Banking and monetary companies organizations are the targets of a brand new multi-stage adversary-in-the-middle (AitM) phishing and enterprise e mail compromise (BEC) assault, Microsoft has revealed.
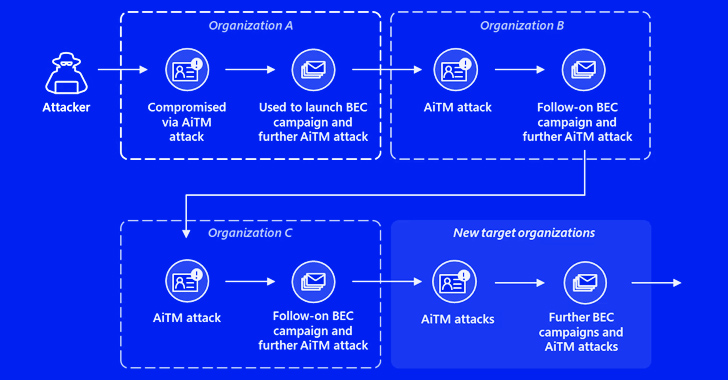
“The assault originated from a compromised trusted vendor and transitioned right into a collection of AiTM assaults and follow-on BEC exercise spanning a number of organizations,” the tech large disclosed in a Thursday report.
Microsoft, which is monitoring the cluster underneath its rising moniker Storm-1167, referred to as out the group’s use of oblique proxy to drag off the assault.
This enabled the attackers to flexibly tailor the phishing pages to their targets and perform session cookie theft, underscoring the continued sophistication of AitM assaults.
The modus operandi is not like different AitM campaigns the place the decoy pages act as a reverse proxy to reap credentials and time-based one-time passwords (TOTPs) entered by the victims.
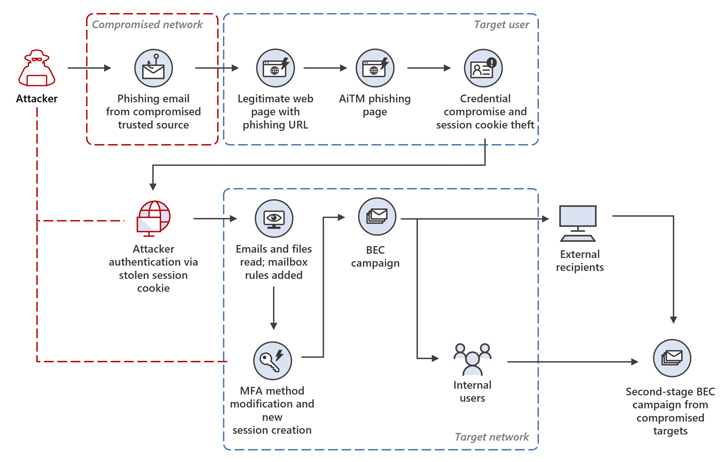
“The attacker introduced targets with an internet site that mimicked the sign-in web page of the focused software, as in conventional phishing assaults, hosted on a cloud service,” Microsoft stated.
“The stated sign-in web page contained sources loaded from an attacker-controlled server, which initiated an authentication session with the authentication supplier of the goal software utilizing the sufferer’s credentials.”
The assault chains start with a phishing e mail that factors to a hyperlink, which, when clicked, redirects a sufferer into visiting a spoofed Microsoft sign-in web page and coming into their credentials and TOTPs.
The harvested passwords and session cookies are then used to impersonate the person and acquire unauthorized entry to the e-mail inbox by the use of a replay assault. The entry is then abused to pay money for delicate emails and orchestrate a BEC assault.
What’s extra, a brand new SMS-based two-factor authentication technique is added to the goal account to be able to sign up utilizing the pilfered credentials sans attracting any consideration.
Within the incident analyzed by Microsoft, the attacker is alleged to have initiated a mass spam marketing campaign, sending greater than 16,000 emails to the compromised person’s contacts, each inside and out of doors of the group, in addition to distribution lists.
The adversary has additionally been noticed taking steps to reduce detection and set up persistence by responding to incoming emails and subsequently taking steps to delete them from the mailbox.
Finally, the recipients of the phishing emails are focused by a second AitM assault to steal their credentials and set off yet one more phishing marketing campaign from the e-mail inbox of one of many customers whose account was hacked because of the AitM assault.

Uncover the untapped vulnerabilities in your API ecosystem and take proactive steps in the direction of ironclad safety. Be part of our insightful webinar!
“This assault exhibits the complexity of AiTM and BEC threats, which abuse trusted relationships between distributors, suppliers, and different companion organizations with the intent of monetary fraud,” the corporate added.
The event comes lower than a month after Microsoft warned of a surge in BEC assaults and the evolving ways employed by cybercriminals, together with the usage of platforms, like BulletProftLink, for creating industrial-scale malicious mail campaigns.
One other tactic entails the usage of residential web protocol (IP) addresses to make assault campaigns seem domestically generated, the tech large stated.
“BEC menace actors then buy IP addresses from residential IP companies matching the sufferer’s location creating residential IP proxies which empower cybercriminals to masks their origin,” Redmond defined.
“Now, armed with localized handle house to assist their malicious actions along with usernames and passwords, BEC attackers can obscure actions, circumvent ‘not possible journey’ flags, and open a gateway to conduct additional assaults.”