A brand new wave of a cellular surveillance marketing campaign has been noticed concentrating on the Uyghur group as a part of a long-standing spy ware operation energetic since at the very least 2015, cybersecurity researchers disclosed Thursday.
The intrusions, initially attributed to a menace actor named Scarlet Mimic again in January 2016, is claimed to have encompassed 20 completely different variants of the Android malware, which have been disguised as e book, footage, and an audio model of the Quran.
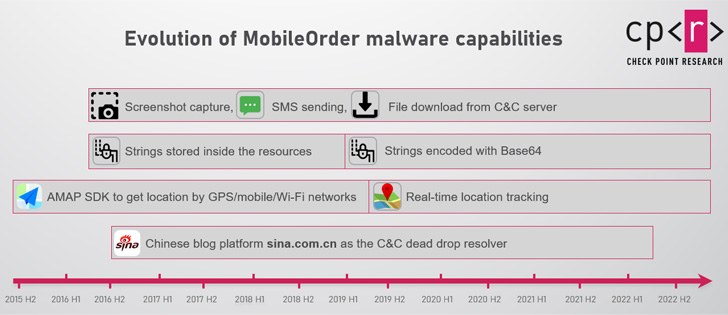
The malware, whereas comparatively unsophisticated from a technical standpoint, comes with in depth capabilities to steal delicate information from an contaminated machine, ship SMS messages on the sufferer’s behalf, make telephone calls, and observe their areas.
Moreover, it permits the recording of incoming and outgoing telephone calls in addition to surrounding audio.
“All this makes it a robust and harmful surveillance software,” Israeli cybersecurity agency Verify Level mentioned in a technical deepdive, calling the spy ware MobileOrder.
It is price noting that part of the marketing campaign was not too long ago disclosed by researchers from the MalwareHunterTeam and Cyble, by which a e book written by the exiled Uyghur chief Dolkun Isa was used as a lure to ship the malware.
Verify Level mentioned it noticed MobileOrder artifacts within the wild proper from 2015 to mid-August 2022, except 2021, when none have been detected.
Assault campaigns possible contain using social engineering techniques to trick unsuspecting victims into launching malicious purposes that reference seemingly innocuous paperwork, pictures, and audio recordsdata.
These apps include a wide range of baits, together with a PDF about guerrilla warfare and footage associated to the deployment of paramilitary forces in Ürümqi, the capital of the Xinjiang Uyghur Autonomous Area, within the aftermath of the lethal April 2014 assault.
Opening the rogue app, in flip, launches a decoy doc designed to distract the goal from noticing the malicious actions within the background.
“A number of the variations additionally ask for Gadget Admin and root entry, which not solely provides the malware full entry to the machine, but additionally prevents the sufferer from simply uninstalling the applying,” the researchers mentioned.
Different options supported by MobileOrder embody executing a distant shell and even dropping further Android Package deal (APK) recordsdata.
The marketing campaign’s attribution to Scarlet Mimic, per Verify Level, stems from clear code overlaps, shared infrastructure, and the identical victimology patterns.
Moreover, the continuing use of MobileOrder alerts a shift in assault vector from desktop to cellular surveillance, what with the actor beforehand linked to a Home windows malware known as Psylo Trojan.
Whereas it isn’t clear which of those assaults all through the previous seven years have been profitable, the actual fact that the malware authors are persevering with to deploy the spy ware is a sign that a few of these efforts have paid off.
“The persistence of the marketing campaign, the evolution of the malware and the persistent concentrate on concentrating on particular populations point out that the group’s operations over time are profitable to some extent,” Verify Level mentioned.