Over the previous few years, SaaS has developed into the spine of company IT. Service companies, similar to medical practices, legislation companies, and monetary providers companies, are virtually completely SaaS based mostly. Non-service companies, together with producers and retailers, have about 70% of their software program within the cloud.
These functions include a wealth of knowledge, from minimally delicate common company info to extremely delicate mental property, buyer information, and worker information. Menace actors have famous this shift, and are actively working to breach apps to entry the info.
Listed here are the highest developments influencing the state of SaaS Safety for 2024 — and what you are able to do about it.
Democratization of SaaS
SaaS apps have reworked the best way organizations buy and use software program. Enterprise items buy and onboard the SaaS instruments that greatest match their wants. Whereas that is empowering for enterprise items which have lengthy been pissed off by delays in procuring and onboarding software program, it does require organizations to rethink the best way they safe information.
Safety groups are being pressured to develop new methods to safe firm information. Missing entry and visibility into an utility, they’re positioned within the function of advising a enterprise unit that’s utilizing SaaS functions. To additional complicate issues, each SaaS utility has completely different settings and makes use of completely different terminology to explain security measures. Safety groups cannot create a one-size-fits-all steering doc due to the variations between the apps.
Safety groups should discover new methods to collaborate with enterprise items. They want a software that gives visibility and steering for every utility setting in order that they – and the enterprise unit – perceive the dangers and ramifications concerned within the configuration decisions that they make.
ITDR Types a Vital Security Web
If a risk actor positive aspects entry to a high-privilege account, they achieve unfettered entry inside the utility. Organizations at the moment are understanding that id is the de facto perimeter for his or her SaaS functions.
When risk actors take over a certified person account, they sometimes observe frequent ways, methods and procedures (TTP) as they work their manner by way of the app towards the info they need. They depart behind indicators of compromise (IoC), which may be based mostly on actions taken inside the app or logs.
As we transfer into the brand new 12 months, we’re going to see extra organizations adopting an Id Menace Detection & Response (ITDR) strategy. ITDR mitigates that concern. As a key part in Id Safety Posture Administration, ITDR capabilities can detect TTPs and IoCs, after which ship an alert to the incident response group. By ITDR, risk actors who’ve managed to breach the id perimeter can nonetheless be stopped earlier than they steal essential information or insert ransomware into the applying.
Study how ITDR will help you deal with these SaaS Safety developments right now
Cross-Border Compliance Means Extra Tenants to Safe
World corporations are more and more going through completely different regulatory necessities from one nation to the following. In consequence, 2024 will see a rise within the variety of geo-specific tenants as a part of the hassle to maintain information segmented in accordance with the completely different rules.
This alteration could have a restricted influence on software program prices as most SaaS app pricing relies on subscribers reasonably than tenants. Nonetheless, it can have a big influence on safety. Every tenant will have to be configured independently, and simply because one occasion of the applying is safe doesn’t suggest that every one tenants are safe.
To safe all these tenants, safety groups ought to search for a safety resolution that enables them to set app benchmarks, examine tenants, and show safety settings side-by-side with out charging further for every further tenant. By making use of greatest practices all through the group, corporations can maintain all their tenants safe.
 |
| Determine 1: Adaptive Protect’s platform monitoring and presenting all Salesforce tenants |
Misconfigured Settings Are Resulting in New Exploits
A default misconfiguration in ServiceNow triggered widespread panic in October. The setting, which was a part of the applying’s Entry Management Lists, allowed unauthorized customers to extract information from information. The misconfiguration impacted 1000’s of corporations. An identical misconfiguration in Salesforce Neighborhood again in Can also impacted a big variety of corporations and led to information breaches.
Misconfigurations like these have the potential to trigger main injury to corporations. They result in information leaks that break the belief between corporations and their stakeholders, and have the potential to show into onerous fines, relying on the character of the info that leaked.
Securing misconfigurations is a corporation’s greatest likelihood at stopping these exploits from impacting their operations and hurting their backside strains.
See the right way to automate SaaS misconfigurations and regain management of your SaaS stack
Elevated Reliance on Third-Occasion Purposes Provides to SaaS Threat
Third-party functions add actual worth for finish customers. They enhance processes, prolong performance, and join information between a number of functions. Customers join these SaaS apps with the press of button, and immediately start bettering their workflows.
In March 2023, Adaptive Protect launched a report exhibiting that organizations utilizing Google Office with 10,000-20,000 customers averaged 13,913 third-party apps linked to Google Office alone. An astonishing 89% of those requested both high- or medium-risk permissions. Many of those high-risk apps are used as soon as and forgotten about, or utilized by a small variety of staff. Nonetheless, even these dormant or calmly used functions have important permissions and can be utilized to compromise or breach a SaaS utility.
The usage of third-party functions is just rising, as extra apps are developed and staff use their very own judgment – reasonably than checking with their safety group – when integrating third-party functions into their stack. Safety groups should develop visibility into all their built-in apps, and achieve insights into the permissions requested, the worth the app contributes to the group, and the chance it poses.
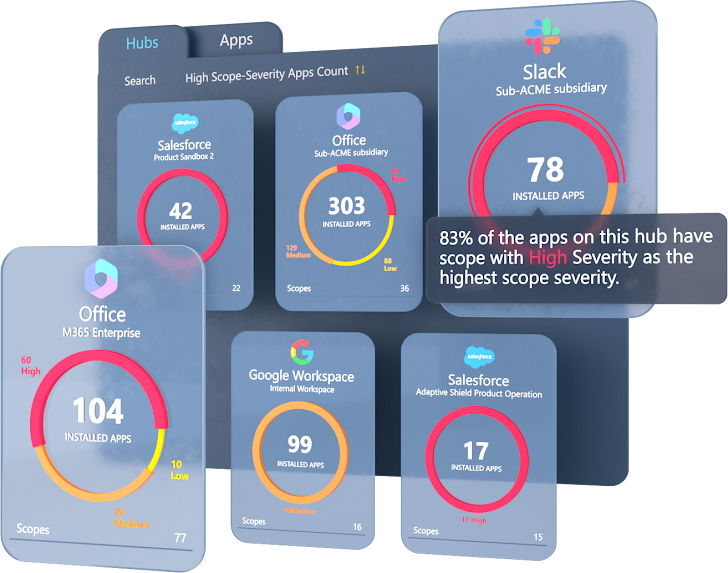 |
| Determine 2: Adaptive Protect’s platform reveals built-in third-party apps, their danger rating, and the scopes granted |
A number of Units to Safe as Working from Residence Is not Going Wherever
In 2023, almost 40% of all staff labored from dwelling at the very least a part of the time. In accordance with WFHResearch, roughly 12% of staff work solely of their houses, whereas one other 28% have hybrid roles.
These figures ought to give pause to safety personnel involved about customers logging in to their work accounts from private units. One of many largest issues safety groups have is when high-privileged customers log into their accounts utilizing an unmanaged or unsecured gadget. These units might have essential vulnerabilities, and create a brand new assault vector. For a lot of groups, there may be virtually no approach to inform which units are used to entry the SaaS app or see whether or not these units are safe.
Organizations Are Turning to SSPM to Safe SaaS
Whereas all these developments level to respectable SaaS safety issues, SaaS Safety Posture Administration (SSPM) instruments coupled with ITDR capabilities, like Adaptive Protect, can totally safe the SaaS stack. SSPMs are designed to robotically monitor configurations, searching for configuration drifts that weaken an app’s posture. In SaaS Safety Survey, 2024 Plans & Priorities by Cloud Safety Affiliation and Adaptive Protect, 71% of respondents mentioned their firm had elevated their funding into SaaS safety instruments over the previous 12 months, and 80% have been both already suing SSPM or deliberate to spend money on one inside the subsequent 18 months.
SSPMs can present baselining instruments for a number of tenants of the identical app, and allow customers to ascertain greatest practices, examine settings from completely different cases, and enhance the general posture of the SaaS stack.
SSPMs additionally detect and monitor third-party functions, alerting customers if their built-in apps are requesting an excessive amount of entry and updating the safety group when built-in apps are dormant. It tracks customers, and screens the units getting used to entry functions to forestall the usage of unmanaged or unsecured units on company SaaS apps. Moreover, their built-in communication instruments make it simple for enterprise items to collaborate with safety personnel in securing their functions.
SaaS apps have grown in reputation for good cause. They permit organizations to scale as wanted, subscribe to the apps they want in the meanwhile, and restrict funding in some IT. With SSPM, these functions will be secured as nicely.
See reside in a ten-minute demo how one can begin securing your SaaS stack


