A brand new Android malware pressure named Goldoson has been detected within the official Google Play Retailer spanning greater than 60 authentic apps that collectively have over 100 million downloads.
An extra eight million installations have been tracked by way of ONE retailer, a number one third-party app storefront in South Korea.
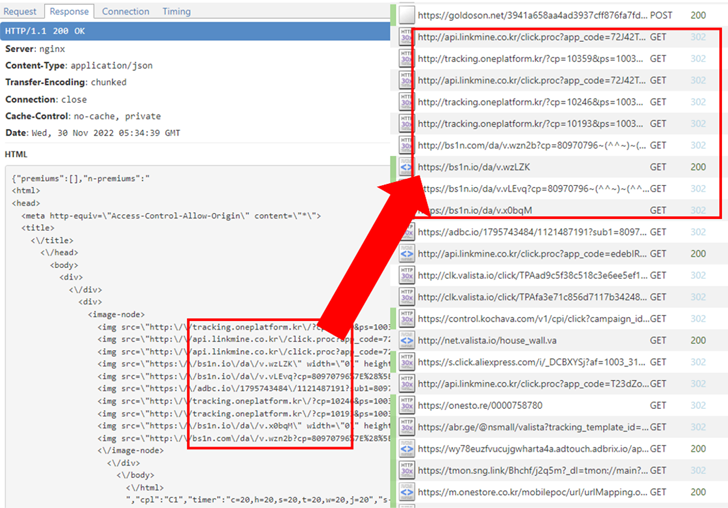
The rogue part is a part of a third-party software program library utilized by the apps in query and is able to gathering details about put in apps, Wi-Fi and Bluetooth-connected units, and GPS places.
“Furthermore, the library is armed with the performance to carry out advert fraud by clicking commercials within the background with out the person’s consent,” McAfee safety researcher SangRyol Ryu stated in a report revealed final week.
What’s extra, it contains the flexibility to stealthily load net pages, a function that may very well be abused to load advertisements for monetary revenue. It achieves this by loading HTML code in a hidden WebView and driving visitors to the URLs.
Following accountable disclosure to Google, 36 of the 63 offending apps have been pulled from the Google Play Retailer. The remaining 27 apps have been up to date to take away the malicious library.
Among the outstanding apps embody –
- L.POINT with L.PAY
- Swipe Brick Breaker (eliminated)
- Cash Supervisor Expense & Funds
- TMAP – 대리,주차,전기차 충전,킥보드를 티맵에서!
- 롯데시네마
- 지니뮤직 – genie
- 컬쳐랜드[컬쳐캐쉬]
- GOM Participant
- 메가박스 (eliminated), and
- LIVE Rating, Actual-Time Rating
The findings spotlight the necessity for app builders to be clear concerning the dependencies used of their software program, to not point out take sufficient steps to safeguard customers’ info in opposition to such abuse.
“Attackers have gotten extra refined of their makes an attempt to contaminate in any other case authentic functions throughout platforms,” Kern Smith, vp of gross sales engineering for the Americas at Zimperium, stated.
“The usage of third-party SDKs and code, and their potential to introduce malicious code into in any other case authentic functions is barely persevering with to develop as attackers begin to goal the software program provide chain to achieve the biggest footprint attainable.”
Grasp the Artwork of Darkish Internet Intelligence Gathering
Study the artwork of extracting menace intelligence from the darkish net – Be part of this expert-led webinar!
The event comes as Cyble took the wraps off a brand new Android banking trojan dubbed Chameleon that has been energetic since January 2023 and is concentrating on customers in Australia and Poland.
The trojan is not any completely different from different banking malware noticed within the wild owing to its abuse of Android’s accessibility providers to reap credentials and cookies, log keystrokes, forestall its uninstallation, and carry out different nefarious actions.
It is also designed to show rogue overlays on high of a selected listing of apps, intercept SMS messages, and even contains an unused performance that permits it to obtain and execute one other payload.
Chameleon, true to its identify, has a penchant for evasion by incorporating anti-emulation checks to detect if the machine is rooted or it is being executed in a debugging setting, and if that’s the case, terminate itself.
To mitigate such threats, customers are really useful to solely obtain apps from trusted sources, scrutinize app permissions, use sturdy passwords, allow multi-factor authentication, and train warning when receiving SMS or emails from unknown senders.