A brand new assortment of eight course of injection methods, collectively dubbed PoolParty, could possibly be exploited to realize code execution in Home windows methods whereas evading endpoint detection and response (EDR) methods.
SafeBreach researcher Alon Leviev stated the strategies are “able to working throughout all processes with none limitations, making them extra versatile than current course of injection methods.”
The findings have been first introduced on the Black Hat Europe 2023 convention final week.
Cracking the Code: Study How Cyber Attackers Exploit Human Psychology
Ever questioned why social engineering is so efficient? Dive deep into the psychology of cyber attackers in our upcoming webinar.
Course of injection refers to an evasion approach used to run arbitrary code in a goal course of. A variety of course of injection methods exists, similar to dynamic hyperlink library (DLL) injection, transportable executable injection, thread execution hijacking, course of hollowing, and course of doppelgänging.
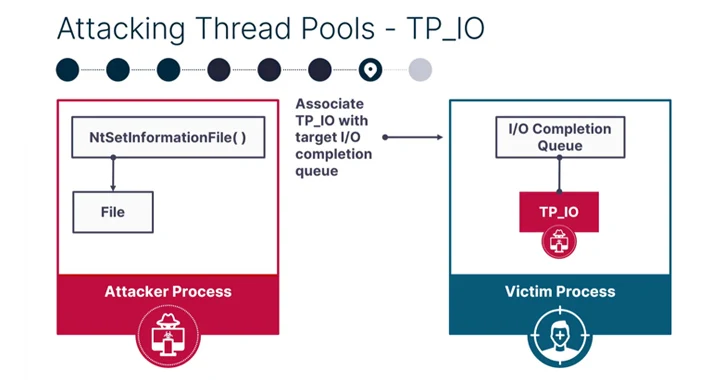
PoolParty is so named as a result of it is rooted in a part known as Home windows user-mode thread pool, leveraging it to insert any sort of labor merchandise right into a goal course of on the system.
It really works by focusing on employee factories – which confer with Home windows objects which are accountable for managing thread pool employee threads – and overwriting the beginning routine with malicious shellcode for subsequent execution by the employee threads.
“Apart from the queues, the employee manufacturing unit that serves because the employee threads supervisor could also be used to take over the employee threads,” Leviev famous.
SafeBreach stated it was in a position to devise seven different course of injection methods utilizing the duty queue (common work objects), I/O completion queue (asynchronous work objects), and the timer queue (timer work objects) primarily based on the supported work objects.
PoolParty has been discovered to realize 100% success charge towards standard EDR options, together with these from CrowdStrike, Cybereason, Microsoft, Palo Alto Networks, and SentinelOne.
The disclosure arrives practically six months after Safety Joes disclosed one other course of injection approach dubbed Mockingjay could possibly be exploited by risk actors to bypass safety options to execute malicious code on compromised methods.
“Although fashionable EDRs have developed to detect identified course of injection methods, our analysis has confirmed that it’s nonetheless doable to develop novel methods which are undetectable and have the potential to make a devastating affect,” Leviev concluded.
“Subtle risk actors will proceed to discover new and revolutionary strategies for course of injection, and safety instrument distributors and practitioners have to be proactive of their protection towards them.”