The SEI SBOM Framework helps organizations use a software program invoice of supplies (SBOM) for third-party software program administration. We created it, partially, in response to Government Order (EO) 14028, Bettering the Nation’s Cybersecurity. Launched within the wake of the SolarWinds and Apache Log4j provide chain assaults, EO 14028 requires U.S. authorities companies to reinforce software program provide chain safety, transparency, and integrity via the usage of SBOMs.
In case your group produces or provides software program for the U.S. authorities, maybe you’ve got already executed your due diligence and complied with EO 14028. You’ve analyzed your code, extracted the related knowledge, composed your SBOM, and made it out there. You possibly can declare victory and go away it at that. However take into account all the info you’ve got assembled and should keep—why not make good use of it?
On this SEI Weblog submit, I’ll study methods you’ll be able to leverage your SBOM knowledge, utilizing the SEI SBOM Framework, to enhance your software program safety and inform your provide chain danger administration.
The SBOM Is a Knowledge-Wealthy Useful resource
An SBOM is a proper file containing the small print and provide chain relationships of assorted parts utilized in constructing software program. Consider it as an annotated listing of components in your software program. To this point, so good. However when you think about that software program consists of many libraries and modules and different (typically open supply) parts, most of which have been produced by third events who, in flip, might incorporate parts from different third events additional upstream, a lot of which could have their very own SBOMs, you start to grasp that an SBOM can shortly develop into a really large knowledge repository.
To assist baseline SBOM knowledge, in July 2021 the Division of Commerce specified the minimal parts for an SBOM:
- provider identify: the identify of an entity that creates, defines, and identifies parts
- part identify: the designation assigned to a unit of software program outlined by the unique provider
- model of the part identifier: the identifier utilized by the provider to specify a change in software program from a beforehand recognized model
- different distinctive identifiers: different identifiers which might be used to establish a part, or function a look-up key for related databases
- dependency relationship: a characterization of the connection that an upstream part X is included in software program Y
- writer of SBOM knowledge: the identify of the entity that creates the SBOM knowledge for this part
- timestamp file: the date and time of the SBOM knowledge meeting
As you’ll be able to see, manually assembling an SBOM for all of the parts that compose a typical software program product would signify an enormous endeavor, even when you solely collected the minimal info required by the Division of Commerce. Nevertheless, most SBOMs are produced utilizing software program composition evaluation (SCA) instruments, which scan code to establish and catalog open supply software program (OSS) parts. To facilitate automation, the next machine- and human-readable knowledge codecs can be found for producing and consuming SBOMs:
Even with automation, creating SBOMs is a weighty, difficult job. The SEI SBOM Framework compiles a set of main practices for constructing and utilizing an SBOM to assist cyber danger discount. This tailor-made model of our Acquisition Safety Framework (ASF) supplies a roadmap for integrating SBOM utilization into the acquisition and growth efforts of a company to arrange for managing vulnerabilities and dangers in third-party software program, together with commercial-of-the-shelf (COTS) software program, government-of-the-shelf (GOTS) software program, and open supply software program (OSS).
The next sections counsel methods organizations can apply the SEI SBOM Framework to handle third-party software program and improve the safety of their software program growth pipelines and merchandise.
Leveraging Your SBOM Knowledge: 2 SEI SBOM Framework Use Circumstances
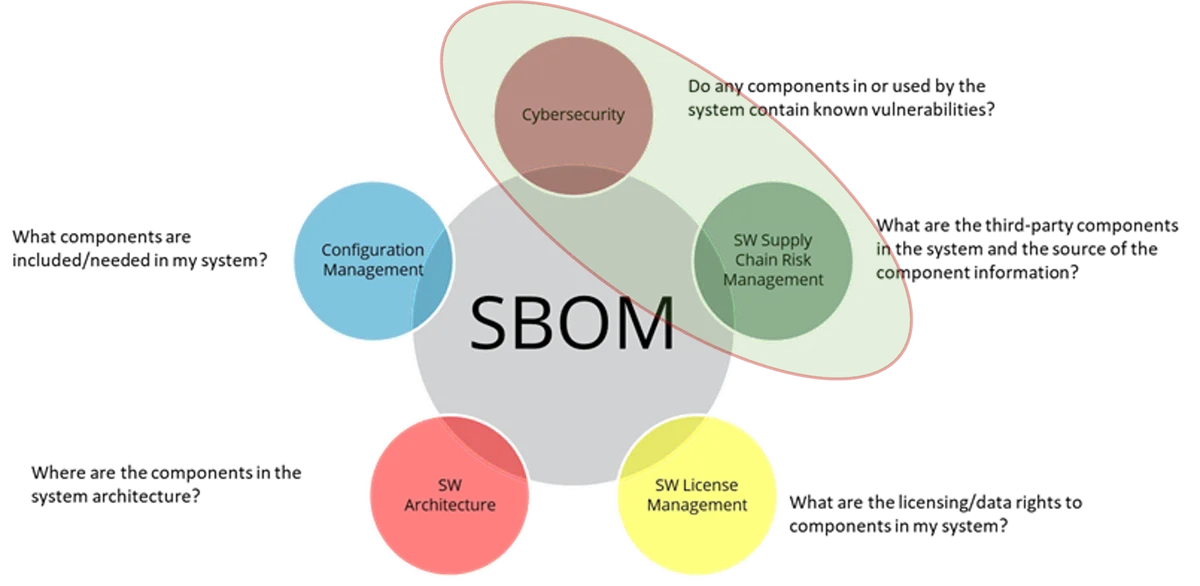
In our SEI Weblog submit introducing the SEI SBOM Framework, we famous 5 apply areas by which you need to use the framework to enhance third-party software program administration (Determine 1). On this submit, I’ll sketch use circumstances for 2 of those areas: cybersecurity and software program provide chain danger administration.
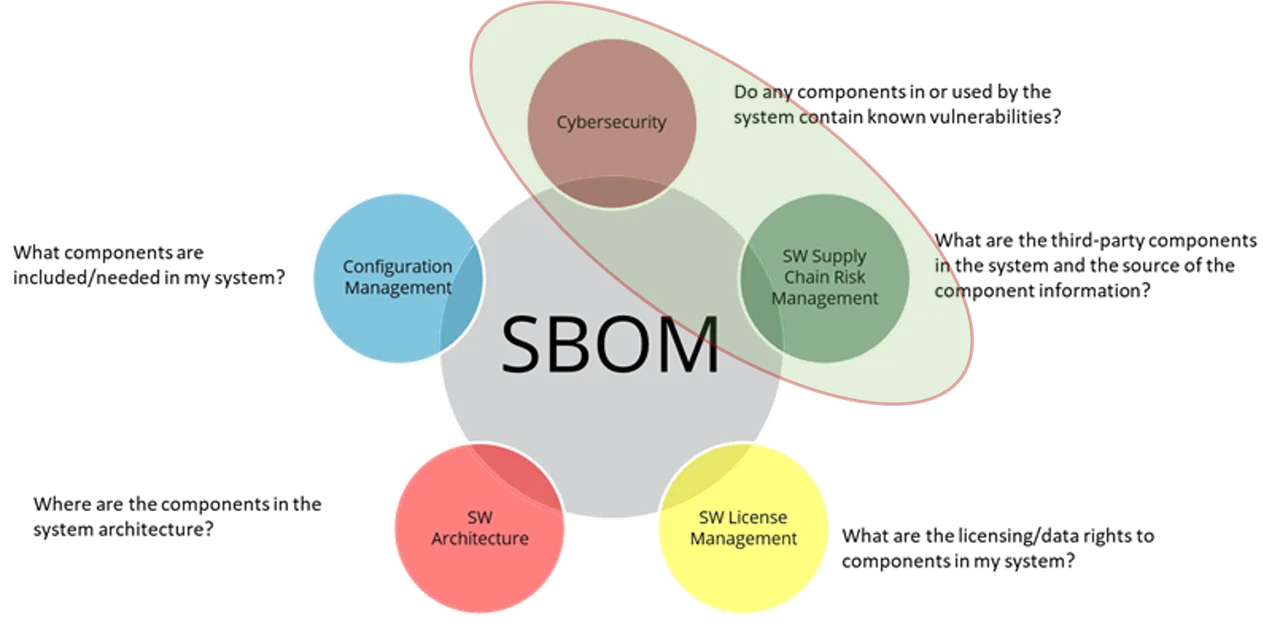
Determine 1: SBOM Framework Use Circumstances Examined in This SEI Weblog Publish
These two areas figured prominently within the motivation for the EO 14028 SBOM mandate within the wake of the SolarWinds assault, by which attackers injected malware into SolarWinds merchandise that unfold the malware via software program updates, and the exploitation of a vulnerability in Apache’s Log4j software program library, a software program part utilized by many different downstream functions. Most not too long ago, a vulnerability in MOVEit, a extensively used file-transfer part integrated in lots of software program packages, enabled attackers to steal info from all kinds of corporations and organizations, together with the U.S. Division of Power.
An SBOM Framework objective defines the end result or goal towards which a program’s effort is directed. Every SBOM objective is supported by a bunch of practices. Practices describe discrete actions that have to be carried out to attain a objective. Practices are framed as questions.
The SEI SBOM Framework construction (Determine 2) is tailored from the SEI Acquisition Safety Framework construction, which is designed to assist a program coordinate managing engineering and supply-chain dangers throughout system parts, together with {hardware}, community interfaces, software program interfaces, and mission. A company can use the SBOM Framework to establish gaps in the way it makes use of SBOM knowledge and to investigate what interventions would offer the best worth for the group. Beneath this multilayered framework, a number of apply areas comprise a number of domains, which in flip comprise a number of targets, which in flip comprise a number of practices.
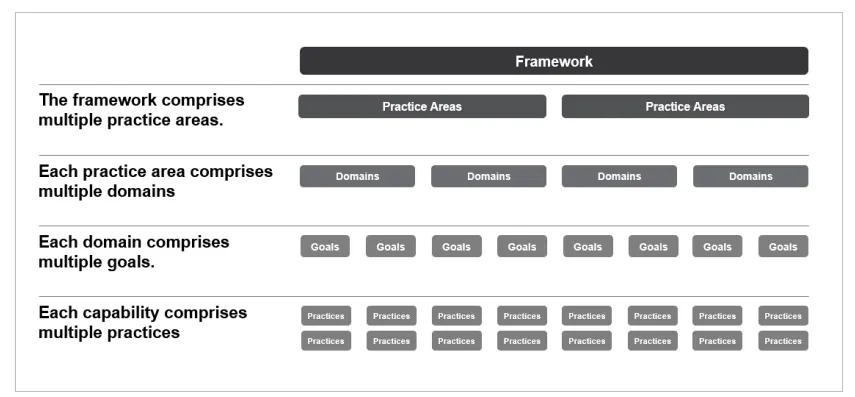
Determine 2: SEI SBOM Framework Construction
From our evaluation of SBOM use circumstances, we assembled a set of related practices, which we then mapped to the acquisition and growth lifecycle to establish related domains as follows: necessities, planning, construct/assemble, deploy/use, handle/assist, and infrastructure. A website is concentrated on a given technical or administration subject, reminiscent of program planning, danger administration, or necessities, and inside every area there are a number of targets supporting it.
USE CASE: Utilizing the SEI SBOM Framework to Enhance Cybersecurity by Managing Identified Vulnerabilities
On this use case, one vital objective related to cybersecurity is vulnerability administration. For every objective, the SBOM Framework focuses particular practices which might be framed as inquiries to encourage a company to discover how properly they’re addressing this apply. The next apply questions had been recognized in vulnerability administration related to SBOMs, and the linkage between SBOM knowledge and vulnerability knowledge supplies perception as as to if a susceptible software program part is in use on the group and poses a cybersecurity danger:
- Are recognized vulnerabilities and out there updates monitored for software program parts recognized within the system’s SBOM? Maintaining observe of recognized vulnerabilities and software program updates is a necessary exercise for efficient vulnerability administration. A well-designed SBOM will comprise details about your software program or system, all of the parts it includes, and the suppliers of these parts. Nevertheless, the present steering principally says you should observe to the primary stage of part use (e.g., you realize what you used, however not essentially under that stage). The secondary and decrease dependencies are unknown dangers until an SBOM provider signifies there aren’t any additional dependencies. This info might be paired with vulnerability info, reminiscent of that communicated via the Frequent Vulnerabilities and Exposures (CVE) listing maintained by MITRE, to assist warn you to any parts with recognized vulnerabilities. Notice that the vulnerability info is saved outdoors of the SBOM (not a part of it). Understanding what you’ve got, when it’s been uncovered, and really helpful mitigations can tremendously facilitate your vulnerability administration efforts.
- Are vulnerabilities in SBOM parts recognized? Right here we transfer from the system stage to the part stage. Scanning supply code and binaries to establish potential vulnerabilities is an choice open to every group. Whereas not all organizations have this experience available, unbiased service suppliers can help. Organizations ought to robotically scan and mitigate vulnerabilities within the supply code they’re creating. The proprietor of the software program might want to deal with the danger mitigation for third-party parts.
- Is the mission danger of every SBOM part assessed? Not all parts are equal. A vulnerability in a single part may result in catastrophic penalties if exploited, whereas a vulnerability in one other part would possibly stay unaddressed for months with out consequence. From a system perspective, understanding the place within the software program and system structure the affected parts are positioned is critical to judge the danger to the system. The software program and system structure info (e.g., implementation) isn’t a part of the SBOM info and can take some material experience (multidisciplinary method) to map these info sources. Mission threads, which hint the circulate of important mission actions via the expertise layers, can help in figuring out the parts of excessive significance. On this manner, you’ll be able to focus your vulnerability administration efforts on parts most important to mission success.
- Are software program updates prioritized based mostly on their potential influence to mission danger? For software program or methods comprising many third-party parts, managing updates for all these parts presents a frightening job. Having recognized the parts most crucial to mission success, it is best to prioritize these parts and allocate assets to updating the highest-priority parts first. In an ideal world, you’ll keep 100% updated on all part releases, however in the true world of restricted organizational assets and a gentle stream of updates for lots of of parts, that you must allocate assets correctly. Utilizing SBOM knowledge to establish and rank parts most crucial to mission success, you’ll be able to maintain important parts first and fewer important parts as time and assets permit.
- Are software program part opinions/updates performed based mostly on their mission-risk priorities? Simply as you prioritized software program updates based mostly on the extent of mission danger every part poses to your software program or system, so too must you prioritize part opinions. As soon as once more, the main focus right here is on utilizing the knowledge you’ve collected within the SBOM to establish parts most crucial to mission success and/or those who current the best mission danger ought to they be compromised. Doing so allows you to slim your focus within the face of an amazing quantity of knowledge and apply your assets successfully and effectively.
- Are vulnerability administration standing, dangers, and priorities tracked for every software program part? Your SBOM knowledge supplies you details about all of the parts in your system. Evaluating that knowledge with knowledge from a vulnerability listing service like CVE allows you to know when certainly one of your parts is in danger. Instruments can be wanted to do that successfully. When you’ve assessed and prioritized your parts based mostly on mission danger, will you realize whenever you final up to date a part? Are you able to simply decide the place a given part ranks when it comes to mission danger? What if a change to your software program or system has elevated the precedence of a part you as soon as thought-about low danger? To make the simplest use of your SBOM knowledge for ongoing vulnerability administration, that you must spend money on knowledge administration methods and practices.
The duties on this vulnerability administration use case, and in danger administration extra usually, provide help to establish and prioritize your most respected belongings. On this case, you’re making selections based mostly on mission danger. These selections contain tradeoffs. Right here, the tradeoff is defending your most respected parts, and due to this fact your software program and/or system, from severe hurt ensuing from vulnerabilities whereas permitting for the opportunity of an exploit of a vulnerability in a part with low mission danger. Such a tradeoff is inevitable for software program and/or methods with lots of or hundreds of parts.
USE CASE: Utilizing the SEI SBOM Framework to Enhance Provide Chain Threat Administration
The dearth of integration amongst a system’s expertise groups, together with suppliers, is one other supply of danger the place SBOM info may help scale back danger and enhance effectivity. {Hardware} has obtained many of the consideration up to now with considerations for counterfeits, however the rising influence of software program dealing with performance requires a deal with each. However groups typically work in stovepipes, and the groups who use provider software program and expertise providers/merchandise can also neglect to interact or oversee these suppliers. Improvement and assist groups typically work independently with various aims and priorities pushed by value and schedule calls for that don’t absolutely take into account present or potential danger.
One other consideration vital to the federal government is overseas possession, management, or affect (FOC) of organizations supplying the {hardware} and software program. That is additionally tracked outdoors of an SBOM however could possibly be built-in utilizing a free-form area.
On this use case, the next apply questions (which, keep in mind, are framed as evaluation questions) apply to the objective of Handle/Assist. The aim of this objective is to make sure that correct, full, and well timed SBOM knowledge is accessible for system parts to successfully handle danger. Connecting the SBOM knowledge with different provider info out there to the group strengthens the flexibility to handle provide chain danger administration. The precise apply questions are as follows:
- Are the suppliers for system parts recognized? This info can come from the SBOM. Understanding the suppliers may help you handle bug fixes, integration points, and different issues extra effectively. Some suppliers could also be unknown, reminiscent of for open-source parts, and this supplies an indicator of potential danger.
- Is provider knowledge reviewed periodically and up to date as wanted? Constructing an SBOM shouldn’t be a “one-and-done” exercise. Over time, info might change. As an illustration, the corporate who provided certainly one of your parts up to now fiscal yr might have been acquired by a bigger firm within the present fiscal yr. Deal with the SBOM as a part of the info that must be configuration managed and managed. To make sure your knowledge is helpful, that you must set up schedules and processes for holding provider knowledge present.
- Are SBOMs for system parts recognized, analyzed, and tracked? Third-party organizations producing system parts ought to be producing their very own SBOMs for these parts. Understanding what’s in these parts, what upstream dependencies would possibly exist, what model has been used, and different related knowledge is crucial whenever you’re working to resolve points launched via third-party part software program. Consequently, it is best to institute practices for figuring out SBOMs revealed for the third-party parts utilized in your software program. You must also decide what SBOM info is most related to your wants and study this info to judge what, if any, penalties incorporating the part may need in your system’s performance and safety. Bear in mind that software program might have exterior dependencies (e.g., Dynamic Hyperlink Libraries in Home windows), which won’t be within the SBOM as it’s at present outlined, since they’re runtime dependencies.
- Are SBOMs managed to make sure they’re present? Suppliers and merchandise are repeatedly altering. Efficient provider administration requires data of dependencies in order that single factors of failure and dangers for provider loss might be proactively managed. The extra your knowledge is outdated, the much less helpful it turns into. As an illustration, in case your SBOM knowledge tells you you’re utilizing model 2.0 of part X, however you’ve not too long ago up to date your system to model 2.4, you would possibly miss a vulnerability alert associated to model 2.4, inflicting ache in your customers or clients and risking the popularity of your group. Counting on the distributors to offer this info can even go away you in danger. You must develop and implement schedules and practices for holding your SBOMs updated that will require contributors from throughout the group (i.e., acquisition, engineering, and operations).
- Are the dangers associated to incomplete or lacking SBOM knowledge recognized and mitigated? There are typically plenty of high quality points with SBOMs which might be slowly being labored out (e.g., lacking or incomplete knowledge, non-compliance with the minimal parts steering, and many others.). The SBOMs have to be validated earlier than being accepted to be used (or revealed). As an illustration, lacking model info, or lacking details about an upstream subcomponent of the part you’ve integrated into your system, can delay or impede efforts to resolve danger in a well timed method. Within the case of lacking upstream dependency knowledge, you may not even concentrate on a provider drawback till it’s too late. You must guarantee you’ve got a system or apply for figuring out incomplete or lacking knowledge in your SBOMs, gathering that info, and updating your SBOMs. This would possibly imply working together with your suppliers to make sure their SBOMs are full and updated.
- Are dangers and limitations associated to managing and redistributing SBOM info recognized and managed? The requirement to make SBOM knowledge out there requires consideration of how extensively that knowledge can be shared. Many have expressed concern that it could actually pose issues associated to the disclosure of delicate or labeled info. Nevertheless, the SBOM is just a listing of the components and never the detailed description of how they’re assembled. If protections are wanted, since there can be consolidation of a variety of details about suppliers, making certain the knowledge is accessible to people who want it throughout the group and downstream within the provide chain have to be a major consideration.
- Is the provenance of SBOM knowledge established and maintained? The usefulness of SBOM knowledge rests on the diploma to which you’ll belief the info is correct and derives from authentic sources. You must analyze which knowledge is most vital to the safety of your system and develop processes to make sure the integrity of the info and the flexibility to hint the possession of that knowledge to a verifiable supply. These processes should be capable of accommodate provider consolidation, shifts in provider sources, and different regular acquisition enterprise processes.
Provider administration is a posh however more and more vital space of consideration for each group as our dependencies via expertise enhance. Leveraging out there SBOM info can set up a focus for gathering and sustaining this info in a sharable format, however timeliness and integrity of the info is important.
The SEI SBOM Framework: Making Software program Administration Extra Manageable
The mandate for SBOMs articulated in Government Order 14028 imposed a heavy raise for many who develop and handle software program supplied to the DoD and U.S. authorities. One results of all of the work that goes into creating an SBOM is much more knowledge to course of and handle. The excellent news is you could put that knowledge to work to enhance your efforts in cybersecurity, provide chain administration, software program license administration, software program structure, and configuration administration. The SEI SBOM Framework may help you alongside your path to organizing, prioritizing, and managing this knowledge that will help you goal your efforts in these areas and make them extra environment friendly and efficient. Actually, it will contain further work within the quick time period, however this work can pay nice long-term dividends.