
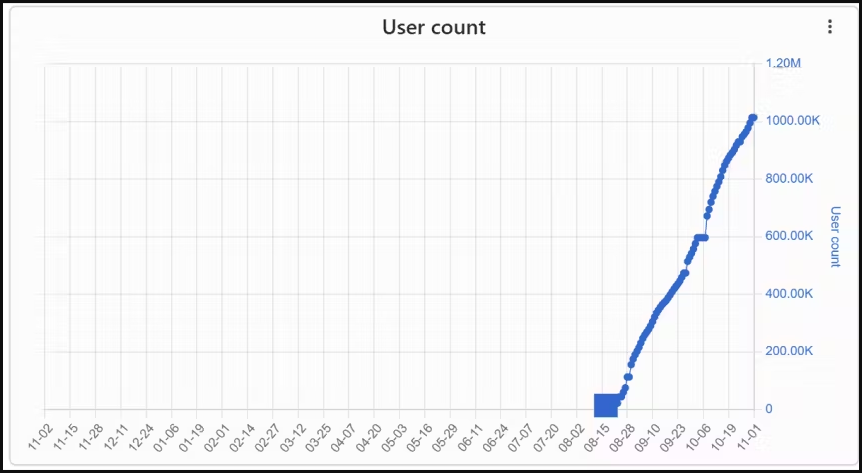
Three malicious Chrome extensions posing as VPN (Digital Personal Networks) contaminated had been downloaded 1.5 million occasions, performing as browser hijackers, cashback hack instruments, and information stealers.
In line with ReasonLabs, which found the malicious extensions, they’re unfold by way of an installer hidden in pirated copies of well-liked video video games like Grand Theft Auto, Assassins Creed, and The Sims 4, that are distributed from torrent websites.
ReasonLabs notified Google of its findings, and the tech large eliminated the offending extensions from the Chrome Net Retailer, however solely after these had amassed a complete of 1.5 million downloads.
Particularly, the malicious extensions had been netPlus (1 million installs), netSave, and netWin (500,000 installs).
Most infections are in Russia and international locations like Ukraine, Kazakhstan, and Belarus, so the marketing campaign seems to focus on Russian-speaking customers.
Planting pretend VPN extensions
ReasonLabs found over a thousand distinct torrent information that ship the malicious installer file, which is an electron app measuring between 60MB and 100MB in measurement.
The set up of the VPN extensions is automated and compelled, going down on the registry stage, and doesn’t contain the consumer or require any motion on the sufferer’s facet.
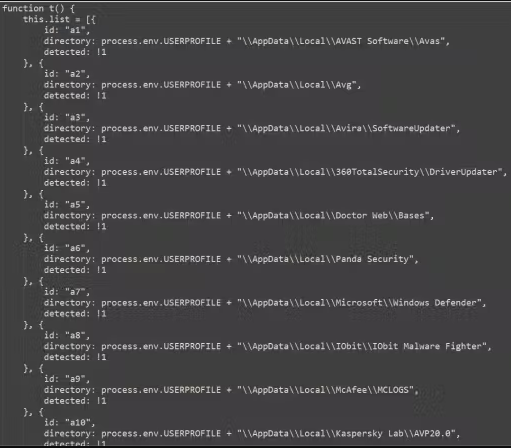
Ultimately, the installer checks for antivirus merchandise on the contaminated machine, then drops netSave on Google Chrome and netPlus on Microsoft Edge, masking both use case.
The malicious extensions use a practical VPN consumer interface with some performance and a paid subscription choice to create a way of authenticity.
Code evaluation reveals that the extension additionally has entry to “tabs,” “storage,” “proxy,” “webRequest,” “webRequestBlocking,” “declarativeNetRequest,” “scripting,” “alarms,” “cookies,” “activeTab,” “administration,” and “offscreen.”
ReasonLabs factors out that the abuse of the ‘offscreen’ permission permits the malware to run scripts by the Offscreen API and stealthily work together with the net web page’s present DOM (Doc Object Mannequin).
This in depth entry to the DOM permits the extensions to steal delicate consumer information, carry out shopping hijacks, manipulate net requests, and even disable different extensions put in on the browser.
One other perform of the extension is to disable different cashback and coupon extensions to eradicate competitors on the contaminated system and redirect earnings to the attackers.
ReasonLabs experiences the malware targets over 100 cashback extensions, together with Avast SafePrice, AVG SafePrice, Honey: Computerized Coupons & Rewards, LetyShops, Megabonus, AliRadar Buying Assistant, Yandex.Market Adviser, ChinaHelper, and Backlit.
The extensions’ communication with the C2 (command and management) servers includes information alternate regarding directions and instructions, IDing the sufferer, exfiltrating delicate information, and extra.
This report highlights the huge safety points round net browser extensions, lots of that are extremely obfuscated to make it tougher to find out what conduct they exhibit.
Because of this, it is best to routinely verify the extensions put in in your browser and verify for brand spanking new critiques within the Chrome Net Retailer to see if others are reporting malicious conduct.

