
Dropbox disclosed a safety breach after menace actors stole 130 code repositories after getting access to one among its GitHub accounts utilizing worker credentials stolen in a phishing assault.
The corporate found the attackers breached the account on October 14 when GitHub notified it of suspicious exercise that began sooner or later earlier than the alert was despatched.
“So far, our investigation has discovered that the code accessed by this menace actor contained some credentials—primarily, API keys—utilized by Dropbox builders,” Dropbox revealed on Tuesday.
“The code and the info round it additionally included just a few thousand names and electronic mail addresses belonging to Dropbox staff, present and previous prospects, gross sales leads, and distributors (for context, Dropbox has greater than 700 million registered customers).”
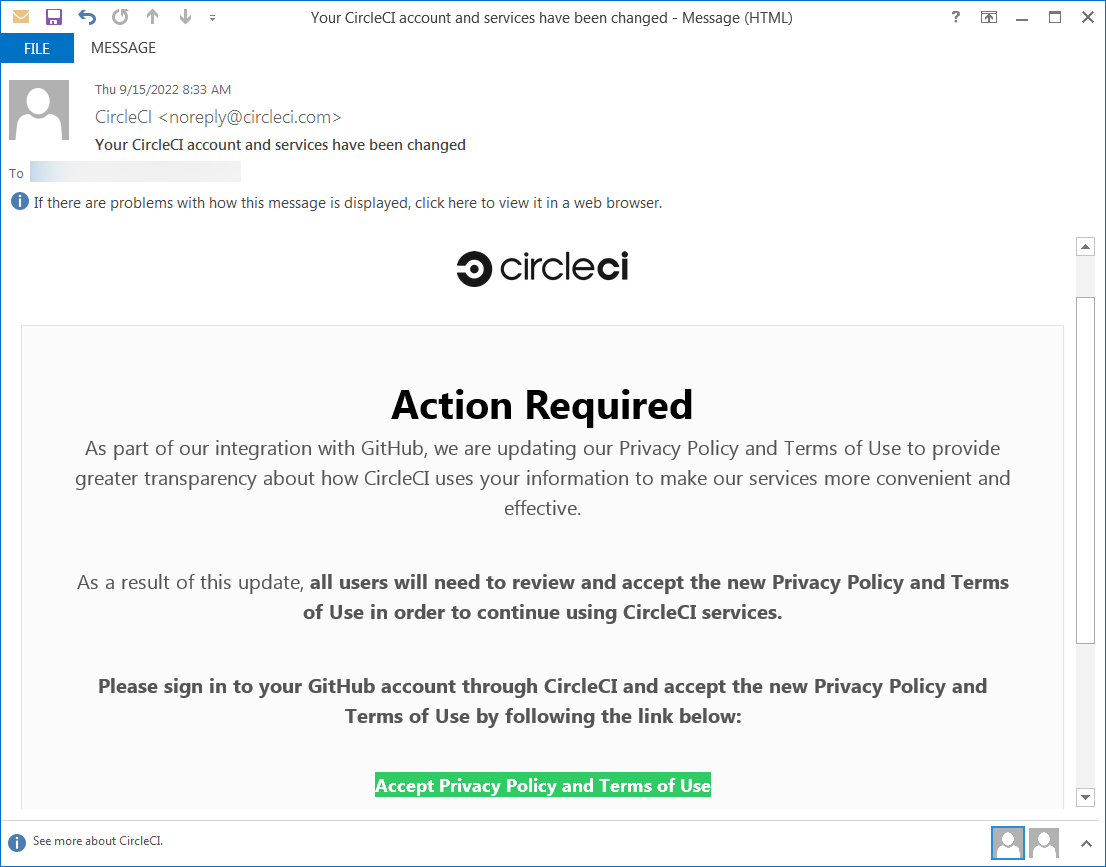
The profitable breach resulted from a phishing assault that focused a number of Dropbox staff utilizing emails impersonating the CircleCI steady integration and supply platform and redirecting them to a phishing touchdown web page the place they have been requested to enter their GitHub username and password.
On the identical phishing web page, the staff have been additionally requested to “use their {hardware} authentication key to move a One Time Password (OTP).”
130 code repositories have been stolen throughout the breach
After stealing the Dropboxers’ credentials, the attackers gained entry to one among Dropbox’s GitHub organizations and stole 130 of its code repositories.
“These repositories included our personal copies of third-party libraries barely modified to be used by Dropbox, inside prototypes, and a few instruments and configuration recordsdata utilized by the safety workforce,” the corporate added.
“Importantly, they didn’t embrace code for our core apps or infrastructure. Entry to these repositories is much more restricted and strictly managed.”
Dropbox added that the attackers by no means had entry to prospects’ accounts, passwords, or fee data, and its core apps and infrastructure weren’t affected on account of this breach.
In response to the incident, Dropbox is engaged on securing its complete surroundings utilizing WebAuthn and {hardware} tokens or biometric components.
In September, different GitHub customers have been additionally focused in an analogous assault impersonating the CircleCI platform and asking them to signal into their GitHub accounts to simply accept person phrases and privateness coverage updates to maintain utilizing the service.
“Whereas GitHub itself was not affected, the marketing campaign has impacted many sufferer organizations,” GitHub mentioned in an advisory on the time.
GitHub mentioned it detected content material exfiltration from non-public repositories nearly instantly after the compromise, with the menace actors utilizing VPN or proxy companies to make tracing them tougher.

