AT&T Cybersecurity is dedicated to offering thought management that will help you strategically plan for an evolving cybersecurity panorama. Our 2023 AT&T Cybersecurity Insights™ Report: Edge Ecosystem is now out there. It describes the frequent traits of an edge computing setting, the highest use circumstances and safety developments, and key suggestions for strategic planning.
That is the twelfth version of our vendor-neutral and forward-looking report. Over the past 4 years, the annual AT&T Cybersecurity Insights Report has targeted on edge migration. Previous experiences have documented how we
This 12 months’s report reveals how the sting ecosystem is maturing together with our steerage on adapting and managing this new period of computing.
Watch the webcast to listen to extra about our findings.
The strong quantitative subject survey reached 1,418 professionals in safety, IT, utility growth, and line of enterprise from all over the world. The qualitative analysis tapped material consultants throughout the cybersecurity business.
On the onset of our analysis, we got down to discover the next:
- Momentum of edge computing available in the market.
- Collaboration approaches to connecting and securing the sting ecosystem.
- Perceived danger and good thing about the frequent use circumstances in every business surveyed.
The outcomes deal with frequent edge use circumstances in seven vertical industries – healthcare, retail, finance, manufacturing, vitality and utilities, transportation, and U.S. SLED and delivers actionable recommendation for securing and connecting an edge ecosystem – together with exterior trusted advisors. Lastly, it examines cybersecurity and the broader edge ecosystem of networking, service suppliers, and high use circumstances.
As with every piece of major analysis, we discovered some shocking and a few not-so-surprising solutions to those three broad questions.
Edge computing has expanded, creating a brand new ecosystem
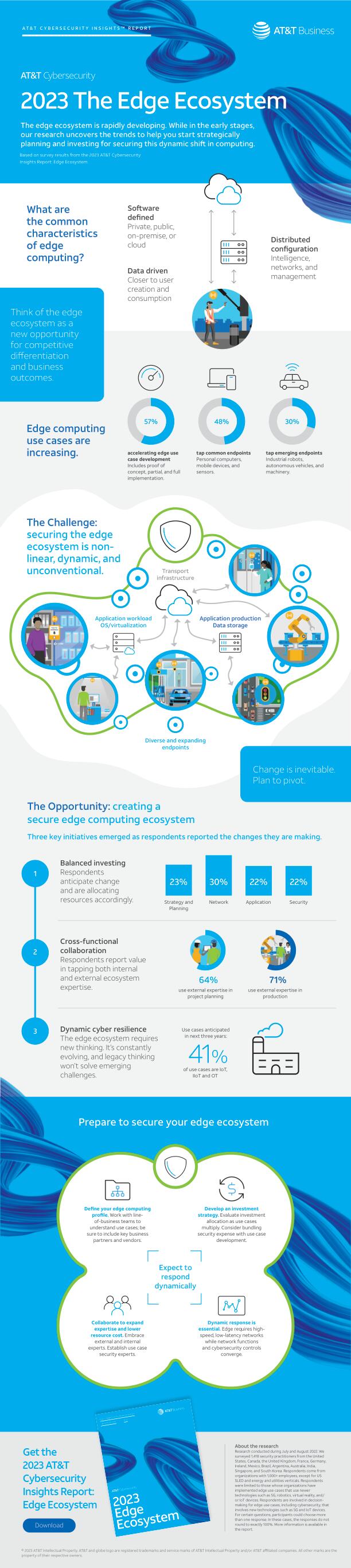
As a result of our survey targeted on leaders who’re utilizing edge to resolve enterprise issues, the analysis revealed a set of frequent traits that respondents agreed outline edge computing.
- A distributed mannequin of administration, intelligence, and networks.
- Purposes, workloads, and internet hosting nearer to customers and digital belongings which can be producing or consuming the information, which may be on-premises and/or within the cloud.
- Software program-defined (which might imply the dominant use of personal, public, or hybrid cloud environments; nevertheless, this doesn’t rule out on-premises environments).
Understanding these frequent traits are important as we transfer to a fair additional democratized model of computing with an abundance of related IoT units that may course of and ship knowledge with velocity, quantity, and selection, not like something we’ve beforehand seen.
Enterprise is embracing the worth of edge deployments
The first use case of industries we surveyed developed from the earlier 12 months. This exhibits that companies are seeing optimistic outcomes and proceed to spend money on new fashions enabled by edge computing.
|
Business |
2022 Major Use Case |
2023 Major Use Case |
|
Healthcare |
Client Digital Care |
Tele-emergency Medical Providers |
|
Manufacturing |
Video-based High quality Inspection |
Good Warehousing |
|
Retail |
Misplaced Prevention |
Actual-time Stock Administration |
|
Power and Utilities |
Distant Management Operations |
Clever Grid Administration |
|
Finance |
Concierge Providers |
Actual-time Fraud Safety |
|
Transportation |
n/a |
Fleet Monitoring |
|
U.S. SLED |
Public Security and Enforcement |
Constructing Administration |
A full 57% of survey respondents are in proof of idea, partial, or full implementation phases with their edge computing use circumstances.
Some of the pleasantly shocking findings is how organizations are investing in safety for edge. We requested survey members how they had been allocating their budgets for the first edge use circumstances throughout 4 areas – technique and planning, community, safety, and purposes.
The outcomes present that safety is clearly an integral a part of edge computing. This balanced funding technique exhibits that the much-needed safety for ephemeral edge purposes is a part of the broader plan.
Edge mission budgets are notably almost balanced throughout 4 key areas:
- Community – 30%
- Total technique and planning – 23%
- Safety – 22%
- Purposes – 22%
A strong companion ecosystem helps edge complexity
Throughout all industries, exterior trusted advisors are being referred to as upon as crucial extensions of the group. In the course of the edge mission planning section, 64% are utilizing an exterior companion. In the course of the manufacturing section, that very same quantity will increase to 71%. These findings reveal that organizations are searching for assist as a result of the complexity of edge calls for greater than a do-it-yourself method.
A shock discovering comes within the type of the altering assault floor and altering assault sophistication. Our knowledge exhibits that DDoS (Distributed Denial of Service) assaults at the moment are the highest concern (when inspecting the information within the combination vs. by business). Surprisingly, ransomware dropped to eighth place out of eight in assault kind.
The qualitative evaluation factors to an abundance of organizational spending on ransomware prevention over the previous 24 months and enthusiasm for ransomware containment. Nonetheless, ransomware criminals and their assaults are relentless. Further qualitative evaluation suggests cyber adversaries could also be biking various kinds of assaults. It is a worthwhile subject to debate in your group. What sorts of assaults concern your group essentially the most?
Constructing resilience is crucial for profitable edge integration
Resilience is about adapting shortly to a altering scenario. Collectively, resilience and safety deal with danger, assist enterprise wants, and drive operational effectivity at every stage of the journey. As use circumstances evolve, resilience features significance, and the aggressive benefit that edge purposes present may be fine-tuned. Future evolution will contain extra IoT units, quicker connectivity and networks, and holistic safety tailor-made to hybrid environments.
Our analysis finds that organizations are fortifying and future-proofing their edge architectures and including cyber resilience as a core pillar. Empirically, our analysis exhibits that because the variety of edge use circumstances in manufacturing grows, there’s a robust want and want to extend safety for endpoints and knowledge. For instance, the usage of endpoint detection and response grows by 12% as use circumstances go from ideation to full implementation.
Maturity in understanding edge use circumstances and what it takes to guard actively is a journey that each group will undertake.
Key takeaways
Chances are you’ll not notice you’ve already encountered edge computing – whether or not it’s by way of a tele-medicine expertise, discovering out there parking locations in a public construction, or working in a sensible constructing. Edge is bringing us to a digital-first world, wealthy with new and thrilling prospects.
By embracing edge computing, you’ll assist your group achieve essential, and sometimes aggressive enterprise benefits. This report is designed that will help you begin and additional the dialog. Use it to develop a strategic plan that features these key growth areas.
- Begin growing your edge computing profile. Work with inner line-of-business groups to know use circumstances. Embody key enterprise companions and distributors to establish initiatives that impression safety.
- Develop an funding technique. Bundle safety investments with use case growth. Consider funding allocation. The elevated enterprise alternative of edge use circumstances ought to embody a safety price range.
- Align assets with rising safety priorities. Use collaboration to increase experience and decrease useful resource prices. Think about creating edge computing use case consultants who assist the safety group keep on high of rising use circumstances.
- Put together for ongoing, dynamic response. Edge use circumstances quickly evolve as soon as they present worth. Use circumstances require high-speed, low-latency networks as community capabilities and cybersecurity controls converge.
A particular due to our contributors for his or her continued steerage on this report
A report of this scope and magnitude comes collectively by way of a collaborative effort of leaders within the cybersecurity market.
Thanks to our 2023 AT&T Cybersecurity Insights Report contributors!
To assist begin or advance the dialog about edge computing in your group, use the infographic beneath as a information.