One irritating facet of e-mail phishing is the frequency with which scammers fall again on tried-and-true strategies that actually haven’t any enterprise working today. Like attaching a phishing e-mail to a conventional, clear e-mail message, or leveraging hyperlink redirects on LinkedIn, or abusing an encoding methodology that makes it straightforward to disguise booby-trapped Microsoft Home windows information as comparatively innocent paperwork.
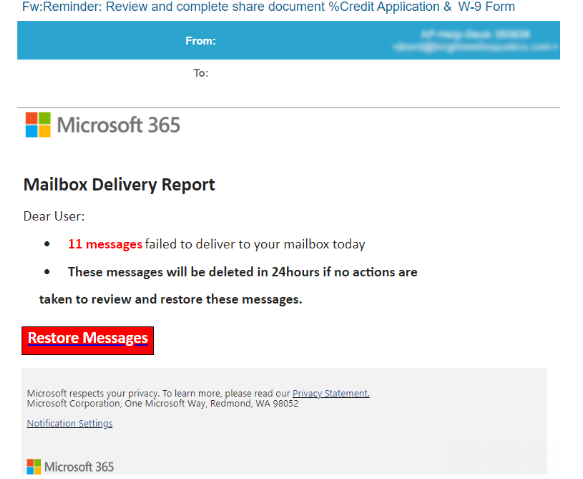
KrebsOnSecurity just lately heard from a reader who was puzzled over an e-mail he’d simply acquired saying he wanted to evaluation and full a equipped W-9 tax type. The missive was made to seem as if it had been a part of a mailbox supply report from Microsoft 365 about messages that had did not ship.
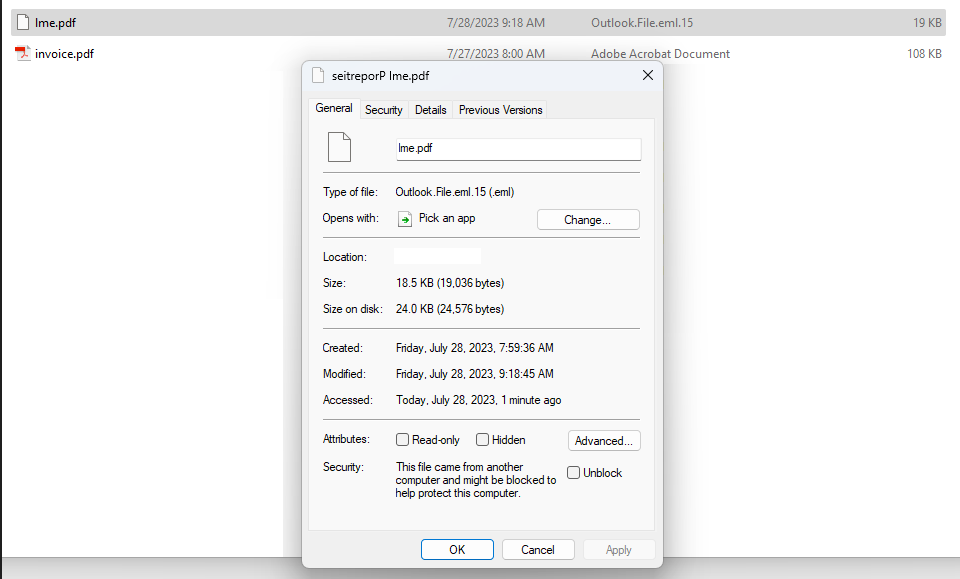
The reader, who requested to stay nameless, stated the phishing message contained an attachment that appeared to have a file extension of “.pdf,” however one thing about it appeared off. For instance, when he downloaded and tried to rename the file, the correct arrow key on the keyboard moved his cursor to the left, and vice versa.
The file included on this phishing rip-off makes use of what’s often known as a “right-to-left override” or RLO character. RLO is a particular character inside unicode — an encoding system that permits computer systems to alternate info whatever the language used — that helps languages written from proper to left, reminiscent of Arabic and Hebrew.
Look rigorously on the screenshot under and also you’ll discover that whereas Microsoft Home windows says the file hooked up to the phishing message is called “lme.pdf,” the complete filename is “pdf.eml Properties” spelled backwards. In essence, it is a .eml file — an piece of email format or e-mail saved in plain textual content — masquerading as a .PDF file.
“The e-mail got here via Microsoft Workplace 365 with all of the detections turned on and was not caught,” the reader continued. “When the identical e-mail is distributed via Mimecast, Mimecast is wise sufficient to detect the encoding and it renames the attachment to ‘___fdp.eml.’ One would assume Microsoft would have had loads of time by now to deal with this.”
Certainly, KrebsOnSecurity first lined RLO-based phishing assaults again in 2011, and even then it wasn’t a brand new trick.
Opening the .eml file generates a rendering of a webpage that mimics an alert from Microsoft about wayward messages awaiting restoration to your inbox. Clicking on the “Restore Messages” hyperlink there bounces you thru an open redirect on LinkedIn earlier than forwarding to the phishing webpage.
As famous right here final 12 months, scammers have lengthy taken benefit of a advertising function on the enterprise networking website which lets them create a LinkedIn.com hyperlink that bounces your browser to different web sites, reminiscent of phishing pages that mimic high on-line manufacturers (however mainly Linkedin’s dad or mum agency Microsoft).
The touchdown web page after the LinkedIn redirect shows what seems to be an Workplace 365 login web page, which is of course a phishing web site made to seem like an official Microsoft Workplace property.
In abstract, this phishing rip-off makes use of an outdated RLO trick to idiot Microsoft Home windows into considering the hooked up file is one thing else, and when clicked the hyperlink makes use of an open redirect on a Microsoft-owned web site (LinkedIn) to ship folks to a phishing web page that spoofs Microsoft and tries to steal buyer e-mail credentials.
In accordance with the newest figures from Test Level Software program, Microsoft was by far essentially the most impersonated model for phishing scams within the second quarter of 2023, accounting for almost 30 p.c of all model phishing makes an attempt.
An unsolicited message that arrives with one in every of these .eml information as an attachment is greater than more likely to be a phishing lure. The most effective recommendation to sidestep phishing scams is to keep away from clicking on hyperlinks that arrive unbidden in emails, textual content messages and different mediums. Most phishing scams invoke a temporal factor that warns of dire penalties must you fail to reply or act rapidly.
If you happen to’re not sure whether or not a message is professional, take a deep breath and go to the positioning or service in query manually — ideally, utilizing a browser bookmark to keep away from potential typosquatting websites.