Assault surfaces are rising quicker than safety groups can sustain. To remain forward, you might want to know what’s uncovered and the place attackers are most probably to strike. With cloud migration dramatically rising the variety of inside and exterior targets, prioritizing threats and managing your assault floor from an attacker’s perspective has by no means been extra essential. Let us take a look at why it is rising, and how one can monitor and handle it correctly with instruments like Intruder.
What’s your assault floor?
First, it is essential to know that your assault floor is the sum of your digital belongings which can be ‘uncovered’ – whether or not the digital belongings are safe or weak, recognized or unknown, in lively use or not. This assault floor adjustments repeatedly over time, and consists of digital belongings which can be on-premises, within the cloud, in subsidiary networks, and in third-party environments. Briefly, it is something {that a} hacker can assault.
What’s assault floor administration?
Assault floor administration is the method of discovering these belongings and providers after which decreasing or minimizing their publicity to stop hackers exploiting them. Publicity can imply two issues: present vulnerabilities comparable to lacking patches or misconfigurations that cut back the safety of the providers or belongings. However it might probably additionally imply publicity to future vulnerabilities.
Take the instance of an admin interface like cPanel or a firewall administration web page – these could also be safe towards all recognized present assaults at the moment, however a vulnerability may very well be found within the software program tomorrow – when it instantly turns into a major threat. An asset does not have to be weak at the moment to be weak tomorrow. When you cut back your assault floor, no matter vulnerabilities, you grow to be tougher to assault tomorrow.
So, a major a part of assault floor administration is decreasing publicity to attainable future vulnerabilities by eradicating pointless providers and belongings from the web. This what led to the Deloitte breach and what distinguishes it from conventional vulnerability administration. However to do that, first you might want to know what’s there.
Asset administration vs vulnerability administration
Usually thought-about the poor relation of vulnerability administration, asset administration has historically been a labour intensive, time-consuming process for IT groups. Even after they had management of the {hardware} belongings inside their group and community perimeter, it was nonetheless fraught with issues. If only one asset was missed from the asset stock, it might evade all the vulnerability administration course of and, relying on the sensitivity of the asset, might have far reaching implications for the enterprise.
Right now, it is a complete lot extra sophisticated. Companies are migrating to SaaS and transferring their techniques and providers to the cloud, inside groups are downloading their very own workflow, mission administration and collaboration instruments, and particular person customers count on to customise their environments. When firms increase via mergers and acquisitions too, they usually take over techniques they are not even conscious of – a traditional instance is when telco TalkTalk was breached in 2015 and as much as 4 million unencrypted information have been stolen from a system they did not even know existed.
Shifting safety from IT to DevOps
Right now’s cloud platforms allow improvement groups to maneuver and scale shortly when wanted. However this places numerous the duty for safety into the palms of the event groups – shifting away from conventional, centralized IT groups with sturdy, trusted change management processes.
This implies cyber safety groups wrestle to see what’s going on or uncover the place their belongings are. Equally, it is more and more laborious for big enterprises or companies with dispersed groups – usually positioned all over the world – to maintain observe of the place all their techniques are.
Consequently, organizations more and more perceive that their vulnerability administration processes needs to be baked right into a extra holistic ‘assault floor administration’ course of since you should first know what you might have uncovered to the web earlier than you consider what vulnerabilities you might have, and what fixes to prioritize.
Important options of assault floor administration instruments
Numerous instruments in the marketplace are good for asset discovery, discovering new domains which seem like yours and recognizing web sites with related content material to your individual. Your staff can then test if it is a firm asset or not, select whether or not it is included in your vulnerability administration processes, and the way it’s secured. However this requires an inside useful resource as a result of the device cannot do that for you.
Equally, some instruments focus solely on the exterior assault floor. However since a standard assault vector is thru worker workstations, assault floor administration ought to embrace inside techniques too. Listed below are three important options that each assault floor monitoring device ought to present:
1. Asset discovery
You may’t handle an asset if you do not know it exists. As we have seen, most organizations have quite a lot of “unknown unknowns,” comparable to belongings housed on associate or third-party websites, workloads operating in public cloud environments, IoT gadgets, deserted IP addresses and credentials, and extra. Intruder’s CloudBot runs hourly checks for brand new IP addresses or hostnames in linked AWS, Google Cloud or Azure accounts.
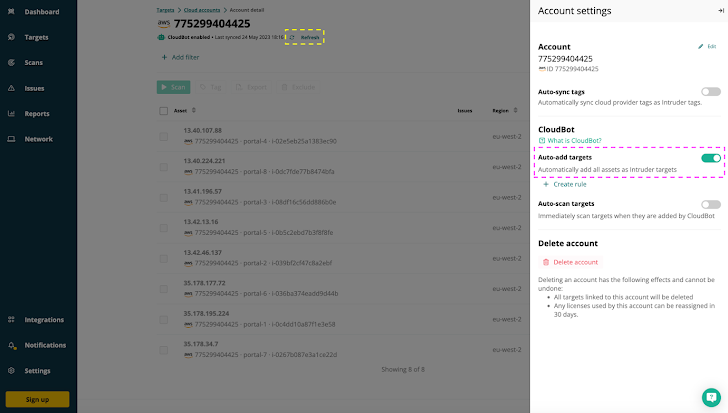 |
| Intruder’s CloudBot robotically provides any new exterior IP addresses or hostnames in cloud accounts as targets for monitoring & vulnerability scanning. |
2. Enterprise context
Not all assault vectors are created equal and the ‘context’ – what’s uncovered to the web – is a crucial a part of assault floor administration. Legacy instruments do not present this context; they deal with all assault surfaces (exterior, inside workplace, inside datacentre) the identical, and so it is laborious to prioritize vulnerabilities. Assault floor administration instruments establish the gaps in your inside and exterior safety controls to disclose the weaknesses in your safety that have to be addressed and remediated first.
Intruder takes this a step additional and supplies perception into any given asset, and the enterprise unit the applying belongs to. For instance, realizing whether or not a compromised workload is part of crucial software managing bank-to-bank SWIFT transactions will allow you to formulate your remediation plan.
3. Proactive and reactive scans
You may’t simply take a look at your assault floor as soon as. On daily basis it continues to develop as you add new gadgets, workloads, and providers. Because it grows the safety threat grows too. Not simply the danger of latest vulnerabilities, but additionally misconfigurations, knowledge exposures or different safety gaps. It is essential to check for all attainable assault vectors, and it is essential to do it repeatedly to stop your understanding from changing into outdated.
Even higher than steady scanning is a platform that may scan proactively or reactively relying on the circumstances. For instance, reacting to a brand new cloud service being introduced on-line by launching a scan, or proactively scanning all belongings as quickly as new vulnerability checks grow to be obtainable.
Decreasing your assault floor with Intruder
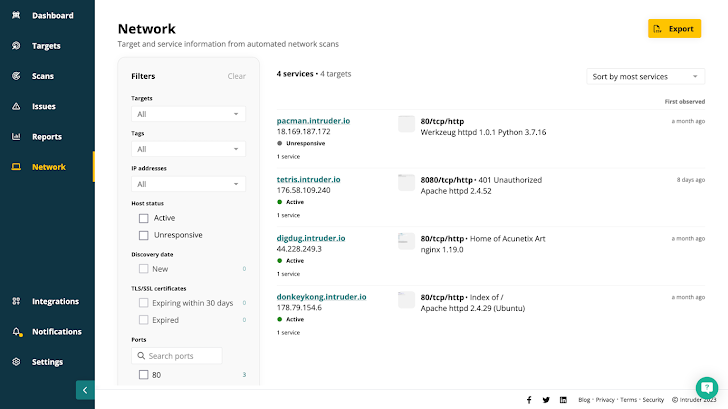
Assault floor monitoring instruments like Intruder do all this and extra. Intruder makes certain that the whole lot you might have going through the web is meant to be – by making it simply searchable and explorable. Its Community View function exhibits precisely what ports and providers can be found, together with screenshots of people who have web sites or apps operating on them.
Most automated instruments are nice at spitting out knowledge for analysts to have a look at, however not at decreasing the ‘noise’. Intruder prioritizes points and vulnerabilities primarily based on context, or whether or not they need to be on the web in any respect. Mixed with Intruder’s steady monitoring and rising risk scans, this makes it a lot simpler and faster to seek out and repair new vulnerabilities earlier than they are often exploited.
Attempt Intruder for your self!
With its assault floor monitoring capabilities, Intruder is fixing probably the most elementary issues in cybersecurity: the necessity to perceive how attackers see your group, the place they’re more likely to break in, and how one can establish, prioritize and eradicate threat.Able to get began ?