Many organizations — together with fairly a couple of Fortune 500 companies — have uncovered net hyperlinks that permit anybody to provoke a Zoom video convention assembly as a legitimate worker. These company-specific Zoom hyperlinks, which embrace a everlasting consumer ID quantity and an embedded passcode, can work indefinitely and expose a corporation’s workers, clients or companions to phishing and different social engineering assaults.

Picture: @Pressmaster on Shutterstock.
At concern is the Zoom Private Assembly ID (PMI), which is a everlasting identification quantity linked to your Zoom account and serves as your private assembly room obtainable across the clock. The PMI portion types a part of every new assembly URL created by that account, comparable to:
zoom.us/j/5551112222
Zoom has an choice to incorporate an encrypted passcode inside a gathering invite hyperlink, which simplifies the method for attendees by eliminating the necessity to manually enter the passcode. Following the earlier instance, such a hyperlink would possibly look one thing like this:
zoom.us/j/5551112222/pwd=jdjsklskldklsdksdklsdkll
Utilizing your PMI to arrange new conferences is handy, however in fact comfort usually comes on the expense of safety. As a result of the PMI stays the identical for all conferences, anybody together with your PMI hyperlink can be a part of any ongoing assembly except you have got locked the assembly or activated Zoom’s Ready Room function.
Together with an encrypted passcode within the Zoom hyperlink positively makes it simpler for attendees to hitch, but it surely would possibly open your conferences to undesirable intruders if not dealt with responsibly. Significantly if that Zoom hyperlink is by some means listed by Google or another search engine, which occurs to be the case for hundreds of organizations.
Armed with certainly one of these hyperlinks, an attacker can create conferences and invite others utilizing the id of the licensed worker. And plenty of corporations utilizing Zoom have made it simple to search out lately created assembly hyperlinks that embrace encrypted passcodes, as a result of they’ve devoted subdomains at Zoom.us.
Utilizing the identical methodology, KrebsOnSecurity additionally discovered working Zoom assembly hyperlinks for The Nationwide Soccer League (NFL), LinkedIn, Oracle, Humana, Disney, Warner Bros, and Uber. And that was from only a few minutes of looking. And as an instance the persistence of a few of these Zoom hyperlinks, Archive.org says a number of of the hyperlinks had been first created way back to 2020 and 2021.
KrebsOnSecurity obtained a tip concerning the Zoom exposures from Charan Akiri, a researcher and safety engineer at Reddit. In April 2023, this web site featured analysis by Akiri displaying that many public Salesforce web sites had been leaking personal information, together with banks and healthcare organizations (Akiri stated Salesforce additionally had these open Zoom assembly hyperlinks earlier than he notified them).
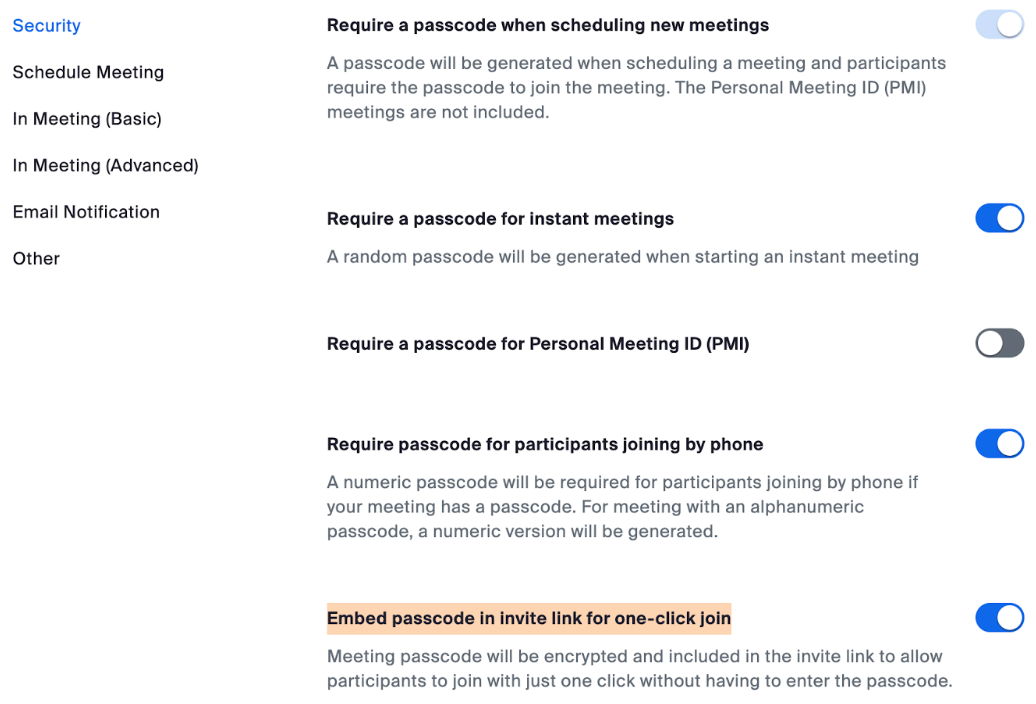
The Zoom hyperlinks that uncovered working assembly rooms all had enabled the highlighted choice.
Akiri stated the misuse of PMI hyperlinks, notably these with passcodes embedded, can provide unauthorized people entry to conferences.
“These one-click hyperlinks, which aren’t topic to expiration or password requirement, will be exploited by attackers for impersonation,” Akiri stated. “Attackers exploiting these vulnerabilities can impersonate corporations, initiating conferences unknowingly to customers. They will contact different workers or clients whereas posing as the corporate, gaining unauthorized entry to confidential data, doubtlessly for monetary achieve, recruitment, or fraudulent promoting campaigns.”
Akiri stated he constructed a easy program to crawl the online for working Zoom assembly hyperlinks from completely different organizations, and up to now it has recognized hundreds of organizations with these completely purposeful zombie Zoom hyperlinks.
Based on Akiri, listed below are a number of suggestions for utilizing Zoom hyperlinks extra safely:
Don’t Use Private Assembly ID for Public Conferences: Your Private Assembly ID (PMI) is the default assembly that launches once you begin an advert hoc assembly. Your PMI doesn’t change except you alter it your self, which makes it very helpful if individuals want a solution to attain you. However for public conferences, it’s best to all the time schedule new conferences with randomly generated assembly IDs. That approach, solely invited attendees will know methods to be a part of your assembly. You may also flip off your PMI when beginning an prompt assembly in your profile settings.
Require a Passcode to Be part of: You possibly can take assembly safety even additional by requiring a passcode to hitch your conferences. This function will be utilized to each your Private Assembly ID, so solely these with the passcode will be capable of attain you, and to newly scheduled conferences. To study all of the methods so as to add a passcode on your conferences, see this assist article.
Solely Permit Registered or Area Verified Customers: Zoom also can provide you with peace of thoughts by letting you already know precisely who shall be attending your assembly. When scheduling a gathering, you possibly can require attendees to register with their e mail, identify, and customized questions. You possibly can even customise your registration web page with a banner and brand. By default, Zoom additionally restricts contributors to those that are logged into Zoom, and you’ll even limit it to Zoom customers whose e mail deal with makes use of a sure area.
Additional studying: Learn how to Hold Uninvited Visitors Out of Your Zoom Assembly
Replace 12:33 p.m.: The record of affected organizations was up to date, as a result of a number of corporations listed apparently solely uncovered hyperlinks that allow anybody hook up with current, always-on assembly rooms — not provoke and utterly management a Zoom assembly. The true hazard with the zombie hyperlinks described above is that anybody can discover and use them to create new conferences and invite others.

