To place community operations in context, analysts want to trace the software program working on the group’s community. This monitoring entails not solely holding tabs on which functions are working, however whether or not these functions are being frequently up to date in variations and patches. Many safety checklists advocate holding software program present on relevant current variations and patches. Such suggestions, together with RFC 2196, underneath “ongoing actions,” have been in place for many years. DHS/CISA suggestions on defending in opposition to present ransomware threats emphasize holding your pc patches updated. Some organizations push updates onto inner purchasers and servers, however others use vendor-supported replace providers. This weblog put up presents an analytic for monitoring software program updates from official vendor places.
There are a selection of ways in which monitoring updates helps to tell community safety efforts. Utilizing vendor-supported replace providers could require purchasers and servers to ballot designated obtain websites for probably the most present updates. By figuring out which hosts are receiving updates, analysts can observe compliance with the group’s replace insurance policies. Monitoring which updates the purchasers and servers are receiving additionally helps affirm the software program configuration on these gadgets, which in flip could feed into the community vulnerability administration course of. Lastly, monitoring the dates at which updates happen helps to establish how present the configured software program is on the group’s purchasers and servers, which can give a way for which vulnerabilities could also be of concern in defending the community.
After we all know why to trace updates, analysts can decide what info is desired from the monitoring. This weblog put up assumes analysts need to observe anticipated updates to software program, as a part of managing and safety the community. Understanding the replace server, whether or not it was polled or downloaded to which consumer or server, and at what time the contact was made to the replace server all present a helpful foundation for this community administration effort. For different functions, alternate info could also be required (e.g., if analysts want to trace the bandwidth consumed by the replace course of, then figuring out length and byte quantity of the contacts with the replace server can be essential). The analytic mentioned beneath is particularly to establish which inner hosts are receiving updates from which supply and over what time interval.
Overview of the Analytic for Monitoring Software program Updates
The analytic lined on this weblog posting assumes that the replace places are identified by the analysts. Frequent URLs for replace places embrace:
Analysts could construct a extra site-specific checklist by way of dialogue with the community directors as to which replace places are allowed by way of firewalls and different defenses.
The strategy taken on this analytic is to make use of the checklist of replace places and establish transfers of information into the interior community related to these places. The checklist of URLs could require conversion by isolating the host portion of it and resolving the IP addresses concerned. These addresses can then be encapsulated as a textual content file, an IP set file, or as an SQL desk, relying on the tooling concerned. The output of this analytic is an inventory of inner addresses and a abstract of the contacts by the replace websites.
A number of completely different instruments can be utilized to trace software program updates. Packet seize and evaluation might be used, however typically the amount of information and the give attention to packet element make it time consuming to combination and extract the data to supply the abstract. Intrusion detection system (IDS) guidelines, both for host or network-based IDS, might be established to problem an alert every time an replace is made, however such alerts are sometimes onerous to federate throughout a medium or large-size community infrastructure and require filtering and post-processing to offer the abstract info.
Logs, both from purchasers, servers, or safety gadgets, similar to firewalls, might comprise data of replace contacts. Once more, nonetheless, a time-consuming course of can be wanted to filter, federate, and combination the logs earlier than processing them to establish the abstract info. This weblog describes use of community circulate data (which summarize community connections) and making use of them in a retrospective evaluation (by way of the SiLK software suite), streaming evaluation (by way of Evaluation Pipeline), and thru an SQL database.
Implementing the Analytic by way of SiLK
Determine 1 presents a sequence of SiLK instructions (SEI’s suite of instruments that retrospectively analyze visitors expressed as community circulate data) to implement an analytic that tracks software program updates. The rwfilter name isolates visitors inbound on identified internet ports (80, 8080, or 443) to the monitored community from one of many recognized replace IP addresses, contemplating solely flows representing greater than a protocol handshake (i.e., these with three packets or extra: two for the protocol handshake and not less than one to switch knowledge). The rwuniq name produces a abstract for every vacation spot (inner) deal with displaying the timing of the visitors. The decision to move abbreviates the output for this weblog and wouldn’t be included for manufacturing use.
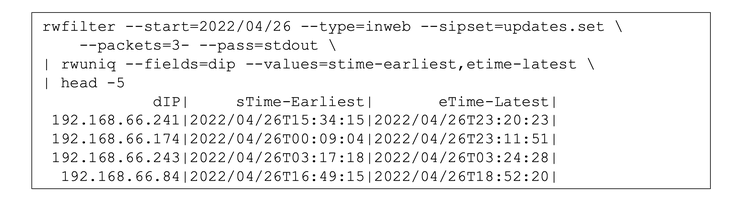
Determine 1: SiLK Instructions and Outcomes
The leads to Determine 1 present 4 inner hosts being contacted (solely 4, resulting from head’s trimming of output). Of those 4, the primary two present contacts over greater than six hours, which is widespread for repeated polling for updates throughout a workday. The latter two present contacts over comparatively temporary intervals of time (7 minutes and a couple of hours, respectively), which might require extra investigation to find out if these belongings have been solely linked briefly or if the contacts recognized aren’t truly replace visitors. Since this analytic makes use of solely IP deal with and visitors sort, false positives (i.e., visitors being categorized as updates when in fact it’s not) could also be anticipated to happen sometimes. One methodology of coping with the false positives can be including an rwfilter name after the preliminary one, which might use quite a lot of traits to exclude the falsely recognized data.
Implementing the Analytic by way of Evaluation Pipeline
Determine 2 exhibits the analytic carried out as a configuration for Evaluation Pipeline. In distinction to the SiLK model described above, the pipeline analytic identifies replace servers utilizing hostnames, transport protocols, and ports, relatively than IP addresses. There are separate lists of hostnames for HTTP and HTTPS replace servers. Because the hostnames from the replace documentation comprise wildcards, these lists have to be structured to match the domains, in addition to hosts.
Evaluation Pipeline helps this functionality by including a header line in every checklist that flags it as being in DNS format (##format:dns). The primary filter, httpHostDetectUpdate_filter, makes use of the checklist for HTTP servers and matches them in opposition to the deep packet inspection (DPI)-derived hostname parsed from the HTTP visitors, utilizing the prolonged circulate fields which might be populated by YAF. This filter solely considers (1) data from one of many servers to the monitored community’s inner addresses and (2) visitors to the widespread internet transport port (TCP/80) with three packets or extra (once more, excluding visitors consisting solely of protocol overhead).
The second filter, sslServerDetectUpdate_filter, follows the same course of however makes use of the sslServerName matched in opposition to the HTTPS server checklist and the HTTPS widespread port (TCP/443). The output of those two filters is mixed within the third filter, updateDetect_filter, which in flip is invoked by the interior filter, updateDetect_intfilter, to assemble a day by day checklist of addresses on the monitored community which have contacts from the replace servers. This checklist is reported to a file by the checklist configuration, updateDetect_list. Evaluation Pipeline produces solely this set file as an output, so no show is proven in Determine 2.

Determine 2: Evaluation pipeline configuration for Analytic
Implementing the Analytic by way of SQL
Determine 3 supplies an implementation of the analytic in SQL-like notation. This notional instance assumes that IPFIX (an Web-standard circulate document format described in RFC7011) info components are current in a desk of data, known as flowData, and that the checklist of identified replace hosts is current in a separate desk known as updateTable and having IP deal with and port info in that desk. The internal SELECT isolates related info components for data the place the supply deal with matches an replace server, and the port and protocol additionally match, contemplating solely data for flows aggregating greater than three packets. The outer SELECT assertion produces a abstract much like the output of the SiLK analytic in Determine 1.
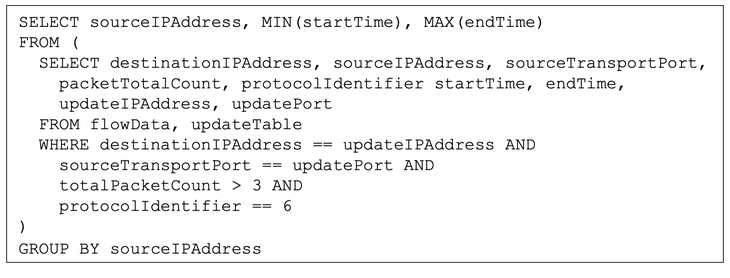
Determine 3: Notional SQL implementation of Analytic
Understanding Software program Adjustments
Whichever type of tooling is used, analysts typically want an understanding of the software program adjustments to their networks, even the anticipated ones. The analytic introduced on this weblog posting supplies a primary step at this understanding, though over time analysts ought to revise and specialize it to mirror their wants. A number of of the next potential causes might have additional investigation if the noticed updates lack most of the anticipated ones:
- There was a change within the replace servers, and the checklist utilized in monitoring have to be up to date. (Trace: see if different inner belongings are being up to date from the server in query)
- There was a change within the inner host: both taken out of service or had its software program reconfigured. (Trace: see what different exercise is current for the interior host)
- The interior host’s administrator or an attacker has disabled the replace service, which is often opposite to safety coverage. (Trace: contact the approved administrator for the interior host)
- There’s a community connectivity problem with respect to the interior host or the replace server. (Trace: validate the connectivity concerned)
- Different components have interfered with the replace course of.
The impression of those causes on the community safety will range relying on the vary of belongings affected and the criticality of these belongings, however a number of the causes could demand instant response.



