An up to date model of a malware loader generally known as BLISTER is getting used as a part of SocGholish an infection chains to distribute an open-source command-and-control (C2) framework known as Mythic.
“New BLISTER replace contains keying function that enables for exact focusing on of sufferer networks and lowers publicity inside VM/sandbox environments,” Elastic Safety Labs researchers Salim Bitam and Daniel Stepanic mentioned in a technical report revealed late final month.
BLISTER was first uncovered by the corporate in December 2021 performing as a conduit to distribute Cobalt Strike and BitRAT payloads on compromised methods.
Using the malware alongside SocGholish (aka FakeUpdates), a JavaScript-based downloader malware, to ship Mythic was beforehand disclosed by Palo Alto Networks Unit 42 in July 2023.
In these assaults, BLISTER is embedded inside a reliable VLC Media Participant library in an try to get round safety software program and infiltrate sufferer environments.
Detect, Reply, Defend: ITDR and SSPM for Full SaaS Safety
Uncover how Identification Risk Detection & Response (ITDR) identifies and mitigates threats with the assistance of SSPM. Discover ways to safe your company SaaS functions and defend your knowledge, even after a breach.
Each SocGholish and BLISTER have been utilized in tandem as a part of a number of campaigns, with the latter used as a second-stage loader to distribute Cobalt Strike and LockBit ransomware, as evidenced by Crimson Canary and Development Micro in early 2022.
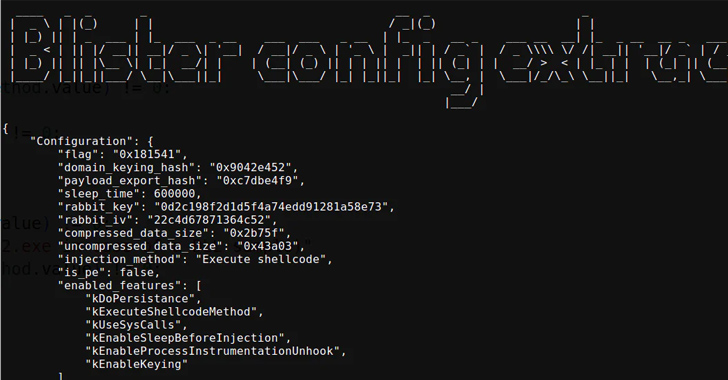
A better evaluation of the malware reveals that it is being actively maintained, with the malware authors incorporating a slew of methods to fly below the radar and complicate evaluation.
“BLISTER is a loader that continues to remain below the radar, actively getting used to load quite a lot of malware together with clipbankers, info stealers, trojans, ransomware, and shellcode,” Elastic famous in April 2023.