
A set of 21 newly found vulnerabilities affect Sierra OT/IoT routers and threaten crucial infrastructure with distant code execution, unauthorized entry, cross-site scripting, authentication bypass, and denial of service assaults.
The issues found by Forescout Vedere Labs have an effect on Sierra Wi-fi AirLink mobile routers and open-source parts like TinyXML and OpenNDS (open Community Demarcation Service).
AirLink routers are extremely regarded within the discipline of business and mission-critical functions as a consequence of high-performance 3G/4G/5G and WiFi and multi-network connectivity.
Varied fashions are utilized in complicated situations like passenger WiFi in transit programs, automobile connectivity for emergency companies, long-range gigabit connectivity to discipline operations, and numerous different performance-intensive duties.
Forescout says Sierra routers are present in authorities programs, emergency companies, power, transportation, water and wastewater services, manufacturing models, and healthcare organizations.
Flaws and affect
Forescout’s researchers found 21 new vulnerabilities in Sierra AirLink mobile routers and the TinyXML and OpenNDS parts, that are a part of different merchandise, too.
Solely one of many safety points has been rated crucial, eight of them obtained a excessive severity rating, and a dozen current a medium danger.
Probably the most noteworthy vulnerabilities are summarized beneath:
- CVE-2023-41101 (Distant Code Execution in OpenDNS – crucial severity rating of 9.6)
- CVE-2023-38316 (Distant Code Execution in OpenDNS – excessive severity rating of 8.8)
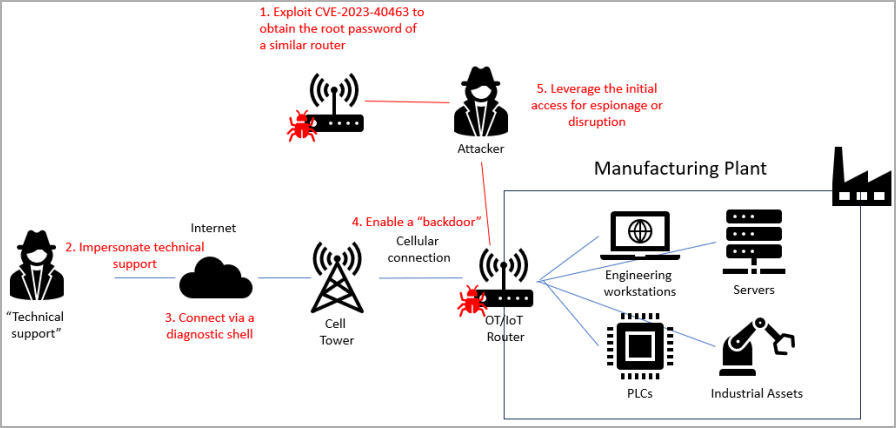
- CVE-2023-40463 (Unauthorized Entry in ALEOS – excessive severity rating of 8.1)
- CVE-2023-40464 (Unauthorized Entry in ALEOS – excessive severity rating of 8.1)
- CVE-2023-40461 (Cross Website Scripting in ACEmanager – excessive severity rating of 8.1)
- CVE-2023-40458 (Denial of Service in ACEmanager – excessive severity rating of 7.5)
- CVE-2023-40459 (Denial of Service in ACEmanager – excessive severity rating of 7.5)
- CVE-2023-40462 (Denial of Service in ACEmanager associated to TinyXML – excessive severity rating of 7.5)
- CVE-2023-40460 (Cross Website Scripting in ACEmanager – excessive severity rating of 7.1)
For no less than 5 of the above flaws, attackers don’t require authentication to take advantage of them. For a number of others affecting OpenNDS, authentication is probably going not required, as widespread assault situations contain purchasers making an attempt to hook up with a community or service.
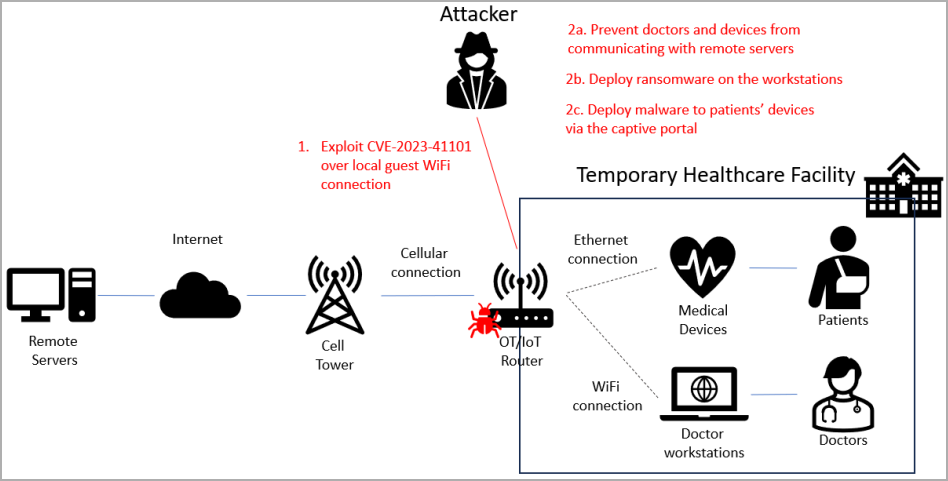
Based on the researchers, an attacker may exploit a few of the vulnerabilities “to take full management of an OT/IoT router in crucial infrastructure.” The compromise may result in community disruption, allow espionage, or transfer laterally to extra vital property, and malware deployment.
“Other than human attackers, these vulnerabilities will also be utilized by botnets for computerized propagation, communication with command-and-control servers, in addition to performing DoS assaults,” the researchers clarify.
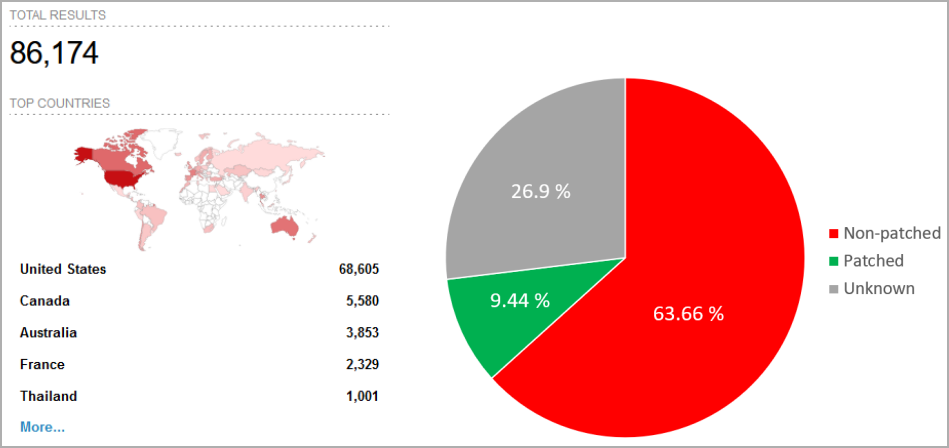
After working a scan on Shodan search enging for internet-connected gadgets, Forescout researchers discovered over 86,000 AirLink routers uncovered on-line in crucial organizations engaged in energy distribution, automobile monitoring, waste administration, and nationwide well being companies.
About 80% of the uncovered programs are in the US, adopted by Canada, Australia, France, and Thailand.
Of these, fewer than 8,600 have utilized patches to vulnerabilities disclosed in 2019, and greater than 22,000 are uncovered to man-in-the-middle assaults as a consequence of utilizing a default SSL certificates.
Remediation recommendation
The advisable motion for directors is to improve to the ALEOS (AirLink Embedded Working System) model 4.17.0, which addresses all flaws, or no less than ALEOS 4.9.9, which accommodates all fixes aside from these impacting OpenNDS captive portals that set a barrier between the general public web and a neighborhood space community.
The OpenNDS venture has additionally launched safety updates for the vulnerabilities impacting the open-source venture, with model 10.1.3.
Observe that TinyXML is now abandonware, so there can be no fixes for the CVE-2023-40462 vulnerability that impacts the venture.
Forescout additionally recommends taking the next extra actions for enhanced safety:
- Change default SSL certificates in Sierra Wi-fi routers and comparable gadgets.
- Disable or limit non-essential companies like captive portals, Telnet, and SSH.
- Implement an online software firewall to guard OT/IoT routers from internet vulnerabilities.
- Set up an OT/IoT-aware IDS to watch exterior and inner community visitors for safety breaches.
Forescout has launched a technical report that explains the vulnerabilities and the circumstances that enable exploiting them.
Based on the corporate, menace actors are more and more concentrating on routers and community infrastructure environments, launching assaults with customized malware that use the gadgets for persistence and espionage functions.
For cybercriminals, routers are often a way to proxy malicious visitors or to extend the measurement of their botnet.

