Our buddies at BlackBerry lately launched an in-depth weblog publish on a marketing campaign by risk actors concentrating on on-line cost companies that discusses what occurs from preliminary compromise to the skimmer scripts themselves. You possibly can learn their weblog right here. This weblog is targeted on what we discovered throughout the AT&T Cybersecurity buyer base as we regarded for the indications of compromise (IOCs) recognized within the BlackBerry weblog and on the quick-follow up evaluation we carried out and supplied to our prospects.
As part of the AT&T Managed Risk Detection and Response (MTDR) risk hunter workforce, we’ve the distinctive alternative to carry out risk searching throughout our fleet of consumers in a really quick and environment friendly method. Leveraging the logs throughout tons of of information sources, we are able to provide you with our personal hunt hypotheses and develop extraordinarily complicated searches to seek out potential prior incidents and compromises.
We are able to additionally work with the AT&T Alien Labs workforce to show that search syntax right into a correlation rule. The Alien Labs workforce makes use of this backend knowledge that we collect to create hundreds of guidelines and signatures throughout the USM Wherever platform. Risk hunters can even seek for particular identified ways, strategies, and procedures (TTPs) and indicators of compromise (IOCs) as we ingest and course of cyber risk intelligence from each open sources (i.e., publicly out there knowledge) and closed sources (i.e., authorities or non-public knowledge that’s not publicly out there).
Once we regarded for the TTPs that the attackers had been utilizing to deploy the bank card skimming scripts, our searches yielded no outcomes, however once we looked for IOCs associated to the place the bank card knowledge was exfiltrated throughout this marketing campaign, we noticed one area come up throughout a number of prospects. Armed with key data corresponding to time frames and which prospects and customers had been impacted, we might now go deeper into USM Wherever to research.
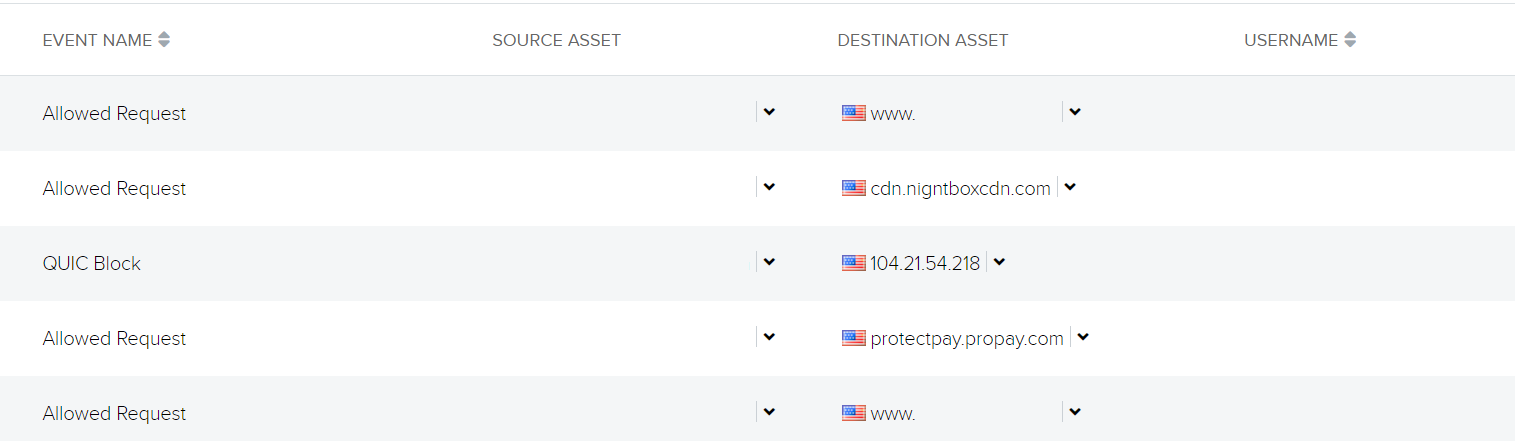
Determine 1 – Net request for bank card skimming exfiltration area
Determine 1 reveals that the request for the bank card skimming website referred from one other web site for a widely known meals firm with a web-based buying choice. We noticed this to be the case for all the opposite prospects too, with the meals website being both the direct referer or being the HTTP request proper earlier than the connection to the cdn[.]nightboxcdn[.]com website. One of many different noticed impacted prospects had a consumer’s credit score data skimmed from a distinct compromised website (see Determine 2).
Determine 2 – Visitors going to procuring website (redacted) adopted by site visitors to the skim exfiltration after which a respectable cost website
We are able to see that the consumer is on a web-based procuring website (redacted) adopted by site visitors to the exfiltration area in addition to to a respectable cost portal service. We are able to conclude from the site visitors move that the consumer went to checkout and that after they enter their cost particulars, this data went to each the exfiltration website and the respectable cost service, ProPay.
By utilizing the web site scanning device urlscan.io and by taking a look at a scan of the procuring website from Could 23, 2023, we might see the skimming script appended to the jquery.hoverIntent.js file (respectable script ends after });).
Determine 3 – Skimming script appended to respectable script
As soon as we decode the attacker-added code snippet and simplify it right down to its most simple elements, we are able to see that it extracts the sphere values of first identify, final identify, cellphone quantity, e mail deal with, deal with, metropolis, state, zip, card holder identify, card quantity, expiration month and 12 months, and CVV. The info will then be despatched to the exfiltration area by way of a XMLHttpRequest:
Determine 4 – Decoded and simplified skimmer script
After we uncovered what was occurring, we shortly notified our impacted prospects so they may advise their staff to request new bank card numbers from their banks. Whereas it was good to know that our prospects weren’t straight compromised by the risk actor deploying these card skimmer scripts, the assaults show the must be to be continuously conscious of the potential for different organizations to be compromised and the impression this might have on your finish customers.
Leveraging a defense-in-depth technique that features endpoint detection and response instruments, community controls and protection, safety monitoring, and worker teaching programs is essential to guard in opposition to risk actors that may trigger your enterprise monetary and reputational loss.
AT&T Cybersecurity has a broad portfolio of managed safety providers that can assist you defend throughout your assault floor. Contact us in the event you’d prefer to be taught extra.