
The APT37 risk group makes use of a brand new evasive ‘M2RAT’ malware and steganography to focus on people for intelligence assortment.
APT37, also called ‘RedEyes’ or ‘ScarCruft,’ is a North Korean cyber espionage hacking group believed to be state-supported.
In 2022, the hacking group was seen exploiting Web Explorer zero-days and distributing a large assortment of malware towards focused entities and people.
For instance, the risk actors focused EU-based organizations with a brand new model of their cell backdoor named ‘Dolphin,’ deployed a customized RAT (distant entry trojan) known as ‘Konni,’ and focused U.S. journalists with a highly-customizable malware named ‘Goldbackdoor.’
In a new report launched right this moment by AhnLab Safety Emergency response Heart (ASEC), researchers clarify how APT37 is now utilizing a brand new malware pressure known as ‘M2RAT’ that makes use of a shared reminiscence part for instructions and information exfiltration and leaves only a few operational traces on the contaminated machine.
Begins with phishing
The current assaults noticed by ASEC began in January 2023, when the hacking group despatched phishing emails containing a malicious attachment to their targets.
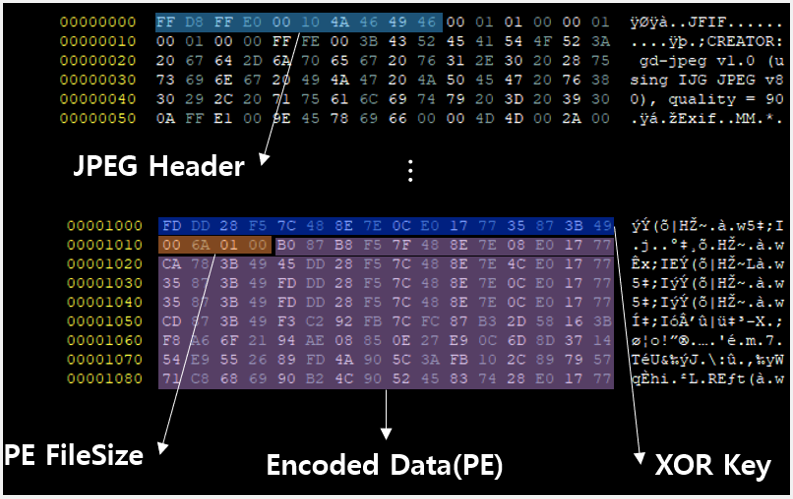
Opening the attachment triggers the exploitation of an previous EPS vulnerability (CVE-2017-8291) within the Hangul phrase processor generally utilized in South Korea. The exploit will trigger shellcode to run on a sufferer’s pc that downloads and executes a malicious executed saved inside a JPEG picture.
This JPG picture file makes use of steganography, a method that enables hiding code inside information, to stealthily introduce the M2RAT executable (“lskdjfei.exe”) onto the system and inject it into “explorer.exe.”
For persistence on the system, the malware provides a brand new worth (“RyPO”) within the “Run” Registry key, with instructions to execute a PowerShell script by way of “cmd.exe.” This similar command was additionally seen in a 2021 Kaspersky report about APT37.
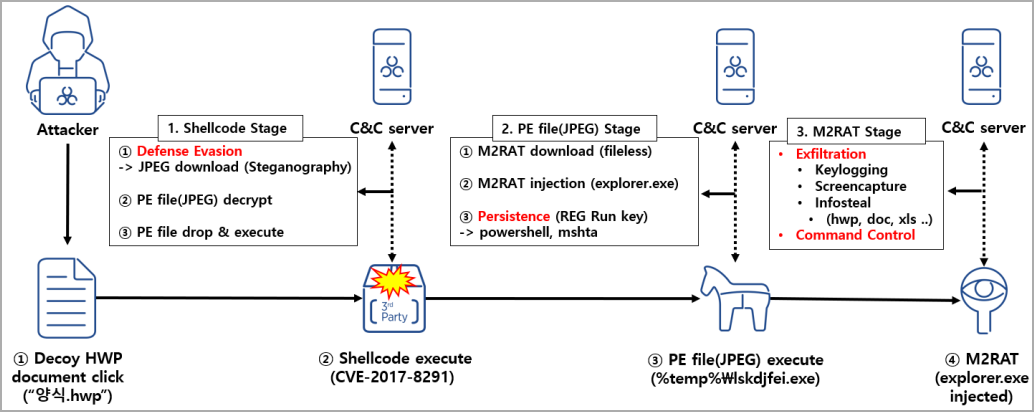
M2RAT steals from Home windows and telephones
The M2RAT backdoor acts as a primary distant entry trojan that performs keylogging, information theft, command execution, and the taking of screenshots from the desktop.
The screenshot-snapping perform is activated periodically and works autonomously with out requiring a particular operator command.
The malware helps the next instructions, which gather info from the contaminated system after which ship it again to the C2 server for the attackers to evaluate.
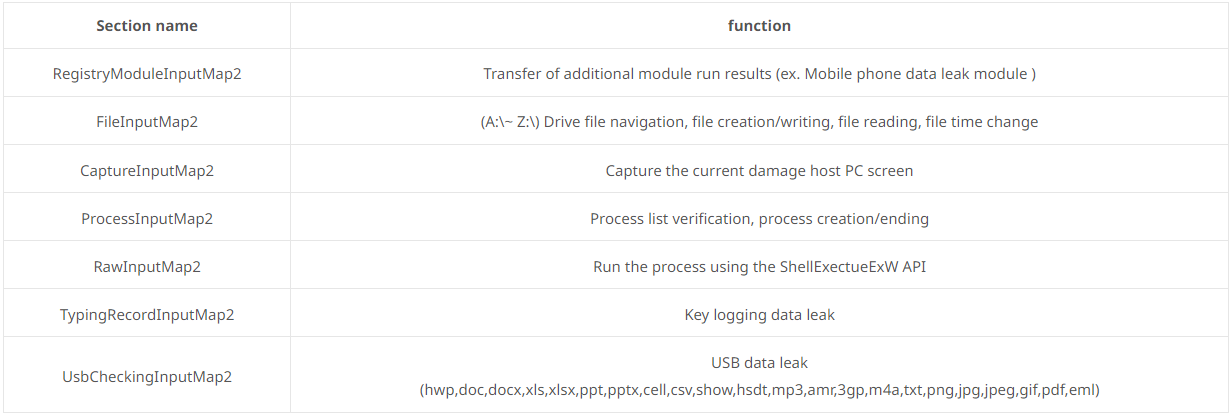
The malware’s skill to scan for moveable gadgets related to the Home windows pc, equivalent to smartphones or tablets, is especially fascinating.
If a conveyable system is detected, it is going to scan the system’s contents for paperwork and voice recording information and, if discovered, copy them to the PC for exfiltration to the attacker’s server.
Earlier than exfiltration, the stolen information is compressed in a password-protected RAR archive, and the native copy is wiped from reminiscence to remove any traces.
One other fascinating function of M2RAT is that it makes use of a shared reminiscence part for command and management (C2) communication, information exfiltration, and the direct switch of stolen information to the C2 with out storing them within the compromised system.
Utilizing a reminiscence part on the host for the above capabilities minimizes the trade with the C2 and makes evaluation tougher, as safety researchers have to investigate the reminiscence of contaminated gadgets to retrieve the instructions and information utilized by the malware.
In conclusion, APT37 continues to refresh its customized toolset with evasive malware that’s difficult to detect and analyze.
That is very true when the targets are people, like within the current marketing campaign noticed by ASEC, who lack bigger organizations’ refined risk detection instruments.

