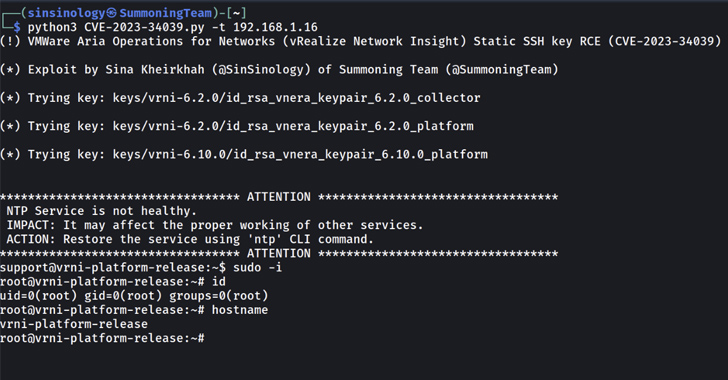
Proof-of-concept (PoC) exploit code has been made obtainable for a lately disclosed and patched crucial flaw impacting VMware Aria Operations for Networks (previously vRealize Community Perception).
The flaw, tracked as CVE-2023-34039, is rated 9.8 out of a most of 10 for severity and has been described as a case of authentication bypass as a consequence of an absence of distinctive cryptographic key era.
“A malicious actor with community entry to Aria Operations for Networks might bypass SSH authentication to achieve entry to the Aria Operations for Networks CLI,” VMware mentioned earlier this week.
Summoning Group’s Sina Kheirkhah, who revealed the PoC following an analyzing the patch by VMware, mentioned the basis trigger might be traced again to a bash script containing a way named refresh_ssh_keys(), which is accountable for overwriting the present SSH keys for the help and ubuntu customers within the authorized_keys file.
“There may be SSH authentication in place; nevertheless, VMware forgot to regenerate the keys,” Kheirkhah mentioned. “VMware’s Aria Operations for Networks had hard-coded its keys from model 6.0 to six.10.”

VMware’s newest fixes additionally handle CVE-2023-20890, an arbitrary file write vulnerability impacting Aria Operations for Networks that might be abused by an adversary with administrative entry to jot down information to arbitrary areas and obtain distant code execution.
In different phrases, a menace actor might leverage the PoC to acquire admin entry to the machine and exploit CVE-2023-20890 to run arbitrary payloads, making it essential that customers apply the updates to safe in opposition to potential threats.
The discharge of the PoC coincides with the virtualization expertise big issuing fixes for an high-severity SAML token signature bypass flaw (CVE-2023-20900, CVSS rating: 7.5) throughout a number of Home windows and Linux variations of VMware Instruments.
“A malicious actor with man-in-the-middle (MITM) community positioning within the digital machine community could possibly bypass SAML token signature verification, to carry out VMware Instruments Visitor Operations,” the corporate mentioned in an advisory launched Thursday.
Peter Stöckli of GitHub Safety Lab has been credited with reporting the flaw, which impacts the next variations –
- VMware Instruments for Home windows (12.x.x, 11.x.x, 10.3.x) – Fastened in 12.3.0
- VMware Instruments for Linux (10.3.x) – Fastened in 10.3.26
- Open-source implementation of VMware Instruments for Linux or open-vm-tools (12.x.x, 11.x.x, 10.3.x) – Fastened in 12.3.0 (to be distributed by Linux distributors)
The event additionally comes as Fortinet FortiGuard Labs warned of continued exploitation of Adobe ColdFusion Vulnerabilities by menace actors to deploy cryptocurrency miners and hybrid bots comparable to Devil DDoS (aka Lucifer) and RudeMiner (aka SpreadMiner) which can be able to finishing up cryptojacking and distributed denial-of-service (DDoS) assaults.
Additionally deployed is a backdoor named BillGates (aka Setag), which is understood for hijacking methods, stealing delicate info, and initiating DDoS assaults.