On this weblog, lets concentrate on the intersection of psychology and expertise, the place cybercriminals manipulate human psychology by means of digital means to realize their aims.
Our world has turn out to be extra interconnected over time, and this has given rise to a completely new breed of felony masterminds: digital criminals with deep psychological insights who use expertise as the final word battlefield for social engineering actions. Welcome to social engineering – the place your thoughts turns into the battlefield!
Earlier than the digital revolution, social engineering was practiced face-to-face and practitioners of this kind had been generally known as “con males,” no matter gender. As we speak nonetheless, cybercriminals use psychological strategies to trick people into compromising their methods, divulging delicate knowledge, or collaborating in malicious actions unwittingly.
An unsuspecting worker receives an e-mail purporting to be from an official subscription service for software program used at their group, prompting them to log-in as rapidly as doable and keep away from having their account frozen resulting from inactivity. Following a hyperlink on this e-mail main them on to a convincing faux login web page, unknowingly making a gift of their credentials which give a risk actor entry to firm methods and confidential knowledge. This deception was a really perfect instance of Enterprise E-mail Compromise (BEC). An attacker created an pressing phishing e-mail designed to distort worker judgment. There was reconnaissance performed beforehand by risk actors, in order that they already possessed info concerning each an worker’s e-mail tackle and web-based purposes, making the assault grew to become much more efficient.
Social engineering is likely one of the major methods criminals use of their makes an attempt to assault our methods. From an info safety perspective, social engineering is using manipulative psychological techniques and deception to commit fraud. The aim of those techniques is to ascertain some degree of belief to persuade the unsuspecting sufferer handy over delicate or confidential info.
Listed below are some books that supply a spread of views and insights into the world of social engineering, from the psychology behind it to sensible defenses in opposition to it. Studying them can assist you higher perceive the techniques utilized by social engineers and shield your self and your group.
1. Affect: The Psychology of Persuasion” by Robert B. Cialdini
Robert Cialdini’s traditional e book explores the six key rules of affect: reciprocity, dedication and consistency, social proof, liking, authority, and shortage. Whereas not solely targeted on social engineering, it supplies beneficial insights into the psychology of persuasion which are extremely related to understanding and defending in opposition to social engineering techniques.
2. “The Artwork of Deception: Controlling the Human Ingredient of Safety” by Kevin D. Mitnick
A former hacker turned cybersecurity guide, delves into the artwork of deception and social engineering. He shares real-life examples of social engineering assaults and supplies sensible recommendation on shield your self and your group from such threats.
3. “Ghost within the Wires: My Adventures because the World’s Most Wished Hacker” by Kevin D. Mitnick On this autobiography, Kevin Mitnick recounts his private experiences as a hacker and social engineer. He supplies an interesting insider’s perspective on the techniques utilized by hackers to control individuals and methods, shedding mild on the world of cybercrime and social engineering.
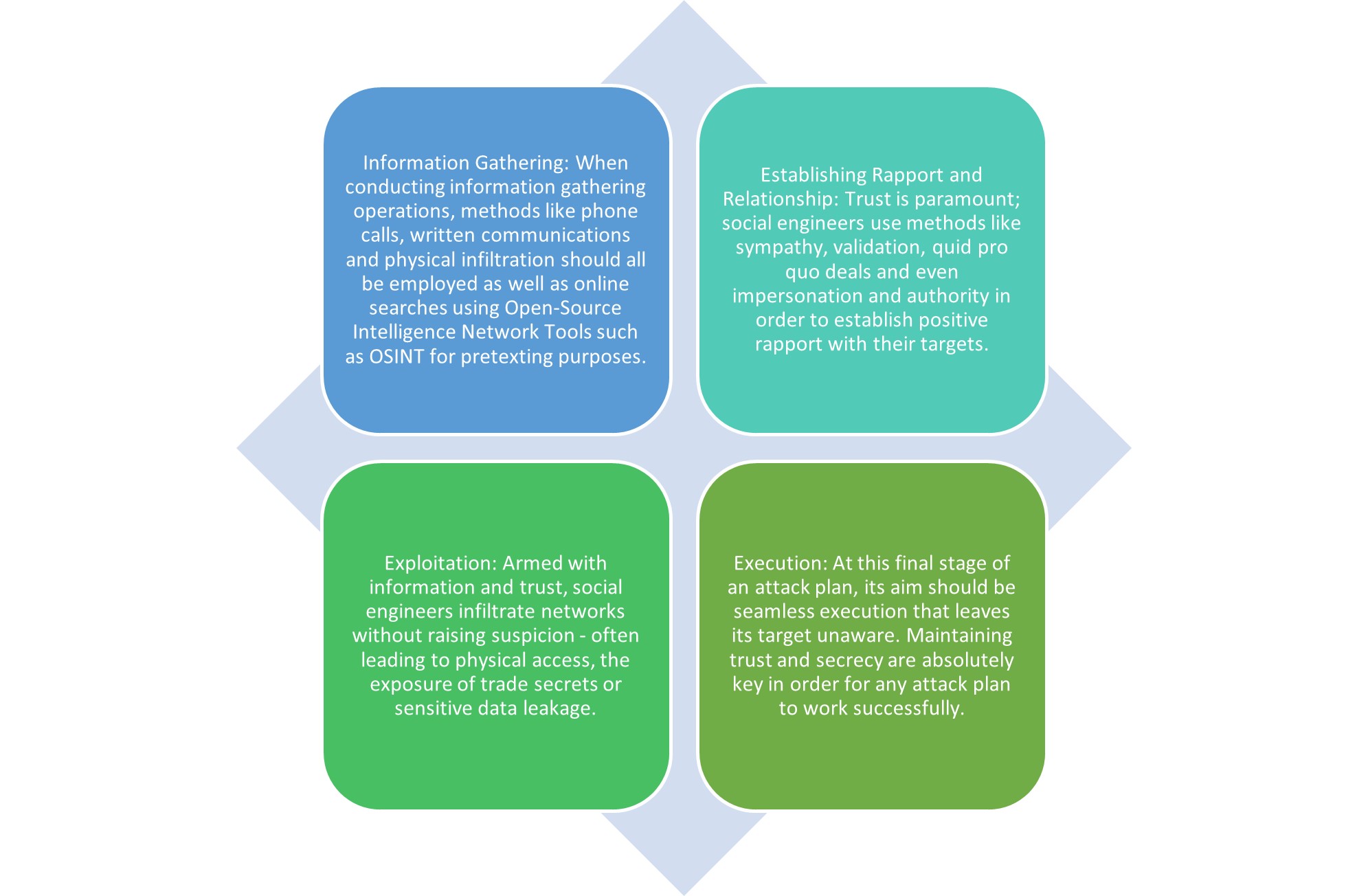
4. “Social Engineering: The Artwork of Human Hacking” by Christopher Hadnagy Abstract: A complete information to social engineering methods and methods. It covers varied facets of human hacking, together with info gathering, constructing rapport, and exploiting psychological vulnerabilities. It is a wonderful useful resource for these seeking to perceive and defend in opposition to social engineering assaults.
5. “No Tech Hacking: A Information to Social Engineering, Dumpster Diving, and Shoulder Browsing” by Johnny Lengthy, Jack Wiles, and Scott Pinzon
Explores low-tech and non-digital strategies of social engineering, together with dumpster diving, bodily intrusion, and eavesdropping. It supplies insights into how attackers can exploit bodily vulnerabilities and affords countermeasures to guard in opposition to such techniques.
6. “Phishing Darkish Waters: The Offensive and Defensive Sides of Malicious Emails” by Christopher Hadnagy and Michele Fincher
Focusing particularly on email-based social engineering assaults, this e book examines phishing methods intimately. It supplies insights into the techniques utilized by attackers to trick people into revealing delicate info and affords steering on defend in opposition to phishing threats.
7. “The Confidence Recreation: Why We Fall for It . . . Each Time” by Maria Konnikova
Whereas not completely about social engineering, this e book delves into the psychology of deception and the the reason why individuals typically fall sufferer to scams and cons. It supplies beneficial insights into the vulnerabilities of human cognition and habits that social engineers exploit.
Cyberattacks more and more rely upon human interplay for profitable execution. Risk actors use psychology to take advantage of vulnerabilities and compromise methods. With enough consciousness, coaching, insurance policies, and procedures organizations can shield themselves in opposition to these insidious assaults by conserving conscious of rising vulnerabilities by means of coaching periods, insurance policies, and procedures in addition to their common evaluation by expert personnel.