This QR code phishing marketing campaign is focusing on a number of industries and utilizing reputable providers corresponding to Microsoft Bing to extend its effectivity and bypass safety.

Cofense, a U.S.-based electronic mail safety firm, launched a brand new report a couple of huge QR code phishing marketing campaign that targets quite a few industries. The marketing campaign has particularly targeted on one main U.S.-based power firm, although Cofense doesn’t identify which one. Cybercriminals are utilizing reputable providers corresponding to Microsoft Bing to extend this marketing campaign’s effectivity and bypass safety. Thankfully, there are steps firms can take to mitigate this notably uncommon phishing menace.
Bounce to:
How does this QR code phishing marketing campaign work?
This marketing campaign leverages QR codes as PNG pictures, which, as soon as scanned, result in Microsoft credential phishing pages. The e-mail content material makes use of completely different however related lures: making the consumer imagine they should replace their account safety or activate two-factor authentication/multi-factor authentication inside 72 hours (Determine A).
Determine A
Which reputable providers are abused on this phishing assault?
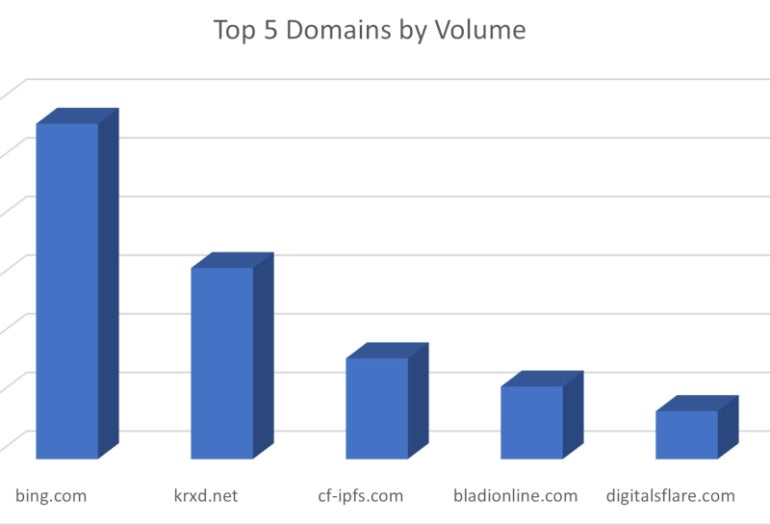
The reputable providers which might be abused to enhance the effectivity of this phishing assault are Microsoft Bing, Salesforce through a website (i.e., krdx.internet) that belongs to the corporate and was used for redirection, two reputable web sites (i.e., digitalsflare.com and bladionline.com) and the InterPlanetary File System.
Bing
On this phishing marketing campaign, many of the malicious QR codes included Bing redirections that contained the sufferer’s electronic mail and a Base64-encoded phishing hyperlink (Determine B).
Determine B
On this case, cybercriminals used Bing — a reputable Microsoft area with redirection functionalities that have been carried out for advertising and marketing functions — to redirect customers to a phishing web site they management. Similar to with the QR code, the advantage of this redirection technique is to assist bypass safety as a result of no malicious area is instantly uncovered — the malicious area is Base64-encoded.
IPFS
The cybercriminals used the InterPlanetary File System to host phishing content material and despatched phishing hyperlinks that used CloudFlare’s gateway to the IPFS system (Determine C).
Determine C
Which industries are vulnerable to this phishing assault?
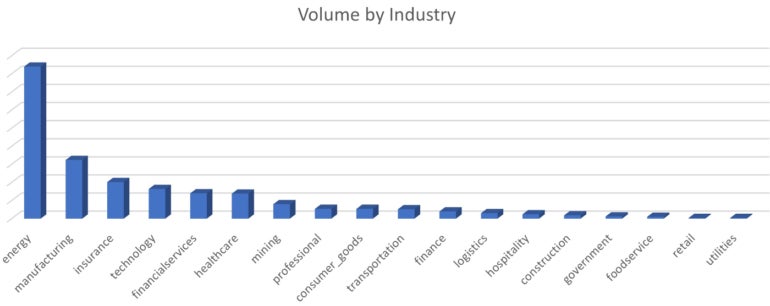
The phishing marketing campaign closely targeted on one main U.S.-based power firm, adopted by the manufacturing, insurance coverage, expertise, monetary providers and healthcare industries (Determine D).
Determine D
Cofense’s Nathaniel Raymond reviews that, from the start of the marketing campaign in Might 2023, the common month-to-month development share has been greater than 270%. Since Might 2023, there was a rise in QR codes in emails of greater than 2,400%.
Why this phishing assault is uncommon
QR codes should not typically utilized in phishing campaigns; cybercriminals have a tendency to make use of them extra in day-to-day life, leaving QR codes in other places so curious individuals will scan them and presumably get scammed or contaminated by malware.
There may be at the least one profit for cybercriminals to make use of QR codes in emails, particularly for launching phishing campaigns: There are much more possibilities to bypass safety and land within the consumer’s mailboxes as a result of the phishing hyperlink is hiding contained in the QR picture.
How this phishing marketing campaign might fail
As said by Raymond, “though QR codes are advantageous for getting malicious emails into consumer’s inbox, they could fall in need of being environment friendly in getting the consumer to the phish.”
QR codes want a scanning gadget for use, which typically shall be a cell phone, as these units now often embed a QR code scanner that works with their digicam. Moreover, these cell phone scanners usually present the hyperlink contained within the QR code to the consumer, who decides if he/she clicks on it or not.
Tips on how to shield from this QR code phishing menace
To reinforce electronic mail safety and shield themselves from the QR code menace, organizations ought to comply with these steps.
- Think about implementing superior menace safety options. Ideally, these options ought to resolve the QR code and have the hyperlink analyzed by safety options.
- On cellular units, solely permit QR codes to be opened by safety functions corresponding to antivirus that embrace QR code scanning as a function. Then, the QR code hyperlink ought to be checked for security.
- Educate customers in order that they’re conscious of the dangers related to QR codes. In firms the place no QR code is used, workers ought to by no means scan any QR code from any supply that pretends to come back from the group.
- Present customers with a fast technique to report suspicious emails to your IT or safety division. This may very well be a button of their electronic mail consumer software program.
- Deploy multifactor authentication for the corporate’s electronic mail accounts. Even when the phishing is profitable, the attacker will nonetheless not be capable to log into the e-mail account.
Disclosure: I work for Development Micro, however the views expressed on this article are mine.


