A brand new, light-weight variant of the RomCom backdoor was deployed towards members of the Girls Political Leaders (WPL) Summit in Brussels, a summit specializing in gender equality and girls in politics.
The marketing campaign used a pretend web site mimicking the official WPL portal to bait individuals searching for to attend or just within the summit.
A Pattern Micro report analyzing the brand new variant warns that its operators, tracked by the agency as ‘Void Rabisu,’ have been utilizing a stealthier backdoor with a brand new TLS-enforcement approach within the C2 (command and management) communications to make discovery more durable.
Additionally, the most recent assault cements the group’s shift from opportunistic ransomware assaults beforehand attributed to a Cuba ransomware affiliate to high-level cyberespionage marketing campaign involving the exploitation of zero-day vulnerabilities in Microsoft merchandise.
Concentrating on ladies political leaders
In August 2023, Void Rabisu arrange a malicious web site on the deal with ‘wplsummit[.]com’, designed to mimic the true Girls Political Leaders (WPL) web site hosted on wplsummit.org.
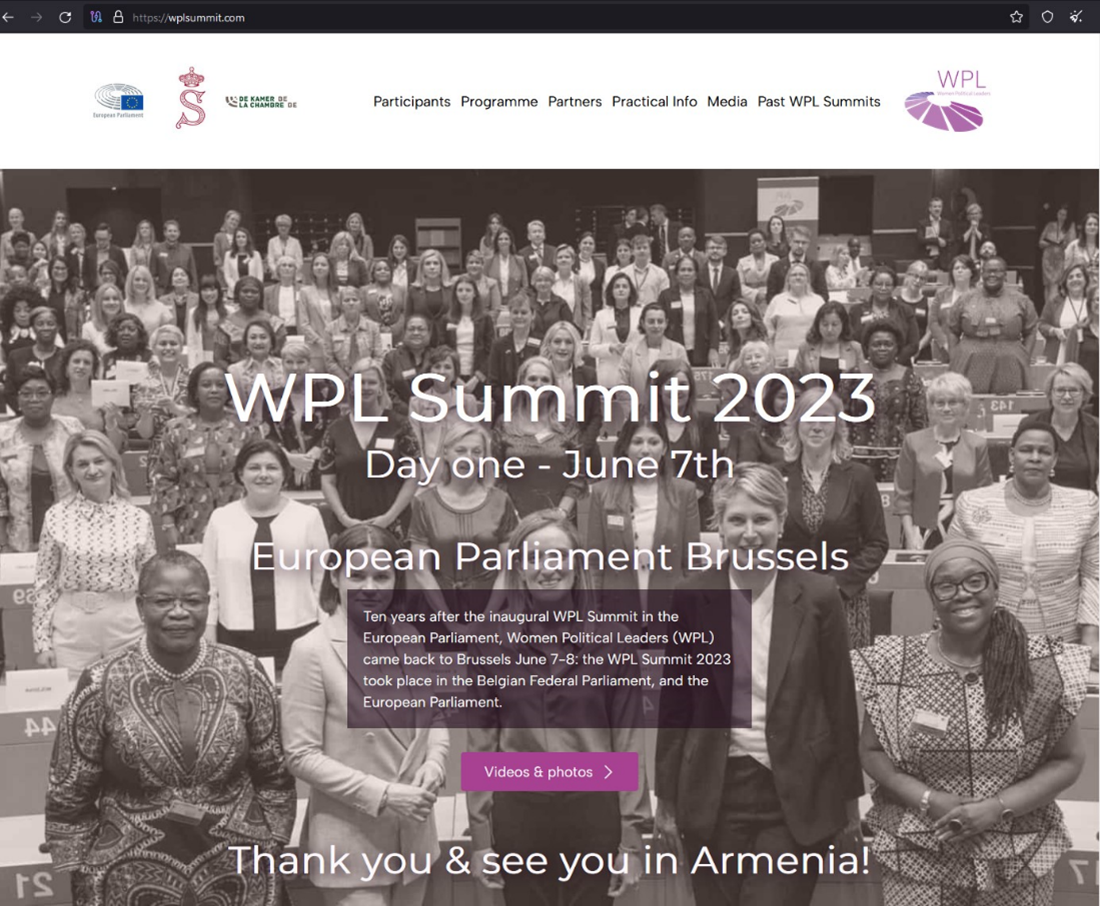
Supply: Pattern Micro
The pretend web site linked to a OneDrive folder by way of a button named ‘Movies & images,’ which contained photos from the 2 days of the occasion, taken from the real web site, and a malware downloader named ‘Unpublished Photos.’
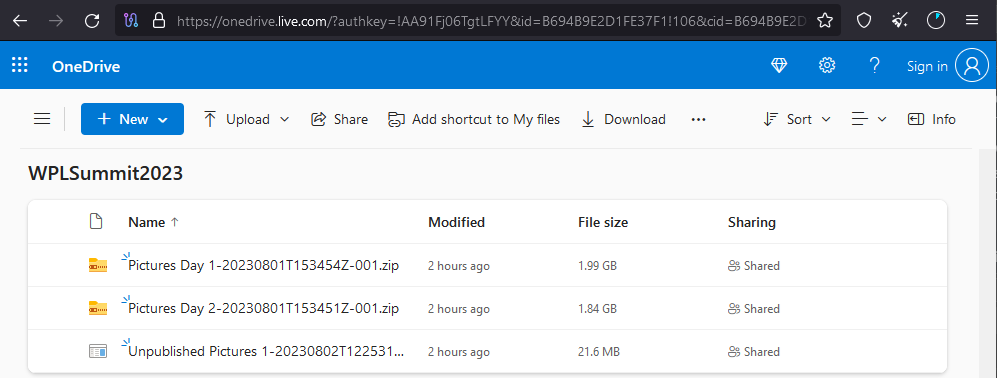
The malicious executable is signed by an Elbor LLC certificates and is a self-extracting archive containing 56 images to behave as decoys, whereas a second encrypted file is downloaded from a distant host.
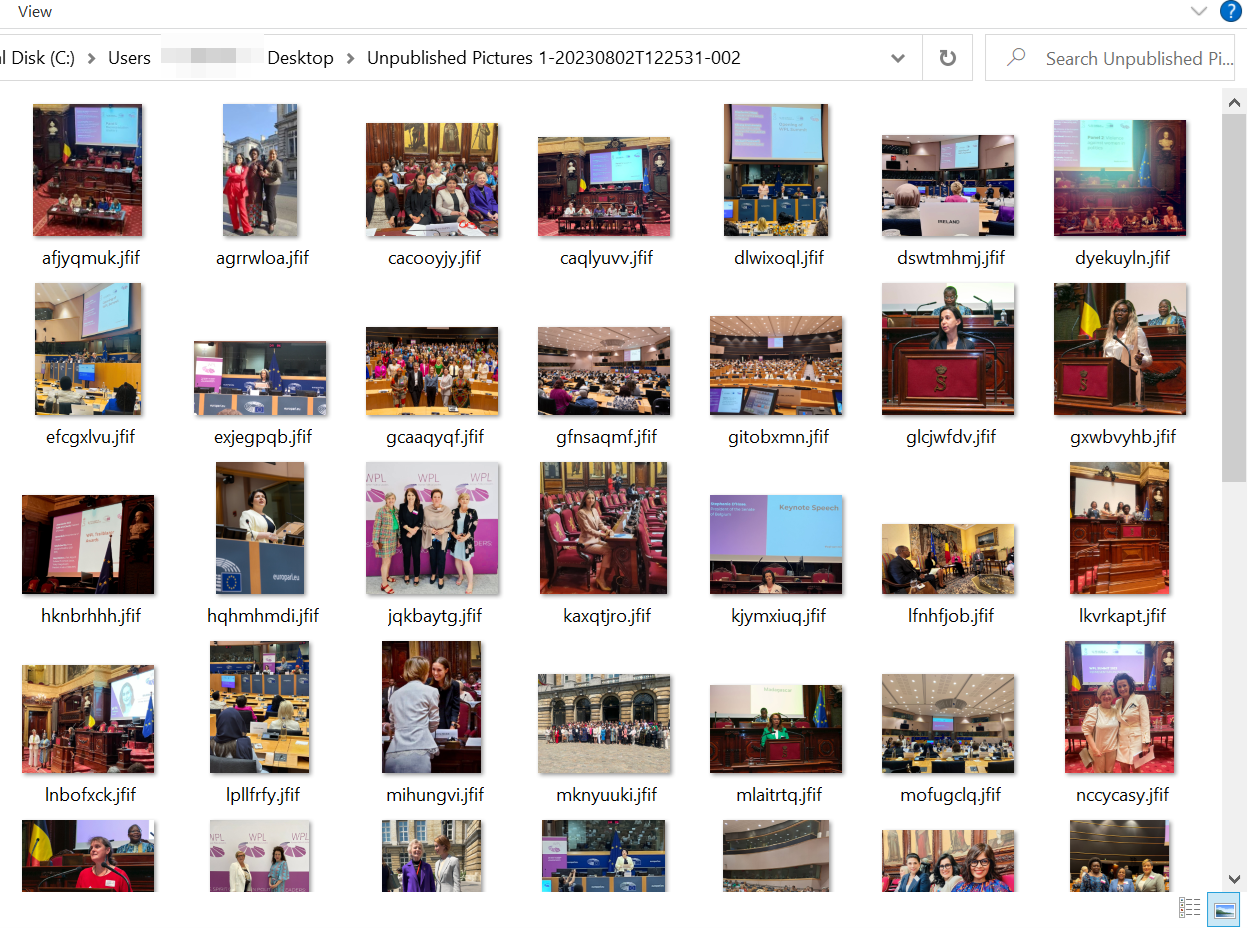
Supply: Pattern Micro
The second payload is a DLL that’s decrypted and loaded into reminiscence to evade detection and continues to fetch extra parts required for establishing communication with the attacker’s server.
Supply: Pattern Micro
RomCom 4.0
Pattern Micro identifies the most recent, stripped-down variant of RomCom because the fourth main launch of the backdoor, explaining that it is the identical malware Volexity researchers just lately named ‘Peapod.’
In comparison with RomCom 3.0, the earlier model seen in Void Rabisu operations, the brand new backdoor variant has undergone vital adjustments, making it lighter and stealthier.
It now helps solely the next ten instructions, a stark discount from the earlier 42.
- No motion – Dealing with perform returns zero; malware waits for the following command.
- Run command – Executes a command and sends again its output.
- Add file – Uploads a file to the compromised machine.
- Obtain file – Retrieves a file from the contaminated machine.
- Run command – Executes a given command.
- Replace interval – Modifies backdoor examine frequency (default 60 seconds) and updates the system registry.
- Get system information – Retrieves RAM, processor, native time, and username.
- Replace community element – Updates knowledge for the community element within the Home windows registry.
- Uninstall – Purges related registry keys and deletes related information.
- Get service identify from the Home windows registry
Additionally, as an alternative of using modified MSIs to drop its parts onto units immediately, the brand new variant leverages an EXE file to fetch XOR-encrypted DLLs, loading all its parts in reminiscence.
RomCom 4.0 has additionally included new options associated to Transport Layer Safety (TLS), a protocol designed to offer safe communication with the C2 server.
The malware has been coded to pressure WinHTTP capabilities to particularly use the TLS model 1.2 quite than permitting the working system to decide on the default TLS model.
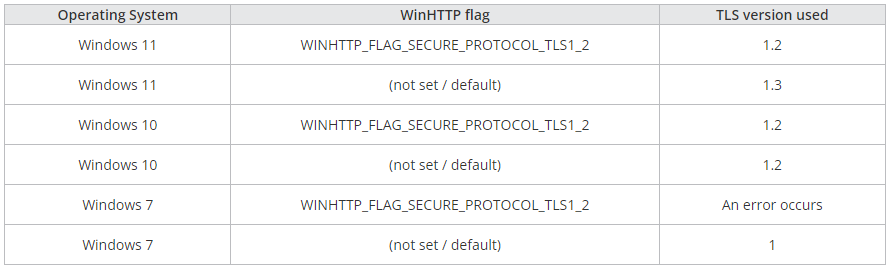
Supply: Pattern Micro
This enforcement system ends in an error on Home windows 7, which Pattern Micro considers protected towards the most recent RomCom variant.
The purpose of this mechanism is prone to make C2 communication extra immune to snooping, complicate automated discovery, and presumably enable attackers to filter out unsuitable victims.
Typically, Void Rabisu’s techniques and the deployment of the RomCom malware stay cloudy.
Nonetheless, it’s clear that the backdoor’s growth continues to be ongoing, and its operators are more and more targeted on top-level cyber espionage.
Pattern Micro concludes that it is vitally probably that Void Rabisu will goal all massive conferences associated to particular curiosity teams, so warning is suggested when visiting occasion websites.

