
The Glupteba malware botnet has sprung again into motion, infecting units worldwide after its operation was disrupted by Google virtually a 12 months in the past.
In December 2021, Google managed to trigger a huge disruption to the blockchain-enabled botnet, securing the courtroom orders to take management of the botnet’s infrastructure and submitting complaints towards two Russian operators.
Nozomi now reviews that blockchain transactions, TLS certificates registrations, and reverse engineering Glupteba samples present a brand new, large-scale Glupteba marketing campaign that began in June 2022 and remains to be ongoing.
Hiding within the blockchain
Glupteba is a blockchain-enabled, modular malware that infects Home windows units to mine for cryptocurrency, steal consumer credentials and cookies, and deploy proxies on Home windows techniques and IoT units.
These proxies are later offered as ‘residential proxies’ to different cybercriminals.
The malware is predominantly distributed by way of malvertising on pay-per-install (PPI) networks and site visitors distribution techniques (TDS) pushing installers disguised as free software program, movies, and films.
Glupteba makes use of the Bitcoin blockchain to evade disruption by receiving up to date lists of command and management servers it ought to contact for instructions to execute.
The botnet’s shoppers retrieve the C2 server handle utilizing a uncover operate that enumerates Bitcoin pockets servers, retrieves their transactions, and parses them to search out an AES encrypted handle.
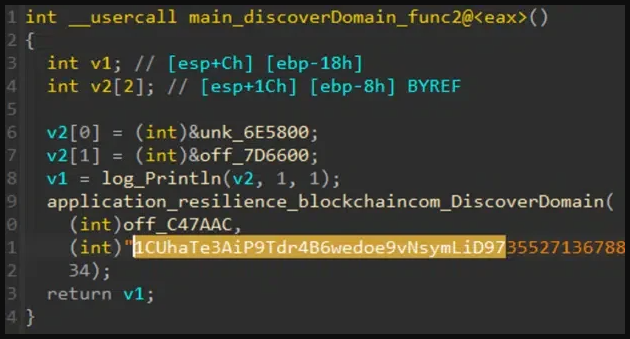
This technique has been employed by Glupteba for a number of years now, providing resilience towards takedowns.
That is as a result of blockchain transactions can’t be erased, so C2 handle takedown efforts have a restricted affect on the botnet.
Furthermore, and not using a Bitcoin personal key, legislation enforcement can not plant payloads onto the controller handle, so sudden botnet takeovers or international deactivations just like the one which impacted Emotet in early 2021 are inconceivable.
The one draw back is that the Bitcoin blockchain is public, so anybody can entry it and scrutinize transactions to collect data.
The return of Glupteba
Nozomi reviews that Glupteba continues to make use of the blockchain in the identical approach, right this moment, so its analysts scanned your complete blockchain to unearth hidden C2 domains.
The hassle was immense, involving the scrutiny of 1,500 Glupteba samples uploaded to VirusTotal to extract pockets addresses and try and decrypt transaction payload information utilizing keys related to the malware.
Lastly, Nozomi used passive DNS data to hunt for Glupteba domains and hosts and examined the most recent set of TLS certificates utilized by the malware to uncover extra details about its infrastructure.
The Nozomi investigation recognized 15 Bitcoin addresses utilized in 4 Glupteba campaigns, with the latest one beginning in June 2022, six months after Google’s disruption. This marketing campaign remains to be underway.
This marketing campaign makes use of extra Bitcoin addresses than previous operations, giving the botnet much more resilience.
.png)
Moreover, the variety of TOR hidden companies used as C2 servers has grown ten occasions for the reason that 2021 marketing campaign, following the same redundancy method.
Probably the most prolific handle had 11 transactions and communicated to 1,197 samples, with its final exercise being registered on November 8, 2022.
Nozomi additionally reviews many Glupteba area registrations as not too long ago as November 22, 2022, found through passive DNS information.
From the above, it is clear that the Glupteba botnet has returned, and the indicators point out it is extra huge than earlier than and doubtlessly much more resilient, establishing a excessive variety of fallback addresses to withstand takedowns by researchers and legislation enforcement.

