Traditionally, menace actors weren’t eager to interact with journalists. They might have adopted press protection about themselves, in fact, however they hardly ever courted such consideration; staying underneath the radar was normally way more necessary to them. The thought of attackers recurrently placing out press releases and statements – not to mention giving detailed interviews and arguing with reporters – was absurd (even when they have been typically very keen to publicly argue with one another).
After which got here the ransomware gangs.
Ransomware has modified many sides of the menace panorama, however a key current improvement is its growing commoditization and professionalization. There’s ransomware-as-a-service; logos and branding (and even paying acolytes to get tattoos) and slick graphics on leak websites; outlined HR and Authorized roles; and bug bounty programmes. Accompanying all this – alongside the astronomical legal beneficial properties and the distress heaped on innumerable victims – is a slew of media consideration, and an more and more media-savvy assortment of menace actors.
Removed from shying away from the press, as so many menace actors did up to now, some ransomware gangs have been fast to grab the alternatives it affords them. Now, menace actors write FAQs for journalists visiting their leak websites; encourage reporters to get in contact; give in-depth interviews; and recruit writers. Media engagement gives ransomware gangs with each tactical and strategic benefits; it permits them to use stress to their victims, whereas additionally enabling them to form the narrative, inflate their very own notoriety and egos, and additional ‘mythologize’ themselves.
After all, it’s not at all times a harmonious relationship. Lately, we’ve seen a number of examples of ransomware actors disputing journalists’ protection of assaults, and making an attempt to right the file – typically throwing insults at particular reporters into the discount. Whereas this has implications for the broader menace panorama, it additionally has ramifications for particular person targets. Along with coping with enterprise impacts, ransom calls for, and reputational fallout, organizations at the moment are compelled to observe as ransomware gangs scrap with the media within the public area – with each incident fuelling extra protection and including additional stress.
Sophos X-Ops carried out an investigation of a number of ransomware leak websites and underground legal boards to discover how ransomware gangs are searching for to leverage the media and management the narrative – thereby hacking not solely programs and networks, but in addition the accompanying publicity.
A short abstract of our findings:
- Ransomware gangs are conscious that their actions are thought-about newsworthy, and can leverage media consideration each to bolster their very own ‘credibility’ and to exert additional stress on victims
- Menace actors are inviting and facilitating communications with journalists by way of FAQs, devoted non-public PR channels, and notices on their leak websites
- Some ransomware gangs have given interviews to journalists, wherein they supply a largely constructive perspective of their actions – probably as a recruitment device
- Nevertheless, others have been extra hostile to what they see as inaccurate protection, and have insulted each publications and particular person journalists
- Some menace actors are more and more professionalizing their method to press and reputational administration: publishing so-called ‘press releases’; producing slick graphics and branding; and searching for to recruit English writers and audio system on legal boards
Our goals in publishing this piece are to discover how and to what extent ransomware gangs are growing their efforts on this space, and to recommend issues that the safety neighborhood and the media can do now to negate these efforts and deny ransomware gangs the oxygen of publicity they’re searching for:
- Chorus from participating with menace actors until it’s within the public curiosity or gives actionable data and intelligence for defenders
- Present data solely to help defenders, and keep away from any glorification of menace actors
- Assist journalists and researchers focused by attackers
- Keep away from naming or crediting menace actors until it’s purely factual and within the public curiosity
Leveraging the media
Ransomware gangs are very acutely aware that the press considers their actions newsworthy, and can typically hyperlink to present protection of themselves on their leak websites. This reinforces their ‘credentials’ as a real menace for the good thing about guests (together with reporters and new victims) – and, in some circumstances, is probably going an ego journey as properly.
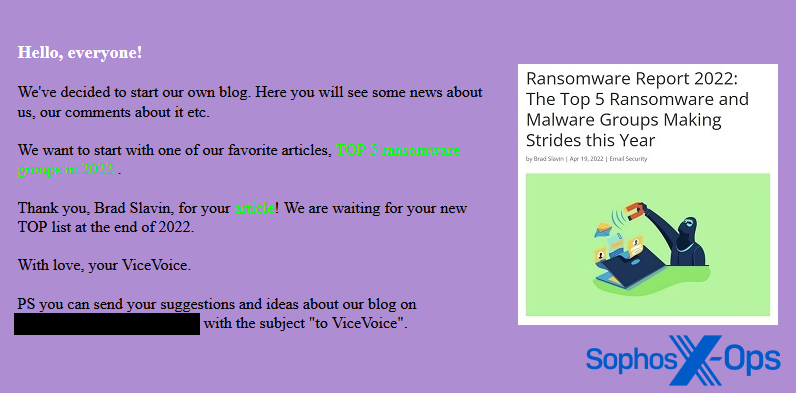
Determine 1: Vice Society thanks a selected journalist for an article wherein it was a part of a ‘Prime 5’ of ransomware and malware teams in 2022
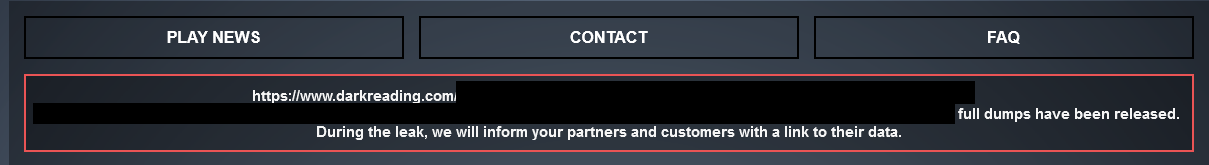
Determine 2: The Play ransomware group hyperlinks to a Darkish Studying article on its leak website
However some ransomware gangs aren’t content material with merely posting present protection; they’ll additionally actively solicit journalists.
Collaboration
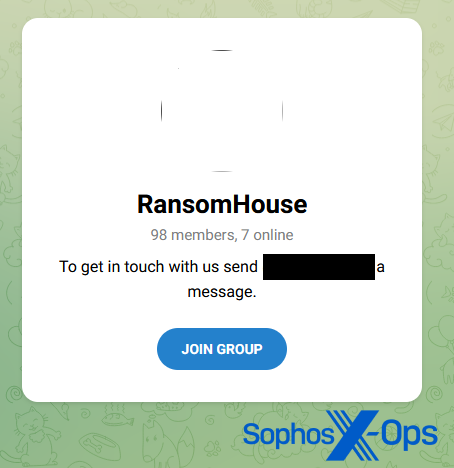
The RansomHouse group, for instance, has a message on its leak website particularly geared toward journalists, wherein it gives to share data on a ‘PR Telegram channel’ earlier than it’s formally printed. It’s not alone on this; allegedly, the LockBit ransomware group communicates with journalists utilizing Tox, an encrypted messaging service (many ransomware gangs listing their Tox ID on their leak websites).
Determine 3: An invite from RansomHouse
Determine 4: The RansomHouse PR Telegram channel
The 8Base leak website has an similar message (as different researchers have famous, 8Base and RansomHouse share different similarities, together with their phrases of service and ransom notes).
Determine 5: 8Base’s message to journalists
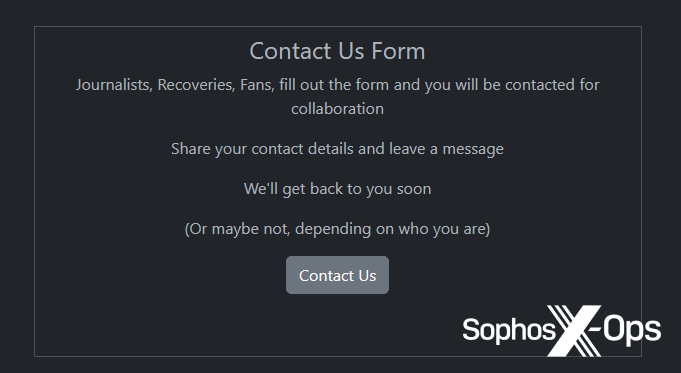
Rhysida’s contact type on its leak website addresses a number of teams of individuals. Apparently, journalists seem first on this listing, earlier than ‘Recoveries’ (presumably referring to victims or individuals engaged on their behalf).
Determine 6: Rhysida’s contact type
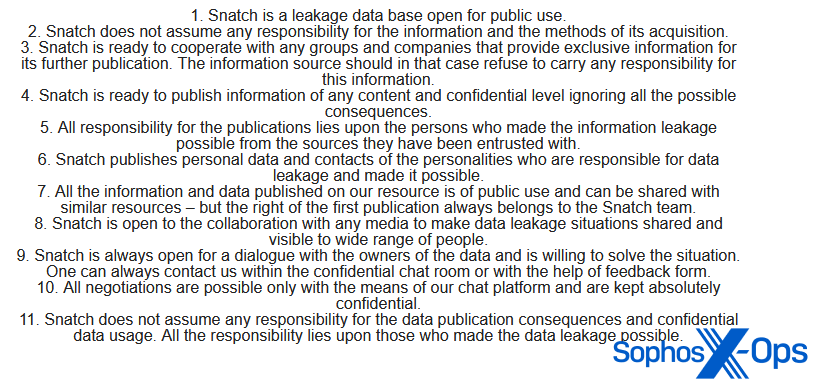
Over on the Snatch leak website, the menace actor maintains a “Public discover.” Of specific be aware is quantity eight on this listing: “Snatch is open to the [sic] collaboration with any media to make knowledge leakage conditions shared [sic] and visual to extensive [sic] vary of individuals.” And, as with Rhysida, journalists come earlier than sufferer negotiations on the listing.
Determine 7: Snatch’s ‘Public discover’
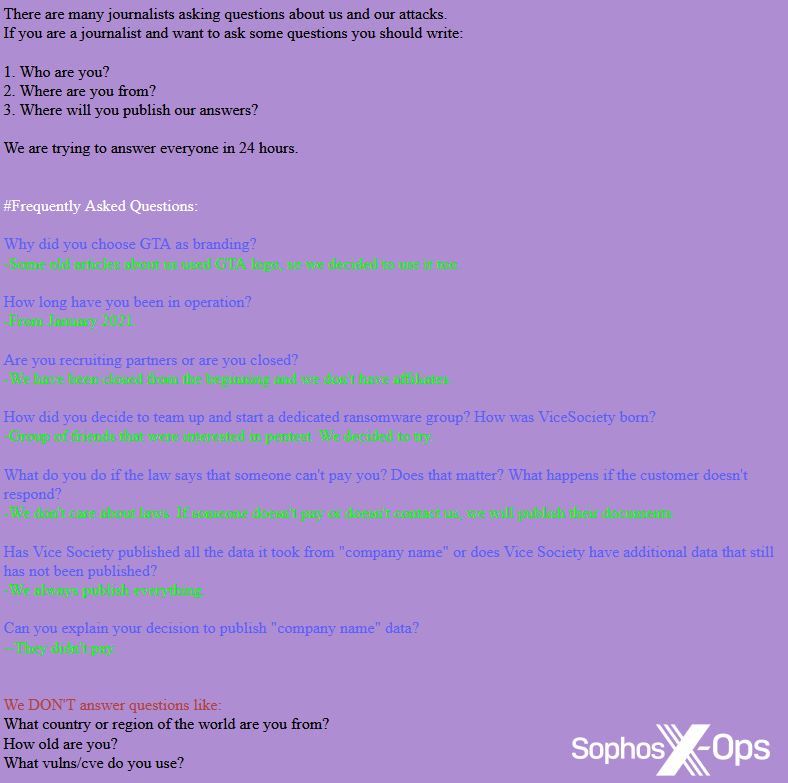
On Vice Society’s leak website, the menace actor notes: “There are lots of journalists asking questions on us and our assaults.” The message goes on to incorporate a full FAQ for reporters, together with a request for journalists to offer their title and outlet, and particulars of questions the group gained’t reply. Helpfully, for reporters with urgent deadlines, the menace actor additionally states that they struggle to answer queries inside 24 hours – an instance {of professional} PR greatest apply, which demonstrates how necessary that is to the menace actor.
Determine 8: Vice Society’s FAQ for journalists
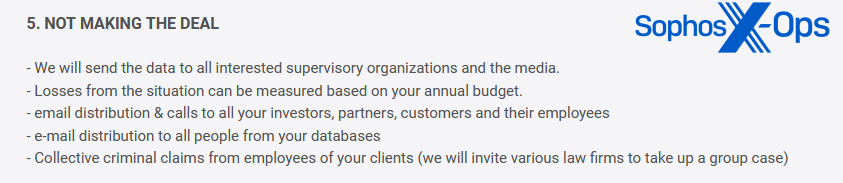
As famous earlier, a lot of that is doubtless achieved for bragging rights and to bolster criminals’ credibility and notoriety (which, in flip, can not directly improve the stress on victims). However some teams are extra express; Dunghill Leak, for instance, warns victims that if they don’t pay, they are going to take a number of actions – together with sending knowledge to the media.
Determine 9: Dunghill Leak’s warning to victims, together with a menace to ship knowledge to the media
Whereas not inside the scope of this text, the final line is price noting as properly: Dunghill threatens to “invite numerous regulation corporations to take up a gaggle case.” Ransomware class motion lawsuits aren’t exceptional, and will change into more and more widespread.
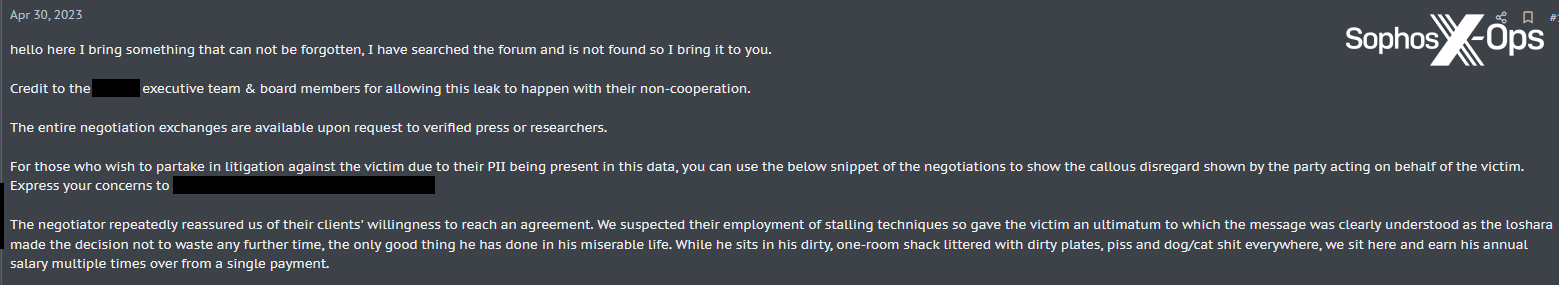
In an analogous vein, we noticed a person posting on a outstanding legal discussion board about an organization which had been the sufferer of a knowledge breach. The person said that negotiations had damaged down, and supplied to offer “all the negotiation exchanges” to “verified press or researchers” – and in addition famous that “for many who want to partake in litigation…you need to use the under snippet of the negotiations.” This is among the methods wherein ransomware actors are shifting their methods, utilizing multi-pronged weaponization (publicity, lawsuits, regulatory obligations) to exert additional stress on victims. As an illustration, ALPHV/BlackCat just lately reported a sufferer to the Securities and Alternate Fee (SEC) for not disclosing a breach – one thing which some commentators imagine could change into more and more widespread.
Determine 10: A put up on a legal discussion board, relating to a knowledge breach
Different ransomware gangs are very conscious that they will exert further stress on victims by elevating the spectre of media curiosity. Our Managed Detection and Response (MDR) staff just lately noticed ransom notes containing this menace from each Inc (“confidential knowledge…could be unfold out to individuals and the media”) and Royal (“anybody on the web from darknet criminals…journalists…and even your workers will be capable to see your inside documentation”).
Not all ransom notes point out the media, in fact, and lots of ransomware gangs preserve minimalist, bare-bones leak websites which merely listing their victims, with no direct appeals to journalists. However others have interaction straight with the media, within the type of interviews.
Interviews
A number of ransomware actors have given in-depth interviews to journalists and researchers. In 2021, the LockBit operators granted an interview to Russian OSINT, a YouTube and Telegram channel. The identical yr, an nameless REvil affiliate spoke to Lenta.ru, a Russian-language on-line journal. In 2022, Mikhail Matveev (a.okay.a. Wazawaka, a.okay.a. Babuk, a.okay.a. Orange), a ransomware actor and founding father of the RAMP ransomware discussion board, spoke intimately to The File – and even offered an image of himself. And some weeks later, a founding member of LockBit spoke to vx-underground (wherein they admitted that they personal three eating places in China and two in New York.
In most of those interviews, the menace actors appear to relish the chance to provide insights into the ransomware ‘scene’, focus on the illicit fortunes they’ve amassed, and supply ‘thought management’ concerning the menace panorama and the safety business. Just one – the REvil affiliate – provides a principally damaging depiction of the legal life (“…you’re afraid on a regular basis. You get up in worry, you go to mattress in worry, you cover behind a masks and a hood in a retailer, you even cover out of your spouse or girlfriend”).
So, along with the motivations we’ve already mentioned – notoriety, egotism, credibility, not directly growing stress on victims – an additional attainable motive for engagement with the media is recruitment. By depicting ransomware exercise as a glamorous, rich enterprise (“the chief in monetization,” as Matveev places it), menace actors could possibly be making an attempt to draw extra members and associates.
Press releases and statements
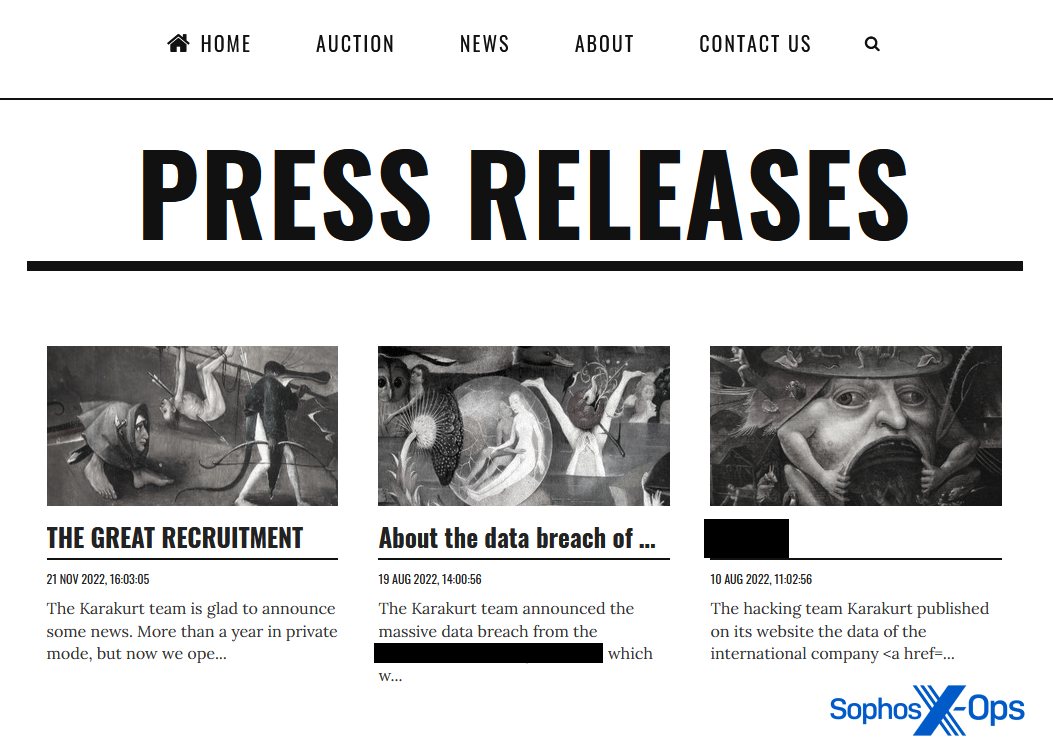
A handful of ransomware teams concern what they name “press releases” – and the truth that they use this time period is telling in itself. Karakurt, for instance, maintains a separate web page for its press releases. Of the three at present printed, one is a public announcement that the group is recruiting new members, and the others are about particular assaults. In each these latter circumstances, based on Karakurt, negotiations broke down, and the so-called ‘press releases’ are the truth is thinly-veiled assaults on each organizations in an try to stress them into paying and/or trigger reputational injury.
Each these items, whereas containing the odd error or idiosyncratic phrasing, are written in remarkably fluent English. One, aping the fashion of real press releases, even incorporates a direct quote from “the Karakurt staff.”
Determine 11: Karakurt’s ‘Press Releases’ web page
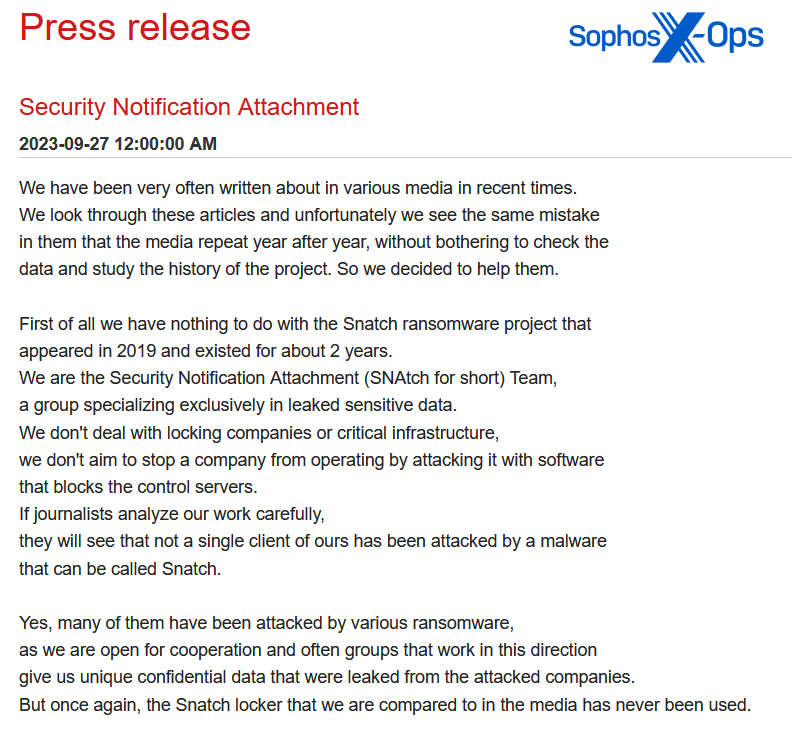
In distinction, an instance of a press launch from the Snatch group is way much less fluent, and doesn’t deal with a selected sufferer. As a substitute, it’s geared toward correcting errors by journalists (one thing that we’ll focus on in additional element shortly).
Determine 12: An excerpt from Snatch’s ‘press launch’
This assertion ends with the next sentence: “We’re at all times open for cooperation and communication and you probably have any questions we’re able to reply them right here in our tg [Telegram] channel.”
An additional instance, this one from Royal (not formally titled as a press launch, however with the heading “FOR IMMEDIATE RELEASE”), declares that the group won’t publish knowledge from a selected sufferer (a faculty), however will as an alternative delete it “consistent with our stringent knowledge privateness requirements and as an indication of our unwavering dedication to moral knowledge administration.” Right here, the menace actor is arguably inviting a comparability between their very own proactive motion to ‘shield’ in opposition to the leak (for which they’re accountable) and the mishandling of ransomware incidents and delicate knowledge by some organizations – thereby aiming to painting itself as extra accountable {and professional} than a few of its victims.
Determine 13: A public assertion by the Royal ransomware group
What’s notably noteworthy right here is the language; a lot of the fashion and tone of this announcement shall be recognisable to anybody who’s handled press releases and public statements. As an illustration: “the bedrock rules upon which Royal Knowledge Providers operates”; “At Royal Knowledge Providers, we respect the sanctity of academic and healthcare companies”; “Transferring ahead, we intention to…”.
It’s additionally price noting that Royal appears to be making an attempt to rebrand itself as a safety service (“Our staff of knowledge safety specialists will provide…a complete safety report, together with our greatest suggestions and mitigations…”). It has this in widespread with many different ransomware teams – who, in wholly unconvincing makes an attempt to painting themselves as forces for good, have referred to themselves as a “penetration testing service” (Cl0p); “sincere and easy pentesters” (8Base); or as conducting “a cybersecurity examine” (ALPHV/BlackCat).
Rebranding is one other PR tactic borrowed from legit business, and it’s not unreasonable to take a position that ransomware teams could step up this tactic sooner or later – maybe as a recruitment device, or to attempt to alleviate damaging protection from the media and a spotlight from regulation enforcement.
Branding
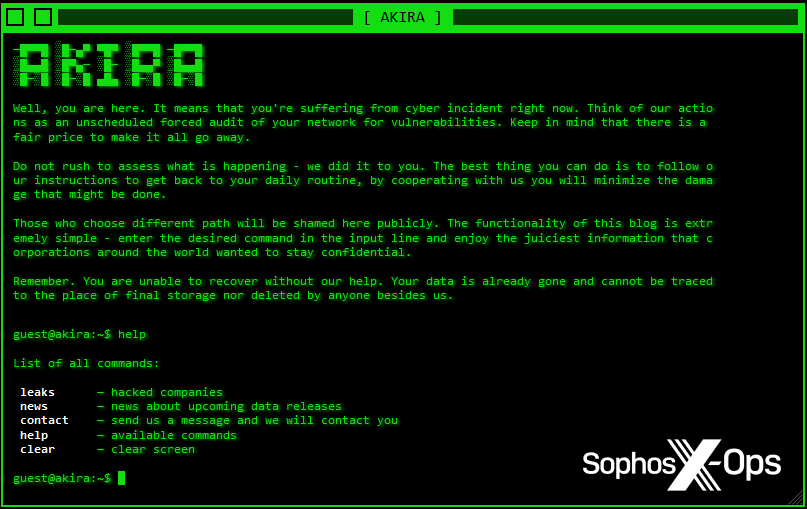
Branding is massively necessary to ransomware gangs searching for press protection. Catchy names and slick graphics assist appeal to the eyes of journalists and readers – notably relating to leak websites, as they’re the public-facing presences of those menace actors, and shall be incessantly visited by journalists, researchers, and victims. Take into account Akira, with its retro aesthetics and interactive terminal, or Donut Leaks, which has a frontpage graphic full with flickering neon indicators.
Determine 14: The Akira leak website
Determine 15: The Donut Leaks website
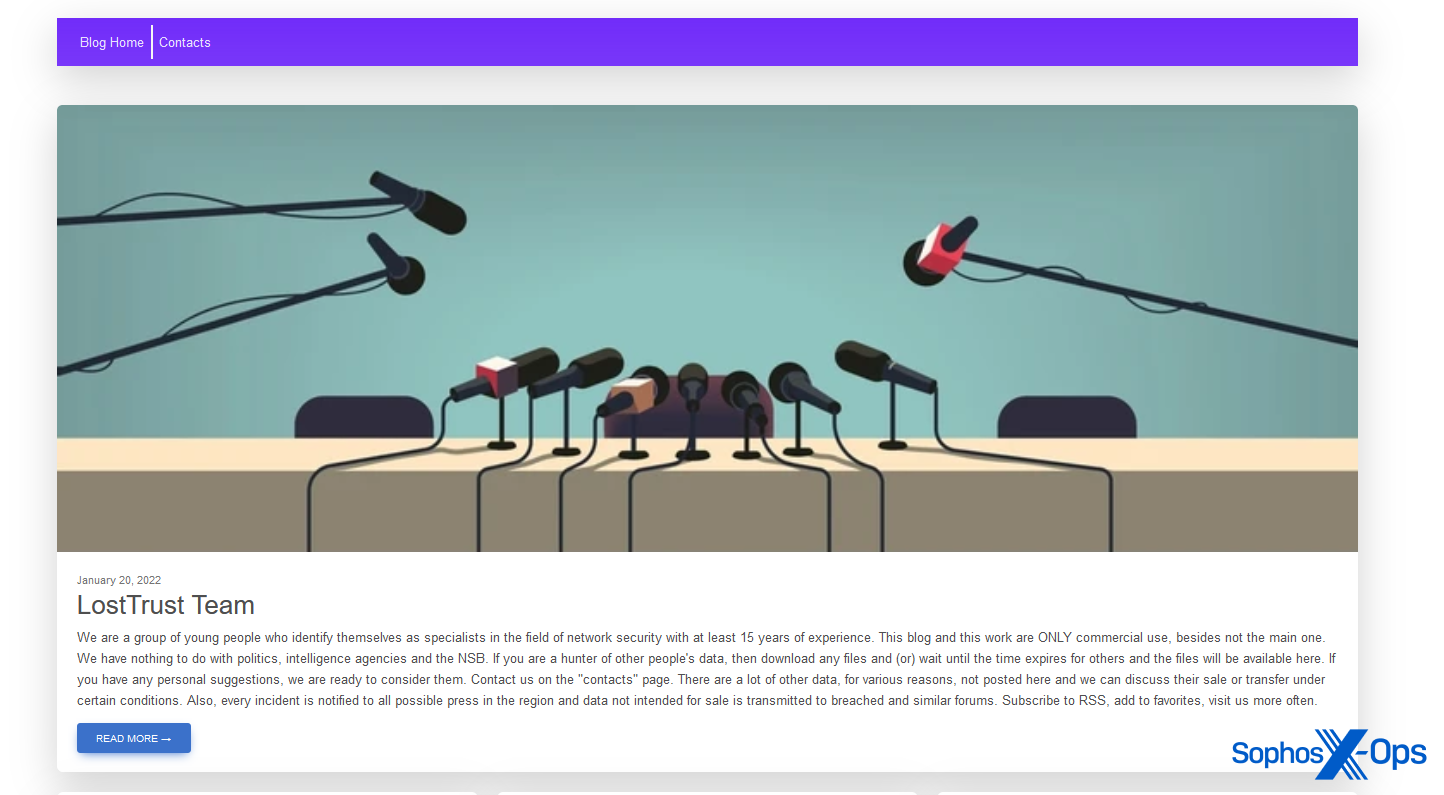
The LostTrust ransomware group (a attainable rebrand of MetaEncryptor) is so patently conscious that its leak website is its level of contact with the broader world, that it opted for a press convention graphic on its homepage.
Determine 16: LostTrust’s leak website. Notice the blurb on the backside, which incorporates the warning that “each incident is notified to all attainable press within the area” – echoing the warning from Dunghill Leak
On the opposite facet of the coin, one ransomware group – both fed up with this development, or getting performatively meta with it – determined to eschew a reputation and model altogether.
Determine 17: A ransomware group which refuses to provide itself a reputation – resulting in it inevitably being named ‘NoName ransomware’
Refined branding isn’t unique to ransomware gangs, in fact, and speaks to a wider level concerning the growing professionalization throughout many classes of menace actor, as we famous in our 2023 Annual Menace Report. Trendy adverts for malware merchandise, for instance, are sometimes characterised by enticing graphics and high-quality design.
One outstanding legal discussion board – which beforehand ran common, well-established ‘analysis contests’ – even has its personal ezine, together with artwork, tutorials, and interviews with menace actors. An instance, maybe, of cybercriminals not solely participating with media retailers, however creating their very own.
Determine 18: Artwork from an ezine produced by members of a legal discussion board
Recruitment
When a Ukrainian researcher leaked 1000’s of messages from contained in the Conti ransomware gang in March 2022, many have been stunned on the extent of group inside the group. It had a definite hierarchy and construction, very similar to a legit firm: bosses, sysadmins, builders, recruiters, HR, and Authorized. It paid salaries recurrently, and set working hours and holidays. It even had bodily premises. However what’s notably attention-grabbing within the context of this text is that Conti had no less than one individual (and presumably as many as three) devoted to negotiating ransoms and writing ‘weblog posts’ for the leak website (a ‘weblog’ is a euphemism for an inventory of victims and their printed knowledge). So the types of issues we’ve been discussing – responding to journalists, writing press releases, and so forth – aren’t essentially simply cobbled collectively by hackers after they’re not busy hacking. Inside outstanding, well-established teams, they could properly add as much as a full-time position – mirroring the scenario in know-how and safety firms, with groups devoted to publicizing analysis and outcomes (Sophos X-Ops being an instance, if that’s not getting too meta).
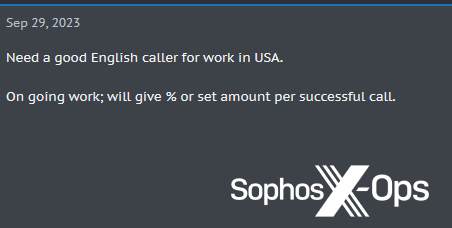
Whereas many ransomware-related actions don’t require fluent English expertise, this type of work does – particularly if menace actors are additionally going to be writing public statements. Such people need to be recruited from someplace, and on legal boards, adverts for English audio system and writers (and, sometimes, audio system of different languages) are pretty widespread. Many of those advertisements aren’t essentially for ransomware teams, in fact, however doubtless for social engineering/scamming/vishing campaigns.
Determine 19: An advert on a legal discussion board for “an excellent English caller.” This advert might be for some form of rip-off marketing campaign
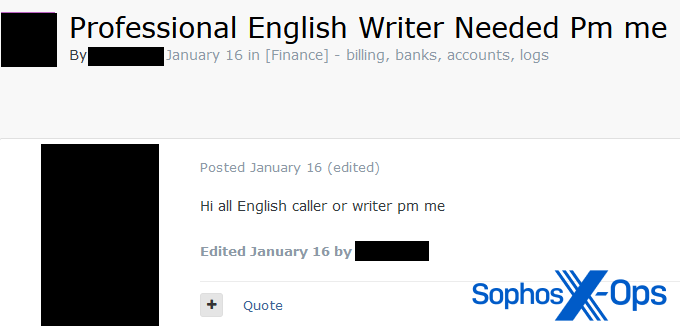
In different circumstances, the type of work being supplied is much less clear, and requires writers reasonably than audio system:
Determine 20: A person on a legal discussion board seeks a “Skilled English Author”
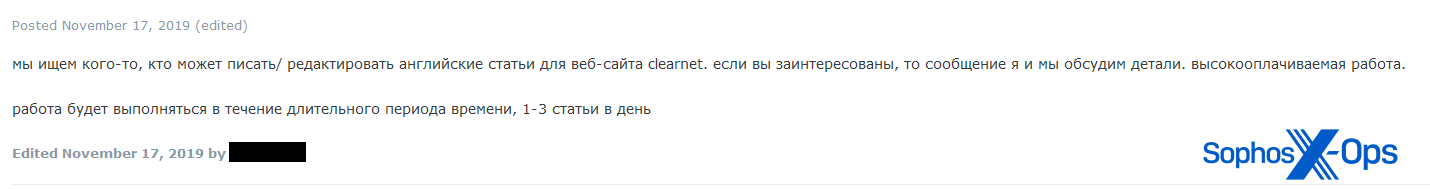
Determine 21: A job advert on a legal discussion board. Trans.: “We’re in search of somebody who can write/edit English articles for the clearnet web site. In case you are , message me and we are going to focus on the main points. excessive paying job. the work shall be accomplished over a protracted time period, 1-3 articles per day.” The identical person additionally marketed for a “journalist/author.”
In a very curious instance – albeit one not associated to the media – a person created a thread entitled: “Evaluation of economic and authorized vulnerabilities for negotiations”:
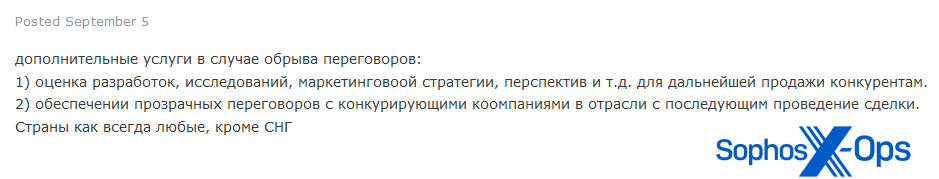
Determine 22: An excerpt from the person’s put up
In the identical thread, the person later added extra element – noting that different duties would come with (trans.) “add bigdata to the onion area”, and that “in case of breakdown of negotiations”, candidates would even be anticipated to carry out “evaluation of developments, analysis, advertising technique, prospects, and so on. for additional sale to opponents.”
Determine 23: Additional element from the identical person
We assess that that is doubtless an try to recruit somebody to assist extort firms into paying a ransom, by discovering compromising data which menace actors may use to use stress throughout negotiations. Notice that the primary a part of the advert states “typically [this] doesn’t require the usage of software program”, implying that this isn’t a ‘conventional’ ransomware group utilizing encrypting malware.
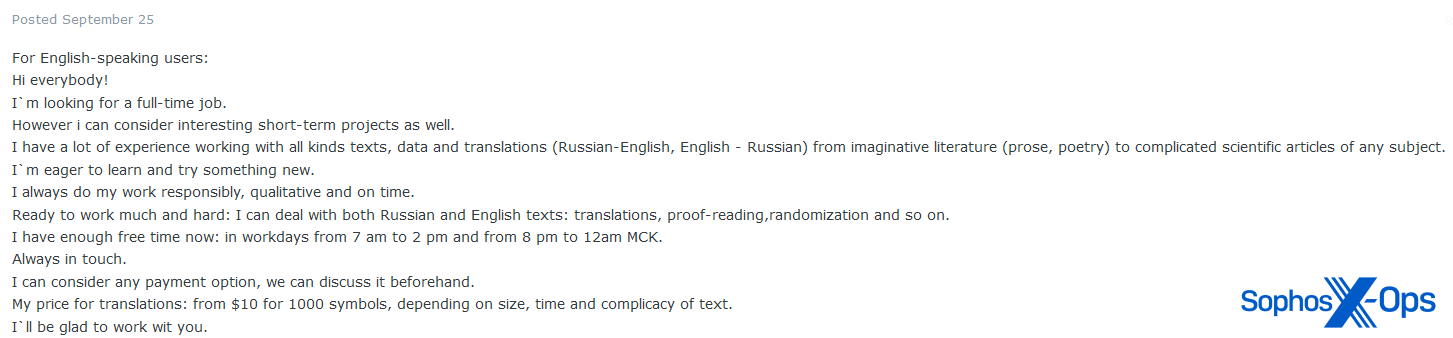
Lastly, we additionally famous a number of cases of customers promoting their companies as translators, notably Russian to English and vice versa.
Determine 24: A person gives their companies as a translator
Whereas we didn’t discover any particular examples of menace actors making an attempt to recruit individuals with advertising/PR expertise, that is one thing we’re going to maintain a watch out for. Given the growing ‘celebrification’ of ransomware teams (see LockBit’s tattoo stunt and comparable developments) and the rebranding methods mentioned beforehand, it could solely be a matter of time earlier than criminals make extra concerted efforts to handle their public photographs and cope with the growing quantities of media consideration they obtain.
When issues go mistaken
We’ve famous that ransomware teams leverage the media in quite a few methods: referring to earlier protection on their leak websites; inviting questions from journalists; giving interviews; and utilizing the specter of publicity to coerce victims into paying ransoms. Nevertheless, as many public figures and firms have discovered to their price, relationships with the media aren’t at all times affable. On a number of events, ransomware teams and different menace actors have criticized journalists for what they really feel is inaccurate or unfair protection.
The builders of WormGPT, for instance – a derivation of ChatGPT, supplied on the market on legal marketplaces to be used by menace actors – shut their challenge down, as a result of quantity of media scrutiny. In a discussion board put up, they said: “we’re more and more harmed by the media’s portrayal…Why do they try to tarnish our popularity on this method?”
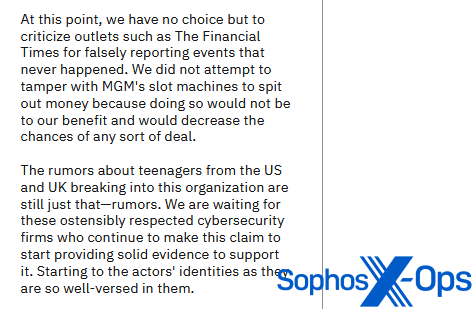
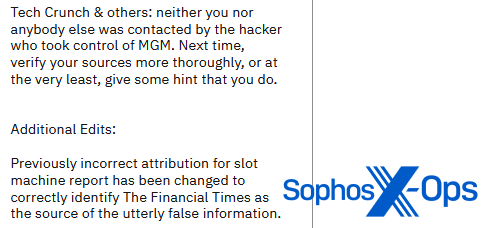
Ransomware teams, alternatively, are typically extra aggressive of their rebuttals. ALPHV/BlackCat, as an illustration, printed an article on its leak website entitled “Assertion on MGM Resorts Worldwide: Setting the file straight”, a 1,300-word put up wherein it criticized quite a few retailers for not checking sources and reporting incorrect data.
Determine 25: ALPHV/BlackCat criticizes an outlet for ‘false reporting’
Determine 26: ALPHV/BlackCat criticizes one other outlet for ‘false reporting’, whereas admitting that it beforehand falsely reported a supply of ‘false data’
The assertion goes on to assault a person journalist and a researcher, earlier than concluding: “we’ve got not spoken with any journalists…We didn’t and more than likely gained’t.” Apparently, then, that is an instance of a ransomware group not participating with the media – as an alternative making an attempt to manage the narrative by presenting itself as the only, dominant, voice of reality. (Perhaps there are some energy dynamics at play right here, too, however digging into the psychology of ransomware actors is one thing we’re neither certified nor inclined to do.)
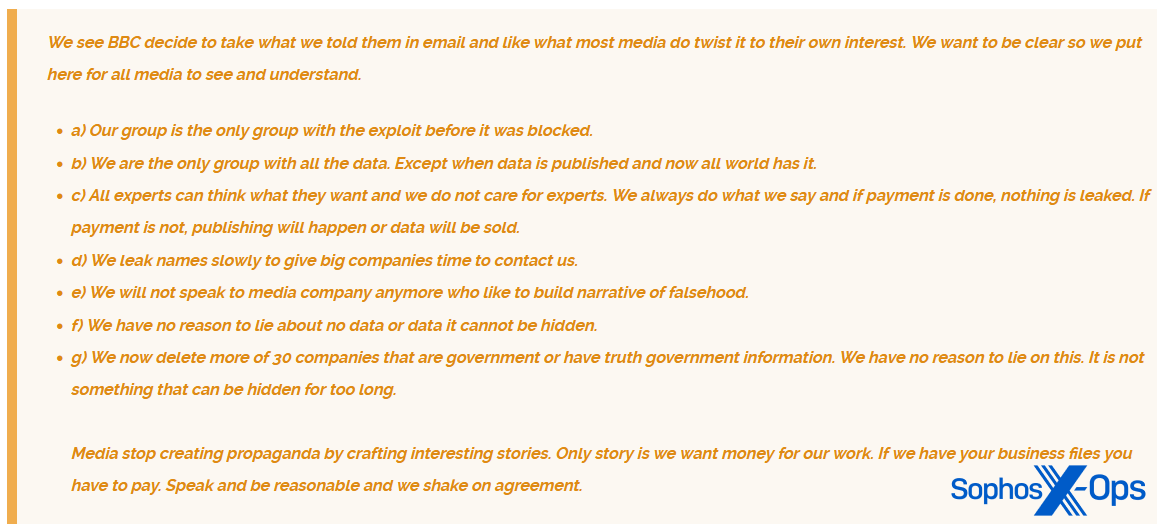
The Cl0p ransomware group tried to do one thing comparable throughout a rash of high-profile assaults earlier this yr, which leveraged a vulnerability within the MOVEit file-transfer system. In a put up on its leak website, it said that “all media talking about this are do [sic] what they at all times do. Present little reality in a giant lie.” Later, the group particularly referred to as out the BBC for “creating propaganda,” after Cl0p had emailed the BBC with data. Very like the ALPHV/BlackCat instance above, Cl0p is making an attempt to ‘set the file straight,’ correcting what it sees as inaccuracies in media protection and representing itself as the one authoritative supply of data. The message to victims, researchers, and the broader public: don’t imagine what you learn within the press; solely we’ve got the actual story.
Determine 27: The Cl0p ransomware gang calls out the BBC for ‘twisting’ data
An uneasy relationship
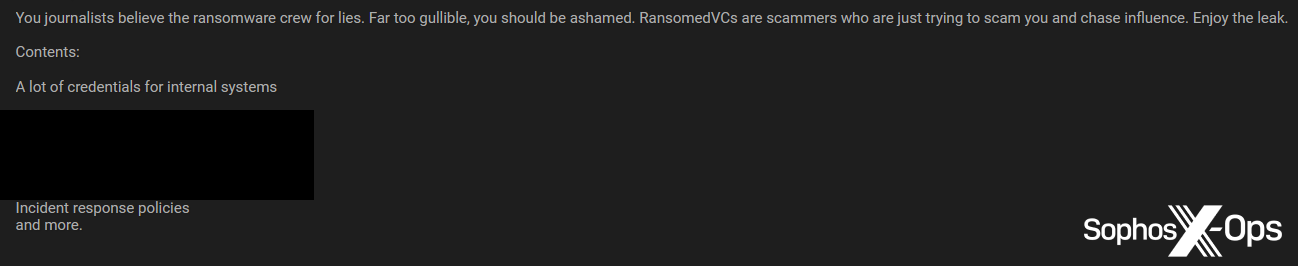
Cl0p isn’t alone in feeling mistrustful of journalists; it’s a standard sentiment on legal boards. Many menace actors – not simply ransomware teams – dislike the press, and a few non-ransomware criminals are skeptical of the connection between journalists and ransomware gangs:
Determine 28: A menace actor criticizes journalists for believing the “lies” of ransomware actors, and criticizes ransomware actors “who’re simply making an attempt to rip-off you [journalists] and chase affect.” Notice that the sentiment right here just isn’t dissimilar to that expressed by ALPHV/BlackCat and Cl0p within the earlier part
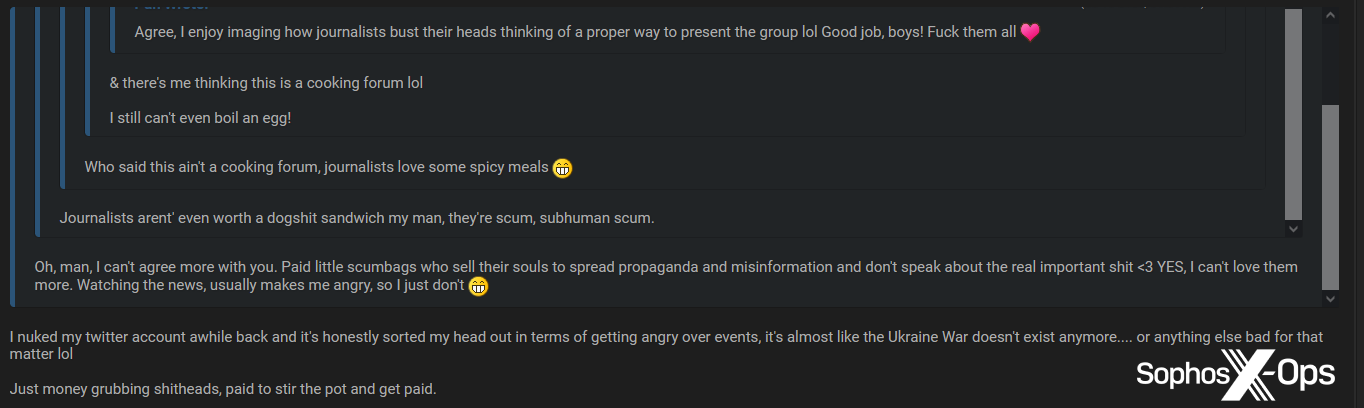
Simply as ransomware teams are acutely aware that their leak websites are frequented by journalists, so members of legal boards know that journalists have infiltrated their websites. Excessive-traffic threads about outstanding breaches and incidents will typically include feedback alongside the strains of ‘Right here come the reporters,’ which sometimes descend into full-blown rants and insults.
Determine 29: A number of members of a legal discussion board insult journalists
Extra hardly ever, menace actors will name out and/or assault particular person journalists, as within the ALPHV/BlackCat instance above. Whereas this hasn’t, to our information, escalated to direct threats, these reactions are doubtless designed to make the journalists in query really feel uncomfortable, and in some circumstances to trigger reputational injury – not at all times efficiently.
The title and branding of the carding market Brian’s Membership, for instance, relies on safety journalist Brian Krebs. The location makes use of Krebs’ picture, first title, and a play on his surname (‘Krabs’, or crabs, for ‘Krebs’), on each its homepage and inside the website itself.
Whereas this doesn’t appear to unduly concern Krebs (he mentions being “stunned and delighted” to obtain a reply from the Brian’s Membership admin after making an enquiry about the positioning being compromised; the admin’s reply started: “No. I’m the actual Brian Krebs right here 😊”), different journalists may not really feel fairly so comfy on this scenario.
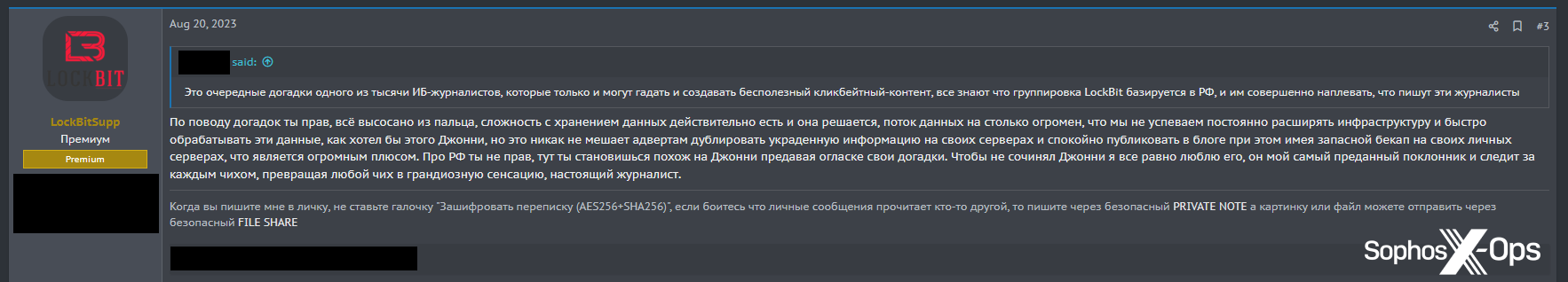
After all, researchers aren’t immune to those techniques both, and are additionally usually topic to insults and threats on boards. The connection between menace actors and researchers is an entire different story, and out of scope for this text, however one instance is price noting. After publishing the primary a part of a three-part sequence on the interior workings of the LockBit gang, researcher Jon DiMaggio was alarmed to find that LockBit’s profile image on a outstanding legal discussion board had been modified to a photograph of himself.
After publication of the ultimate a part of the sequence, menace actors mentioned the report amongst themselves. One was dismissive (trans.: “These are simply the most recent guesses from one of many 1000’s of data safety journalists who can solely guess and create ineffective clickbait content material”), to which the LockBit account replied: “you’re proper, every little thing is made up…[but] it doesn’t matter what Johnny says, I nonetheless love him, he’s my most devoted fan and follows each sneeze, turning any sneeze into an enormous sensation, an actual journalist.”
Determine 31: LockBit posts in a dialogue about DiMaggio’s experiences
So even LockBit – some of the outstanding ransomware gangs, which has devoted important effort and time into cultivating its picture, professionalizing itself, and giving media interviews – is sceptical of journalists and their motivations.
Conclusion
The truth that some ransomware teams will eagerly solicit media protection and talk with journalists, regardless of being mistrustful and demanding of the press on the whole, is a contradiction which shall be acquainted to many public figures. In the identical method, many journalists will acknowledge the sensation of getting qualms concerning the actions, ethics, and motivations of many public figures, whereas additionally figuring out that reporting on these figures is within the public curiosity.
And, prefer it or not, some ransomware actors are on their approach to changing into public figures. Accordingly, they’re devoting an growing period of time to ‘managing the media.’ They’re conscious of protection about themselves, and publicly right inaccuracies and omissions. They encourage questions, and supply interviews. They’re acutely aware that cultivating media relationships is helpful for attaining their very own targets and refining their public picture.
That is, in some methods, distinctive to ransomware gangs. Not like nearly all different kinds of menace – that are primarily based on going undetected for so long as attainable, and ideally indefinitely – a ransomware marketing campaign should finally make itself identified to the sufferer, to demand a ransom. Leak websites have to be publicly out there, in order that the criminals can apply stress to victims and publish stolen knowledge. These elements, and the explosive progress of the ransomware menace, have led to a scenario the place menace actors, removed from shunning the more and more vibrant glare of the media highlight, acknowledge the potential to mirror and redirect it for their very own ends. They will leverage alternatives to straight and not directly apply stress to victims; appeal to potential recruits; improve their very own notoriety; handle their public picture; and form the narrative of assaults.
In the intervening time, these developments are nascent. Whereas there’s actually an effort amongst some ransomware actors to mimic the environment friendly ‘PR machines’ of legit companies, their makes an attempt are sometimes crude and amateurish. Typically they appear extra of an afterthought than the rest.
Nevertheless, there are indications that that is altering. Initiatives resembling devoted PR Telegram channels, FAQs for journalists, and makes an attempt to recruit journalists/writers, could develop and evolve. And as with many facets of ransomware – and the menace panorama on the whole – commodification and professionalization are on the rise. It could be a method off, however it’s not unfeasible that sooner or later, ransomware teams could have devoted, full-time PR groups: copywriters, spokespeople, even picture consultants. This will present some ‘nice-to-haves’ for ransomware actors – inflating egos, bolstering recruitment efforts – however it’s going to predominantly come all the way down to including to the already important stress positioned on victims, and lowering any stress on themselves from regulation enforcement or the legal neighborhood.
Within the meantime, it’s doubtless that ransomware teams will proceed to attempt to management the narratives round particular person assaults, as we’ve seen just lately with Cl0p and ALPHV/BlackCat. We’ll be conserving a detailed eye on developments on this area.
Acknowledgments
Sophos X-Ops want to thank Colin Cowie of Sophos’ Managed Detection and Response (MDR) staff for his contribution to this text.