
Microsoft’s Digital Crimes Unit seized a number of domains utilized by a Vietnam-based cybercrime group (Storm-1152) that registered over 750 million fraudulent accounts and raked in thousands and thousands of {dollars} by promoting them on-line to different cybercriminals.
Storm-1152 is a serious cybercrime-as-a-service supplier and the primary vendor of fraudulent Outlook accounts, in addition to different unlawful “merchandise,” together with an computerized CAPTCHA-solving service to bypass Microsoft’s CAPTCHA challenges and register extra fraudulent Microsoft electronic mail accounts.
“Storm-1152 runs illicit web sites and social media pages, promoting fraudulent Microsoft accounts and instruments to bypass id verification software program throughout well-known know-how platforms. These companies cut back the effort and time wanted for criminals to conduct a number of legal and abusive behaviors on-line,” in accordance with Amy Hogan-Burney, the Basic Supervisor of Microsoft’s Digital Crimes Unit.
“Since a minimum of 2021, the Defendants have been engaged in a scheme to acquire thousands and thousands of Microsoft Outlook electronic mail accounts within the names of fictitious customers based mostly on a sequence of false representations, after which promote these fraudulent accounts to malicious actors to be used in varied kinds of cybercrime,” in accordance with the criticism.
In line with Microsoft Risk Intelligence, quite a few cybergroups concerned in ransomware, information theft, and extortion have purchased and used accounts offered by Storm-1152 of their assaults.
As an example, financially-motivated Storm-0252, Storm-0455, and Octo Tempest (aka Scattered Spider) cybercrime gangs used Storm-1152 fraudulent accounts to infiltrate organizations worldwide and deploy ransomware on their networks.
The ensuing service disruptions resulted in damages estimated by Microsoft to be within the a whole lot of thousands and thousands of {dollars}.
“Upon data and perception, proof gathered to date by Microsoft’s investigation on this case exhibits that Microsoft electronic mail accounts—which had been fraudulently obtained by Defendants and bought to cybercriminals—have been utilized by organized cybercrime teams recognized to Microsoft as Storm-0252, Storm-0455, and Octo Tempest to have interaction in cybercrime exercise, together with electronic mail phishing scams, that are continuously used as a automobile for spreading ransomware and different malware,” the criticism provides.
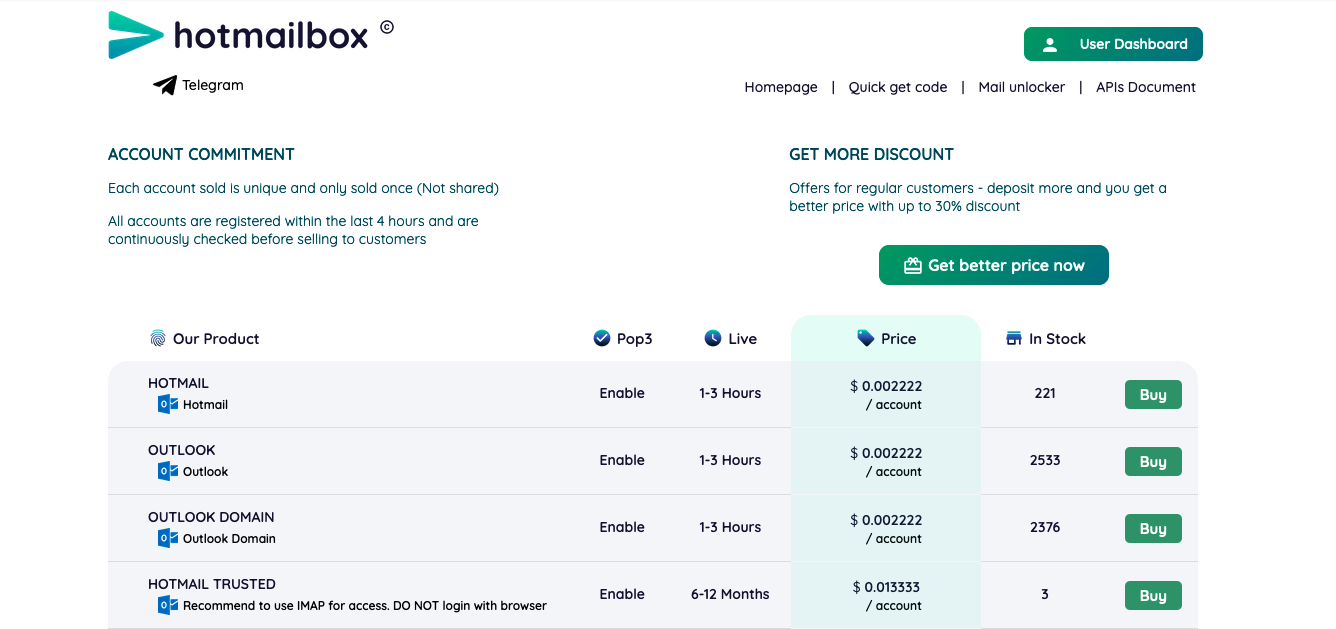
On December 7, Microsoft seized Storm-1152’s U.S.-based infrastructure and took down the next web sites after acquiring a courtroom order from the Southern District of New York:
- Hotmailbox.me, a web site promoting fraudulent Microsoft Outlook accounts
- 1stCAPTCHA, AnyCAPTCHA, and NoneCAPTCHA, web sites that facilitate the tooling, infrastructure, and promoting of the CAPTCHA fixing service to bypass the affirmation of use and account setup by an actual particular person. These websites bought id verification bypass instruments for different know-how platforms
- The social media websites actively used to market these companies
The corporate additionally sued Duong Dinh Tu, Linh Van Nguyen (a/okay/a Nguyen Van Linh), and Tai Van Nguyen for his or her purported involvement in internet hosting the cybercriminal operation on the seized domains.
As additional alleged within the criticism, the defendants managed and developed the code for the seized web sites. They had been additionally concerned in publishing video guides on the best way to use the fraudulent Outlook accounts and supplied chat help to ‘prospects’ utilizing their fraudulent companies.
“At the moment’s motion is a continuation of Microsoft’s technique of taking intention on the broader cybercriminal ecosystem and focusing on the instruments cybercriminals use to launch their assaults. It builds on our enlargement of a authorized methodology used efficiently to disrupt malware and nation-state operations,” Hogan-Burney mentioned.

