The trendy software program engineering practices of Agile and DevSecOps have revolutionized the apply of software program engineering. These methods have offered a basis for producing working software program merchandise quicker and extra reliably than ever earlier than. Nevertheless, we discovered that almost all literature about Agile and DevSecOps focuses on the product and ignores the enterprise mission and capability-delivery features of each software program product beneath growth. This hole is problematic as a result of not each group in a software-oriented group is straight concerned with the event of the product and, in reality, the enterprise mission and functionality supply features of DevSecOps are essential to the profitable supply of the product.
Increasing the view of DevSecOps past product growth permits different groups to extend their capabilities and enhance their processes. Although the first use of Agile methodologies and DevSecOps ideas could stay throughout the realm of software program product growth, “Agile strategies are getting used for complicated system and {hardware} developments as nicely.” On this SEI Weblog submit, we share our experiences leveraging DevSecOps pipelines in help of groups targeted on the potential supply and enterprise mission for his or her organizations.
The Greater Image
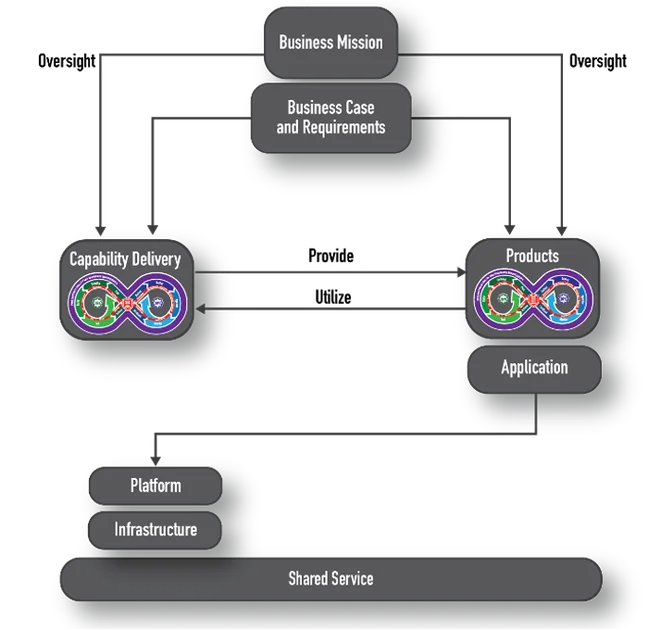
As outlined in Utilizing Mannequin-Based mostly Techniques Engineering (MBSE) to Guarantee a DevSecOps Pipeline is Sufficiently Safe and articulated in Determine 1 under, all software-oriented enterprises are pushed by three issues:
- enterprise mission
- functionality to ship worth
- merchandise
The enterprise mission captures stakeholder wants and channels the entire enterprise in assembly these wants. The enterprise mission is owned by the group’s management and is supported by varied enterprise capabilities, relying on the area through which the enterprise operates. This a part of the enterprise can reply the questions why and for whom the enterprise exists.
The functionality to ship worth in a software-oriented enterprise covers the folks, processes, and expertise obligatory to construct, deploy, and function the enterprise’s merchandise. On the whole, this enterprise concern consists of the software program manufacturing unit and product operational environments, nevertheless it doesn’t include the merchandise themselves.
Merchandise, generically, are the items of worth delivered by the group. In a software-oriented enterprise, these merchandise embody the parts, purposes, providers, and outputs which might be delivered, deployed, and operated to be used by the group’s clients. These merchandise make the most of the capabilities delivered by the software program manufacturing unit and operational environments.
The enterprise offers the enterprise case and necessities to every of the opposite issues which might be accountable for offering the potential to ship worth and the worth itself. Each functionality supply and product growth execute utilizing totally different course of steps to attain their deliberate outcomes. They, nevertheless, have to synchronize with one another periodically to make sure that the software program manufacturing unit and operational environments stay able to assembly the wants of the merchandise beneath growth.
Leveraging Pipelines to Implement Agile and DevSecOps Ideas
We’ve established that not each group in a software-oriented group is concentrated particularly on the engineering of the software program product. We frequently encounter groups supporting the enterprise mission or the potential to ship worth, however not the writing of code. These groups can nonetheless profit from the event and use of steady integration/steady supply (CI/CD) pipelines.
It’s virtually not possible to debate DevSecOps with out speaking about pipelines. Enablement of steady integration/steady supply (CI/CD) pipelines is a key side of DevSecOps, and we contemplate it a finest apply of the Agile methodology. As famous in an earlier submit, a CI/CD pipeline offers for the automated vetting, constructing, testing, packaging, and supply of a change to a product within the desired vacation spot.
The everyday software-product-focused DevSecOps pipeline is depicted in Determine 2. As famous within the introduction to the DevSecOps Pipeline Impartial Mannequin, this pipeline seamlessly integrates “three conventional factions that generally have opposing pursuits: growth; which values options; safety, which values defensibility; and operations, which values stability.”
A easy implementation of the software-product-focused pipeline in Determine 2 could be described within the following steps:
- A patch or new function for the product is accepted and assigned a precedence for implementation.
- A developer implements the chosen patch and/or new function for the product and submits the modifications to a version-control system.
- Automated construct processes for the product are initiated.
- If construct processes are profitable, automated assessments are executed on the product, together with verifying the developer-used correct secure-coding practices.
- If all assessments are profitable, a launch package deal is produced.
- If packaging processes are profitable, the discharge package deal is delivered manually to the manufacturing techniques.
- Bundle deliveries provoke automated set up or improve processes for the product on the manufacturing techniques.
- Over time, operations personnel implement and automate monitoring capabilities for the product.
- A person observes the product’s performance and requests a patch or a brand new function within the product. This request is fed again to step 1.
As depicted within the infinity diagram, every of the steps within the pipeline integrates safety controls acceptable for the product. Nevertheless, this instance pipeline might not be mapped readily to all conditions. There are settings through which group processes would profit from the usage of a pipeline, however the place the precise steps and procedures differ from this software-product-focused archetype.
In our varied buyer engagements, now we have discovered many advantages within the software of a CI/CD pipeline, leveraging the ideas and practices of Agile and DevSecOps to make knowledgeable choices about course of enhancements.
Pipeline Purposes in Atypical Settings
First Utility: Software program Growth Surroundings
Our first instance is firmly rooted within the Functionality Supply department proven in Determine 1. In help of our authorities consumer, we labored on the deployment, operation, and ongoing upkeep of a growth setting. This setting was designed to allow the product growth groups to use Agile and DevSecOps ideas within the growth of their software program merchandise. Duties concerned the set-up of bodily servers, networking gadgets, a virtualization platform, a growth platform, storage techniques, and the administration of endpoint system software program.
The aptitude supply group should steadiness three separate issues: upkeep of insurance policies and practices, upkeep of the infrastructure that hosts the product beneath growth’s pipeline, and upkeep of the product’s pipeline. Every process might need a barely totally different pipeline. All of the competing-but-related issues are maintained on their very own cycles and timelines over the course of the event setting’s lifecycle. Although all of them depend upon each other, in addition they are separate entities.
On this setting, on the potential supply group, our pipeline regarded barely totally different from the instance above:
- A repair or a brand new functionality to be deployed within the setting is accepted for implementation and assigned a precedence for implementation.
- The group evaluates the out there expertise and selects the required {hardware} and/or software program to help the repair/new functionality.
- The group obtains the brand new {hardware} and/or software program.
- The group integrates the brand new {hardware} and/or software program with the prevailing infrastructure (ideally in a check setting, not manufacturing!) and validates that it’s working accurately.
- The repair and/or new functionality is made out there to the top customers.
- Over time, operations personnel implement and automate monitoring capabilities for the product.
- The group collects info from finish customers about how the repair/new functionality is working and makes use of that info to tell the planning for the subsequent set of fixes and options. This info is fed again into Step 1.
On this pipeline, many concerns in a roundabout way associated to the event of the product could impression the product growth groups. Step 1 of the pipeline should contemplate each enhancements for the potential supply group (together with updates to low-level techniques that preserve the setting working easily, like storage, networking, a area identify system (DNS), time synchronization, identification administration, and configuration administration) and builders’ providers (resembling a version-control system, container registry, and subject tracker). Builders care about whether or not the code repository is working accurately and whether or not they can entry the construct system. Each units of priorities have to be balanced throughout planning.
Second Utility: Acquisitions Group
Our second instance pertains to the enterprise mission of a corporation. We labored with the acquisitions group to implement course of enhancements to their current procedures for gathering approvals and documenting the acquisition course of. We proposed and applied a technical resolution after which, because the group used the brand new expertise, we used the iterative pipeline under to maintain bettering the group’s processes.
Firstly of the method, the group used a totally paper-based resolution through which a folder of knowledge was handed from individual to individual to evaluation (and approve or reject) the submitted paperwork. Our first process was to assemble necessities to grasp the group’s present processes. Subsequent, primarily based on the group’s necessities, we arrange the technical instruments required to trace acquisition requests. Then, we launched the group to the brand new procedures that leveraged the technical instruments. From there, we gathered suggestions from the group and made obligatory changes to make the system prepared for customers. The acquisitions group’s pipeline was additionally totally different from the usual software program growth pipeline.
- Based mostly on necessities and suggestions from group members, change requests are submitted after which mentioned to make sure that the modifications might be helpful general.
- The configuration of the technical device is modified to mirror the chosen change.
- The group begins to make use of the up to date device configuration.
- The group offers info on its experiences with the brand new device configuration, each optimistic and damaging, that’s fed again into the starting stage the place modifications to the method are thought-about, prioritized, and applied.
Over time, each requests and utilization started to grow to be clear. This readability stemmed from familiarity with the system and from the customers’ adoption of the Agile mindset of regularly bettering the device to make their lives simpler. This familiarity was very encouraging and allowed fulfilling requests at a quicker tempo. Ultimately, the system turned extra secure, and there weren’t any main modifications by way of change requests. This case allowed the acquisitions group to conduct an evaluation and evaluate the speed of completion to the paper course of.
Pipeline Comparability
Within the two instance pipelines we’ve introduced, there are 4 widespread features over which the pipelines iterate:
- Choose a change.
- Implement the change.
- Observe the impression of the change.
- Make an knowledgeable resolution in regards to the subsequent change.
In our three examples, the principle variations could be summarized briefly: the mechanisms for implementing the modifications are totally different. There are totally different ranges of automation in a position for use in every case. There are totally different timelines for implementing and vetting every change. There are totally different prices to implementing every change; some modifications require purchases, others require effort.
Agile Classes Realized and Alternatives
Implementing the pipelines in these organizations was difficult, and we realized so much via our efforts. First, as a result of the DevSecOps literature presently out there is concentrated on methods for the product groups, it won’t at all times be apparent that different forms of groups can profit from making use of DevSecOps ideas. Nevertheless, it appears that evidently this development is beginning to shift, and we’re starting to see extra literature aimed toward extending the applying of DevSecOps and Agile into non-product areas. The Platform Impartial Mannequin highlights this development in its distinction between the Product Circulation and System Circulation. Practitioners are additionally discussing this development with extra frequency (https://www.usenix.org/convention/srecon22emea/presentation/looney). We predict it’s necessary for DevSecOps practitioners to search for new alternatives to behave as DevSecOps evangelists, who share the advantages of DevSecOps and Agile practices and ideas at any time when they’ve the chance to work with a brand new group.
Second, we’ve realized that generally the duties in a roundabout way associated to product growth aren’t related to the product groups utilizing the environments. Consequently, these duties don’t get a excessive precedence for implementation. When these things are beneath prioritized, the result’s an setting that’s not as resilient and mature because it could possibly be. In some unspecified time in the future sooner or later, this may have a damaging impression the product groups.
The answer to this problem is to make sure that the continued upkeep of the potential supply setting is allotted ample assets to take care of present and future points. To allocate assets appropriately, we expect it’s necessary for the potential supply groups to interact repeatedly with the product groups and with the managers accountable for overseeing the enterprise’s mission. In so doing, they need to talk the significance of the upkeep actions that impression the long-term well being, safety, and compliance of the potential.
Third, we don’t work in a vacuum, and we’ve realized that each the technical and cultural environments continually change. Groups should assess and adapt to those modifications to proceed to function on the highest degree. For technical and non-technical groups alike, in each the capability-delivery and business-mission realms, documentation have to be curated, new paperwork created as normal working procedures change, and previous paperwork are revised or eliminated as they grow to be out of date. Likewise, these groups should groom their process backlogs, eradicating these duties which might be now not related and prioritizing duties in response to the present mission and aims of the group.
Fourth, we’ve realized that it may be very tempting to be too agile, rapidly abandoning a high-level plan within the face of sudden technical points. When issues aren’t dealt with correctly, it’s simple to each create technical debt and grow to be consumed by the fire-fighting cadence. So, how do you keep away from the technical debt? Start by making a high-level plan that has correct effort and time inbuilt to permit every step within the plan to be correctly applied. This isn’t to say that the plan have to be rigidly adopted to completion (as a result of that wouldn’t be following Agile ideas) however to vary the plan as wanted and put it to use at each stage. Overcoming this problem additionally requires good communication with the opposite associated groups, particularly the administration group.
Lastly, now we have realized that these atypical purposes of DevSecOps and Agile nonetheless encountered a few of the identical challenges confronted by product groups. Particularly, that change in a corporation is tough, and Agile and DevSecOps practitioners ought to anticipate to satisfy some resistance and expertise some pushback when advocating for the establishment of Agile and DevSecOps practices. We have now noticed the next criticisms of the workflow modifications:
- skepticism in regards to the effectiveness of the brand new methodologies
- outright refusal to make use of new methodologies and instruments
- the concept ceremonies (i.e., conferences) are an excessive amount of of a burden
- resistance to the thought of estimating how lengthy some duties will take
- hesitancy to hitch retrospective conferences the place errors and errors are mentioned
We definitely can’t present options for each one of many cultural and personnel points you might encounter, however we provide what we expect are two keys to efficiently navigating these challenges.
First, coaching and onboarding for the group can ease the assimilation course of, guaranteeing that everybody on the group understands the overriding objectives of the actions and ceremonies being carried out. In some circumstances, wholesome skepticism can result in distinctive options. For added insights into mitigating worker resistance, take a look at the weblog submit Six Treatments to Worker Resistance to DevOps.
Second, be certain that Agile ceremonies and DevSecOps practices and processes are strategically chosen and executed. The chosen ceremonies and processes ought to help the group’s objectives and allow the group to persistently produce high quality work. Deciding on ceremonies and processes is a strategic exercise that may produce advantages, resembling a discount in impediments to day by day work and avoidance of technical debt. Execution of the chosen ceremonies have to be on level. Conferences seen as too lengthy or missing in worth are sometimes met with disdain by individuals. Efficient ceremonies will encourage communication among the many group, assist the group preserve give attention to a standard aim, and foster the group’s understanding of how their work will obtain that aim. For extra communication methods, take a look at this webcast through which our colleagues provide instruments to assist organizations shift the tradition to attain DevSecOps.
The Advantages of Adaptation
In an effort to lower the effort and time required to launch software program merchandise, the DoD has lengthy beneficial the usage of Agile strategies in software program engineering. Furthermore, since 2009 the DoD has advocated for the usage of Agile ideas throughout the acquisition of IT techniques. Our expertise has proven that when used exterior the scope of a conventional, product growth setting, Agile and DevSecOps ideas have the potential to enhance the productiveness of groups targeted on enterprise mission and functionality deliveries.
The mindset, processes, and practices adopted from Agile and DevSecOps, together with the usage of iterative pipelines and the fixed incorporation of suggestions, could be utilized in non-traditional methods by quite a lot of groups, with the last word aim of bettering group processes. Inevitably, challenges will come up, however as we’ve found, there are beneficial classes to be realized and utilized all through the method, and we’re assured that the advantages of leveraging the tried-and-true Agile and DevSecOps ideas outweigh the downsides.