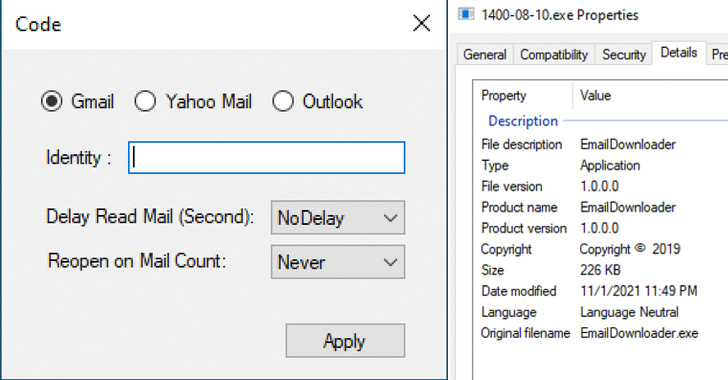
The Iranian government-backed actor generally known as Charming Kitten has added a brand new software to its malware arsenal that enables it to retrieve person knowledge from Gmail, Yahoo!, and Microsoft Outlook accounts.
Dubbed HYPERSCRAPE by Google Risk Evaluation Group (TAG), the actively in-development malicious software program is claimed to have been used in opposition to lower than two dozen accounts in Iran, with the oldest recognized pattern courting again to 2020. The software was first found in December 2021.
Charming Kitten, a prolific superior persistent risk (APT), is believed to be related with Iran’s Islamic Revolutionary Guard Corps (IRGC) and has a historical past of conducting espionage aligned with the pursuits of the federal government.
Tracked as APT35, Cobalt Phantasm, ITG18, Phosphorus, TA453, and Yellow Garuda, components of the group have additionally carried out ransomware assaults, suggesting that the risk actor’s motives are each espionage and financially pushed.
“HYPERSCRAPE requires the sufferer’s account credentials to run utilizing a legitimate, authenticated person session the attacker has hijacked, or credentials the attacker has already acquired,” Google TAG researcher Ajax Bash stated.
Written in .NET and designed to run on the attacker’s Home windows machine, the software comes with capabilities to obtain and exfiltrate the contents of a sufferer’s e-mail inbox, along with deleting safety emails despatched from Google to alert the goal of any suspicious logins.
Ought to a message be initially unread, the software marks it as unread after opening and downloading the e-mail as a “.eml” file. What’s extra, earlier variations of HYPERSCRAPE are stated to have included an choice to request knowledge from Google Takeout, a function that enables customers to export their knowledge to a downloadable archive file.
The findings observe the current discovery of a C++-based Telegram “grabber” software by PwC used in opposition to home targets to acquire entry to Telegram messages and contacts from particular accounts.
Beforehand, the group was noticed deploying a customized Android surveillanceware referred to as LittleLooter, a feature-rich implant able to gathering delicate info saved within the compromised units in addition to recording audio, video, and calls.
“Like a lot of their tooling, HYPERSCRAPE will not be notable for its technical sophistication, however reasonably its effectiveness in conducting Charming Kitten’s targets,” Bash stated. The affected accounts have since been re-secured and the victims notified.