Programs whose failure is insupportable, typically termed vital methods, have to be designed rigorously, no matter whether or not they’re safety-, security-, mission-, or life-critical—or some mixture of the 4. A variety of improvement methodologies and applied sciences exists to assist this cautious design, however one of many extra well-studied and promising is model-based engineering (MBE) the place fashions of a system, subsystem, or a set of parts are constructed and analyzed. Because of the sophistication of those fashions and the intricacies of their analyses, nonetheless, software program tooling is nearly required for all however the easiest duties. On this put up, I describe a brand new extension to the Open Supply AADL Device Surroundings (typically abbreviated as OSATE), SEI’s software program toolset for MBE. This extension, referred to as the OSATE Slicer, adapts an idea referred to as slicing to architectural fashions of embedded, vital methods. It does this by calculating of varied notions of reachability that can be utilized to assist each handbook and automatic analyses of system fashions.
Earlier than diving into the main points, let me take a step again and focus on the method of model-based engineering in a bit extra depth. Usually, fashions are constructed and analyzed previous to the ultimate development of the part or system itself, resulting in the early discovery of system integration points. Whereas engineering fashions are helpful by themselves (e.g., speaking between stakeholders and figuring out gaps in necessities) they will also be analyzed for numerous purposeful or non-functional system properties. What’s extra, if the mannequin is constructed utilizing a sufficiently rigorous language, these analyses will be automated. Fashions are, by definition, abstractions of the entities they characterize, and people abstractions emphasize a selected perspective. However one factor that analyses—each handbook and automatic—can battle with is deciphering a mannequin constructed to showcase one perspective (e.g., a purposeful mannequin of a system’s structure) from a distinct perspective (e.g., the move of information or management sequences by means of these purposeful parts).
This explicit shift in perspective is usually crucial, although, and it underlies lots of the handbook and automatic analyses we now have created right here on the MBE crew on the SEI. Whether or not it’s a security evaluation that should think about the move of inaccurate sensor readings by means of a system, a safety evaluation that should assure confidential knowledge can’t leak out unencrypted ports, or a efficiency evaluation that calculates end-to-end latency, the necessity to extract the paths that knowledge or management messages take by means of a system is properly established.
The OSATE Slicer
Latest work finished by the MBE crew goals to assist calculate these paths by means of fashions of a system’s structure. We have now created a software program implementation that generates a graph-based illustration of the paths by means of a system, after which makes use of that graph to reply reachability queries. This concept might sound acquainted to some readers: it underlies the idea of program or mannequin slicing, which may be very intently associated to our work, therefore the software program software’s identify: The OSATE Slicer (or, the place context makes it clear, simply the slicer). The essential thought of slicing is to take a program or mannequin and a few enter referred to as a slicing criterion, after which discard every part that doesn’t should do with the slicing criterion to provide a decreased model of this system or mannequin. Whereas our work doesn’t but assist this full imaginative and prescient of mannequin discount, the reachability graph and question assist we now have applied are a crucial first step, and—as we focus on on this put up—helpful in their very own proper.
Like a whole lot of the work finished by the SEI MBE crew, this undertaking was enabled by two key SEI applied sciences. First, the Architectural Evaluation and Design Language (AADL) is an structure modeling language for vital methods. It has well-specified semantics that make it notably amenable to automated analyses, and has been used for many years by the U.S. Division of Protection (DoD), business, and researchers for a wide range of functions. The second key expertise is OSATE, which is an built-in improvement setting for AADL. Many analyses that function on AADL fashions are applied as plug-ins to OSATE, and the slicer is as properly.
For those who’re not acquainted with AADL, there are a variety of sources accessible to elucidate the ins and outs of the language (the AADL web site particularly is a superb start line). On this put up, although, I’ll use a easy mannequin as an example a number of the particulars of the OSATE Slicer. This mannequin, proven beneath, is known as the BasicErrorFlow instance. It consists of each core AADL, which specifies the fundamental structure of a system, and annotations from AADL’s EMV2 Language Annex, which extends the core language in order that error habits will also be modeled.
The black packing containers and features within the mannequin beneath are legitimate AADL (which has each a graphical and a textual syntax) that present three speaking summary (i.e., undefined and supposed for later refinement) parts. These parts talk over options, named “i” for enter or “o” for output, and numbered 1-3. Superimposed on high of this (in crimson) in a notional syntax is an instance error move from aspect a, by means of aspect b, into aspect c. You may think aspect a as some sort of sensor that’s liable to a selected failure, b as an automatic controller which interprets that sensor knowledge and points instructions primarily based upon them, and c as some type of actuator which effectuates the instructions.
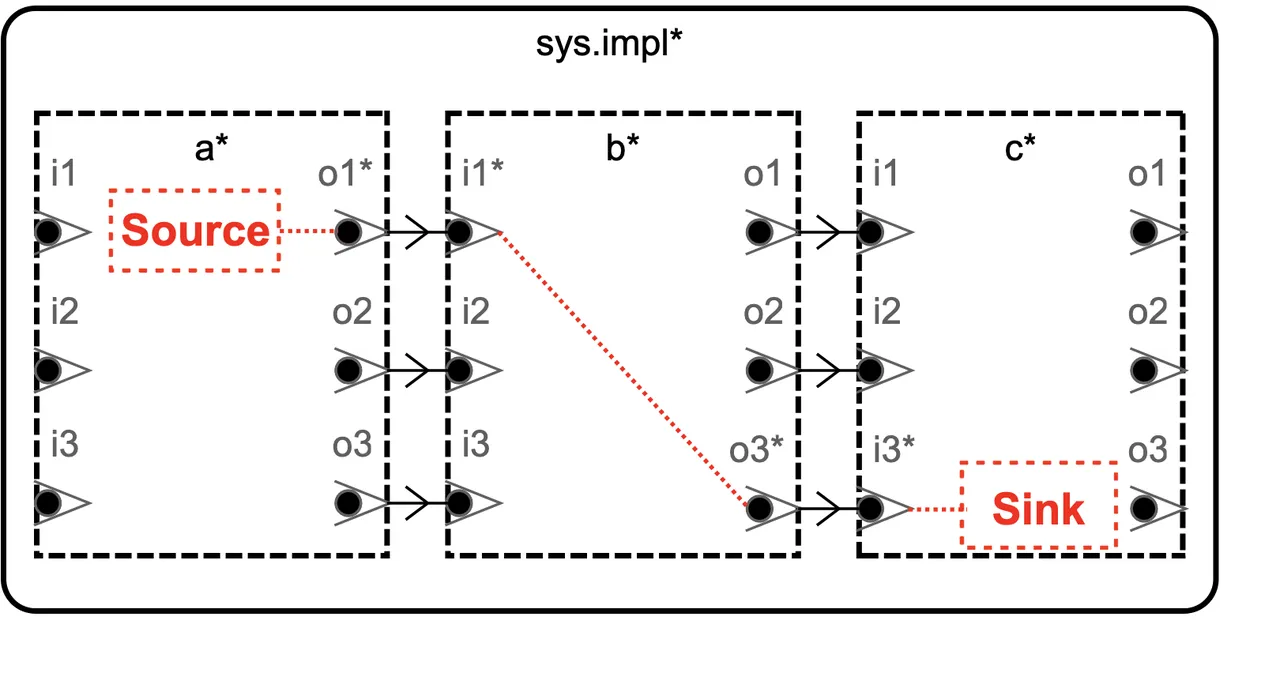
Determine 1: A snippet of graphical AADL, exhibiting the BasicErrorFlow mannequin
“Underneath the Hood” of Architectural Mannequin Evaluation
Let’s dive a bit deeper into how these evaluation plug-ins usually work. Like many instruments that course of inputs laid out in some type of programming or modelling language, OSATE offers plug-in builders entry to AADL mannequin parts utilizing a way referred to as the customer sample. Basically, this sample ensures that each aspect can be “visited” and when it’s, the developer of an evaluation plug-in can specify some motion to take (e.g., recording an related property worth or storing a reference to the aspect for later use). Considerably, although, the order through which these parts are visited has little to no bearing on the order through which they may create or entry knowledge or management messages when the system is operational. As an alternative, they’re visited in response to their place within the mannequin’s summary syntax tree.
Earlier work finished as a part of the Awas undertaking by Hariharan Thiagarajan and colleagues at Kansas State College’s SAnToS Lab in collaboration with the SEI demonstrated the worth of extracting and querying a reachability graph from AADL fashions. That work was subsequently constructed on by tasks each right here on the SEI and externally. See, for instance, its use in DARPA’s Cyber Assured Programs Engineering (CASE) program. We had been satisfied of the worth of this method, however wished to see if we might create our personal implementation which—whereas easier and fewer feature-rich than Awas—may very well be extra properly aligned with OSATE’s implementation and design ideas, and in doing so, may very well be extra maintainable and performant.
Maintainability and Efficiency by way of Cautious Design
Graph Definition and Implementation
Earlier within the put up, I discussed how the OSATE Slicer generates and queries one thing referred to as a reachability graph. The time period graph is used right here to imply not a chart evaluating totally different values of some variable, however somewhat a mathematical or knowledge construction the place vertices are linked collectively by edges, (i.e., “a set of vertices and and edges that be part of pairs of vertices”). The reachability a part of the time period refers back to the that means of the graph: vertices characterize explicit parts of the system structure, and if two vertices are related by an edge, that signifies that knowledge or management messages can move from the mannequin aspect related to the supply vertex to the aspect related to the vacation spot vertex. The best graph definition is simply G=(V,→), and that is the definition we use: V is the set of architectural parts, and → is a perform connecting a few of these parts to another parts. The satan is within the particulars, in fact; on this case these particulars are which parts are included in V and which relationships are included in →. These particulars are specified and defined in a paper revealed earlier this 12 months on the work.
Whereas our graph definition is straightforward, which ought to assist obtain our purpose of constructing it quick and simple to generate and question, it’s nonetheless solely a mathematical abstraction. We have to characterize the graph in software program, and for that we turned to the wonderful and well-established graph idea library JGraphT. Encoding our graph in JGraphT was simple: we might affiliate OSATE’s illustration of AADL parts with JGraphT vertex objects, which lets analyses simply use each the graph and its related system mannequin. Virtually, because of this analyses can run operations on the reachability graph, which can yield graph objects, corresponding to subgraphs or particular person vertices, after which translate these objects to AADL mannequin parts that can be significant to customers.
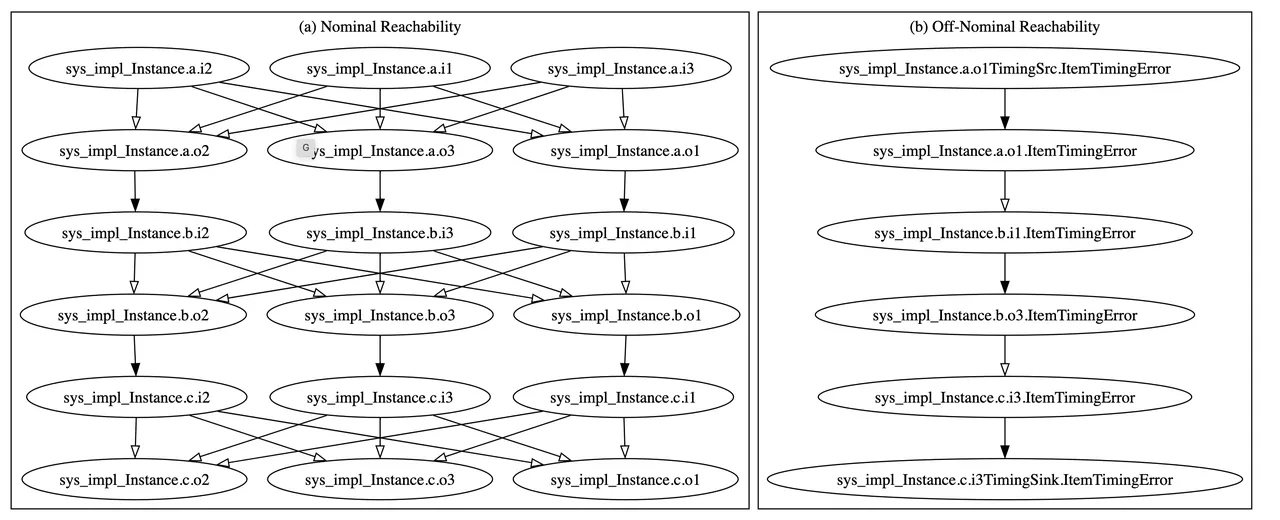
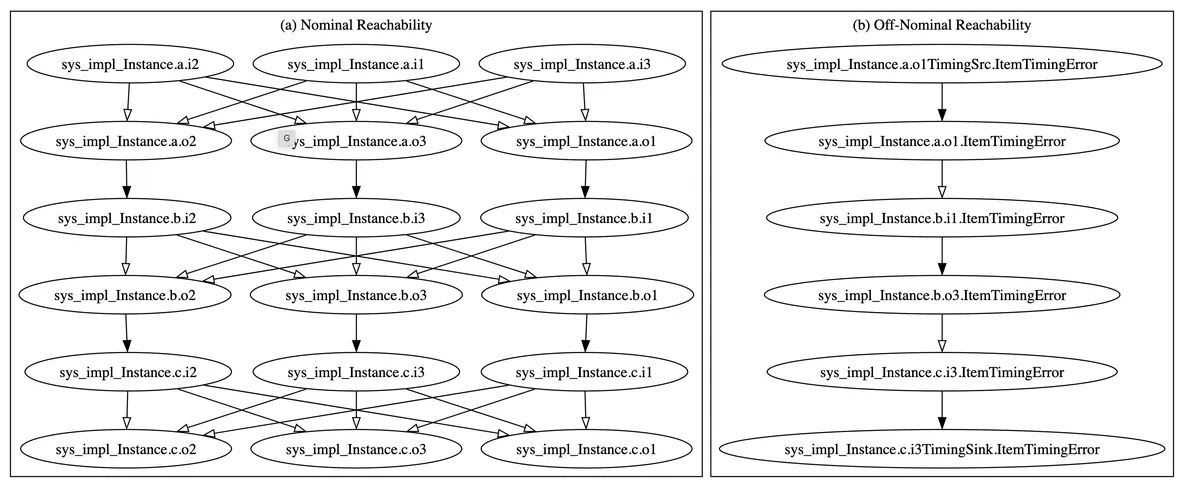
Determine 2: The reachability graph for the BasicErrorFlow mannequin
The reachability graph for the BasicErrorFlow mannequin launched earlier is proven in Determine 2. There are a pair notable issues in regards to the graph: First, it’s really two graphs, the one on the left is the nominal graph, constructed utilizing solely core AADL, which is the bottom language. The (far easier) graph on the suitable is the off-nominal graph, constructed utilizing each core AADL and its error-modeling extension often known as EMV2. For the exact meanings of the graphs, I’ll once more refer readers to the paper. For this put up, I’ve included them to present an intuitive feeling of the type of knowledge buildings we’re working with. The essential thought, although, is {that a} extra detailed mannequin produces a much less ambiguous reachability graph; so the off-nominal graph (which might make the most of the error move data current within the mannequin) is way easier and extra exact.
Querying the Reachability Graph
To get any worth out of the reachability graph, we now have to have the ability to question it, pose questions on relationships between numerous vertices. There are 4 foundational queries: attain ahead, attain backward, attain from, and attain by means of.
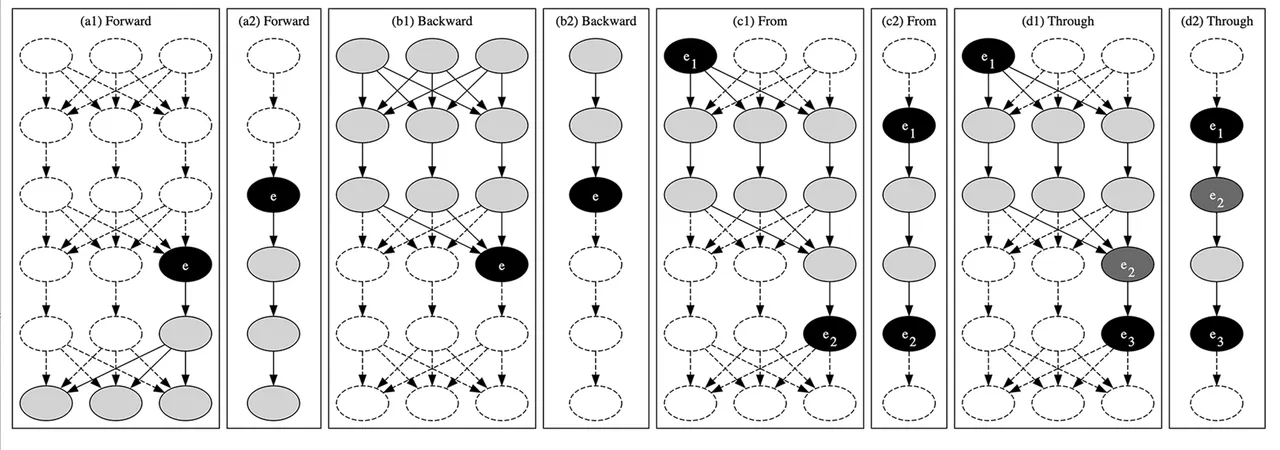
Determine 3: Queries of the reachability graph for the BasicErrorFlow mannequin
Attain Ahead and Backward
The primary two queries are pretty simple. Attain ahead queries ask, What mannequin parts can this mannequin aspect have an effect on? That’s, if we return to our conceptualization of the BasicErrorFlow mannequin as a sensor related to a controller related to an actuator, we would ask, The place can knowledge readings produced by the sensor, or any instructions derived from them, go? Attain backward queries are comparable, however they as an alternative pose the query, What mannequin parts can have an effect on this mannequin aspect? Utilized to a real-world system, these queries would possibly ask, What sensors and controllers produce data used to control this explicit actuator?
Determine 3 reveals graphically, in (a1) and (a2), instance ahead reachability queries on the reachability graphs: nominal in (a1), off-nominal in (a2). Equally, (b1) and (b2) present instance backward reachability queries. The aspect used because the slicing criterion, i.e., the question origin, is proven in black and labeled with an e. The outcomes of the question are all shaded parts—together with the question origin. Notably, the results of executing this question is a decreased portion of a system’s related reachability graph (particularly an induced subgraph). In contrast to a number of the different queries that return a easy sure/no-style consequence, these subgraphs aren’t more likely to be very helpful by themselves in automated analyses, they usually don’t lend themselves to, for instance, DevOps-style automated analysis. They’re more likely to be helpful, although, for both producing visible outcomes that may then be interpreted by a human, or as the primary stage in additional complicated, multi-stage queries.
Attain From
The third question sort is a kind of multi-stage queries, although it’s not terribly complicated. In attain from queries, we merely ask, Can this mannequin aspect attain that one? We do that by first executing a ahead attain question from the primary aspect (e1 in (c1) and (c2) in Determine 3) after which seeing if the second aspect (e2) is contained within the ensuing subgraph. Figuring out whether or not data from a sensor, or instructions from a controller, can have an effect on a selected actuator is helpful, however this question actually shines when executed on the off-nominal reachability graph. Recall that it’s constructed utilizing a system’s structure (laid out in AADL) and details about what occurs when the system encounters errors (specified within the error-modeling extension to AADL referred to as EMV2). This design signifies that attain from queries let modelers or automated analyses ask, Can an error from this system attain that one, or is it in some way stopped?
Attain By means of
The fourth and remaining foundational question sort solutions questions of the shape, Do all paths from this mannequin aspect which attain that one undergo some explicit intermediate aspect?
The utility of this question might not be instantly apparent, however think about two situations. The primary, from the protection area, entails (a) a sensor that’s recognized to sometimes produce jittery values, (b) a “checker” mannequin aspect that may detect and discard these jittery readings, and (c) an actuator, which actuates in response to the sensor readings. We might need to examine that every one paths from the sensor (i.e., the origin, or e1 in (d1) and (d2) in Determine 3) to the actuator (e3) undergo the checker (e2)—hardly a easy job in a system the place there could also be a number of makes use of of the sensor’s knowledge by a lot of totally different intermediate controllersor different system parts.
In a second situation from the area of knowledge safety, some secret data have to be despatched throughout an untrusted community. To take care of secrecy, we must always encrypt the information earlier than broadcasting it. However how can we decide that there aren’t any “leaks,” i.e., that no system parts processing or manipulating the key data can ship it instantly or not directly to the broadcasting aspect with out its first passing by means of the encryption module? We will use the attain by means of question, with the supply of the key data being the origin, the encryption module being the intermediate aspect, and the broadcasting aspect the goal.
Different Queries
From these 4 foundational queries, builders constructing automated analyses in OSATE can create extra complicated queries that in the end can reply deep questions on a system. The utility of this method is one thing we explored in our analysis of the OSATE Slicer.
How Properly Did We Do?
After creating the OSATE Slicer, we wished to guage each how helpful it’s and the way properly it performs. On the whole, we had been happy with the outcomes of our work, although as all the time, there’s extra to be finished.
How Helpful is the OSATE Slicer?
The primary place we used the slicer was within the Structure Supported Audit Processor (ASAP), an experimental automated security evaluation. ASAP had initially been created utilizing Awas, however sustaining that dependency proved difficult. We had been in a position to substitute Awas with the Slicer in our implementation of ASAP. Doing so was comparatively simple; whereas most of our current implementation transferred seamlessly, we did have to put in writing one customized question (described additional in the paper).
The second place we used the OSATE Slicer is in an as but unpublished re-implementation of OSATE’s current Fault Affect Evaluation (described in, e.g., this paper by Larson et al.), which considers the place a selected aspect’s fault or error can go (i.e., be propagated to) in a fully-specified system. This was trivial to reimplement utilizing the ahead slice question, after which—as a part of an ongoing analysis effort—we had been in a position to take issues a step additional with a handful of customized queries to validate foundational assumptions a couple of system mannequin that have to be true for the evaluation’s outcomes to be legitimate.
Wanting ahead, we’ve recognized two potential safety analyses that we’re desirous about updating to make use of the OSATE Slicer: an attack-tree calculator and a verifier that checks if a system meets the Bell-LaPadula safety coverage. Past that, there are different analyses that, at their core, discover properties of paths by means of a system. These can probably profit from the OSATE Slicer, although some are fairly complicated and should require further options to be added to the Slicer.
How Quick is the OSATE Slicer?
Of their publication on Awas, Thiagarajan et al. analyzed a corpus of 11 system fashions written in AADL. We got down to run the OSATE Slicer on this identical corpus in order that we might evaluate the efficiency of the 2 instruments. Sadly, whereas lots of the fashions had been open-source, model data and different key specifics crucial for reproducibility will not be current of their publication. We had been in a position to work instantly with them (we owe them thanks for that) as a part of this effort to get entry to most of these fashions and specifics, although, and have made an archive of the corpus accessible publicly as a part of this effort.
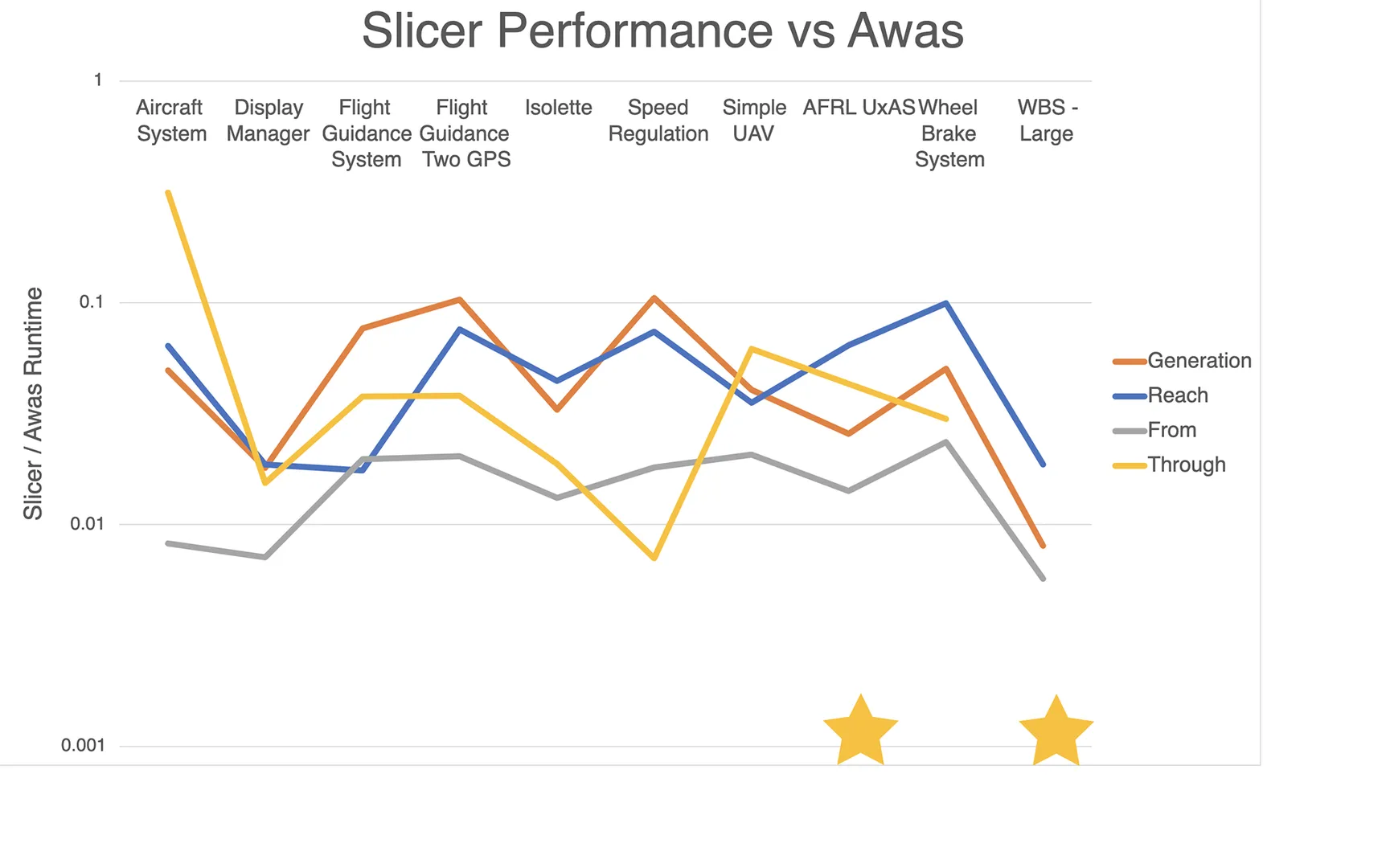
Determine 4: The efficiency of the OSATE Slicer relative to Awas, not the Y Axis is logarithmic
Total, we discovered the efficiency of the Slicer to be fairly passable: we noticed a 10-100x speedup over Awas on the technology and querying of almost all of the fashions within the corpus (see Determine 4). What’s extra, some attain by means of queries wouldn’t execute underneath Awas on two of the bigger fashions (denoted with ★ symbols within the determine), however we had been in a position to run them with out challenge utilizing our software.
Subsequent Steps: We’re On the lookout for Collaborators!
We’re excited in regards to the purposes of the OSATE Slicer, each those we’ve recognized on this put up and those who we haven’t even considered but. To assist us out with these, we’re all the time on the lookout for individuals to collaborate with—do you’ve got system fashions that you just’d like to investigate extra simply or shortly? In that case, please attain out. Since their inception, AADL and OSATE have been knowledgeable by the wants of DoD and industrial customers. The Slicer is not any totally different on this regard, and we welcome person ideas, suggestions, concepts, and collaborations to enhance the work.