Government abstract
In latest developments, a classy malware stealer pressure crafted within the Go programming language has been found by AT&T Alien Labs, posing a extreme menace to each Home windows and macOS working techniques.
As of the time of publishing of this text, conventional antivirus options have low and even non-existent detection charges, making it a stealthy and formidable adversary.
Key takeaways:
- The malware is supplied with an in depth array of instructions from its Command and Management (C&C) server.
- JaskaGO can persist in numerous strategies in contaminated system.
- Customers face a heightened danger of knowledge compromise because the malware excels at exfiltrating invaluable info, starting from browser credentials to cryptocurrency pockets particulars and different delicate consumer information.
Background
JaskaGO contributes to a rising development in malware improvement leveraging the Go programming language. Go, often known as Golang, is acknowledged for its simplicity, effectivity, and cross-platform capabilities. Its ease of use has made it a horny selection for malware authors looking for to create versatile and complicated threats.
Whereas macOS is commonly perceived as a safe working system, there exists a prevalent false impression amongst customers that it’s impervious to malware. Traditionally, this misbelief has stemmed from the relative shortage of macOS-targeted threats in comparison with different platforms. Nevertheless, JaskaGO serves as a stark reminder that each Home windows and macOS customers are always susceptible to malware assaults.
Because the malware use of file names resembling well-known purposes (equivalent to “Capcut_Installer_Intel_M1.dmg”, “Anyconnect.exe”) recommend a typical technique of malware deployment beneath the guise of professional software program in pirated software internet pages.
The primary JaskaGo pattern was noticed in July 2023, initially concentrating on Mac customers. Following this opening assault, dozens of recent samples have been recognized because the menace developed its capabilities and developed in each macOS and to Home windows variations; its low detection fee is obvious by its latest pattern by anti-virus engines. (Determine 1)
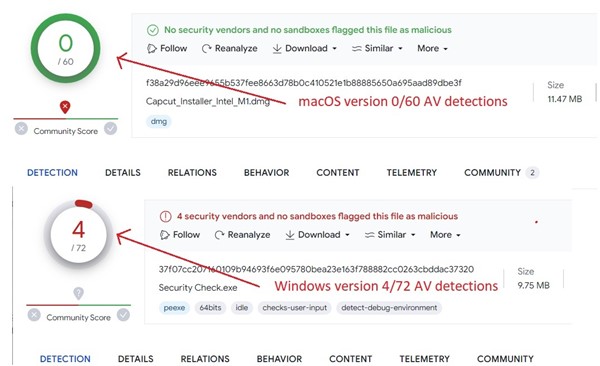
Determine 1. As captured by Alien Labs: Anti-virus detection for latest JaskaGO samples inside VirusTotal.
Evaluation
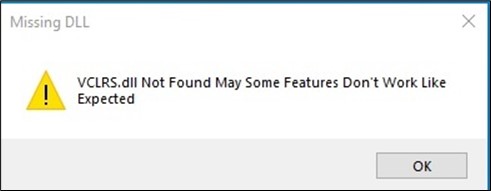
Upon preliminary execution, the malware cunningly presents a misleading message field, displaying a faux error message, claiming a lacking file. That is strategically designed to mislead the consumer into believing that the malicious code didn’t run. (Determine 2)
Determine 2. As captured by Alien Labs: Faux error message.
Anti-VM
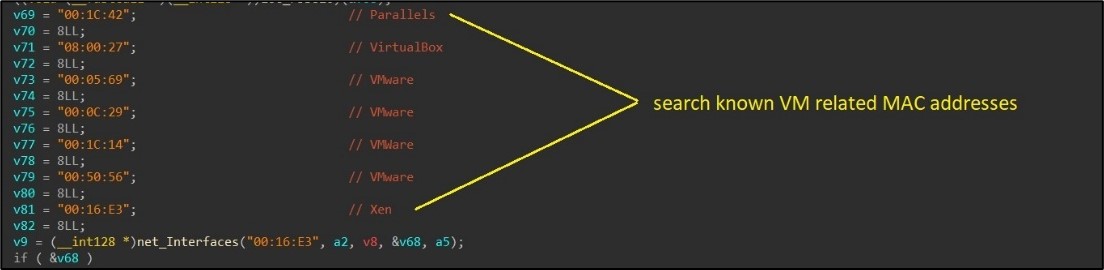
The malware conducts thorough checks to find out whether it is working inside a digital machine (VM). This course of begins with the examination of normal machine info, the place particular standards such because the variety of processors, system up-time, accessible system reminiscence, and MAC addresses are checked. The presence of MAC addresses related to well-known VM software program, equivalent to VMware or VirtualBox, is a key indicator. (Determine 3)
Determine 3. As captured by Alien Labs: On the lookout for VM associated MAC addresses.
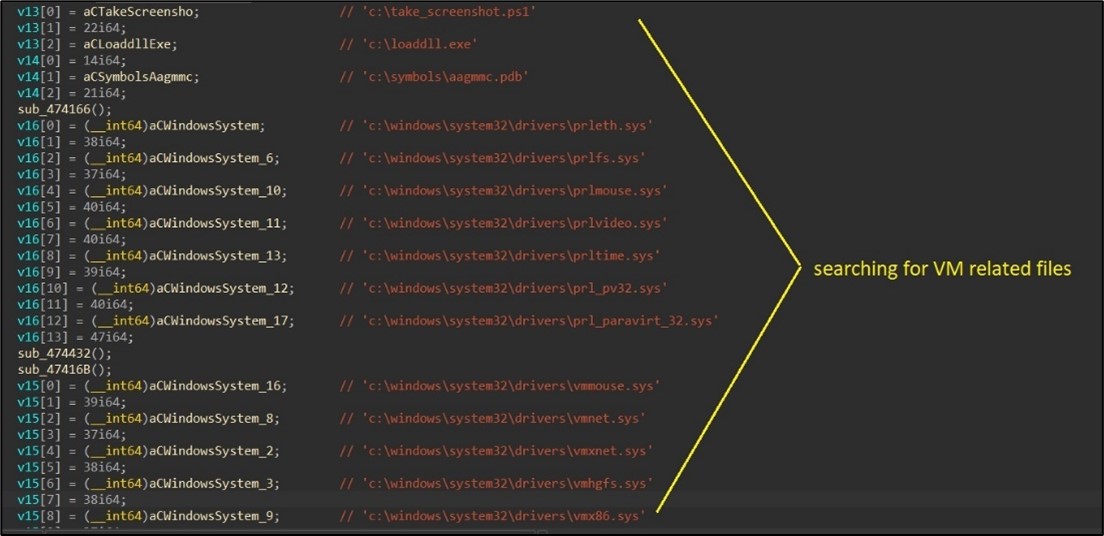
Moreover, the malware’s Home windows model searches for VM-related traces in each the registry and the file system. (Determine 4)
Determine 4. As captured by Alien Labs: On the lookout for VM associated information.
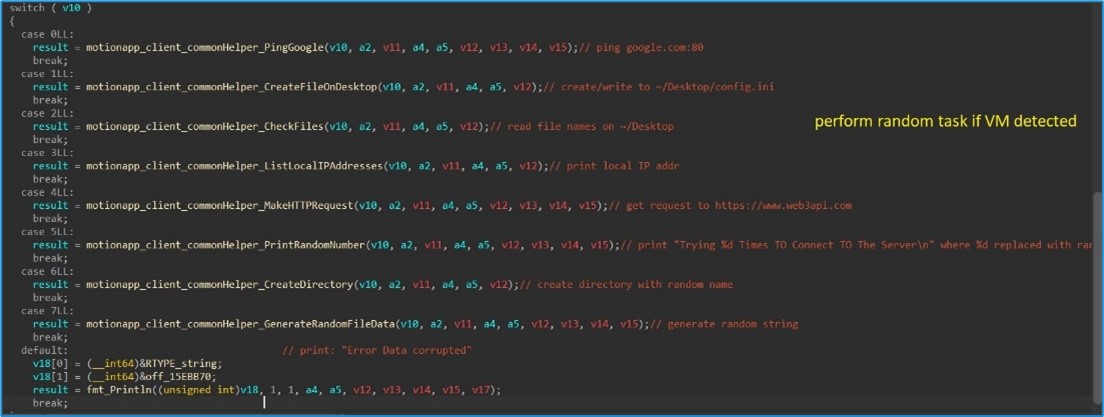
Ought to the malware detect that it’s working inside a digital surroundings, it randomly executes one of many following instructions:
- Ping Google.
- Create File on Desktop (e.g., config.ini).
- Record information on the consumer’s desktop.
- Record native IP addresses.
- Make a easy HTTP GET request to https://www.web3api.com.
- Print a random quantity.
- Create a listing with a random identify within the consumer’s residence listing.
- Print a random string.
Determine 5. As captured by Alien Labs: Carry out random process.
Deal with C&C instructions
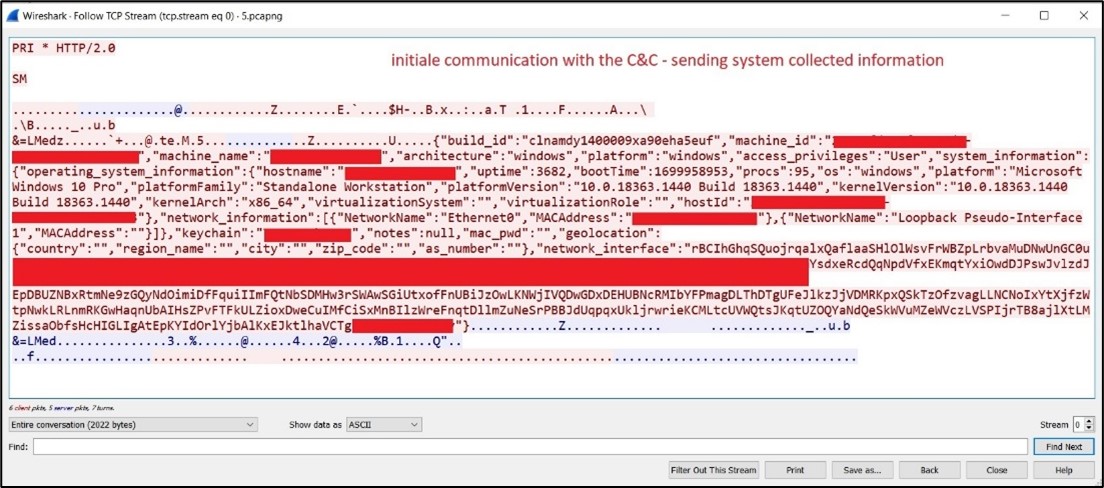
If the VM detection is bypassed, JaskaGO proceeds to gather info from the sufferer and establishes a connection to its command and management for additional actions. (Determine 6)
Determine 6. As captured by Alien Labs: Communication with the C&C.
The malware constantly queries its command and management server, awaiting directions. The potential instructions embrace:
- Creating persistence for the malware (particulars within the subsequent part).
- Stealer functionalities: gathering info from the contaminated gadget and transmitting it to the command and management server.
- Pinging the command and management.
- Executing shell instructions.
- Displaying alert messages.
- Retrieving working course of listing.
- Executing information on disk or in reminiscence.
- Writing to the clipboard:a typical tactic for stealing cryptocurrency funds.
- Performing a random process (like these within the VM detection part).
- Downloading and executing further payloads.
- Initiating the method to exit (self).
- Initiating the method to exit and delete itself.
Stealer
JaskaGO is supplied with in depth knowledge exfiltration capabilities. It shops acquired knowledge in a specifically created folder, zipping and sending it to the malware’s menace actor when prepared.
Browser stealer
Whereas default assist contains info theft from Chrome and Firefox browsers, the malware may be configured to focus on further browsers. The collected browser info contains:
- Browser credentials.
- Historical past.
- Cookies: Information and folders – “Cookies”, “cookies.sqlite”, Community”.
- Password encryption keys key4.db – Shops the grasp key to decrypt all passwords saved in logins.json.
- Profile information (profile.ini, ^Profiled+$).
- Login info – “Login Knowledge” folder.
Crypto forex stealer
The malware searches for browsers crypto wallets extension beneath the folder browser’s extension folder “ֿNative Extension Settings”. As well as, it helps receiving a listing of wallets to seek for and add to the server.
Information
The malware can obtain a listing of information and folders to exfiltrate.
Persistence mechanisms
Home windows
Within the Home windows model, the malware establishes persistence by means of two strategies:
- Service Creation: The malware creates a service and initiates its execution.
- Home windows Terminal “Profiles”: Unusual however efficient, JaskaGO creates a Home windows Terminal profile by producing the file “C:customers$env:UserNameAppDataLocalPackagesMicrosoft. WindowsTerminal_*LocalStatesettings.json.” This file is configured to run mechanically on Home windows reboot, launching a PowerShell course of to execute the malware. Additional particulars on this method may be discovered right here. (Determine 7)
Determine 7. As captured by Alien Labs: Home windows persistence.
macOS
On macOS, JaskaGO employs a multi-step course of to ascertain persistence throughout the system:
- Execution as Root: The malware initiates its execution with an try and run itself with root privileges.
- Disabling Gatekeeper: Gatekeeper, a safety function on macOS, is systematically disabled by the malware utilizing the command “spctl –master-disable“. This motion goals to bypass safety checks and facilitate unhindered operation.
- JaskaGO duplicates itself, adopting the identify format “com.%s.appbackgroundservice,” with %s being changed by a randomly generated string. This renaming tactic helps obfuscate the malware’s presence on the system.
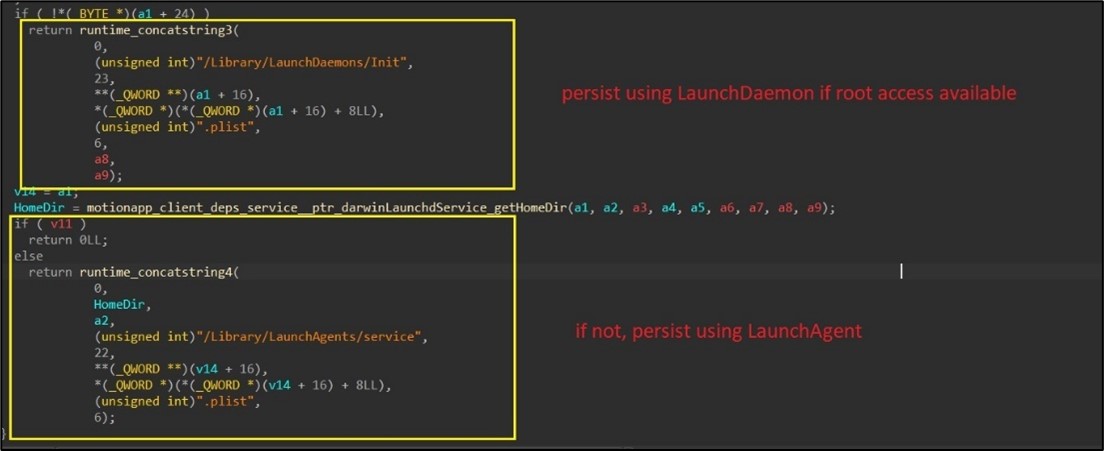
- LaunchDaemon / LaunchAgent Creation: To make sure persistence, primarily based on profitable root entry, the malware creates both the LaunchDaemon “/Library/LaunchDaemons/Init.plist” (if root) or LaunchAgent “/Library/LaunchAgents/service.plist” (if not root). This configuration ensures that the malware is mechanically launched throughout system startup, additional embedding itself into the macOS surroundings. (Determine 8)
Determine 8. As captured by Alien Labs: macOS persistence.
Conclusion
JaskaGO, a cross-platform menace, stands as a compelling instance of the evolving menace panorama. It challenges the extensively held notion of macOS invulnerability, highlighting the shared vulnerability of each Home windows and macOS techniques. Using subtle anti-VM ways, JaskaGO sidesteps computerized evaluation, making it a formidable problem for detection. Its persistence mechanisms reveal a decided effort to embed itself inside techniques, whereas its stealer capabilities remodel the malware right into a harmful menace, extracting delicate info from unsuspecting victims.
Related indicators (IOCs)
The next technical indicators are related to the reported intelligence. An inventory of indicators can also be accessible within the OTX Pulse. Please observe, the heart beat could embrace different actions associated however out of the scope of the report.
|
TYPE |
INDICATOR |
DESCRIPTION |
|
SHA256 |
7bc872896748f346fdb2426c774477c4f6dcedc9789a44bd9d3c889f778d5c4b |
Home windows malware hash |
|
SHA256
|
f38a29d96eee9655b537fee8663d78b0c410521e1b88885650a695aad89dbe3f |
macOS malware hash
|
|
SHA256
|
6efa29a0f9d112cfbb982f7d9c0ddfe395b0b0edb885c2d5409b33ad60ce1435 |
Home windows malware hash
|
|
SHA256
|
f2809656e675e9025f4845016f539b88c6887fa247113ff60642bd802e8a15d2 |
Home windows malware hash
|
|
SHA256
|
85bffa4587801b863de62b8ab4b048714c5303a1129d621ce97750d2a9a989f9 |
Home windows malware hash
|
|
SHA256
|
37f07cc207160109b94693f6e095780bea23e163f788882cc0263cbddac37320 |
Home windows malware hash
|
|
SHA256
|
e347d1833f82dc88e28b1baaa2657fe7ecbfe41b265c769cce25f1c0e181d7e0 |
Home windows malware hash
|
|
SHA256
|
c714f3985668865594784dba3aeda1d961acc4ea7f59a178851e609966ca5fa6 |
Home windows malware hash
|
|
SHA256
|
9b23091e5e0bd973822da1ce9bf1f081987daa3ad8d2924ddc87eee6d1b4570d |
Home windows malware hash
|
|
SHA256
|
1c0e66e2ea354c745aebda07c116f869c6f17d205940bf4f19e0fdf78d5dec26 |
Home windows malware hash
|
|
SHA256
|
e69017e410aa185b34e713b658a5aa64bff9992ec1dbd274327a5d4173f6e559 |
Home windows malware hash
|
|
SHA256
|
6cdda60ffbc0e767596eb27dc4597ad31b5f5b4ade066f727012de9e510fc186 |
macOS malware hash
|
|
SHA256
|
44d2d0e47071b96a2bd160aeed12239d4114b7ec6c15fd451501c008d53783cf |
Home windows malware hash
|
|
SHA256
|
8ad4f7e14b36ffa6eb7ab4834268a7c4651b1b44c2fc5b940246a7382897c98e |
Home windows malware hash
|
|
SHA256
|
888623644d722f35e4dcc6df83693eab38c1af88ae03e68fd30a96d4f8cbcc01 |
Home windows malware hash
|
|
SHA256
|
3f139c3fcad8bd15a714a17d22895389b92852118687f62d7b4c9e57763a8867 |
Home windows malware hash
|
|
SHA256
|
207b5ee9d8cbff6db8282bc89c63f85e0ccc164a6229c882ccdf6143ccefdcbc |
macOS malware hash
|
Mapped to MITRE ATT&CK
The findings of this report are mapped to the next MITRE ATT&CK Matrix methods:
-
- TA0003: Persistence
- T1543: Create or Modify System Course of
- T1543.001: Launch Agent
- T1543.003: Home windows Service
- T1543.004: Launch Daemon
- T1543: Create or Modify System Course of
- TA0007: Discovery
- T1082: System Data Discovery
- T1057: Course of Discovery
- T1082: System Data Discovery
- T1518: Software program Discovery
- T1518.001: Safety Software program Discovery
- TA0011: Command and Management
- TA0010: Exfiltration
- T1020: Automated Exfiltration
- T1041: Exfiltration Over C2 Channel
- TA0003: Persistence