
Credential safety firm Past Id has launched the Zero Belief Authentication initiative for organizations to hack-proof consumer credentials, with backing from main companies.
Zero belief is a framework that secures infrastructure and knowledge, partially by eliminating arbitrary perimeter and demanding authentication from all customers and endpoints inside and outside. It contains, subsequently, credentials.
In an effort to codify simply how IT ought to apply that in observe, firms together with Zero Scaler, Optiv, Palo Alto Networks, Crowdstrike and Ping Id are supporting an initiative led by safety agency Past Id to put out a zero belief structure to inoculate company accounts and credentials in opposition to phishing and ransomware, amongst different threats.
The corporate held a digital kickoff on March 15, 2023 in New York to announce this system, which goals to deal with weak hyperlinks in safety, passwords and MFA that may permit assaults equivalent to that which led to the hacking of a LastPass engineer’s company laptop computer in 2022.
SEE: Cellular Machine Safety Coverage (TechRepublic Premium)
“Basically, we’re speaking about authentication, however authentication that rises to the zero belief stage,” stated Patrick McBride, chief advertising and marketing officer at Past Id. “As a result of so many auth protocols on the market are simply bypassed — not even a velocity bump.”
Leap to:
Passwordless, phishing free protocols amongst ZTA measures
The corporate laid out a set of measures organizations can implement to bolster defenses and insulate endpoints from lateral motion:
- Passwordless – No use of passwords or different shared secrets and techniques, as these can simply be obtained from customers, captured on networks, or hacked from databases.
- Phishing resistant – No alternative to acquire codes, magic hyperlinks, or different authentication elements by way of phishing, adversary-in-the-middle, or different assaults.
- Able to validating consumer units – Ready to make sure that requesting units are certain to a consumer and licensed to entry data property and functions.
- Able to assessing gadget safety posture – Capable of decide whether or not units adjust to safety insurance policies by checking that applicable safety settings are enabled, and safety software program is actively working.
- Able to analyzing many varieties of danger alerts – Capable of ingest and analyze knowledge from endpoints and safety and IT administration instruments.
- Steady danger evaluation – Capable of consider danger all through a session fairly than counting on one-time authentication.
- Built-in with the safety infrastructure – Integrating with a wide range of instruments within the safety infrastructure to enhance danger detection, speed up responses to suspicious behaviors, and enhance audit and compliance reporting.
How one can obtain excessive safety credentials
McBride stated that to determine excessive belief within the consumer id, a passwordless, phishing resistant MFA is crucial, e.g., a FIDO2 passkey: a FIDO2 passkey.
Primarily based on FIDO authentication requirements and utilizing uneven public/personal pairs, FIDO2 login credentials are distinctive for every site, and, like biometric passkeys, by no means depart a consumer’s gadget and are by no means saved on a server “That additionally provides phishing resistance. I’m not sending something over the community that’s usable by a nasty man,” McBride added (Determine A).
Determine A
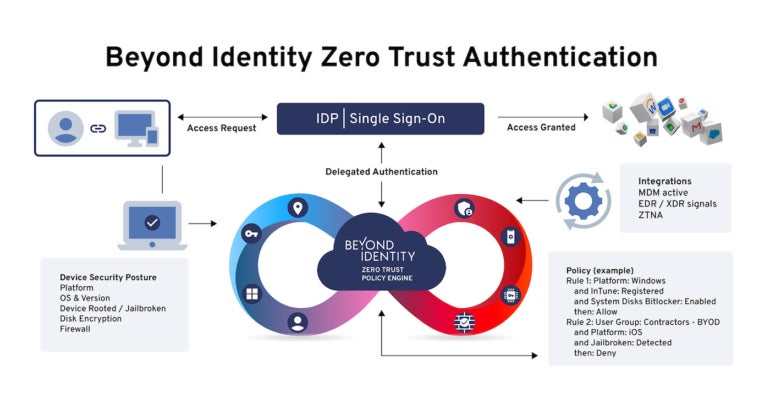
Chris Cummings, VP product and options at Past Id defined that steady monitoring is crucial to safety. He stated Past Id’s coverage engine takes alerts in and sends directions out both to authenticate or not authenticate to the one sign-on Okta, or to take motion on a selected gadget (for instance, quarantine it till the consumer or IT can examine it).
“That notion of continuity stems from Palo Alto Networks,” he stated. “They actually emphasize steady and the explanation why they work with us is as a result of we offer steady verification — one of many seven parts of Zero Belief Authentication — and so they try this for utility entry.
A key side of implementation is ease of use — eradicating time-consuming duties for the legitimate endpoint gadget consumer, famous McBride.
He defined finish customers need to have the ability to entry their units shortly, and that forcing customers although cumbersome, high-friction safety strategies usually prompts customers to modify them off totally. “We predict you possibly can have your cake and eat it too: Excessive safety with low friction,” stated McBride.
Shifting past passwords and MFA
In accordance with McBride, the ZTA ideas will assist organizations transfer past the constraints of passwords and multi-factor authentication. “Auth strategies aren’t working. Passwords are basically flawed, so in case you retailer them or transit over networks they get stolen, and each 75% to 80% of preliminary entry comes from these points,” he stated.
The ZTA protocols embrace danger scoring and what the corporate refers to as steady authentication capabilities — authentication selections which can be danger primarily based and up to date, primarily based on knowledge from cybersecurity instruments for an ‘always-on’ zero belief world, per the corporate.
SEE: 1Password is seeking to a password-free future. Right here’s why (TechRepublic)
Threats within the wild: A number of assault vectors by way of legitimate accounts
The Mitre ATT&Okay framework retains a log of cyber risk actors and strategies. Amongst them are 17 credential entry strategies used to acquire and abuse credentials of current accounts to achieve entry, persist inside a system, escalate privilege and so forth. The group notes that credentials may even be used to entry distant programs and exterior providers together with VPNs, Outlook Internet Entry, community units, and distant desktops.
A short pattern of the greater than 40 risk teams that Mitre studies have exploited legitimate accounts over the previous decade and a half contains:
- APT18: Leverages reliable credentials to log into exterior distant providers to focus on know-how, manufacturing, human rights teams, authorities and medical industries.
- Axiom: Suspected Chinese language cyber espionage group that used beforehand compromised administrative accounts to escalate privileges.
- Spider Wizard: a Russia state actor utilizing legitimate credentials for privileged accounts with the purpose of accessing area controllers.
- Polonium: A Lebanon-based group has primarily focused Israeli organizations, together with crucial manufacturing, data know-how, and protection business firms utilizing legitimate compromised credentials.
“For attackers, the preliminary vector of alternative is legitimate accounts,” stated McBride. “Refined actors use this on a regular basis and there’s an arms size listing of dangerous actors utilizing them, and so they use them as a result of they represent the ‘simple button.’ They don’t wish to burn a zero day, or use a extremely subtle technique if there’s a simple button to make use of.”
He added that phishing, opposite to widespread opinion, is the second commonest solution to deploy ransomware. Primary is logging in utilizing stolen credentials to achieve distant entry to software program, desktop or servers. “Weak authentication has actual world penalties,” he stated.
“12 months after yr, id and authentication vulnerabilities stay the one largest supply of ransomware and safety breaches, so one thing has to basically change to shut this vulnerability and allow organizations to satisfy the safety mandates issued by the White Home, NIST and CISA,” stated Chase Cunningham, chief technique officer at Ericom Software program, who’s backing the initiative, in a press release.
Jay Bretzmann, analysis VP at IDC, added: “Delivering steady verification of id — consumer and units — is crucial to assembly the promise of zero belief.. Past Id has taken the strategy to make the most of alerts from safety infrastructure in close to real-time to boost the safety normal and capitalize on current safety infrastructure investments in EDR and SASE instruments.”


