
Posted by Kateryna Semenova, Developer Relations Engineer, Android
Introduction
KAYAK is among the world’s main journey search engines like google that helps customers discover the very best offers on flights, resorts, and rental vehicles. In 2023, KAYAK built-in passkeys – a brand new kind of passwordless authentication – into its Android and internet apps. Because of this, KAYAK lowered the common time it takes their customers to sign-up and sign-in by 50%, and in addition noticed a lower in help tickets.
This case examine explains KAYAK’s implementation on Android with Credential Supervisor API and RxJava. You need to use this case examine as a mannequin for implementing Credential Supervisor to enhance safety and consumer expertise in your personal apps.
In order for you a fast abstract, take a look at the companion video on YouTube.
Drawback
Like most companies, KAYAK has relied on passwords prior to now to authenticate customers. Passwords are a legal responsibility for each customers and companies alike: they’re usually weak, reused, guessed, phished, leaked, or hacked.
“Providing password authentication comes with plenty of effort and danger for the enterprise. Attackers are continually making an attempt to brute drive accounts whereas not all customers perceive the necessity for robust passwords. Nevertheless, even robust passwords will not be totally safe and may nonetheless be phished.” – Matthias Keller, Chief Scientist and SVP, Expertise at KAYAK
To make authentication safer, KAYAK despatched “magic hyperlinks” through e-mail. Whereas useful from a safety standpoint, this further step launched extra consumer friction by requiring customers to change to a special app to finish the login course of. Further measures wanted to be launched to mitigate the chance of phishing assaults.
Answer
KAYAK’s Android app now makes use of passkeys for a safer, user-friendly, and sooner authentication expertise. Passkeys are distinctive, safe tokens which can be saved on the consumer’s system and may be synchronized throughout a number of gadgets. Customers can check in to KAYAK with a passkey by merely utilizing their present system’s display lock, making it less complicated and safer than getting into a password.
“We have added passkeys help to our Android app in order that extra customers can use passkeys as an alternative of passwords. Inside that work, we additionally changed our previous Smartlock API implementation with the Sign up with Google supported by Credential Supervisor API. Now, customers are ready to enroll and check in to KAYAK with passkeys twice as quick as with an e-mail hyperlink, which additionally improves the completion fee” – Matthias Keller, Chief Scientist and SVP, Expertise at KAYAK
Credential Supervisor API integration
To combine passkeys on Android, KAYAK used the Credential Supervisor API. Credential Supervisor is a Jetpack library that unifies passkey help beginning with Android 9 (API stage 28) and help for conventional sign-in strategies reminiscent of passwords and federated authentication right into a single consumer interface and API.
Designing a sturdy authentication circulation for apps is essential to make sure safety and a reliable consumer expertise. The next diagram demonstrates how KAYAK built-in passkeys into their registration and authentication flows:

At registration time, customers are given the chance to create a passkey. As soon as registered, customers can check in utilizing their passkey, Sign up with Google, or password. Since Credential Supervisor launches the UI robotically, watch out to not introduce surprising wait instances, reminiscent of community calls. All the time fetch a one-time problem and different passkeys configuration (reminiscent of RP ID) at first of any app session.
Whereas the KAYAK workforce is now closely invested in coroutines, their preliminary integration used RxJava to combine with the Credential Supervisor API. They wrapped Credential Supervisor calls into RxJava as follows:
override enjoyable createCredential(request: CreateCredentialRequest, exercise: Exercise): Single<CreateCredentialResponse> {
|
This instance defines a Kotlin perform known as createCredential() that returns a credential from the consumer as an RxJava Single of kind CreateCredentialResponse. The createCredential() perform encapsulates the asynchronous means of credential registration in a reactive programming type utilizing the RxJava Single class.
For a Kotlin implementation of this course of utilizing coroutines, learn the Sign up your consumer with Credential Supervisor information.
New consumer registration sign-up circulation
This instance demonstrates the strategy KAYAK used to register a brand new credential, right here Credential Supervisor was wrapped in Rx primitives.
webAuthnRetrofitService
|
Rx allowed KAYAK to provide extra complicated pipelines that may contain a number of interactions with Credential Supervisor.
Current consumer sign-in
KAYAK used the next steps to launch the sign-in circulation. The method launches a backside sheet UI component, permitting the consumer to log in utilizing a Google ID and an present passkey or saved password.

Builders ought to comply with these steps when organising a sign-in circulation:
- Because the backside sheet is launched robotically, watch out to not introduce surprising wait instances within the UI, reminiscent of community calls. All the time fetch a one-time problem and different passkeys configuration (reminiscent of RP ID) at first of any app session.
- When providing Google sign-in through Credential Supervisor API, your code ought to initially search for Google accounts which have already been used with the app. To deal with this, name the API with the setFilterByAuthorizedAccounts parameter set to true.
- If the consequence returns an inventory of obtainable credentials, the app exhibits the underside sheet authentication UI to the consumer.
- If a NoCredentialException seems, no credentials have been discovered: No Google accounts, no passkeys, and no saved passwords. At this level, your app ought to name the API once more and set setFilterByAuthorizedAccounts to false to provoke the Join with Google circulation.
- Course of the credential returned from Credential Supervisor.
Single.fromSupplier<GetPublicKeyCredentialOption> {
|
“As soon as the Credential Supervisor API is mostly applied, it is vitally simple so as to add different authentication strategies. Including Google One-Faucet Signal In was virtually zero work after including passkeys.” – Matthias Keller
To be taught extra, comply with the information on the right way to Combine Credentials Supervisor API and the right way to Combine Credential Supervisor with Sign up with Google.
UX concerns
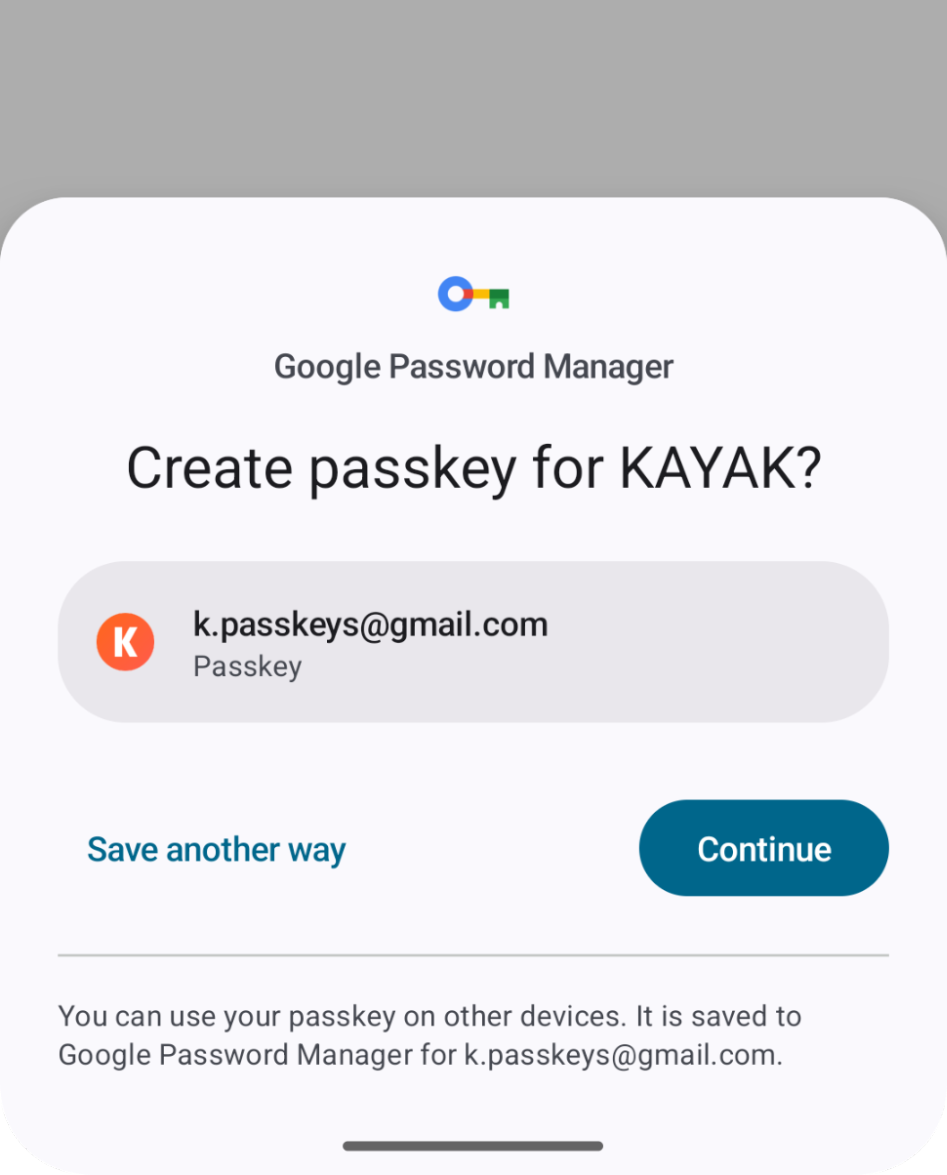
A few of the main consumer expertise concerns KAYAK confronted when switching to passkeys included whether or not customers ought to be capable of delete passkeys or create multiple passkey.
Our UX information for passkeys recommends that you’ve got an choice to revoke a passkey, and that you make sure that the consumer doesn’t create duplicate passkeys for a similar username in the identical password supervisor.
To forestall registration of a number of credentials for a similar account, KAYAK used the excludeCredentials property that lists credentials already registered for the consumer. The next instance demonstrates the right way to create new credentials on Android with out creating duplicates:
enjoyable WebAuthnClientParamsResponse.toCreateCredentialRequest(): String {
|
And that is how KAYAK applied excludeCredentials performance for his or her Internet implementation.
var registrationOptions = {
|
Server-side implementation
The server-side half is an integral part of an authentication resolution. KAYAK added passkey capabilities to their present authentication backend by using WebAuthn4J, an open supply Java library.
KAYAK broke down the server-side course of into the next steps:
- The consumer requests parameters wanted to create or use a passkey from the server. This contains the problem, the supported encryption algorithm, the relying social gathering ID, and associated objects. If the consumer already has a consumer e-mail tackle, the parameters will embrace the consumer object for registration, and an inventory of passkeys if any exist.
- The consumer runs browser or app flows to start out passkey registration or sign-in.
- The consumer sends retrieved credential data to the server. This contains consumer ID, authenticator information, consumer information, and different associated objects. This data is required to create an account or confirm a sign-in.
When KAYAK labored on this undertaking, no third-party merchandise supported passkeys. Nevertheless, many sources at the moment are accessible for making a passkey server, together with documentation and library examples.
Outcomes
Since integrating passkeys, KAYAK has seen a major improve in consumer satisfaction. Customers have reported that they discover passkeys to be a lot simpler to make use of than passwords, as they don’t require customers to recollect or kind in an extended, complicated string of characters. KAYAK lowered the common time it takes their customers to sign-up and sign-in by 50%, have seen a lower in help tickets associated to forgotten passwords, and have made their system safer by decreasing their publicity to password-based assaults. Thanks to those enhancements, KAYAK plans to remove password-based authentication of their app by the top of 2023.
“Passkeys make creating an account lightning quick by eradicating the necessity for password creation or navigating to a separate app to get a hyperlink or code. As a bonus, implementing the brand new Credential Supervisor library additionally lowered technical debt in our code base by placing passkeys, passwords and Google sign-in all into one new fashionable UI. Certainly, customers are ready to enroll and check in to KAYAK with passkeys twice as quick as with an e-mail hyperlink, which additionally improves the completion fee.” – Matthias Keller
Conclusion
Passkeys are a brand new and modern authentication resolution that provides vital advantages over conventional passwords. KAYAK is a superb instance of how a corporation can enhance the safety and value of its authentication course of by integrating passkeys. In case you are on the lookout for a safer and user-friendly authentication expertise, we encourage you to think about using passkeys with Android’s Credential Supervisor API.



