An up to date model of a botnet malware known as Prometei has contaminated greater than 10,000 methods worldwide since November 2022.
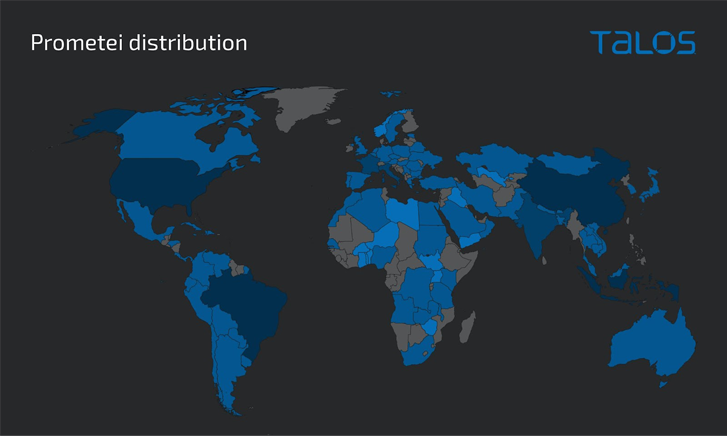
The infections are each geographically indiscriminate and opportunistic, with a majority of the victims reported in Brazil, Indonesia, and Turkey.
Prometei, first noticed in 2016, is a modular botnet that options a big repertoire of parts and a number of other proliferation strategies, a few of which additionally embrace the exploitation of ProxyLogon Microsoft Change Server flaws.
It is also notable for avoiding placing Russia, suggesting that the risk actors behind the operation are seemingly based mostly within the nation.
The cross-platform botnet’s motivations are monetary, primarily leveraging its pool of contaminated hosts to mine cryptocurrency and harvest credentials.
The most recent variant of Prometei (known as v3) improves upon its current options to problem forensic evaluation and additional burrow its entry on sufferer machines, Cisco Talos mentioned in a report shared with The Hacker Information.
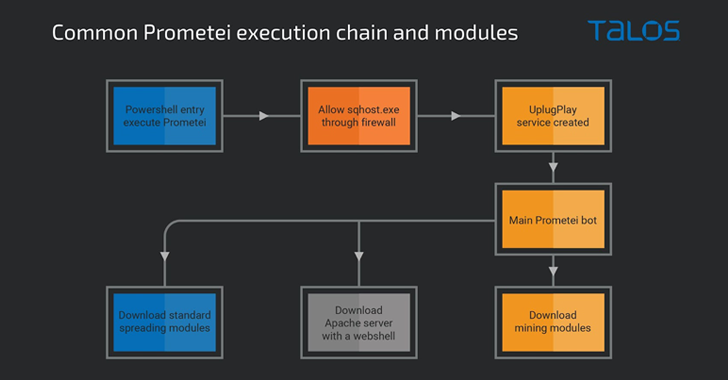
The assault sequence proceeds thus: Upon gaining a profitable foothold, a PowerShell command is executed to obtain the botnet payload from a distant server. Prometei’s major module is then used to retrieve the precise crypto-mining payload and different auxiliary parts on the system.
A few of these help modules operate as spreader packages designed to propagate the malware by means of Distant Desktop Protocol (RDP), Safe Shell (SSH), and Server Message Block (SMB).
Uncover the Hidden Risks of Third-Celebration SaaS Apps
Are you conscious of the dangers related to third-party app entry to your organization’s SaaS apps? Be a part of our webinar to study in regards to the sorts of permissions being granted and how you can decrease threat.
Prometei v3 can be noteworthy for utilizing a website technology algorithm (DGA) to construct out its command-and-control (C2) infrastructure. It additional packs in a self-update mechanism and an expanded set of instructions to reap delicate information and commandeer the host.
Final however not least, the malware deploys an Apache net server that is bundled with a PHP-based net shell, which is able to executing Base64-encoded instructions and finishing up file uploads.
“This latest addition of latest capabilities [indicates] that the Prometei operators are constantly updating the botnet and including performance,” Talos researchers Andrew Windsor and Vanja Svajcer mentioned.