In response to a 2023 report from Enterprise Search Group, 85% of organizations indicated they deploy functions on two or extra IaaS suppliers, testifying that the age of multi-cloud is formally right here. A typical motive for this decentralized mannequin is that information residency necessities typically require information to stay native to a particular area. For instance, Nationwide Information Residency Legal guidelines in Germany and France mandate particular delicate information (e.g., well being, monetary) stay inside the nation. Information residency necessities create further complexities as organizations are confronted with managing programs each on-prem and within the cloud.
For cybersecurity operations, groups want to watch logs and telemetry produced by the functions and infrastructure in a number of clouds and areas. With the information egress prices levied by cloud suppliers, consolidating the information right into a single bodily location is clearly not possible for data-intensive organizations.
Our earlier weblog on Cybersecurity within the Period of A number of Clouds & Areas highlighted the question federation strategy to deal with the issue of querying cybersecurity logs throughout a number of clouds and areas, whereas respecting information sovereignty legal guidelines and minimizing egress prices (see determine under). Nonetheless, there have been nonetheless three further information governance alternative areas to deal with:
- Ease of federating tables from a number of Databricks workspaces
- Ease of managing entry management to the federated tables
- Ease of deploying federation as code
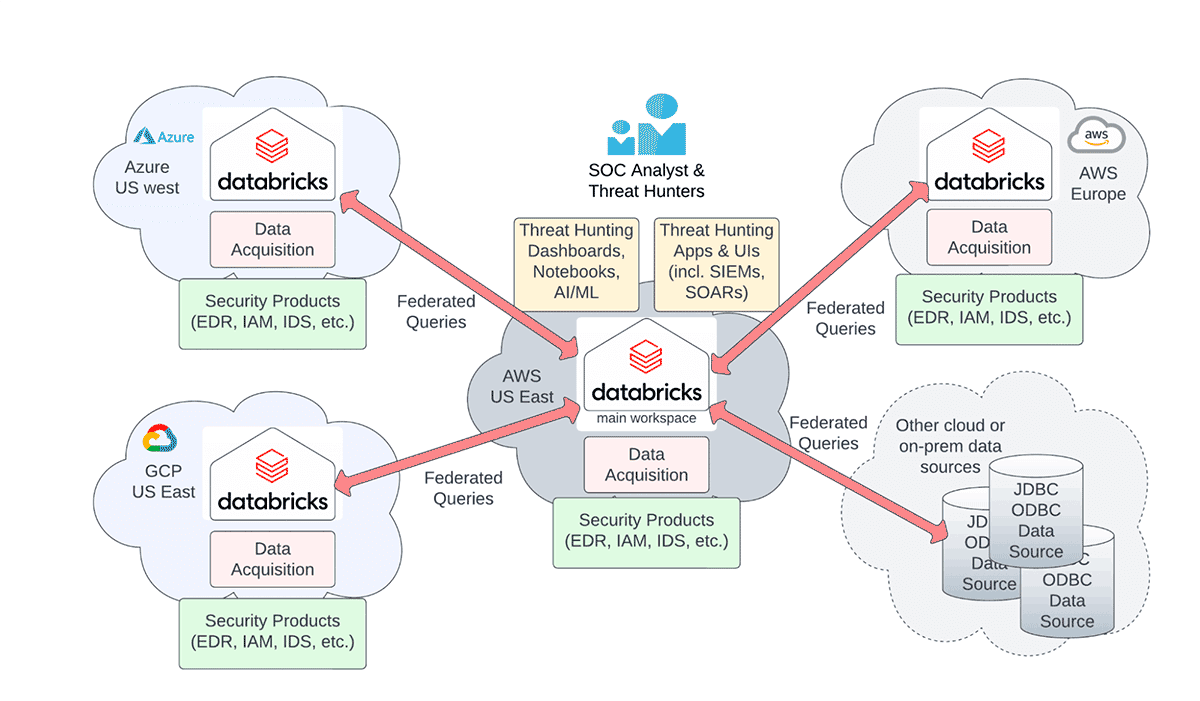
On this weblog, we present how Unity Catalog, Delta Sharing & Lakehouse Federation elevates the multi-cloud, multi-region cybersecurity capabilities to a first-class citizen within the Databricks Lakehouse platform with straightforward governance of all of your cybersecurity information irrespective of which cloud and which area they’re situated.
Whereas we use cybersecurity menace looking as a concrete use case, the strategy outlined on this weblog is broadly relevant to all forms of enterprise information siloed in several clouds, completely different areas, and completely different information shops. Multi-cloud and multi-region information governance is the important thing to unlocking the worth of siloed enterprise information with out sacrificing risk-based controls. The truth is, in keeping with the AWS MIT CDO Agenda 2023 Report, 45% of CDOs said “establishing clear and efficient information governance” as the highest precedence on the journey to unlock worth from enterprise information.
To handle the governance challenges outlined above, we show how
- Delta Sharing can be utilized to seamlessly federate tables from a number of Databricks workspaces,
- Unity Catalog can be utilized to simply handle entry management to the federated tables, and
- A Terraform-based deployment framework can be utilized to deploy the federation as code.
Governance is barely a method to an finish. We show how all these capabilities come collectively to facilitate the deployment of distributed logging capabilities throughout clouds and areas whereas enabling safety analysts to centrally handle and question the information for menace detection and looking. The demonstration is grounded within the distributed Indicators of Compromise (IOC) matching use case, a basic constructing block for menace detection guidelines or AI fashions. Databricks has already launched an answer accelerator that implements the IOC use case – what we’ve executed is benefit from Lakehouse Federation companies to simplify integrating cross-cloud querying.
Constructing Your Multi-Cloud Structure
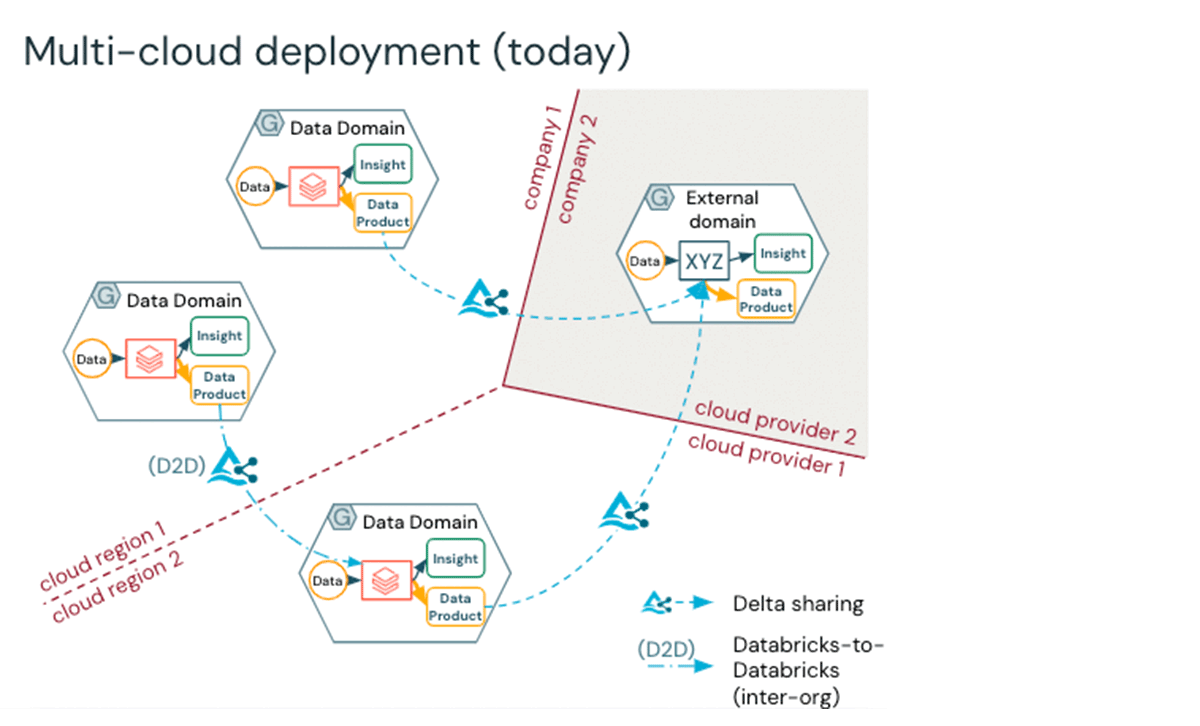
The rest of this weblog will present you the way to shortly arrange a multi-cloud, multi-region Databricks setting inside minutes by leveraging our Business Lakehouse Blueprints and Terraform. Delta Sharing is the muse for multi-cloud information entry patterns, and we signify this in a mesh-like illustration under. Core advantages of utilizing Unity Catalog to handle information embrace the flexibility to:
- Apply fine-grained entry controls on information
- Perceive end-to-end information lineage
- Allow information distribution in a easy, seamless means.
As soon as information is positioned right into a container, referred to as a Delta share, enterprise governance groups can handle entry to the shared information. Furthermore, as soon as the information is centralized, for instance, in a hub-and-spoke structure, the primary hub, which unions the information, applies entry controls to guard the information throughout the enterprise.
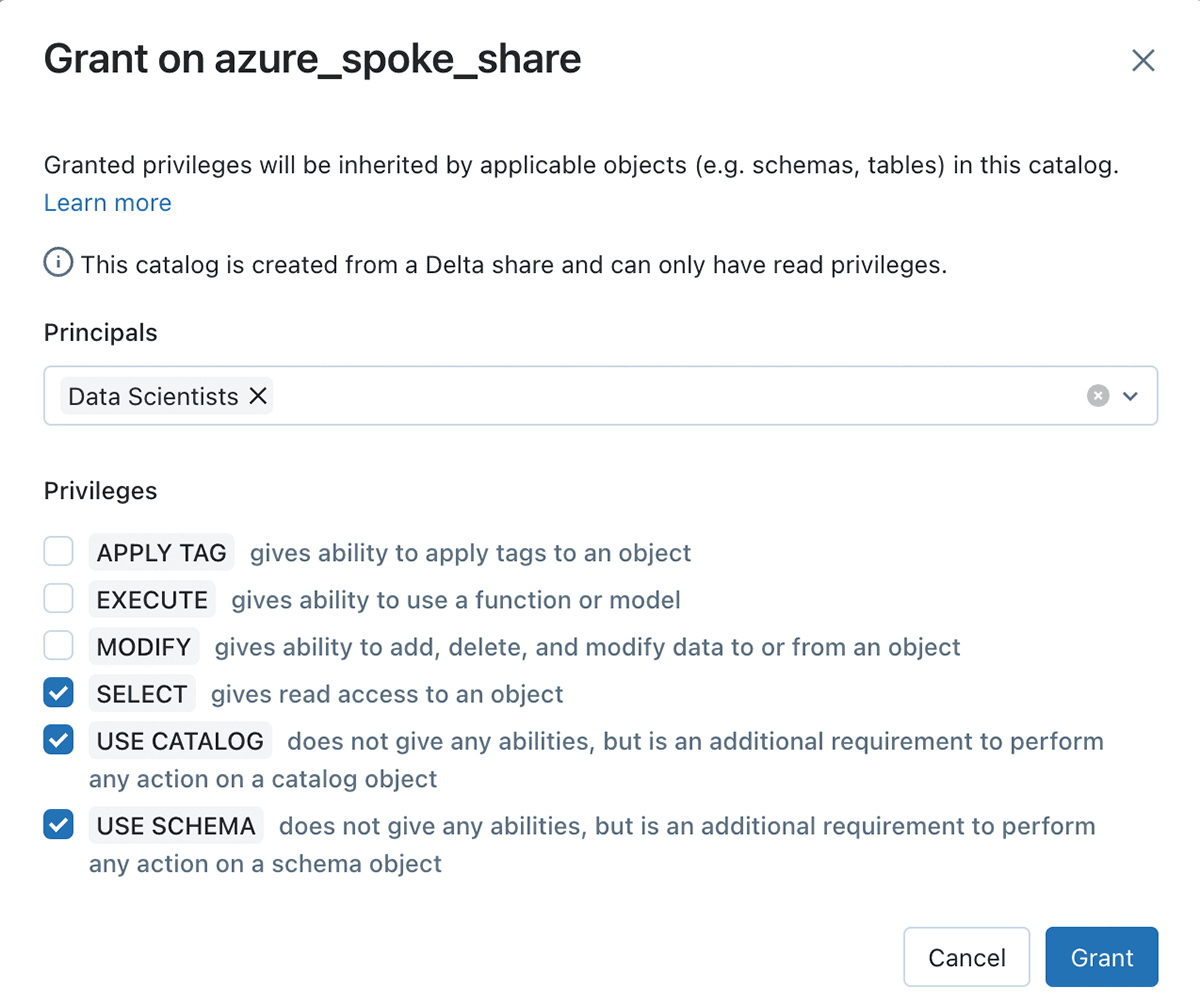
Step 1 – Retrieve Tables from Current Cyber Catalog
Assuming you might have an current catalog on your cyber supply tables for IOC matching (e.g. DNS, HTTP log information from the IOC matching resolution), use an information supply variable to load these so you’ll be able to create a Delta Share object later.
information "databricks_tables" "aws_cyber_tables" {
supplier = databricks.spoke_aws_workspace
catalog_name = "cyber_catalog"
schema_name = "ioc_matching"
depends_on = [databricks_job.load_aws, databricks_job.load_azure]
}
Step 2 – Invoke the Cyber blueprint module to automate the creation of shares of IOC, IDS, and different Information Sources
We have now created a module which lets you hyperlink all of your spoke workspaces primarily based on our information exfiltration prevention hub and spoke mannequin. This module requires the worldwide metastore IDs, retrieved from the hub and spoke workspaces.
module "multicloud_cyber" {
supply = "../../modules/multicloud_cyber/"
aws_spoke_databricks_username = var.aws_spoke_databricks_username
aws_spoke_databricks_password = var.aws_spoke_databricks_password
aws_hub_databricks_username = var.aws_hub_databricks_username
aws_hub_databricks_password = var.aws_hub_databricks_password
aws_spoke_ws_url = var.aws_spoke_ws_url
aws_hub_ws_url = var.aws_hub_ws_url
azure_spoke_ws_url = var.azure_spoke_ws_url
azure_metastore_id = var.azure_metastore_id
aws_metastore_id = var.aws_metastore_id
aws_region = var.aws_region
global_azure_metastoreid = var.global_azure_metastoreid
global_aws_metastoreid = var.global_aws_metastoreid
global_hub_metastoreid = var.global_hub_metastoreid
}
Step 3 – Federate queries throughout a number of clouds utilizing pre-created shares
One of many main challenges to federate queries for cybersecurity use instances is cross-cloud querying. Organizations need to keep away from replicating information throughout clouds, which incurs excessive prices each from the information motion and the egress value perspective. Because of this, it’s ideally suited to question the information in place the place it lives. We referred to as out a few of these challenges from the cyber log information perspective within the IOC matching accelerator.
- Consolidating log information to a single workspace is unimaginable due to information sovereignty laws.
- The egress value to consolidate information from one cloud or area to the central workspace is prohibitive.
On this federation sample, you’ll merely reference information the place it lives and limit entry to these menace hunters and information scientists who want the flexibility to question the information. For instance, the catalog akin to the Delta Share may be managed with typical ANSI SQL entry controls.
Listed here are the steps now you can omit from the unique Cyber IOC matching accelerator utilizing the Delta Sharing paradigm:
- Configuration of init scripts with a path to your Simba driver jar
- Validate the prevailing ODBC binary on the cluster
- Handle private entry tokens
- Arrange ODBC in your compute cluster to run the federation
- Create an exterior desk with credentials
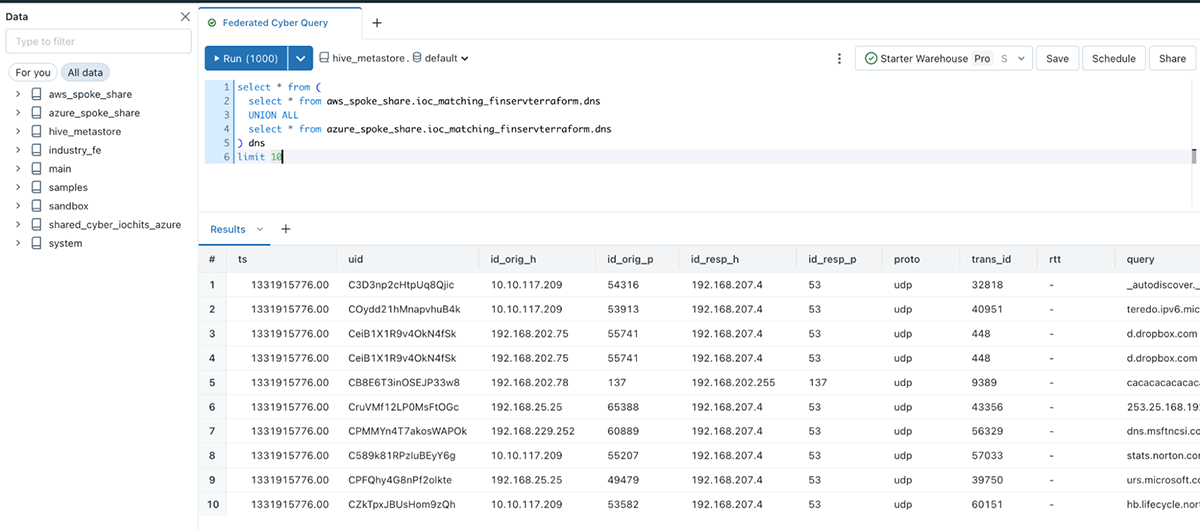
Now, you’ll be able to simply question tables in place out of your current catalog. Under, we’re seeing the results of making use of our automation – querying all Delta shared log tables from the hub workspace, which runs in opposition to Serverless compute for simplified safety and information entry.
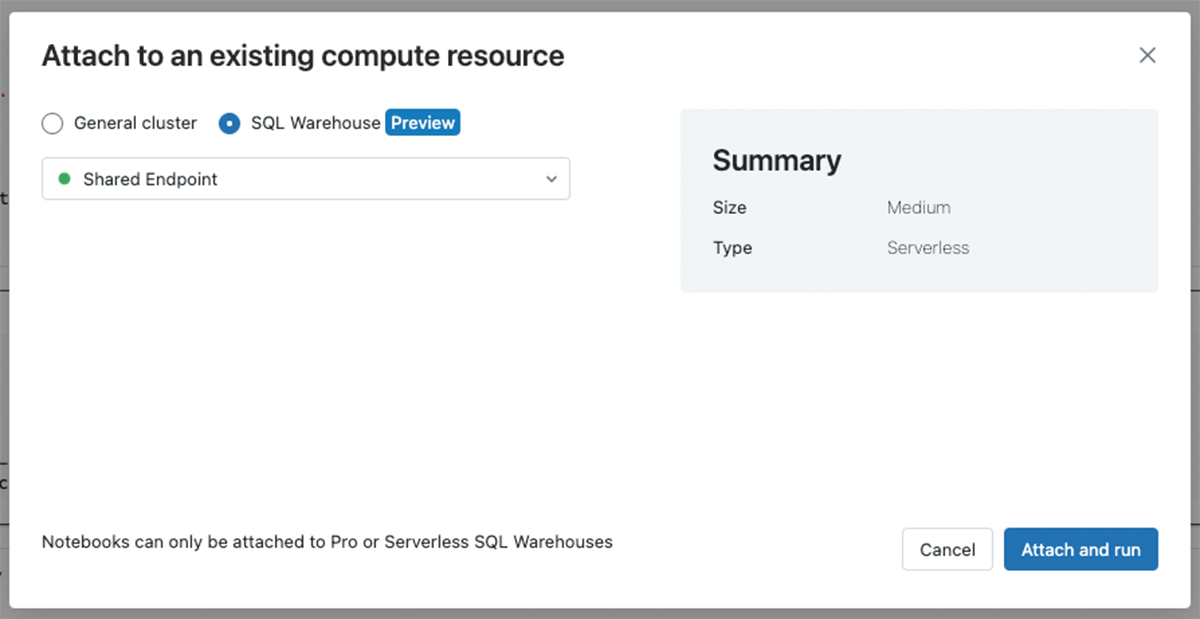
We have now drastically simplified information entry and averted costly information copy steps. Past this, we’ve executed this all with an open, extensible format, Delta Lake, which simply helps information sharing.
Conclusion
Multi-cloud efforts are at a serious crossroads in right this moment’s world. Clients are balancing the price of replication, cloud information retailer lock-in, and an information administration technique. To be used instances in cybersecurity the place information locality is crucial, the sharing technique have to be executed thoughtfully. The pillars of TCO, question federation, and governance are crucial components right here.
TCO ensures prospects hold prices in line, notably in enhancing safety measures. Question federation is important for real-time menace evaluation, all whereas avoiding the safety dangers related to copying information throughout geographic boundaries. Lastly, stringent governance protocols be sure that all information sharing complies with regional and international safety laws. These three tenets are non-negotiable for securing a multi-cloud setting successfully and effectively and are enabled by Unity Catalog and Delta Sharing, as proven above. Uncover the Cybersecurity Lakehouse options to grasp the way to allow extra use instances within the cybersecurity ecosystem right this moment.
For additional info, try the weblog on “Cybersecurity within the Period of A number of Clouds and Areas.”


