalls itself.
Neither listing was configured within the analyzed occasion, so we don’t know what processes may usually be checked for; we consider it’s most likely supposed to evade evaluation instruments that would detect suspicious exercise and result in discovery of the backdoor.
Communication
The Orchestrator makes use of two embedded modules for C&C communication – Timer and Community. Just like the Orchestrator, these modules are obfuscated with .NET Reactor. The configuration for each modules is provided by the Orchestrator. Inside the Orchestrator, a preset configuration for the modules is included; optionally, the Orchestrator can even load an up to date configuration model from the registry:
HKLMSoftwareClassesCLSID{<variable_GUID>}<mod_cfg_res_ID>
The backdoor accommodates an attention-grabbing security measure associated to communication. If the backdoor is unable to determine communication with the C&C server for a length surpassing a predefined threshold, configured inside the Executor, a self-uninstallation mechanism is triggered. This time threshold is laid out in hours and was set at one hour within the examined case.
This method serves a twofold function. On one hand, it prevents the era of redundant community requests in direction of an inaccessible server. Then again, it reduces the probabilities of subsequent detection if the operators lose management over the backdoor.
Timer module
This small module executes the required callback at a configurable interval. It’s utilized by the Orchestrator together with the Community module to speak with the C&C server periodically. To forestall the creation of detectable patterns in community logs, the execution interval is topic to randomization, based mostly on a share specified within the configuration. Within the analyzed occasion, the interval was set to 5 minutes, with a ±20% variation launched for randomness.
One other technique to keep away from detectable community patterns in periodic communication might be present in era of requests despatched to the C&C server. This mechanism, carried out within the Executor, includes the inclusion of padding of various size, comprised of random bytes, inside the requests, leading to requests of numerous sizes.
Community module
The Community module implements communication with the C&C servers laid out in its configuration. It might probably ship knowledge to a C&C server utilizing HTTP(S) POST requests. Notably, it provides a number of mechanisms to accumulate proxy configuration particulars. This function suggests a possible deal with environments the place direct web entry shouldn’t be obtainable.
An instance of a decrypted (and beautified) configuration is proven in Determine 5.
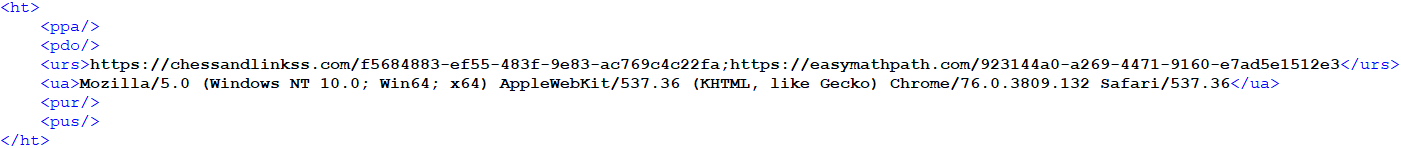
Configuration entries comprise particulars associated to community communications – C&C URLs, HTTP Person-Agent, and optionally a proxy configuration.
When speaking with the C&C server, a customized binary protocol with encrypted content material is used beneath HTTPS.
Instructions
The Orchestrator receives instructions from the C&C server within the type of duties, that are queued for execution. There are three sorts of duties processed:
- Orchestrator duties,
- Executor duties, and
- Add duties.
The primary two sorts are acquired from the C&C server and the third is created internally to add the output of instructions and errors.
Orchestrator duties
Orchestrator duties supply the power to handle the configuration of the Community and Timer modules, and likewise to cancel pending duties. The overview of Orchestrator duties is proven in Desk 3.
Desk 3. Orchestrator duties
|
Kind |
Description |
|
Set configuration of community and timer modules. |
|
Get configuration of community and timer modules. |
|
Cancel process. |
|
Cancel all duties. |
Executor duties
Executor duties supply the power to handle the backdoor and execute further modules. It’s notable that the standard backdoor performance shouldn’t be inherently current inside the binary itself. As a substitute, these capabilities are obtained from the C&C server within the type of PE recordsdata or shellcode. The complete extent of the backdoor’s potential stays unknown with out these further modules, which successfully unlock its true capabilities. An outline of module duties is proven in Desk 4, which incorporates particulars concerning the few recognized modules. Equally, Desk 5 gives an outline of administration duties related to the Executor.
Desk 4. Executor duties – modules
|
Kind |
Description |
|
Unknown |
|
File reader |
|
Unknown |
|
Unknown |
|
Unknown |
|
Unknown |
|
Course of creator |
|
Unknown |
|
Unknown |
|
Data collector |
|
Unknown |
|
Unknown |
Desk 5. Executor duties – administration
|
Kind |
Description |
|
0x6F-0x76 |
Not carried out |
|
0x77 |
Set Executor configuration |
|
0x78 |
Get Executor configuration |
|
0x79-0x7C |
Not carried out |
|
0x7D |
Replace |
|
0x7E |
Give up |
|
0x7F |
Uninstall |
The command that units the Executor configuration can change the:
- undesirable course of lists,
- time threshold of C&C communication failure, and
- time restrict for execution of further modules.
Modules
We managed to acquire three distinctive modules from the C&C server, every akin to a special Executor process sort, as proven in Desk 4. Primarily based on obtainable data, we estimate there are 9 to 14 modules in complete. Because the modules are in actual fact backdoor instructions, they’ve one fundamental operation to execute after which optionally return their output. The modules we obtained are DLLs with one unnamed export (ordinal 1), by which they resolve essential API capabilities and name the primary operate.
When executed, the modules are supplied with an API decision operate, which may resolve Home windows APIs and customized Executor APIs. The Home windows APIs are referenced by a DWORD hash, calculated from the identify of the API and its DLL. Small hash values (<41) are handled specifically, referencing the Executor API operate. The Executor API contains a complete of 39 capabilities which can be accessible to the modules. These capabilities pertain to a wide range of operations, together with:
- file operations,
- encryption and hashing,
- compression,
- PE loading,
- entry Token Impersonation, and
- utility.
In the remainder of this part, we describe the modules that we obtained.
Course of creator
Module 0x69 executes the required command line as a brand new course of and gives the ensuing output again to the Orchestrator. The method might be created underneath a special person, and its execution time might be restricted. Notably, an uncommon Job API is used on this module’s performance.
This module was served with the command line cmd.exe /c tasklist /v.
We assume it serves as an idle command issued robotically, whereas the operators look ahead to one thing attention-grabbing to occur on the compromised laptop.
Data collector
Module 0x6C collects in depth details about the pc by way of WMI queries and passes it again to the Orchestrator. Details about the next is collected:
- working system,
- community adapters,
- put in software program,
- drives,
- providers,
- drivers,
- processes,
- customers,
- atmosphere variables, and
- safety software program.
File reader
Module 0x64 reads the required file and passes the content material again to the Orchestrator. Optionally, it may delete the file after studying.
We noticed this module used to retrieve the sufferer’s Outlook knowledge file
c:Customers<redacted>AppDataLocalMicrosoftOutlookoutlook.ost.
Chain with shellcode downloader
Within the means of investigating Deadglyph, we encountered a doubtful CPL file signed with an expired certificates and no countersignature with a timestamp, which had been uploaded to VirusTotal from Qatar. Upon nearer examination, it grew to become evident that this CPL file functioned as a multistage shellcode downloader, sharing sure code resemblances with Deadglyph. The loading chain is illustrated in Determine 6.
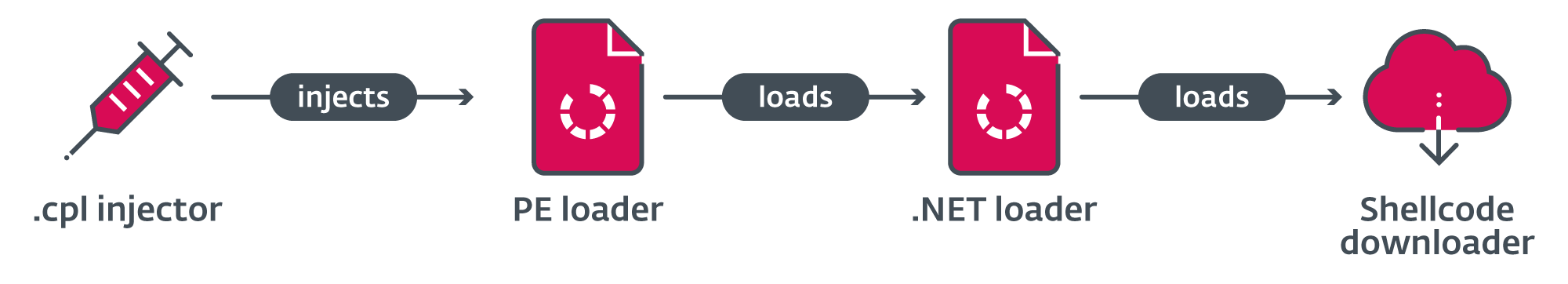
In its preliminary kind, which serves as the primary stage, this file anticipates having a .cpl extension (Management Panel file) and is supposed to be executed by way of a double-click motion. Upon execution on this method, the embedded shellcode undergoes XOR decryption, and the operating processes are checked to determine an acceptable host course of for subsequent injection.
If avp.exe (a Kaspersky endpoint safety course of) is operating, %windirpercentsystem32UserAccountBroker.exe is used. In any other case, the default browser is used. Then, it creates the host course of in a suspended state, injects the shellcode by hijacking its major thread, and resumes the thread.
The second stage, the shellcode, consists of two components. The primary a part of the shellcode resolves API hashes, utilizing the identical distinctive hash calculation method employed in Deadglyph, and decrypts strings with course of names. It begins a self-delete thread tasked with overwriting and subsequently erasing the first-stage file. Following this, the shellcode proceeds to examine the presently energetic processes, concentrating on a safety answer.
If any of the required processes are detected, the shellcode creates a sleeper thread with the bottom precedence (THREAD_PRIORITY_IDLE) and permits it to stay energetic for a length of 60 seconds earlier than terminating its operation. This interval is probably going carried out as a precautionary measure to evade sure detection mechanisms employed by safety options. Lastly, the shellcode proceeds to invoke the execution of the second a part of its code.
The second a part of the shellcode hundreds an embedded PE file with stage three and calls its export with ordinal quantity 1.
The third stage, a DLL, serves as a .NET loader and accommodates the payload in its .rsrc part.
To load the payload, the .NET runtime is initialized. Throughout the .NET initialization, two intriguing strategies are carried out, seemingly supposed to evade Home windows Antimalware Scan Interface (AMSI) scanning:
- The .NET loader quickly hooks the
- It then subtly patches the AmsiInitialize import identify string within the .rdata part of the loaded clr.dll to amsiinitialize.
The fourth stage is a .NET meeting, obfuscated with ConfuserEx, that serves as a shellcode downloader. First, it XOR-decrypts its configuration in XML format from its assets. A beautified model of the extracted configuration is introduced in Determine 7. The configuration entries comprise particulars associated to community communication and blocklisted processes.
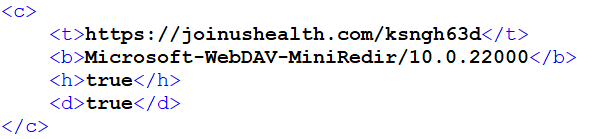
Earlier than continuing, it checks the operating processes towards a listing of blocklisted processes from the configuration. If a match is detected, the execution halts. You will need to notice that within the analyzed occasion, this blocklist wasn’t arrange.
Subsequent, it sends an HTTP GET request to the C&C server to retrieve some shellcode, utilizing parameters specified within the configuration (URL, Person-Agent, and optionally Proxy). Regrettably, throughout our investigation we had been unable to accumulate any shellcode from the C&C server. Nonetheless, we hypothesize that the content material being retrieved might doubtlessly function the installer for Deadglyph.
Following this, the retrieved shellcode is executed inside a newly created thread. After ready till the shellcode thread finishes execution, the shellcode downloader removes all recordsdata positioned within the listing %WINDIRpercentServiceProfilesLocalServiceAppDataLocalTempTfsStoreTfs_DAV.
Lastly, it makes an try to delete itself after a 20-second interval, using the following command, earlier than concluding its operation and exiting:
cmd.exe selection /C Y /N /D Y /T 20 & Del /f /q <current_process_exe_path>
This self-deletion doesn’t make sense on this chain. This is because of the truth that the shellcode downloader is executed inside a browser or system course of after being injected, moderately than working as an unbiased executable. Furthermore, the preliminary file was already deleted by the second stage. This remark means that the shellcode downloader may not be an unique payload of this chain and might also be used individually in different operations.
Conclusion
Now we have found and analyzed a complicated backdoor utilized by the Stealth Falcon group that we have now named Deadglyph. It has an uncommon structure, and its backdoor capabilities are offered by its C&C within the type of further modules. We managed to acquire three of those modules, uncovering a fraction of Deadglyph’s full capabilities.
Notably, Deadglyph boasts a variety of counter-detection mechanisms, together with steady monitoring of system processes and the implementation of randomized community patterns. Moreover, the backdoor is able to uninstalling itself to reduce the probability of its detection in sure circumstances.
Moreover, our investigation led us to the invention of a compelling multistage shellcode downloader chain on VirusTotal. We suspect this downloader chain is probably going leveraged within the set up means of Deadglyph.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Analysis provides personal APT intelligence reviews and knowledge feeds. For any inquiries about this service, go to the ESET Menace Intelligence web page.
IoCs
Recordsdata
|
SHA-1 |
Filename |
Detection |
Description |
|
C40F1F46D230A85F702DAA38CFA18D60481EA6C2 |
pbrtl.dll |
Win64/Deadglyph.A |
Registry Shellcode Loader. |
|
740D308565E215EB9B235CC5B720142428F540DB |
N/A |
Win64/Deadglyph.A |
Deadglyph Backdoor – Executor. |
|
1805568D8362A379AF09FD70D3406C6B654F189F |
N/A |
MSIL/Deadglyph.A |
Deadglyph Backdoor – Orchestrator. |
|
9CB373B2643C2B7F93862D2682A0D2150C7AEC7E |
N/A |
MSIL/Deadglyph.A |
Orchestrator Community module. |
|
F47CB40F6C2B303308D9D705F8CAD707B9C39FA5 |
N/A |
MSIL/Deadglyph.A |
Orchestrator Timer module. |
|
3D4D9C9F2A5ACEFF9E45538F5EBE723ACAF83E32 |
N/A |
Win64/Deadglyph.A.gen |
Course of creator module. |
|
3D2ACCEA98DBDF95F0543B7C1E8A055020E74960 |
N/A |
Win64/Deadglyph.A |
File reader module. |
|
4E3018E4FD27587BD1C566930AE24442769D16F0 |
N/A |
Win64/Deadglyph.A |
Data collector module. |
|
7F728D490ED6EA64A7644049914A7F2A0E563969 |
N/A |
Win64/Injector.MD |
First stage of shellcode downloader chain. |
Certificates
|
Serial quantity |
00F0FB1390F5340CD2572451D95DB1D92D |
|
Thumbprint |
DB3614DAF58D041F96A5B916281EA0DC97AA0C29 |
|
Topic CN |
RHM LIMITED |
|
Topic O |
RHM LIMITED |
|
Topic L |
St. Albans |
|
Topic S |
Hertfordshire |
|
Topic C |
GB |
|
|
rhm@rhmlimited[.]co.uk |
|
Legitimate from |
2021-03-16 00:00:00 |
|
Legitimate to |
2022-03-16 23:59:59 |
C&C servers
|
IP |
Area |
First seen |
Remark |
|
185.25.50[.]60 |
chessandlinkss[.]com |
2021-08-25 |
Deadglyph C&C server. |
|
135.125.78[.]187 |
easymathpath[.]com |
2021-09-11 |
Deadglyph C&C server. |
|
45.14.227[.]55 |
joinushealth[.]com |
2022-05-29 |
Shellcode downloader C&C server. |
MITRE ATT&CK strategies
This desk was constructed utilizing model 13 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Title |
Description |
|
Useful resource Improvement |
Purchase Infrastructure: Domains |
Stealth Falcon has registered domains for C&C servers and to acquire a code-signing certificates. |
|
|
Purchase Infrastructure: Digital Personal Server |
Stealth Falcon has used VPS internet hosting suppliers for C&C servers. |
||
|
Develop Capabilities: Malware |
Stealth Falcon has developed customized malware, together with customized loaders and the Deadglyph backdoor. |
||
|
Receive Capabilities: Code Signing Certificates |
Stealth Falcon has obtained a code-signing certificates. |
||
|
Execution |
Home windows Administration Instrumentation |
Deadglyph makes use of WMI to execute its loading chain. |
|
|
Command and Scripting Interpreter: Home windows Command Shell |
Shellcode downloader makes use of cmd.exe to delete itself. |
||
|
Native API |
A Deadglyph module makes use of CreateProcessW and CreateProcessAsUserW API capabilities for execution. |
||
|
Person Execution: Malicious File |
The shellcode downloader chain requires the person to double-click and execute it. |
||
|
Persistence |
Occasion Triggered Execution: Home windows Administration Instrumentation Occasion Subscription |
The preliminary Deadglyph loader is endured utilizing WMI occasion subscription. |
|
|
Protection Evasion |
Obfuscated Recordsdata or Info |
Deadglyph elements are encrypted. Deadglyph Orchestrator and embedded modules are obfuscated with .NET Reactor. The shellcode downloader is obfuscated with ConfuserEx. |
|
|
Indicator Elimination: File Deletion |
Deadglyph can uninstall itself. The shellcode downloader chain deletes itself and deletes recordsdata within the WebDAV cache. |
||
|
Modify Registry |
Deadglyph shops its configuration and encrypted payload within the registry. |
||
|
Entry Token Manipulation |
Deadglyph can impersonate one other person. |
||
|
Deobfuscate/Decode Recordsdata or Info |
Deadglyph decrypts encrypted strings. The shellcode downloader chain decrypts its elements and configurations. |
||
|
System Binary Proxy Execution: Rundll32 |
The preliminary Deadglyph loader is executed utilizing rundll32.exe. |
||
|
Execution Guardrails: Environmental Keying |
Deadglyph is encrypted utilizing a machine-specific key derived from the system UUID. |
||
|
Impair Defenses: Disable or Modify Instruments |
The shellcode downloader avoids AMSI scanning by patching clr.dll in reminiscence . |
||
|
Reflective Code Loading |
Deadglyph reflectively hundreds its modules utilizing a customized PE loader. |
||
|
Discovery |
System Service Discovery |
A Deadglyph module discovers providers utilizing the WMI question SELECT * FROM Win32_Service. |
|
|
Question Registry |
The shellcode downloader chain queries the registry for the default browser. |
||
|
System Community Configuration Discovery |
A Deadglyph module discovers community adapters utilizing WMI queries SELECT * FROM Win32_NetworkAdapter and SELECT * FROM Win32_NetworkAdapterConfiguration the place InterfaceIndex=%d. |
||
|
System Proprietor/Person Discovery |
A Deadglyph module discovers customers with the WMI question SELECT * FROM Win32_UserAccount. |
||
|
Course of Discovery |
A Deadglyph module discovers processes utilizing WMI question SELECT * FROM Win32_Process. |
||
|
System Info Discovery |
A Deadglyph module discovers system data equivalent to OS model, drives, atmosphere variables, and drivers utilizing WMI queries. |
||
|
Software program Discovery |
A Deadglyph module discovers put in software program utilizing WMI question SELECT * FROM Win32_Product. |
||
|
Software program Discovery: Safety Software program Discovery |
A Deadglyph module discovers safety software program utilizing WMI queries SELECT * FROM AntiVirusProduct, SELECT * FROM AntiSpywareProduct and SELECT * FROM FirewallProduct. The shellcode downloader chain checks operating processes for a safety answer. |
||
|
Assortment |
Information from Native System |
Deadglyph has a module for studying recordsdata. |
|
|
Command and Management |
Software Layer Protocol: Net Protocols |
Deadglyph and the shellcode downloader talk with the C&C server by way of the HTTP protocol. |
|
|
Proxy |
Deadglyph and the shellcode downloader can use HTTP proxy for C&C communication. |
||
|
Encrypted Channel: Symmetric Cryptography |
Deadglyph makes use of AES to encrypt C&C communications. |
||
|
Exfiltration |
Exfiltration Over C2 Channel |
Deadglyph makes use of the C&C channel for exfiltration. |


