A sophisticated persistent menace (APT) actor referred to as Dragon Breath has been noticed including new layers of complexity to its assaults by adopting a novel DLL side-loading mechanism.
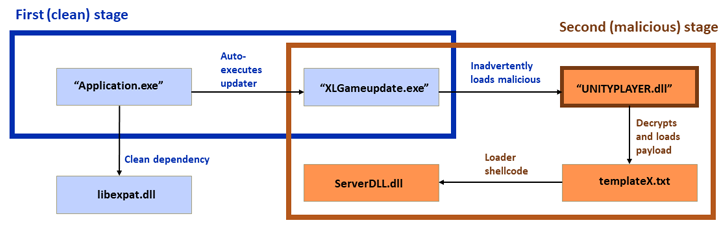
“The assault relies on a basic side-loading assault, consisting of a clear software, a malicious loader, and an encrypted payload, with varied modifications made to those elements over time,” Sophos researcher Gabor Szappanos stated.
“The most recent campaigns add a twist by which a first-stage clear software ‘facet’-loads a second clear software and auto-executes it. The second clear software side-loads the malicious loader DLL. After that, the malicious loader DLL executes the ultimate payload.”
Operation Dragon Breath, additionally tracked beneath the names APT-Q-27 and Golden Eye, was first documented by QiAnXin in 2020, detailing a watering gap marketing campaign designed to trick customers into downloading a trojanized Home windows installer for Telegram.
A subsequent marketing campaign detailed by the Chinese language cybersecurity firm in Might 2022 highlighted the continued use of Telegram installers as a lure to deploy further payloads corresponding to gh0st RAT.
Dragon Breath can be stated to be half of a bigger entity known as Miuuti Group, with the adversary characterised as a “Chinese language-speaking” entity focusing on the web gaming and playing industries, becoming a member of the likes of different Chinese language exercise clusters like Dragon Castling, Dragon Dance, and Earth Berberoka.
The double-dip DLL side-loading technique, per Sophos, has been leveraged in assaults focusing on customers within the Philippines, Japan, Taiwan, Singapore, Hong Kong, and China. These tried intrusions have been finally unsuccessful.
The preliminary vector is a faux web site internet hosting an installer for Telegram that, when opened, creates a desktop shortcut that is designed to load malicious elements behind the scenes upon launch, whereas additionally displaying to the sufferer the Telegram app person interface.
What’s extra, the adversary is believed to have created a number of variations of the scheme by which tampered installers for different apps, corresponding to LetsVPN and WhatsApp, are used to provoke the assault chain.
Be taught to Cease Ransomware with Actual-Time Safety
Be part of our webinar and learn to cease ransomware assaults of their tracks with real-time MFA and repair account safety.
The subsequent stage entails the usage of a second clear software as an intermediate to keep away from detection and cargo the ultimate payload through a malicious DLL.
The payload capabilities as a backdoor able to downloading and executing information, clearing occasion logs, extracting and setting clipboard content material, working arbitrary instructions, and stealing cryptocurrency from the MetaMask pockets extension for Google Chrome.
“DLL sideloading, first recognized in Home windows merchandise in 2010 however prevalent throughout a number of platforms, continues to be an efficient and interesting tactic for menace actors,” Szappanos stated.
“This double-clean-app method employed by the Dragon Breath group, focusing on a person sector (on-line playing) that has historically been much less scrutinized by safety researchers, represents the continued vitality of this method.”