DevSecOps just isn’t merely a expertise, a pipeline, or a system. It’s a complete socio-technical surroundings that encompasses the individuals in sure roles, the processes that they’re fulfilling, and the expertise used to offer a functionality that leads to a related services or products being supplied to satisfy a necessity. In a lot less complicated phrases, DevSecOps encompasses all the most effective software program engineering ideas identified in the present day with an emphasis on sooner supply by elevated collaboration of all stakeholders leading to safer, useable, and higher-quality software program methods. On this weblog publish, we current a DevSecOps Platform-Unbiased Mannequin (PIM), which makes use of mannequin primarily based system engineering (MBSE) constructs to formalize the practices of DevSecOps pipelines and set up related steering. This primary-of-its-kind mannequin provides software program improvement enterprises the construction and articulation wanted for creating, sustaining, securing, and bettering DevSecOps pipelines.
Though firms have adopted, applied, and benefited from DevSecOps, many challenges stay in extremely regulated and cybersecurity-constrained environments, akin to protection, banking, and healthcare. These firms and authorities companies lack a constant foundation for managing software-intensive improvement, cybersecurity, and operations in a high-speed lifecycle. There are requirements being printed for DevSecOps, such because the not too long ago printed IEEE 2675 working group normal, however this steering and different reference structure design nonetheless requires a substantial quantity of interpretation for any specific group to use efficiently. A reference design doesn’t deal with technique, coverage, or acquisition, but organizations are leaping proper in to construct or purchase the assorted parts outlined in a reference design with out the mandatory planning or understanding of why sure design choices have been made.
Our crew was not too long ago brainstorming on how we might guarantee a DevSecOps pipeline and presumably stop assaults that focused the pipeline, not simply the applying or system being developed. We realized that it was too difficult to guarantee a pipeline as a result of complexity and lack of a single supply of reality of what DevSecOps encompasses. To handle this downside, we determined it was finest to mix a MBSE method and enterprise structure to seize the social, technical, and course of elements of a DevSecOps ecosystem throughout its lifecycle. The result’s a platform-independent mannequin (PIM), which we focus on beneath.
What Is the DevSecOps Platform-Unbiased Mannequin and Why Is It Wanted?
An authoritative reference is required to allow organizations to completely design and execute an built-in DevSecOps technique wherein all stakeholder wants are addressed. Most literature discussing DevSecOps depicts it utilizing some variation of the infinity diagram proven in Determine 1 beneath. This diagram is a high-level conceptual depiction since DevSecOps is a cultural and engineering follow that breaks down boundaries and opens collaboration between the event, safety, and operations organizations utilizing automation to deal with speedy, frequent supply of safe infrastructure and software program to manufacturing.
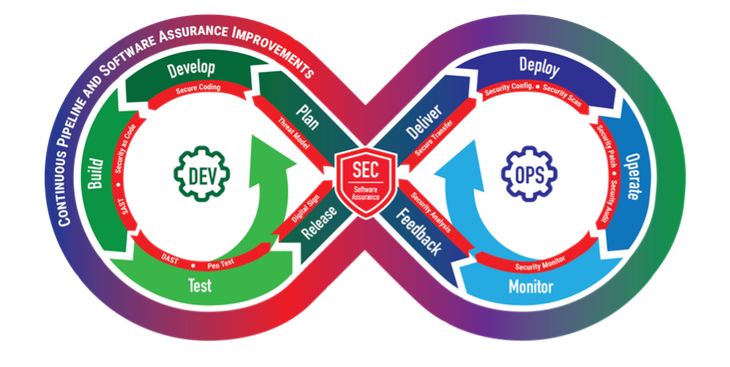
Determine 1: DevSecOps Infinity Diagram
One instance of this collaboration is engineering safety into all elements of the DevSecOps pipeline to display and check safety issues for each the pipeline and the product. Whereas giant organizations have efficiently applied some elements of DevSecOps on smaller initiatives, they’ll wrestle to implement these similar strategies on large-scale initiatives. Even in small, comparatively profitable initiatives, substantial lack of productiveness can happen when technical debt and inadequate safety and operational practices are in place. This loss usually outcomes from inadequate information, expertise, and reference supplies wanted to completely design and execute an built-in DevSecOps technique wherein all stakeholder wants are addressed.
Whereas organizations, initiatives, and groups need to reap the pliability and pace anticipated by the implementation of DevSecOps ideas, practices, and instruments, the lacking reference materials should first be addressed to make sure that DevSecOps is applied in a safe, secure, and sustainable manner. We created the DevSecOps PIM to handle this want by enabling organizations, initiatives, groups, and acquirers to
- specify DevSecOps necessities to the lead system integrators tasked with creating a platform-specific answer that features the designed system and steady integration/steady deployment (CI/CD) pipeline
- determine organizational, undertaking, and crew information and expertise gaps
- assess and analyze various pipeline performance and have modifications because the system evolves
- apply DevSecOps strategies to complicated merchandise that don’t comply with well-established software program architectural patterns utilized in trade
- present a foundation for risk and assault floor evaluation to construct a cyber assurance case to display that the product and DevSecOps pipeline are sufficiently free from vulnerabilities and that they perform solely as supposed
Whereas one can search “DevSecOps” on the Web and discover a variety of literature that paints an image of what DevSecOps may very well be or ought to be, this literature just isn’t definitive and requires a substantial quantity of interpretation, significantly for closely regulated and cybersecurity-constrained environments. This interpretation leads to
- DevSecOps views not being totally built-in in organizational steering and coverage paperwork
- initiatives being unable to carry out an evaluation of options (AoA) relating to the DevSecOps pipeline instruments and processes
- a number of initiatives utilizing comparable infrastructure and pipelines in numerous and incompatible methods, even inside the similar group
- suboptimal instruments and safety controls
To handle these issues the DevSecOps PIM supplies
- constant steering and modeling functionality that guarantee all correct layers and improvement issues related to the wants of the group, undertaking, and crew are captured
- the premise for making a DevSecOps Platform-Particular Mannequin (PSM) that may be included into the product’s model-based engineering method because the DevSecOps grasp mannequin is included within the product’s mannequin. This PSM permits correct modeling of DevSecOps design trades inside a undertaking’s AoA processes, leading to less expensive and safer merchandise.
- the premise for metrics and documentation of trade-offs to seize and analyze by the model-based engineering method. The mannequin supplies dynamic matrices of whether or not these factors have been addressed, how they have been addressed, and the way effectively the corresponding (to the factors) module is roofed.
- the premise for performing danger modeling in opposition to choices and DevSecOps model-based engineering to make sure safety controls and processes are correctly chosen and deployed
Addressing the Bigger Assault Floor of the Mission
A DevSecOps pipeline is a method for constructing merchandise that assist a corporation’s mission. To construct a pipeline, first develop enterprise instances and necessities to outline the features that the assorted applied sciences will deal with. These instances and necessities are additional refined, feeding the pipeline and establishing the event cadence for an built-in pipeline and infrastructure, as proven in Determine 2 beneath.
Instruments and infrastructure capabilities are then chosen to permit designers, architects, builders, testers, verifiers, customers, operators, and different related stakeholders to work collectively to supply the merchandise wanted to satisfy the aims utilizing the pipeline (as depicted within the Merchandise field in Determine 2). As well as, a parallel group of members implements and helps the automation that permits product creators to construct and facilitate administration oversight (as depicted within the Functionality Supply field in Determine 2).
Every of those roles requires specialised technical experience, and every department depends on the identical instruments, repositories, and processes structured by the pipeline. The pipeline should be structured to permit every related stakeholder to entry what they should carry out their position. Furthermore, the processes should be organized so that every exercise flows by the pipeline and is well handed off from one position to the subsequent all the best way from planning to supply.
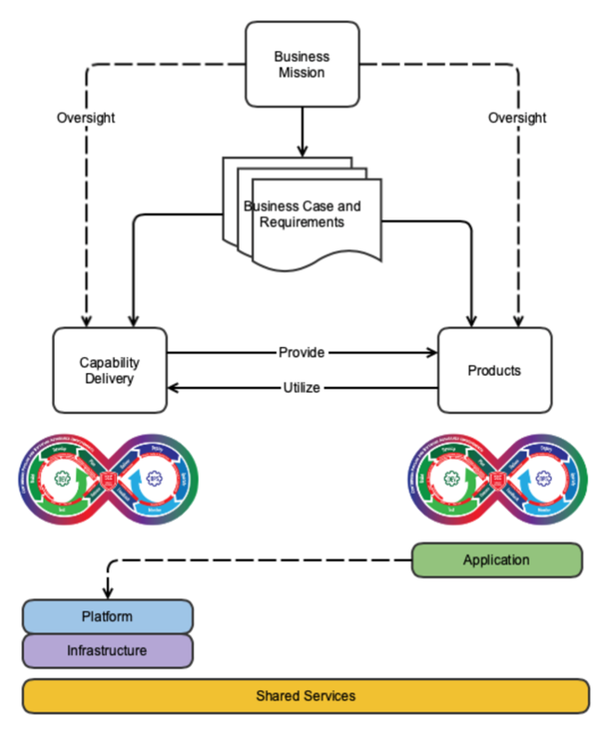
Determine 2: Built-in Pipeline and Infrastructure
The appliance and pipeline are constructed incrementally and up to date repeatedly to handle altering enterprise necessities, in addition to safety and expertise calls for. The pipeline encompasses the consumption to the discharge of software program and manages these flows predictably, transparently, and with minimal human intervention/effort .
A company should be aware of what it’s constructing to instantiate a DevSecOps pipeline that fulfills its specific wants. Sadly, there is no such thing as a one-size-fits-all pipeline. Every DevSecOps pipeline should be tailor-made to meet the wants of a selected program. In some instances, the potential supply may very well be extra sophisticated than the merchandise themselves.
The DevSecOps pipeline just isn’t merely instantiated as soon as and used all through the product’s lifecycle. As a substitute, it evolves repeatedly because the product evolves. The precise automation of processes is realized over time as a pipeline matures. This idea is captured within the DevSecOps PIM by the DevSecOps Functionality Supply Mannequin diagram represented in Determine 3 beneath. In that determine, the DevSecOps Functionality Supply Mannequin provides a number of new actions to the normal DevSecOps infinity diagram to signify the aware nature of creating and evolving a undertaking’s functionality supply pipeline.
Determine 3 additionally depicts an exercise movement that begins with enterprise, or mission wants that feed the groups’ planning actions and embrace the potential supply wants of the product. In flip, this exercise movement feeds the DevSecOps platform-independent mannequin (PIM), which is used to create a DevSecOps PSM that represents the present system and its deliberate updates, ideally maintained utilizing a model-based system engineering instrument.

Determine 3: DevSecOps Functionality Supply Mannequin
This DevSecOps PSM captures all socio-technical elements of the undertaking’s particular functionality supply pipeline. It permits the group to carry out trade-off analyses amongst options to make sure that the undertaking’s functionality supply pipeline is working in an economical and safe manner, whereas constantly assembly the wants of the product and all related stakeholders.
Primarily based on the PSM, the potential supply pipeline is configured and instantiated inside the Configure DevSecOps System exercise. The Configure DevSecOps System exercise is analogous to the idea of Infrastructure as Code (IaC) and Configuration as Code (CaC). The product is developed, secured, and operationalized through the use of the instantiated functionality supply pipeline.
All through the lifecycle of the product, information should be collected repeatedly from each the pipeline and the product beneath improvement. This information should be analyzed and evaluated through the Analyze System Suggestions exercise. If new dangers or enhancements are recognized, akin to safety vulnerabilities or the potential for not assembly contractual supply dates, then the Carry out Mannequin Evaluation exercise is used to judge options to the present functionality supply pipeline instantiation. Ensuing modifications are modeled after which applied within the Configure DevSecOps System exercise, and the method repeats.
Necessities modifications require danger evaluation, in addition to an analysis of the potential supply which may be impacted. Even with all this evaluation and work, we haven’t but addressed what the DevSecOps Infinity diagram actually represents. From a high-level modeling perspective, the DevSecOps Infinity diagram is solely represented because the Product Underneath Growth Most important Stream exercise proven in Determine 3 above. Breaking out the infinity diagram to the subsequent degree of abstraction would seem like determine 4 beneath. The complexity of the DevSecOps pipeline grows shortly, which motivates us to discover why a DevSecOps Platform-Unbiased Mannequin is required.
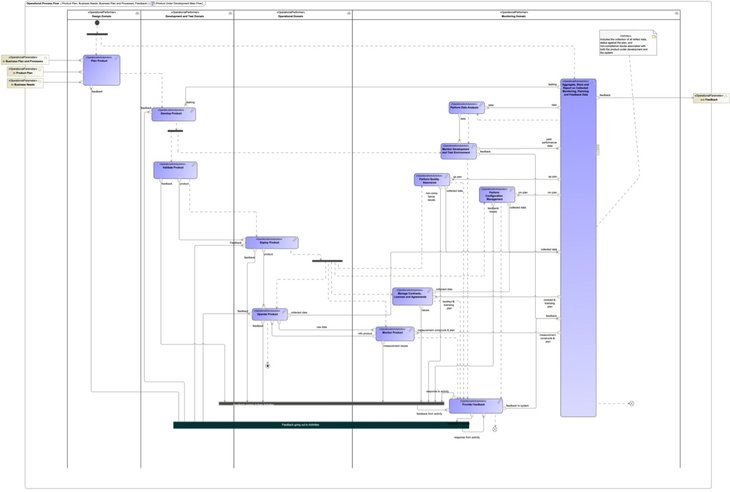
Determine 4: Product Underneath Growth Most important Stream
Giant, complicated, closely regulated, and cybersecurity-constrained initiatives have already embraced model-based engineering however haven’t utilized the identical strategies to their DevSecOps CI/CD pipelines. This limitation impedes a undertaking’s skill to construct a cyber-physical software program manufacturing unit that’s match for function. Establishing a DevSecOps PIM allows initiatives to develop a sturdy framework for making a custom-made mannequin the place the system’s structure and the DevSecOps pipeline structure aren’t in battle and the place they deal with the bigger assault floor of the undertaking. This mannequin allows DevSecOps to develop into part of the enterprise structure of the product being constructed. In distinction, present practices don’t embrace DevSecOps within the total product structure and thus don’t combine successfully with the compliance and operational context of the undertaking.


