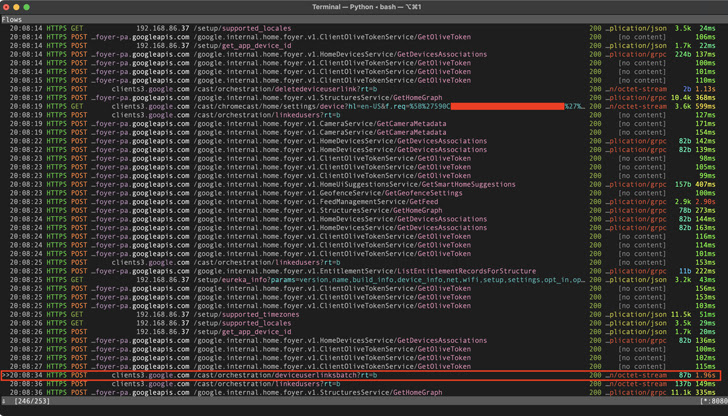
A safety researcher was awarded a bug bounty of $107,500 for figuring out safety points in Google Residence sensible audio system that might be exploited to put in backdoors and switch them into wiretapping units.
The failings “allowed an attacker inside wi-fi proximity to put in a ‘backdoor’ account on the machine, enabling them to ship instructions to it remotely over the web, entry its microphone feed, and make arbitrary HTTP requests throughout the sufferer’s LAN,” the researcher, who goes by the title Matt, disclosed in a technical write-up printed this week.
In making such malicious requests, not solely might the Wi-Fi password get uncovered, but in addition present the adversary direct entry to different units linked to the identical community. Following accountable disclosure on January 8, 2021, the problems have been remediated by Google in April 2021.
The issue, in a nutshell, has to do with how the Google Residence software program structure may be leveraged so as to add a rogue Google consumer account to a goal’s dwelling automation machine.
In an assault chain detailed by the researcher, a risk actor seeking to listen in on a sufferer can trick the person into putting in a malicious Android app, which, upon detecting a Google Residence machine on the community, points stealthy HTTP requests to hyperlink an attacker’s account to the sufferer’s machine.
Taking issues a notch increased, it additionally emerged that, by staging a Wi-Fi deauthentication assault to drive a Google Residence machine to disconnect from the community, the equipment may be made to enter a “setup mode” and create its personal open Wi-Fi community.
The risk actor can subsequently hook up with the machine’s setup community and request particulars like machine title, cloud_device_id, and certificates, and use them to hyperlink their account to the machine.
Whatever the assault sequence employed, a profitable hyperlink course of allows the adversary to reap the benefits of Google Residence routines to show down the quantity to zero and name a particular cellphone quantity at any given cut-off date to spy on the sufferer by the machine’s microphone.
“The one factor the sufferer could discover is that the machine’s LEDs flip strong blue, however they’d in all probability simply assume it is updating the firmware or one thing,” Matt stated. “Throughout a name, the LEDs don’t pulse like they usually do when the machine is listening, so there isn’t a indication that the microphone is open.”
Moreover, the assault may be prolonged to make arbitrary HTTP requests throughout the sufferer’s community and even learn information or introduce malicious modifications on the linked machine that might get utilized after a reboot.
This isn’t the primary time such assault strategies have been devised to covertly eavesdrop on potential targets by voice-activated units.
In November 2019, a bunch of lecturers disclosed a way known as Mild Instructions, which refers to a vulnerability of MEMS microphones that allows attackers to remotely inject inaudible and invisible instructions into fashionable voice assistants like Google Assistant, Amazon Alexa, Fb Portal, and Apple Siri utilizing gentle.