
The StrongPity APT hacking group is distributing a faux Shagle chat app that may be a trojanized model of the Telegram for Android app with an added backdoor.
Shagle is a reputable random-video-chat platform permitting strangers to speak through an encrypted communications channel. Nevertheless, the platform is completely web-based, not providing a cellular app.
StrongPity has been discovered utilizing a faux web site since 2021 that impersonates the precise Shagle web site to trick victims into downloading a malicious Android.
As soon as put in, this app allows the hackers to conduct espionage on the focused victims, together with monitoring telephone calls, accumulating SMS texts, and grabbing contact lists.
Supply: ESET
StrongPity, also referred to as Promethium or APT-C-41, was beforehand attributed to a marketing campaign that distributed trojanized Notepad++ installers and malicious variations of WinRAR and TrueCrypt to contaminate targets with malware.
The newest StrongPity exercise was found by ESET researchers who attributed the marketing campaign to the espionage APT group primarily based on code similarities with previous payloads.
Moreover, the Android app is signed with the identical certificates the APT used to signal an app that mimicked the Syrian e-gov Android utility in a 2021 marketing campaign.
Trojanizing the Android Telegram app
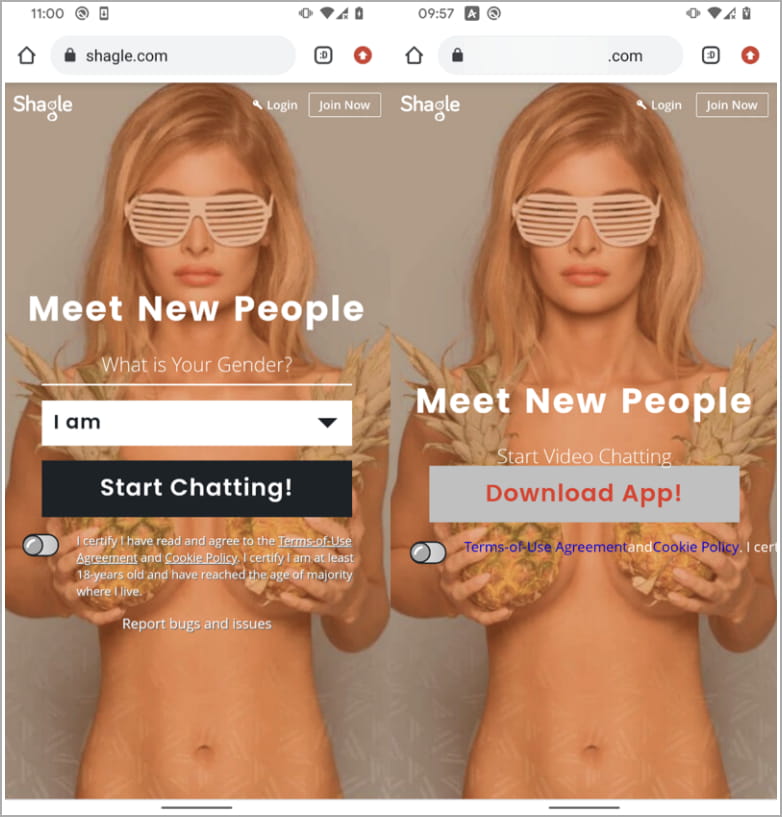
The malicious Android utility distributed by StrongPity is an APK file named “video.apk,” the usual Telegram v7.5.0 (February 2022) app modified to impersonate a Shagle cellular app.
ESET could not decide how victims arrive on the faux Shagle web site, however it’s possible via spear phishing emails, smishing (SMS phishing), or on the spot messages on on-line platforms.
The malicious APK is supplied instantly from the faux Shagle web site and has by no means been made out there on Google Play.
ESET says the cloned web site first appeared on-line on November 2021, so the APK has possible been below lively distribution since then. Nevertheless, the first confirmed detection within the wild got here in July 2022.
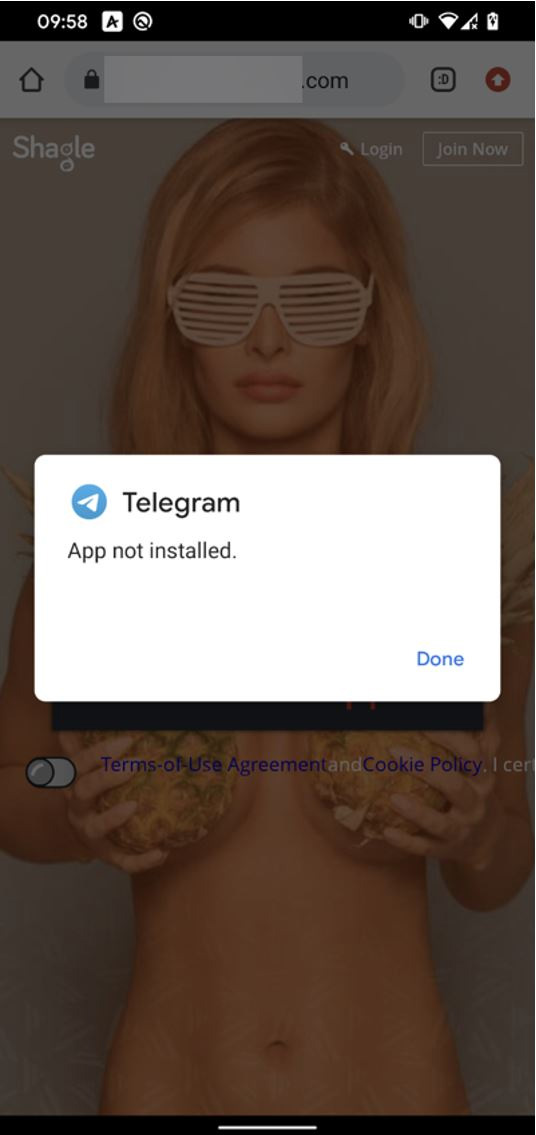
One downside of utilizing Telegram as the premise for the hacking group’s faux app is that if the sufferer already has the actual Telegram app put in on their telephones, the backdoored model will not be put in.
Supply: ESET
At the moment, the API ID used within the captured samples has been restricted as a result of overuse, so the trojanized app will now not settle for new person registrations; therefore, the backdoor will not work.
ESET believes this means that StrongPity has efficiently deployed the malware on focused victims.
Backdoor designed to spy on victims
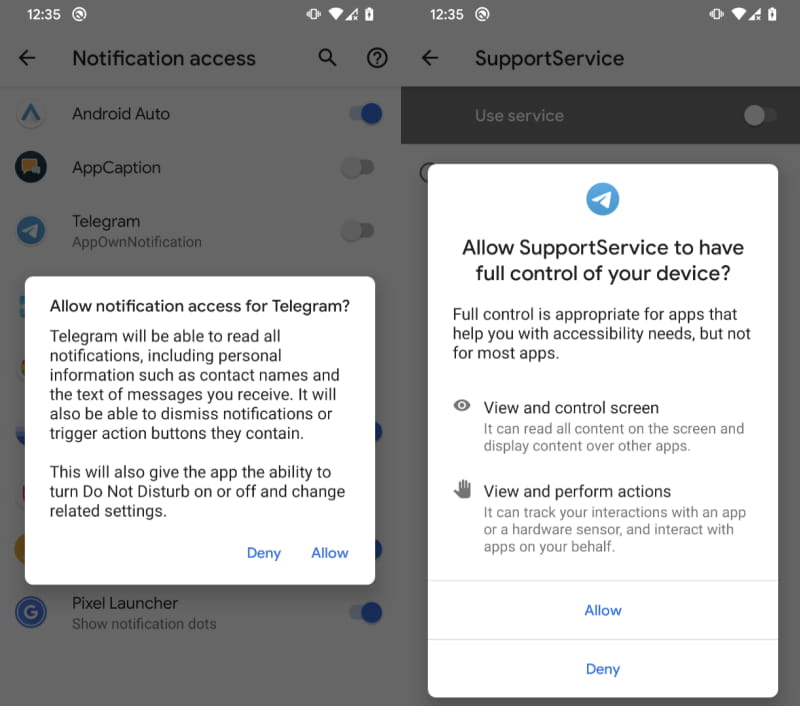
Upon set up, the malware requests entry to Accessibility Service after which fetches an AES-encrypted file from the attacker’s command and management server.
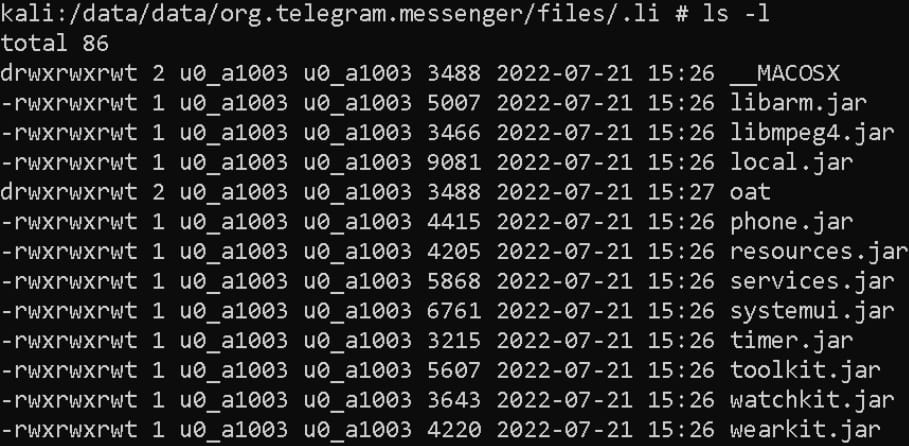
This file consists of 11 binary modules extracted to the gadget and utilized by the backdoor to carry out varied malicious performance.
Supply: ESET
Every module performs an espionage perform and is triggered as wanted. The whole checklist of the malicious adware modules is listed beneath:
- libarm.jar – data telephone calls
- libmpeg4.jar – collects textual content of incoming notification messages from 17 apps
- native.jar – collects file checklist (file tree) on the gadget
- telephone.jar – misuses accessibility providers to spy on messaging apps by exfiltrating contact title, chat message, and date
- sources.jar – collects SMS messages saved on the gadget
- providers.jar – obtains gadget location
- systemui.jar – collects gadget and system data
- timer.jar – collects a listing of put in apps
- toolkit.jar – collects contact checklist
- watchkit.jar – collects a listing of gadget accounts
- wearkit.jar – collects a listing of name logs
The gathered information is saved within the app’s listing, encrypted with AES, and finally despatched again to the attacker’s command and management server.
By abusing the Accessibility Service, the malware can learn notification content material from Messenger, Viber, Skype, WeChat, Snapchat, Tinder, Instagram, Twitter, Gmail, and extra.
Supply: ESET
In rooted units the place the common person has administrator privileges, the malware robotically grants itself permission to carry out modifications on safety settings, write on the filesystem, carry out reboots, and carry out different harmful features.
The StrongPity hacking group has been lively since 2012, generally hiding backdoors in reputable software program installers. Based mostly on ESET’s report, the risk actor continues to make use of the identical tactic after a decade.
Android customers must be cautious with APKs sourced outdoors Google Play and take note of permission requests whereas putting in new apps.

